What Are the 5/9/14 Eyes Countries? Surveillance in 2026
- What Are the 5 Eyes, 9 Eyes, and 14 Eyes Alliances?
- What Impact Does the 5/9/14 Eyes Alliances Have on Citizens?
- What Type of Data Does the 5/9/14 Eyes Alliance Collect?
- Surveillance Systems Used By These Alliances and the Data They Collect
- What Are the Best Ways to Safeguard Your Privacy in 5 Eyes Regions?
- Should You Avoid VPNs That Are Located in the 5/9/14 Eyes or Using Servers in These Countries?
- Quick Checklist for Choosing A Privacy-Focused VPN
- More Ways To Avoid Surveillance From 5/9/14 Eyes Countries
- FAQs on the 5/9/14 Eyes Alliance
- Conclusion
The Eyes Alliances collect data from your internet traffic, phone calls, emails, and other forms of communication. The collected intelligence is shared among member countries, collectively called the 5/9/14 Eyes. This freaked me out too when I first heard about it.
Who are the 5 Eyes nations? Established in 1946, the Five Eyes network includes the US, the UK, Canada, Australia, and New Zealand, and recent polls show that at least 71% of Americans are worried about government surveillance (Pew Research, 2023)1. Altogether, the 5/9/14 Eyes countries pose major problems for everyone’s online freedom.
If you’re in one of these participating 14 countries, private conversations and images you share with friends or family are accessible to surveillance agencies. My mouth was literally hanging open when I learned that these agencies monitor global tech companies like Google, Microsoft, Facebook, and Apple, so your data is being collected even if you’re outside the Eyes Alliances. In this article, I'll reveal their spying tactics, and how you can protect yourself.
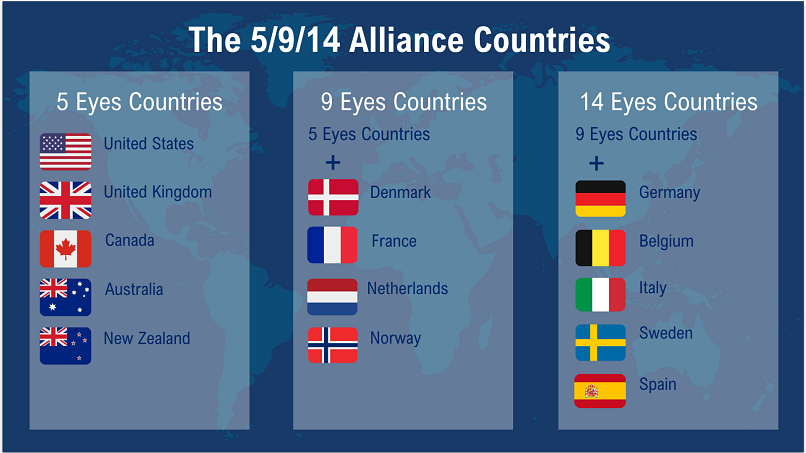
Short on Time? These Are the 5/9/14 Eyes Countries
- 5 Eyes Alliance — US, UK, Canada, Australia, and New Zealand
- 9 Eyes Alliance — US, UK, Canada, Australia, New Zealand, Denmark, France, Netherlands, and Norway
- 14 Eyes Alliance — US, UK, Canada, Australia, New Zealand, Denmark, France, Netherlands, Norway, Germany, Belgium, Italy, Sweden, and Spain
What Are the 5 Eyes, 9 Eyes, and 14 Eyes Alliances?
The 5, 9, and 14 Eyes Alliances are international intelligence-sharing networks that monitor digital communications. These countries have insights into your internet traffic, phone calls, and metadata, often bypassing domestic privacy laws by sharing intelligence.
Whistleblower Edward Snowden’s leaks in 2013 exposed the extent of these programs. They revealed mass monitoring of emails, browsing habits, and social media activity.
5 Eyes Alliance
Members: USA, UK, Canada, Australia, and New Zealand
Focus: Signals intelligence (SIGINT), mass electronic surveillance, and metadata collection
The Alliance was established to enhance collective security by sharing intelligence. However, they monitor not only potential threats but also regular people. Laws in these countries grant intelligence agencies extensive monitoring powers. Examples of national surveillance include:
- US. The PATRIOT Act allows the NSA to monitor phone calls, emails, and metadata without a warrant. Programs like PRISM collect user data from tech companies (Google, Apple, Microsoft, etc.). By 2014, the NSA collected over a billion communications annually (ACLU, 2023)2.
