Report: Fake Android Apps Were Used to Monitor Iranian Protesters
vpnMentor has teamed up with cybersecurity firm ClearSky to release this report.
Following the protests that broke out in December 2017, the Iranian government cracked down on internet usage and blocked popular social media sites like Twitter and Telegram.
In response, many Iranians began to use to VPNs in order to bypass these restrictions and access censored sites and apps.
On January 6, while monitoring cyberspace activity in Iran, ClearSky identified complaints from citizens about suspicious text messages that encouraged them to download a VPN in order to easily connect to Telegram.
ClearSky conducted an investigation that revealed malicious Android software called Ir.ops.breacker, which imitated the popular VPN app, Psiphon.

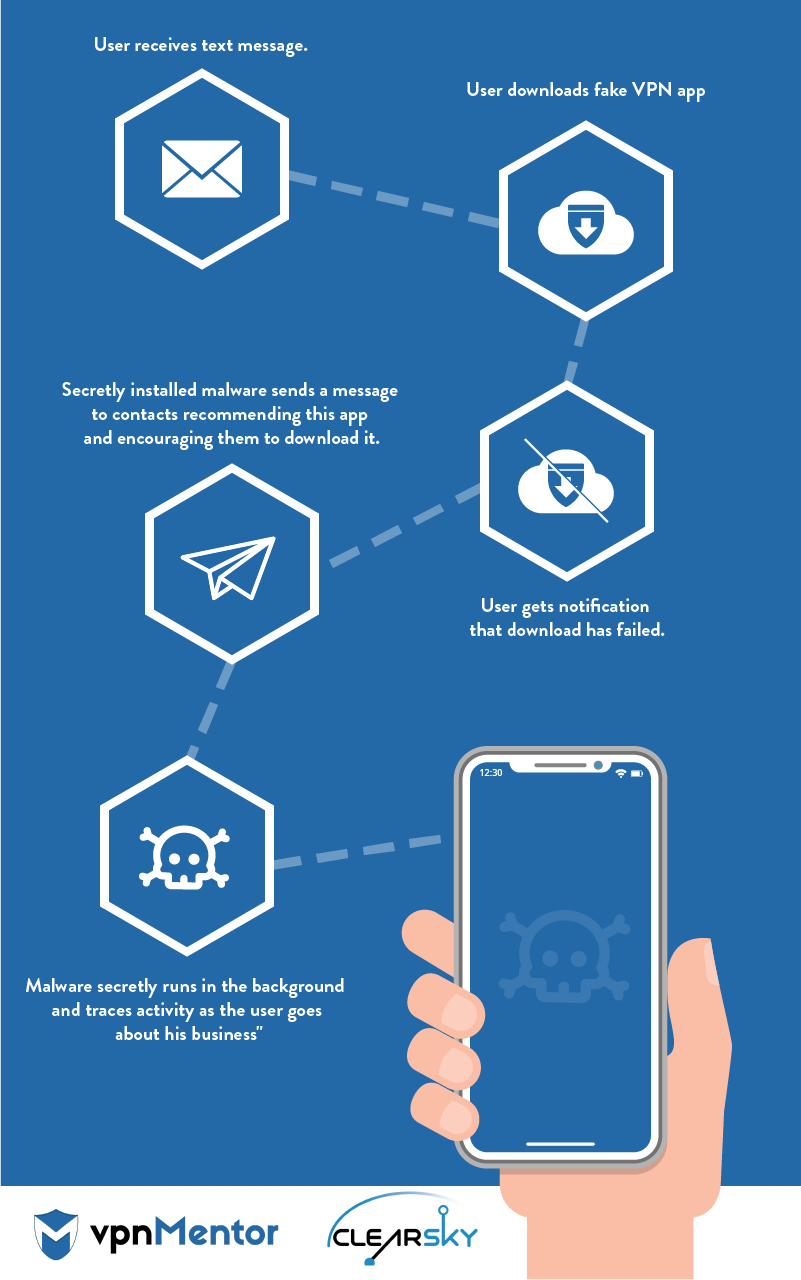
The following is a close look at how this malware impersonates Psiphon and spreads.
