Report: Software Companies Exposed to Hacking in Major Data Breach
- Data Breach Summary
- Company Profile
- Timeline of Discovery and Owner Reaction
- Example of Entries in the Blob Account
- Pitch decks
- Source codes
- Data Breach Impact
- Corporate Espionage & Theft of Intellectual Property
- Advice from the Experts
- Securing an Open Blob Storage
- Advice For The Companies Affected
- How and Why We Discovered the Breach
- About Us and Previous Reports
- Help Us Protect The Internet!
Led by Noam Rotem, vpnMentor’s research team recently uncovered a data breach exposing sensitive internal data, which may presumably be owned by one of the biggest companies in the world: Microsoft.
The data in question was stored on a misconfigured Microsoft Azure cloud storage account. The owner of the data (presumably Microsoft) failed to adequately secure the files. As a result, they were easily accessible to anyone with even the most basic hacking skills.
The files appeared to originate from a series of pitches made to Microsoft Dynamics from numerous companies vying for a project or partnership with the company. Many of the pitches included the source codes for software products - some of which were eventually released to the market.
As a result, each of these firms - including some well-known companies - was exposed, with highly sensitive internal data about their operations and product lines publicly accessible.
Data Breach Summary
| Company | Presumably Microsoft (the presumption stems from the content of the leaked files) |
| Headquarters | USA |
| Industry | Consulting; Enterprise software products |
| Size of data in gigabytes | 63GB |
| Suspected no. of files | 3,800+ |
| No. of people exposed | N/A |
| Date range | January - September 2016 |
| Geographical scope | Global |
| Types of data exposed | Business pitches; product descriptions, product code, hardcoded passwords |
| Potential impact | Corporate espionage; theft of intellectual property |
| Data storage format | Misconfigured Microsoft Azure Blob Storage |
Company Profile
Microsoft Dynamics is a suite of integrated enterprise products and software applications offered by Microsoft to large companies primarily working in financial services, retail, the public sector, and manufacturing.
Many of the products sold under the Microsoft Dynamics brand were developed by small independent software companies and acquired by Microsoft. The company then integrated each of these separate products into a single product line.
Microsoft Dynamics focuses on software products related to enterprise resource planning (ERP), customer relationship management (CRM), and software as a service (SAAS).
Timeline of Discovery and Owner Reaction
- Date discovered: 7th January 2021
- Date KPMG contacted: 11th January 2021
- Date of response: 12th January 2021
- Date Microsoft contacted: 12th January 2021
- Date of action: by 23rd February 2021
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, our team discovered an unsecured Microsoft Azure Blob account containing 100s of files. Azure Blob Storage is a popular form of cloud storage developed by the tech giant for large enterprise costumes, like multinational companies.
After an initial investigation, we identified two potential owners, starting with Canadian consulting firm Adoxio. As KPMG now owns Adoxio, we contacted KPMG to notify it of the breach.
KPMG replied, confirming it didn’t own the data and suggested it belonged to Microsoft.
We also suspected Microsoft was responsible. So, we then reached out to the company several times to ensure the files were made secure and to confirm the data belonged to it. While we received only automated responses from the company, the Azure Blob account was secured in the meantime.
Over two months after initially discovering the vulnerability, we finally received a reply from Microsoft. However, the company appears to have mistaken the data breach disclosure for a disclosure of a flaw in its software. In its response, Microsoft failed to acknowledge the data breach or claim responsibility. As a result, we have no way to verify whether the file belongs to Microsoft.
Update: In late April, once the story started to circulate in the press, a journalist notified us that Microsoft had claimed the cloud storage account was a 'demo' - thus indirectly confirming it belonged to the company.
Example of Entries in the Blob Account
The contents of the blob were all from late September 2016. They appear to be pitches made to Microsoft from various tech companies, and relating to its then-recent purchase of the Dynamic 365 CRM.
Companies whose pitches were exposed include Adoxio (now Adoxio KPMG), Adobe, and more.
Data in the Blob storage account can be broken into two categories:
1. Pitch decks
The breach exposed up to 100 pitch decks outlining various features, benefits, etc., of products being pitched to Microsoft by each company. These included products that the company eventually adopted, such as ‘Package Deployer.’

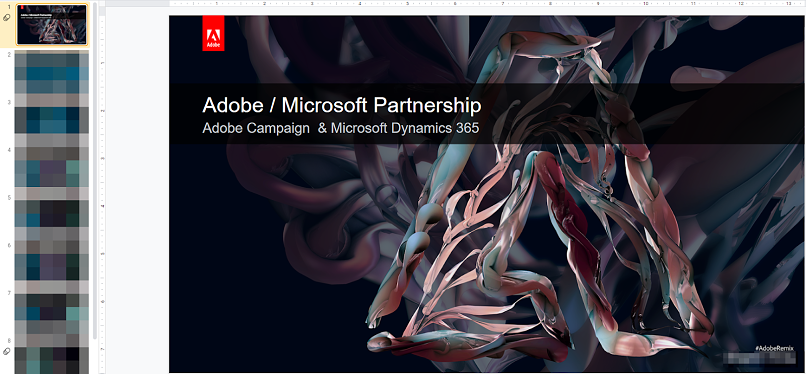 Screenshots from leaked pitches made to Microsoft
Screenshots from leaked pitches made to Microsoft
The partnership between Microsoft and Adobe was announced publicly before the discovery of the data breach.