- UK. In the UK, your online activity is stored and accessible to government agencies for a year, as per the Investigatory Powers Act ("Snooper’s Charter"). Recent developments have seen the UK government ordering tech companies like Apple to provide access to encrypted data.
- Australia. The Data Retention Act forces ISPs to keep metadata for two years, which law enforcement can access without a warrant. This means that information such as the time, date, and recipients of emails and phone calls is stored and can be reviewed by authorities.
- Canada & New Zealand. Work closely with the NSA and GCHQ to collect and analyze communications data.
Do the 5 Eyes countries share immigration data? Investigations have revealed that up to 8 million immigration data checks are conducted among Alliance members annually (Biometric Update, 2024)3, with no restrictions on data retention. The data-sharing protocol covers the personal data of any traveler, visitor, or migrant, encompassing 35 items of information, including family members, medical history, and travel records.
In my experience, the governments start with non-citizens because they assume you won’t care if it’s only directed at them. This is ridiculous, and everyone knows they’ll eventually turn around and use those same surveillance tactics on citizens, too (if they aren’t already).
With the development of AI, the Alliance now has access to more personal data than ever. Due to the depth and personalization inherent in conversational exchanges, AI chat interactions can facilitate more detailed monitoring and profiling than traditional browser searches. I shudder to think what kind of horrors these governments will come up with using large language models.
9 Eyes Alliance
Focus: Expanded data-sharing agreements and broader surveillance programs
- France. The "Loi de Renseignement" allows authorities to monitor phone and internet activity without judicial oversight, especially after terror attacks. This means that everyday citizens can have their communications intercepted even if they have no criminal ties.
- Netherlands. The "Sleepwet" or "Dragnet Act" permits bulk data collection, sparking public opposition due to its invasive nature. While officials claim it enhances national security, critics argue that ordinary people’s private conversations, browsing habits, and metadata can be indiscriminately swept up and stored.
- Denmark & Norway. Intelligence agencies actively cooperate with NSA programs, sharing intercepted digital communications. This partnership means citizens' emails, messages, and calls may be accessible to foreign intelligence agencies.
14 Eyes Alliance
Members: 9 Eyes + Germany, Belgium, Italy, Sweden, and Spain
Focus: Further expansion of intelligence cooperation across Europe
- Germany. The Federal Intelligence Service (BND) collaborates extensively with the US, sharing vast amounts of intercepted data. This partnership reportedly involved the NSA intercepting approximately 500 million communications, including phone calls, emails, and text messages, within Germany during 2012 and 2013 (OSW, 2014)4.
- Spain. The "Gag Law" enables government agencies to surveil citizens and prosecute individuals for certain online activities.
- Sweden & Belgium. Maintain strict laws on domestic surveillance but share intelligence with 5 Eyes members.
Third-Party Contributors
Several countries contribute to the 5, 9, and 14 Eyes Alliances without being formal members. They aren’t typically subject to the same oversight and accountability mechanisms that apply to formal members of the Eyes Alliances. However, it's advisable to hide your IP address to stay safe online in these countries.
- Japan. A close US ally with extensive intelligence-sharing pacts. Which country is set to join as the sixth member of the 5 Eyes intelligence network? Japan has considered potentially becoming the "6th Eye". Its surveillance laws allow authorities to monitor online activity and social media under counterterrorism measures. I really hope this never happens as Japan is one of the most prosperous and populous countries that still hasn’t gotten involved in these shenanigans.
- Germany. A 14 Eyes member with additional intelligence agreements with the US. The BND was revealed to have worked with the NSA to monitor European leaders and corporations.
- Israel. Shares counterterrorism and cybersecurity intelligence, particularly in the Middle East. Mossad has been linked to advanced spyware, such as Pegasus, which has been used to monitor journalists and activists worldwide.
- South Korea. Collaborates on monitoring North Korea and cyber threats. Surveillance laws allow authorities to track the communications of individuals deemed national security risks.