How the Virus Operates
Targeted users receive the following text message:
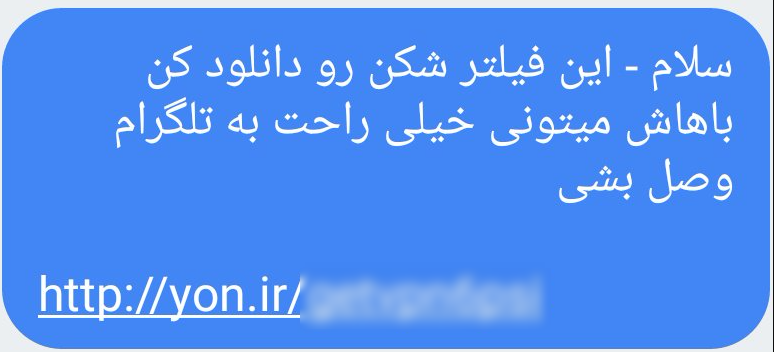
[translation of message in Farsi: Hello - download this VPN in order to easily connect to Telegram]
This text promises users that if they download this VPN, they can unblock Telegram.
To make it look like a safe URL, the attackers use the Iranian qqt address shortcut (the equivalent of bit.ly service) to disguise the original address, which is serverclient12[.]tk/dlvpn/vpn[.]apk
When users arrive to this domain, an apk called psiphon6 – which bares the official Psiphon logo – automatically downloads.
When the user installs this fake VPN, the app asks for permission to access the user’s phone.
Below is the list of permissions requested by the app.
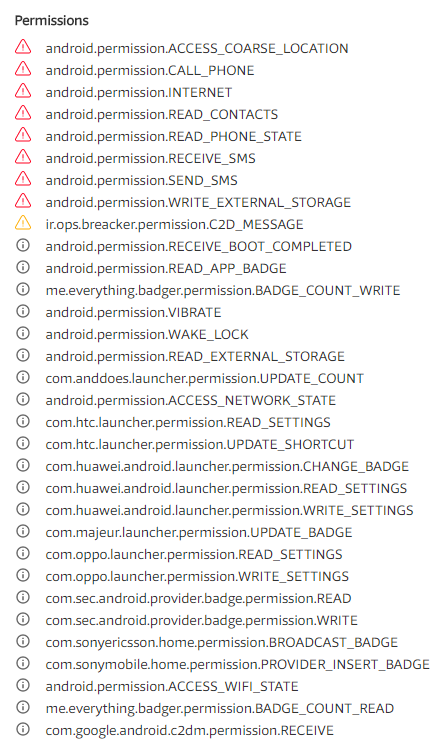
The app also requests access to the user’s contact list. In our investigation, VirusTotal, a service that combines all major antivirus software, indicated that the requested permission to send text messages was suspicious.
This permission allows the malware to send hidden text messages to the user’s contacts without the user’s knowledge. This is how the attacker spreads the malware.
