Dave Peck, Co-Founder of Cloak, Reveals What Cloak VPN Can and Cannot Do - Interview
- vpnMentor: I understand that Cloak VPN began in the coffee shops of Seattle. What motivated you to begin this startup?
- vpnMentor: Nick Robinson is the “Product Guy,” Peter Sagerson is the “Engineering Guy,” and you are the “Everything Guy.” What does that mean?
- vpnMentor: What’s the glue that holds you together?
- vpnMentor: What makes Cloak unique?
- vpnMentor: What cautions do you have about VPN usage?
- vpnMentor: You are passionate about the integrity that goes with providing VPN services. How does that show up at Cloak?
- vpnMentor: What does that mean for Cloak and the services you provide?
- vpnMentor: You recently said that President Obama is wrong about privacy and encryption. The president “misunderstands that ‘encryption absolutism’ is not an ideological position. It’s a technical one.” How does this affect the average consumer?
- vpnMentor: Mainland China is notorious for blocking everything internet, and now they are fighting the services that try to unblock sites, e.g. VPNs. What’s your recommendation for using a VPN beyond the Great (fire) Wall?
- vpnMentor: What are the competitive advantages of using Cloak VPN?
- vpnMentor: After a while with Cloak, you launched OverCloak. What is it exactly and why do VPN users need it?
- vpnMentor: Any upcoming trends we should know about?
- vpnMentor: What does that mean for Cloak?
- vpnMentor: What are you most proud of?
- vpnMentor: What is your advice for staying safe online?
- Summary
Dave Peck, Co-Founder of Cloak, reveals the inside scoop on what you should expect from a VPN provider, and he predicts surprising trends you might not have seen coming in a dynamic industry that never rests. A former software engineer and now Everything Guy in a company with a stellar rating from Macworld, Dave already knows what you need to know for yourself and for your clients, and he’s willing to share it all here with you. Share
With Dave Peck, Nick Robinson and Peter Sagerson working on the VPN security you need for encrypting your transmitted data, you don’t have to worry about what’s “under the hood” of the products and services they provide at Cloak.
Cloak users enjoy user friendly VPN that comes with honesty and integrity, and this interview with Dave Peck shows why.
vpnMentor: I understand that Cloak VPN began in the coffee shops of Seattle. What motivated you to begin this startup?
We were working as freelance software developers in coffee shops here in town, and we realized we needed this tool for ourselves. We looked at the landscape of consumer VPNs, and we felt that we could offer something a little different, based on what mattered to us.
We care about providing quality security features while trying to build a company that is direct and cautious about how it differentiates itself based on claims of what it does and doesn’t do.
vpnMentor: Nick Robinson is the “Product Guy,” Peter Sagerson is the “Engineering Guy,” and you are the “Everything Guy.” What does that mean?
I am a software developer. Prior to working at Cloak, I was a software engineer at Microsoft here in the Seattle area; this background was the most important thing I could bring to the table.
When you build a company, you end up wearing a lot of hats.
It turned out that I ended up wearing a bunch of them early on in getting the whole project together with shipping the actual software and keeping up-to-date with security changes. “Everything Guy” means I am wearing the most hats right now. Peter and Nick wear many hats, too — none of us really does just one thing.

vpnMentor: What’s the glue that holds you together?
When I look at the broader question of online digital security and safety, I see Cloak as a niche in a much broader and dynamic market.
The three of us are excited about this broader space. For the long-term, we are looking at building products that our customers will really like.
vpnMentor: What makes Cloak unique?
Cloak is different than most VPN companies.
While some VPNs advertise that they allow you to by-pass geographic blocks to watch Netflix or BitTorrent online with impunity, Cloak wants to provide real security software so that when you are using untrusted networks, you can have a strong guarantee that your data is securely transmitted away from that network. You won’t be exposed to network security threats.
That has led us to build features that the rest of the VPN universe doesn’t have, and it encourages us to talk about ourselves and our future in a different way.

vpnMentor: What cautions do you have about VPN usage?
While there are undoubtedly many very good VPN providers, always be aware of free VPN services, and do your research about the company. Be aware of their intentions; some of these companies may sell your information or otherwise abuse your trust.
Additionally, other VPN companies may charge a one-time fee for life. My concern with this approach, however, is that consumers don't get to vote with their dollars; there is no economic incentive for the VPN service provider to improve their VPN services. The consumer must trust that the provider updates its software and meets the promised security guarantees.
There’s got to be a financial incentive for VPN providers to improve their services; when selecting a VPN provider, choose the company that you feel best looks after the users’ interests.
vpnMentor: You are passionate about the integrity that goes with providing VPN services. How does that show up at Cloak?
We see the words security, privacy and anonymity used a lot in the marketing copy for our VPN competitors. I get the feeling that some VPN companies want to use these words to confuse potential customers about what they provide. Some companies seem to suggest that you’ll be completely hidden online and you can do “bad stuff” without anyone knowing.