- Singapore. Supports Indo-Pacific intelligence-sharing and cybersecurity efforts. It enforces strict internet regulations and monitors online activities under its national security framework.
- India. Strengthening intelligence ties with the 5 Eyes, especially in counterterrorism. Laws like the Information Technology Act allow broad government surveillance of digital communications.
What Impact Does the 5/9/14 Eyes Alliances Have on Citizens?
Without strict oversight, surveillance can be misused to suppress political dissent and activism. The FBI has been criticized for monitoring Black Lives Matter protesters, while China’s surveillance tools have been used to suppress journalists and activists. Intelligence-sharing Alliances like Five Eyes also enable countries to bypass domestic privacy laws. For instance, the UK’s GCHQ allegedly monitored US citizens on behalf of the NSA, avoiding direct legal restrictions.
The fear of constant surveillance affects individuals’ willingness to express their opinions freely. In authoritarian states, this has led to widespread suppression of speech, while even in democratic countries, privacy concerns have made people hesitant to engage in political discussions or online activism. This erosion of free expression threatens democratic principles and fundamental human rights.
Alliance members can also use jurisdictional loopholes to put citizens under surveillance. For example, I was stunned that the National Security Agency (NSA) was involved in the surveillance of German businesses and nationals, including Angela Merkel (their prime minister!).
The German intelligence agency, BND, supposedly forwarded data it intercepted on European and German targets to the NSA, effectively allowing the US agency to spy on German entities in ways it could not legally do itself. Another example is GCHQ asking the NSA to do it, effectively bypassing UK privacy laws.
What Type of Data Does the 5/9/14 Eyes Alliance Collect?
I initially thought that the Eyes Alliances focused mainly on intercepting conventional communications, such as phone calls and text messages. However, the 2013 Edward Snowden leaks revealed that the surveillance activities extended far beyond just calls and messages. Below are some of the significant data categories that the Alliances collect and share.
- Communications & metadata. They can collect the contents of emails, phone calls, and text messages, along with metadata such as sender and recipient details, time stamps, call duration, and location information. All this data can help map communication networks and intercept specific conversations.
- Internet activity. Your online data is used to analyze your behavior and determine if you may pose a potential security risk. This includes your browsing history, search queries, social media interactions, file transfers, and logs from internet service providers. Pro tip: Incognito windows are your best friends.
- Location & geospatial data. GPS data, cell tower locations, device movement logs, and IP-based geolocation can be used to track your movements and confirm if you’re present at a specific place and time. I know it’s hard, but sometimes you just gotta power off that phone.
- Financial & transactional data. Bank transfers, credit and debit card usage, or other financial transactions are collected by the Alliances to identify suspicious financial activities and link individuals to illicit behavior.
- Biometric & identity data. The Alliance nations also collect fingerprint records, facial recognition data, iris scans, and, where accessible, DNA samples to help identify individuals and verify suspect identities.
- Technical & Device Metadata. Information such as device identifiers (IMEI, MAC addresses) and hardware or software fingerprints is used to link devices to users and detect unusual activity.
- Selector Lists. The alliances use “selectors” or targets, such as specific email addresses, phone numbers, and IP addresses, to track particular individuals, organizations, or networks.
Surveillance Systems Used By These Alliances and the Data They Collect
Governments and intelligence agencies use advanced surveillance systems to monitor communications and online activities. While some programs were initially designed to address security threats, they can now gather information on ordinary individuals. Below is a simplified overview of some of the most well-known surveillance systems, what they do, and why they matter.
- ECHELON. A global surveillance system that uses satellites and ground antennas to intercept communications like phone calls, emails, and internet traffic. It was first set up during the Cold War to keep an eye on the Soviet Union, but now it collects data from all over the world. Governments use it to search for specific keywords in the massive amounts of data it gathers.
- PRISM. Run by the US National Security Agency (NSA), PRISM collects internet data like emails, chats, photos, and more from big tech companies such as Google, Facebook, and Microsoft. While it’s mainly focused on people outside the US, it can also pick up information on Americans.
- XKeyscore. This powerful NSA tool can track almost everything you do online, from emails and browsing history to social media activity and even where you are. It became widely known in 2013 when Snowden revealed its existence.