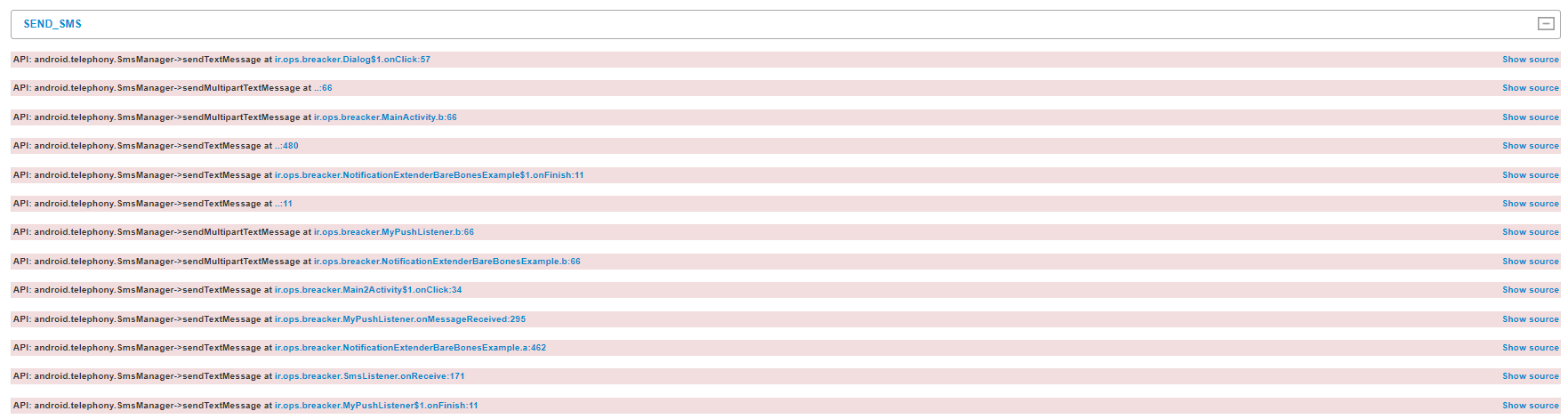
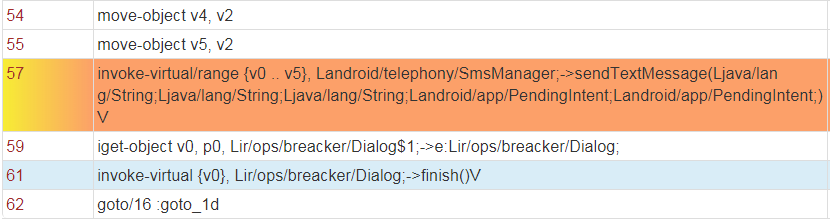
When the user attempts to open the app, he is requested to connect to the internet. He then receives an error message and is requested to connect again. After receiving another (fake) error message, a new message appears notifying the user that the app didn’t install correctly, and he needs to reinstall it from the Google Play Store.
A message then appears saying the app was deleted from the device. However, in reality, the app is still there and running in the background.
How We Traced the Malware
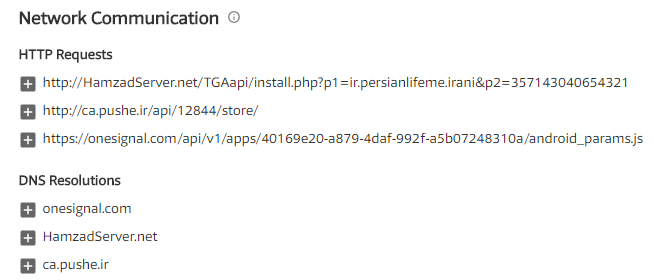
Once the malware is installed, it uses two push alert services to move commands from the C&C server under the HamzadServer[.net] domain to the servers ronash[.]pushe[.]Ir and onesignal[.]com.