Anonymity, to me, is a very strong concept meaning that your identity isn’t known and can’t be known. That’s really hard to achieve in practice, and I’m not convinced that any third party VPN solution can provide that.
When I see companies promising anonymity, I feel like it’s not really something you can promise, or that a third-party VPN service can deliver, so Cloak is very careful to say we don’t do that.
Some customers believe that if their IP address hidden then no one will know who they are. Changing your IP address is really a side effect of the safety and security that VPNs provide when you are on untrusted networks. Changing your IP address could keep you hidden online but remember that when you are using a web browser there are a million ad and tracking services that are trying to watch you. There are a million ways to figure out who you are online and they have nothing to do with your IP address. From a technical perspective, we don’t think that changing your IP address is a good way to hide your identity.
vpnMentor: What does that mean for Cloak and the services you provide?
Cloak’s guarantee is that we will correctly and reliably encrypt your data and send it away from the network you don’t trust. That is the extent.
All of the security threats that come from things like sidejacking, traffic injection, or eavesdropping — the kind of attacks that you would expect from hackers who are sitting in the Starbucks with you, or from bad actors who have control of the router or the network you’re connected to.
With Cloak, you don't need to worry about those things. That’s what we want to promise to our customers: nothing more and nothing less. For our customers, that is exactly the right set of promises, and VPN can be a useful tool to have.
vpnMentor: You recently said that President Obama is wrong about privacy and encryption. The president “misunderstands that ‘encryption absolutism’ is not an ideological position. It’s a technical one.” How does this affect the average consumer?
I am not a legal professional, but in the Apple vs. United States government question, I think it's very clear that the government is overreaching. I agree with the philosophical stance that Apple is taking; If we open the floodgates a little bit, we’re going to be opening them a lot.
There’s not a single academic or industry cryptographer or security expert who thinks that “safe” backdoors are actually technically feasible. They can’t be built in a way that keeps people safe and also gives the government access only when they need it.
Our inability to create a “secure” backdoor is not due to a lack of technical imagination. Our inability to create it is a fundamental feature of cryptography. Even if, in some alternate universe, it were for us to have these backdoors, I would strongly question the value of them. I would fall on the side of trying to restrict them whenever possible.
I feel very strongly that absolutism is a necessary stance only because the technology tells you that you can't do anything else. The idea that you can't be an encryption absolutist doesn't sit well with me.
vpnMentor: Mainland China is notorious for blocking everything internet, and now they are fighting the services that try to unblock sites, e.g. VPNs. What’s your recommendation for using a VPN beyond the Great (fire) Wall?
We tell customers who travel to Mainland China that they should not expect to have reliable internet connectivity or possibly any internet connectivity that they can trust during their entire trip.
These users should have multiple VPN services available to them. We generally recommend opening up accounts with some of our competitors and making sure that those services are installed and ready to go before they even hit the ground in China.
The final thing that we recommend is to make sure that you have multiple VPN protocols at your disposal. At the very least, make sure you can support both OpenVPN TLS and IPSec. We find that entire classes of protocols are sometimes completely blocked for a period of time.
If you are not able to secure your connection at any given time, we strongly recommend not using the Internet — at least not if you value your personal privacy.
We have found that the great firewall is very dynamic. What works one day may not work the next, and the other way around. It will work great in Beijing but not in Shanghai, or the other way around, but it’s very hard to triangulate exactly what is happening there. Our customers who travel to mainland China tell us that the results of using Cloak in particular are wildly varied.
vpnMentor: What are the competitive advantages of using Cloak VPN?
Because we’re so focused on security, we have built some features that you don’t see very often in our competition, if at all.
Security is not something that you as a consumer should have to think about. A lot of VPN client apps are big and fancy: they draw maps of the world and they get in your face. We try to be the opposite.
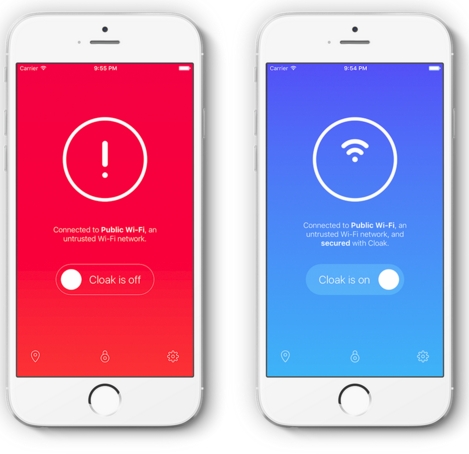
Once you login to Cloak, you should never have to think about it again. We want to recede into the background. To do this, we built the concept of trusted networks into our apps. We have a set of preferences in our apps that let you tell Cloak which networks you trust. Then, when you connect to a network you don’t trust, Cloak automatically secures your connection.
This means that you don’t even have to remember to use Cloak to get its security benefits! Open your laptop or iPhone and connect to the Wi-Fi at the coffee shop or an airport, and the app immediately sees a network it doesn't trust and secures your connection.