- Tempora. Operated by the UK’s GCHQ, Tempora taps into undersea internet cables to intercept and store vast amounts of online communications, like emails, phone calls, and browsing history. The data is kept for up to 30 days and shared with other countries in the Five Eyes Alliance.
- MUSCULAR. A joint effort between the NSA and GCHQ, MUSCULAR secretly captures data as it moves between the internal networks of tech companies like Google and Yahoo. It grabs millions of records daily, including emails and search queries, often without the companies or users knowing.
- Stone Ghost (DNIE). This is a NATO-led system used to share defense-related intelligence, like intercepted communications, satellite images, and reports from field agents. It’s mainly focused on security and military operations.
What Are the Best Ways to Safeguard Your Privacy in 5 Eyes Regions?
Use a VPN (Virtual Private Network)
A VPN can mask your IP address by assigning a new one, making it more difficult to put your online data under surveillance. It also uses encryption to prevent hackers, government agencies, and even your internet service provider (ISP) from tracking your online activities. Some VPNs also offer advanced features like obfuscation to bypass VPN-detection surveillance firewalls. I know I’m biased based on the site I write for, but I think they’re pretty great.
Use Tools With End-to-End Encryption
Tools like VeraCrypt can encrypt your full-disk data, making it almost impossible to track any of your online data. ProtonMail offers an end-to-end encrypted email service, while other examples are Telegram or Signal, which encrypt your online data. You can also combine these tools with HTTPS Everywhere so that you are always using HTTPS connections for additional online privacy.
Consider Tor (With Bridges)
The Tor network can help protect anonymity by routing your traffic through multiple relays. You can further enhance your online security by using Tor bridges that are basically unlisted entry points to the Tor network. Bridges make it harder for ISPs or governments to know if you’re using Tor, since using it may even constitute grounds for putting you under surveillance in some countries.
Practice Good OPSEC
OPSEC, or operational security, is the first layer of privacy against any kind of surveillance. For example, using strong passwords and two-factor authentication (2FA) can protect your accounts from unauthorized access. I know it can be a bit annoying, but it’s worth a couple extra minutes to fully protect your devices. In addition, always keep your operating system and apps up-to-date to protect against any system-related vulnerabilities.
Should You Avoid VPNs That Are Located in the 5/9/14 Eyes or Using Servers in These Countries?
For most everyday internet users that want to stream, game or torrent securely, jurisdiction doesn’t matter. The only thing you need to make sure is that your VPN has safe real-world practices like adherence to independently audited no-logs policies and RAM-only servers (wipes your data with every reboot). Even if a VPN collects minimal data it should be anonymized meaning that it can’t be traced back to you.
Jurisdiction matters more for high-risk users like journalists or activists. If you fall into this group, you'll want a VPN that's headquartered in a privacy-friendly country and follows a proven no-logs policy. You might also want to use other secure platforms like Tor for greater online privacy.
Quick Checklist for Choosing A Privacy-Focused VPN
If you live in a 5/9/14 Eyes country, the following can help you identify the ideal VPN for safeguarding your online privacy. My checklist outlines a few non-negotiables and will help you identify potential red flags before making a decision.
- Audit stamp. Regular audits prove a VPN actually follows its no-logging policies. I feel more comfortable when third parties have come in to verify their claims. Ideally, the audits should not be more than 18 months old and must list the auditor, along with the report, on the VPN’s website. I’m shocked at the number of VPNs I’ve reviewed that claim to go through audits but never offer public reports (sure).
- Logging specifics. Only choose a VPN that clearly states it keeps “no activity logs” and “no connection timestamps or IPs” in its privacy policy. Anything less is a deal-breaker when it comes to your privacy.
- Security features. A solid VPN should have RAM-only servers, a kill switch, leak protection, and private DNS servers to support the no-logs policy. I think of it this way: the policy is their promise not to interfere with your data, and these security features ensure that no one else can either.
- Transparency. Prioritize VPNs that feature a warrant canary (which signals if secret government requests are being made) and a transparency report (which shows how many data requests the VPN receives and rejects). Additionally, VPNs with bug bounties or security post-mortem programs demonstrate an impressive level of transparency.