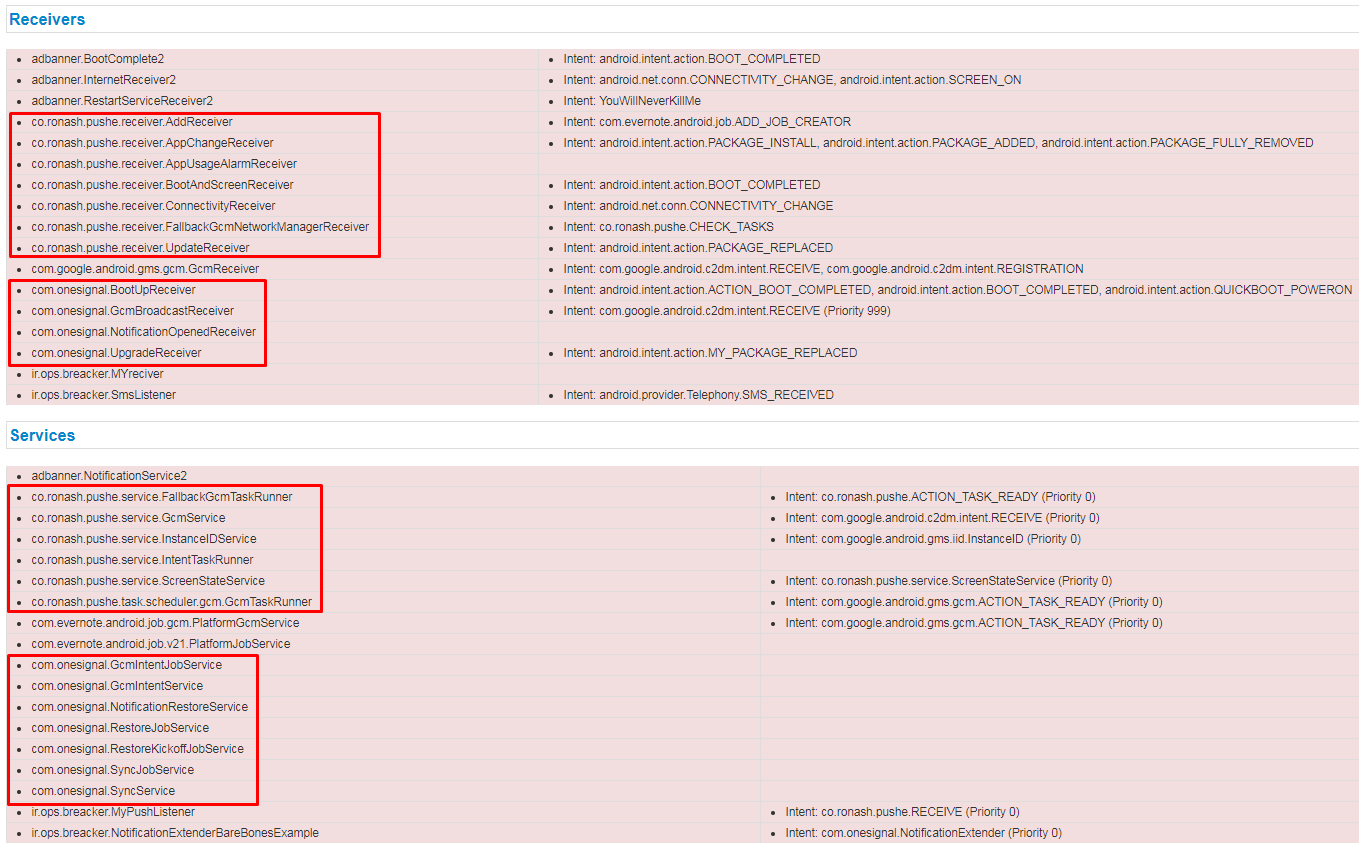
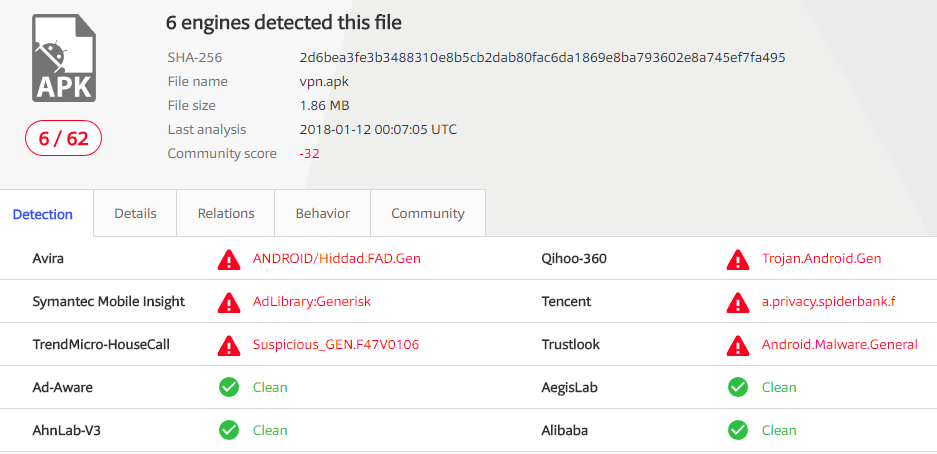
When we scanned the apk file on VirusTotal, only six antivirus services flagged it. (A recent rescan showed that now 23 engines detect it as a virus.)