Under the hood, Cloak also works hard to deliver a high-performance secure connection. Performance is of course a tradeoff anytime you use a VPN. That’s why, every time you secure yourself, Cloak makes sure you have the lowest hit to your latency possible.
Cloak iOS app - 4 stars rating for this "easy to use" app
vpnMentor: After a while with Cloak, you launched OverCloak. What is it exactly and why do VPN users need it?
When you first open your laptop lid, there is a period of time when you are connected unsafely to the WiFi. While you are trying to secure your connection, you have apps chattering away over the network, possibly leaking data.
That's why we built our feature called OverCloak. On a Mac, it uses the built-in firewall, and it shuts down the networking hard so that no data gets in or out until a secure connection is established. It's a complicated feature, and although we have seen competitors try to provide kill switches before, ours is a stronger.
OverCloak has to take captive portal networks into account, giving you just enough access so you can log in to the network, while still ensuring your important data is safe. We do a lot of backflips in OverCloak to make this work. It's not something that I have seen duplicated.
We built OverCloak because we are so focused on using VPNs as a security measure. Even though we've had OverCloak on the market for several years, surprisingly, nothing else's come close to it.
vpnMentor: Any upcoming trends we should know about?
A few trends will change the way consumers relate to VPNs.
Companies like Google and Apple are pushing hard on the entire Internet to secure their websites and endpoints. There are a percentage of websites that offer https only by default; it’s much higher than it was a few years ago.
And the Electronic Frontier Foundation (EFF) just started their new Let’s Encrypt program, to provide free and trustworthy TLS certificates to website owners. These certificates are accepted in all major browsers, which is a huge step forward for the web as a whole.
From a security perspective, the day that the entire Internet uses SSL or TLS to secure your connectivity to everything is the day we close up shop because VPNs then won't provide a lot of security benefit. Although that day is a long way away, the percentage of TLS secured traffic is going up — a lot faster than I would've expected.
Companies like Google are also pushing good initiatives like a future version of Chrome that will shows you a broken lock Icon if you are on a normal HTTP (non-secure) website. Although Today you see nothing in when you visit these websites in Chrome, but Google’s update will make it obvious when there is no security.
In a decade we may be living in a world where everything all network traffic is secure by default, and that is an exciting world in which to live.
vpnMentor: What does that mean for Cloak?
We just have to broaden the kinds of products we offer to consumers and small businesses. Consumers may not always need VPN, but small businesses will always need to build secure, private networks. There are also a lot of other new privacy-related tools we can offer down the road.
I perceive a future where VPNs may no longer serve as a security solution. This transition is not imminent, nor likely within the forthcoming five years, but it wouldn't astonish me if it occurred within the next decade.
Another interesting trend we are watching is the switch to IPv6. There are a few things driving this momentum, especially cellular network providers — most of whom would undoubtedly love to cut out IPv4. In a few years, there may be only IPv6 cellular connectivity, and that’s going to change the reliability of a lot of VPN software on the market now. A lot of VPN software does the “wrong thing” in the face of IPv6. A recent study showed that many VPN apps simply weren’t IPv6 aware, and as a result, IPv6 data was skipping the secure tunnel entirely. The VPN apps would indicate that they were offering a secure connection... but they weren’t.
For Cloak, we currently shut down IPv6 completely as a security measure, but by the end of this year or early next year we will support IPv6 system-wide. This is a big leap that everyone in the industry will have to make.
vpnMentor: What are you most proud of?
We have users who know they need the kind of security Cloak VPN provides, and even though they have no idea how things work under the hood, they can install our app and get it running in two or three minutes or less, and get a secure connection.
This is due to the work Nick has done on user experience.
We are also proud of building a company that is very direct about its services and capabilities. We feel clear communication is very important in any VPN provider; we’re disappointed and alarmed by how little the consumer VPN market segment seems to prize clarity and transparency overall.
vpnMentor: What is your advice for staying safe online?
It’s easy if you do a handful of things.
First, use a password vault or management app. If you are not doing this, do it now. Never share passwords from site to site or use weak passwords.
Second, if you are on a Mac, enable FileVault full disk encryption. If you lose your laptop, you never have to worry about people recovering data from it. And enable pin codes on iPads and iPhones, opting for 6-digit access or, even better, strong passphrases.
Third, use a trusted VPN service any time you are connected to networks you don't trust.
Summary
To further keep users safe online, Cloak VPN takes care of security and safety behind the scenes for their clients. Dave Peck, along with Nick Robinson and Peter Sagerson, sees to that. Cloak’s intention is to always do the right things by protecting their users with software that has the consumer’s best interests in mind. It’s something they are passionate about, and it’s something that they wish all VPN providers would do.
*The interview was conducted by Debi Christensen on behalf of vpnMentor.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.


Please, comment on how to improve this article. Your feedback matters!