2. Source codes
Some of the pitches were accompanied by source codes for the products being presented to Microsoft.
Between 10-15 products had source codes exposed, including passwords for live databases that had been hardcoded into the source codes.
An exposed source code makes it much easier for hackers to find vulnerabilities in a product or database and gain access to highly sensitive areas which data security protocols would typically protect.
With such access, they could extract highly sensitive data or even assume control of some of the systems running the code, to devastating effect.
The following screenshot shows a configuration file with passwords and addresses of databases and internal information about the application.
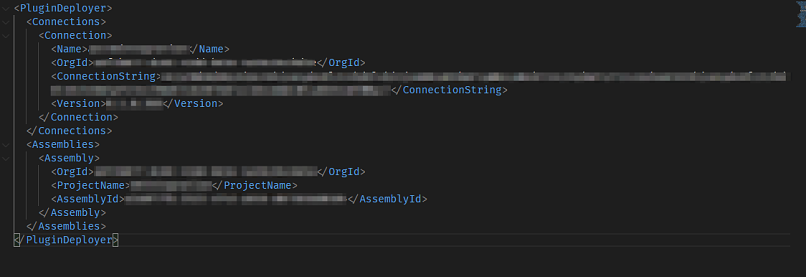 Sample of exposed source code for a software product
Sample of exposed source code for a software product
In the following, you can see the size and number of files in one of the source code archives for a single product.
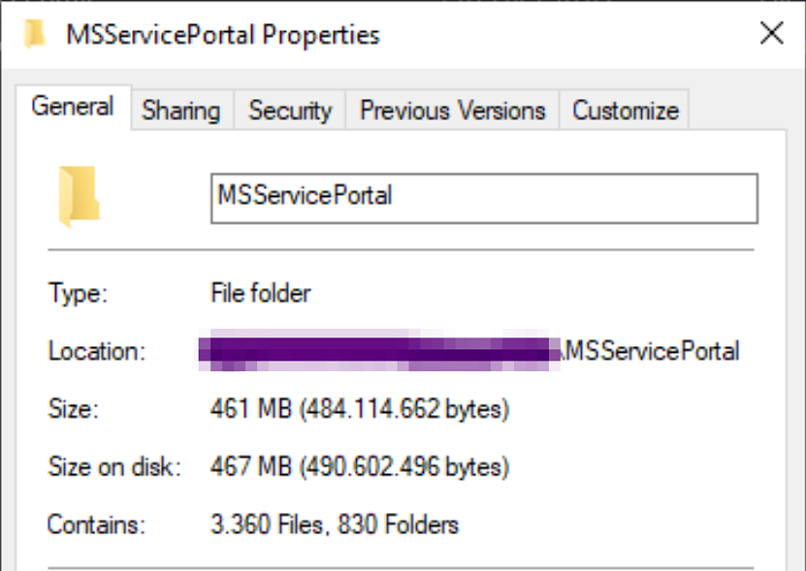 Source code archives
Source code archives
Data Breach Impact
This breach could have had severe consequences for the companies exposed.
By exposing product source codes, whoever was responsible for the breach compromised any data security protocols in place for each product. Malicious hackers could use the source code to identify vulnerabilities otherwise hidden and easily break into the products.
Upon doing so, they would gain access to the most sensitive data from a product, including admin credentials like usernames and passwords. Hackers could easily download all of this information and sell it on the dark web.
Alternatively, they could find ways to embed malicious viruses like malware or spyware into the product. If the software was connected to a larger network, they could potentially use the source code from this one product to access and infect an entire network.
Corporate Espionage & Theft of Intellectual Property
Source codes are the most valuable assets for software and technology companies. As a result, they’re often closely guarded secrets.
This data breach exposed the source codes for 10-15 software products belonging to numerous companies. As a result, had the data breach been discovered and leaked online publicly, competitors to these companies could have had the opportunity to steal and replicate the source codes, creating rival products for much cheaper.
Advice from the Experts
The owner of this Blob account could have easily avoided exposing its data if it had taken some basic security measures. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open Blob Storage
It’s important to note that open, publicly viewable Blobs are not a flaw of Azure. Microsoft provides detailed instructions to Azure users to help them secure Blobs and keep them private.
In this case, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow Azure access and authentication best practices.
- Add more layers of protection to their Azure account to further restrict who can access it from every point of entry.
Advice For The Companies Affected
If you think a pitch you made to Microsoft was exposed in this breach, contact the company directly to find out what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It demonstrates the numerous methods employed by cybercriminals to target individuals using the internet, while also providing guidance on the measures you can adopt to ensure your safety.
How and Why We Discovered the Breach
The vpnMentor research team discovered this data breach as part of a huge web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this Azure Blob account because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the data’s owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to KPMG and Microsoft to let them know about the vulnerability and suggest ways to make their systems secure.
These ethics also mean we carry a responsibility to the public. Companies (and their employees) must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence - and no way of knowing - whether the data in our reports have been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included a group of free VPNs secretly tracking their users’ activity and data and leaking it online. We’ve also uncovered potential criminal activities and scams targeting users on Spotify, Instagram, and Facebook.
You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.


Please, comment on how to improve this article. Your feedback matters!