This means that even if you have antivirus software installed on your phone, it most likely won’t classify the file as malicious. Furthermore, we believe there are other malwares working in a similar manner that have yet to be flagged by antivirus software.
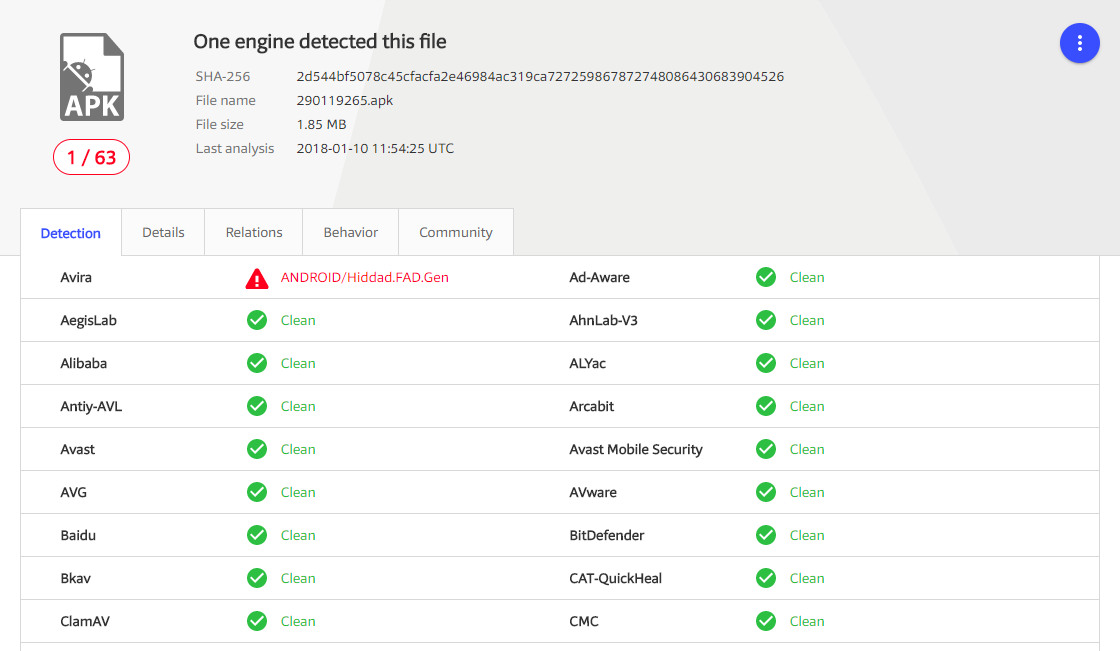
Specifically, we found that the php page http://elicharge[.]/Ir/mp20ibest[.]php is suspicious. This php page was also flagged as being present in other malware with the same characteristics, including the malware that masquerades as Android TV (using the logo stolen from a TV app called TocaTV, which was discontinued).

As you can see, when we scanned this file, only Avira identified it as a virus.
When we traced the HamzadServer.net domain, we saw that the main domain where the malicious applications were planted is serverclient12.tk
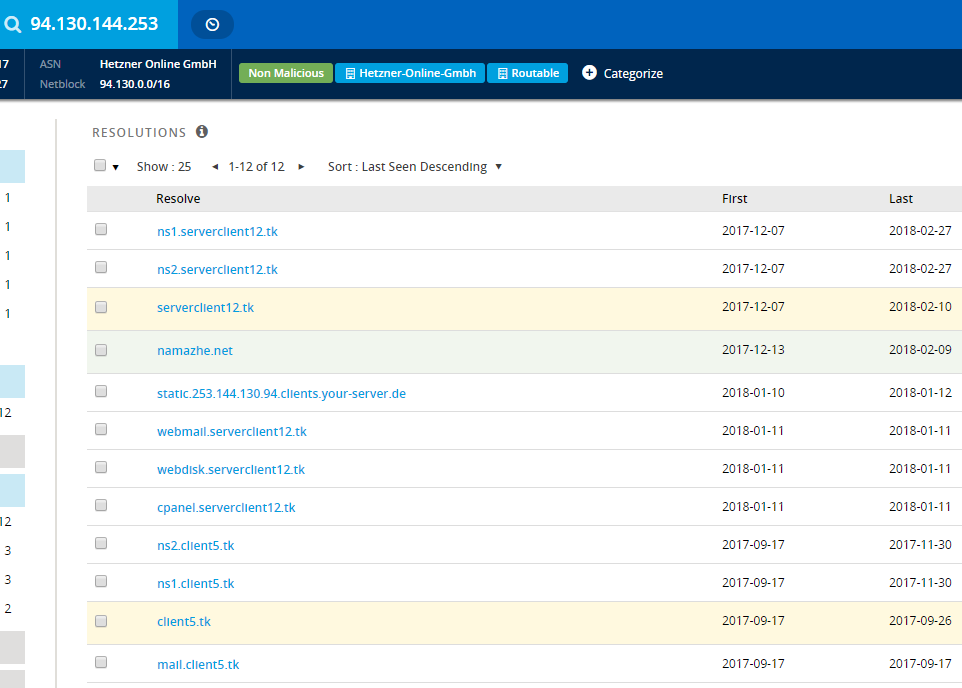
This domain is linked to the IP address 94.130.144.253, as are several other domains, all of which are for sale, except namazhe[.]Net
Using Whois we traced the email of the person who registered the domain name – apd_1379@yahoo.com.
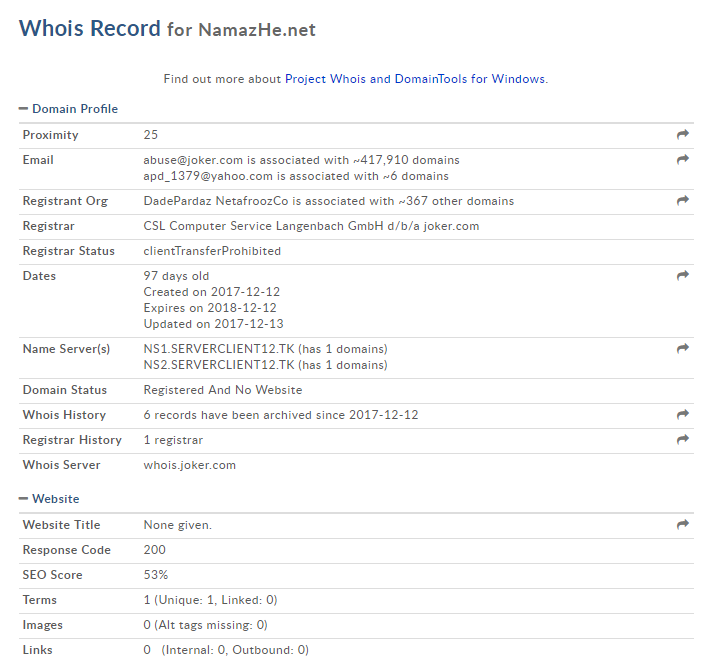
We found five more domains associated with this email address, including elipay[.]net and hamzad[.]net (which is mostly likely connected to the server hamzadserver[.]net).
According to the Whois data, the person who registered the domain is linked to the email address rilufeapd@gmail.com which, like the previous address, contains the term APD.
An additional domain was opened by the email address apd_1379@yahoo.com.
We don’t know exactly who is sending out these text messages. However, we do know that this malware is very sophisticated. Whether it’s government operated or not, it traces Iranians’ mobile activities without permission and has already spread virally throughout the country.
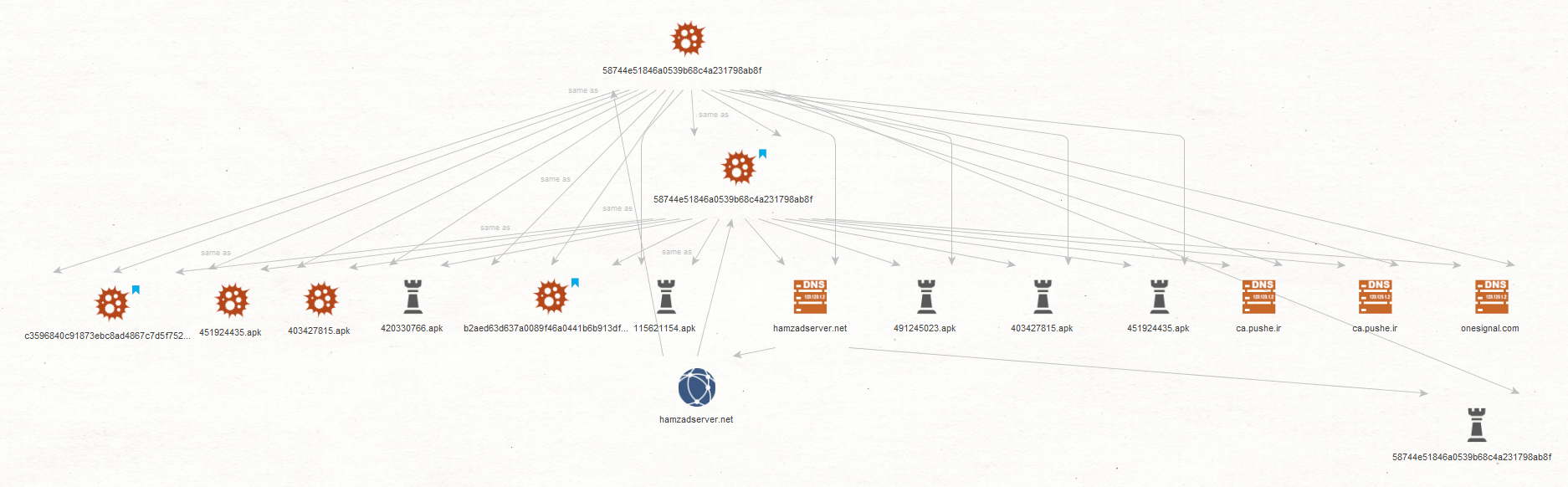
Below is a Maltego graph showing the connections between the hamzadserver central server and the various malware:
To Summarize
Ironically, the intended victims of this attack are users who prioritize their privacy and seek to utilize the secure messaging platform Telegram. However, the deceptive VPN application employed in this scenario cunningly spies on their activities and surreptitiously propagates itself to their contacts, all without their awareness.
Since governments all over the world are actively recording and tracking citizens who legally protest, it is advisable to take security measures and be wary of messages that suggest to install apps, even if the name of the app is familiar and the message comes from a known contact.
About ClearSky and vpnMentor

Clearsky – Over the past several years Clearsky Security has been monitoring the cyber activity of threat groups in the Middle East, including Iranian actors. In recent months we identified an increase of Iranian social engineering campaigns. Of note, in December we exposed a campaign by the Charming Kitten group, which created a fake western news agency called "Britishnews," and in February we exposed an Iranian disinformation campaign targeting western media outlets such as the BBC.

vpnMentor – Our site evaluates over 300 VPNs on the market. It allows users to rate each of the VPNs, differentiating the good ones from the bad. We actively check VPNs for leaks and adherence to their privacy standards and other policies, performing a service for which the average user does not have resources.
We encourage you to share this report by whatever means you wish (including copying the images it includes), with attribution to the source.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.


Please, comment on how to improve this article. Your feedback matters!