- Clients & supply chain. Look for options with open-source apps, no shady trackers, and minimal crash reports by default. If an app is full of SDKs (software kits from third parties that can collect data) and analytics I can’t turn off, I don’t trust it.
- Jurisdiction. The location of their headquarters matters, but I treat it as a tiebreaker. A transparent provider with strong practices beats one hiding behind a “safe” jurisdiction but with vague policies.
Red Flags (Avoid These VPNs)
- Data logging. If a VPN claims to follow a no-logs policy but still collects unanonymized connection timestamps or IP addresses, then it's a clear sign that they may be tracking you.
- Lack of transparency. Any audit with only a vague summary of what the VPN was tested for, without mentioning the details of the testing methods, is also a big red flag. I look for gaps in the scope of the audit report, such as the mention of only one server or the DNS network not being audited, to help choose the most secure option.
- Insecure apps. If the VPN apps are packed with SDKs or excessive telemetry (usage and diagnostic data sent back to the provider), that’s also a red flag.
- Contradictions. Substandard services will almost always have contradictions between their marketing and privacy policies. They never mention past incidents on what went wrong and what steps they are taking to prevent this.
Best VPNs With Audited No-Logs Policies Outside the 5 Eyes
- ExpressVPN — This VPN is headquartered in the British Virgin Islands and offers a strict no-logging policy that has passed multiple independent audits. All its servers also run on RAM-only and automatically conceal your VPN traffic (obfuscation).
- CyberGhost — A beginner-friendly VPN that's located in Romania and makes it easy to protect your data against third-party access. Upgrade to No-Spy servers that are independently operated.
- NordVPN — Advanced security features, such as obfuscated servers, double encryption, and Onion over VPN, that make it harder for government agencies to get hold of your sensitive data.
More Ways To Avoid Surveillance From 5/9/14 Eyes Countries
- Avoid cloud services from countries on the 5/9/14 list. Options like Google Drive, OneDrive, or Dropbox are subject to US jurisdiction and may be compelled to share data with government agencies. I avoid this by accessing Switzerland-based services like Tresorit or pCloud instead.
- Use privacy-focused operating systems. These systems minimize data collection and tracking by default. For desktops, consider Tails, Qubes OS, or privacy-focused Linux distributions. For mobile, use GrapheneOS (Android) or iOS with careful configuration.
- Be wary of metadata. Even encrypted communications can reveal metadata, such as who you communicate with, when, and how often. You can minimize metadata by using burner devices and accounts, avoiding linking accounts together, and utilizing anonymous payment methods, such as cryptocurrency.
- Conduct personal privacy audits. Regularly check for IP/DNS/WebRTC leaks to confirm your VPN or other services are working correctly. Review app permissions on your devices and revoke unnecessary ones. I’ve made this a habit. It’s easy to do while you’re waiting for a bus or lying in bed, and it could make a big difference.
- Don’t overshare. Avoid sharing personal or identifiable information online. Disable tracking services, such as browsing activity and location logging, where possible.
- Stay educated. Privacy and security are constantly evolving. Stay informed about the latest threats and best practices to keep your digital footprint secure.
FAQs on the 5/9/14 Eyes Alliance
Conclusion
Why is it called Five Eyes? The original Alliance included 5 English-speaking countries (the US, the UK, Canada, Australia, and New Zealand) before expanding to 9 and then 14 nations. These countries form international surveillance networks that monitor and share personal data, including internet traffic, phone calls, and emails.
To protect my privacy, I make it a habit to use a VPN, disable location tracking, and carefully manage app permissions. Unfortunately, we live in an environment where surveillance programs like PRISM and ECHELON are collecting larger and larger amounts of data for intelligence agencies. As AI continues to grow stronger every day, governments are becoming increasingly adept at spying on us. Therefore, I suggest you take steps to improve your own protection.
References
- https://www.pewresearch.org/internet/2023/10/18/views-of-data-privacy-risks-personal-data-and-digital-privacy-laws/
- https://www.aclu.org/news/national-security/five-things-to-know-about-nsa-mass-surveillance-and-the-coming-fight-in-congress
- https://www.biometricupdate.com/202406/five-eyes-biometric-data-sharing-increases-by-over-100x-with-little-transparency
- https://www.osw.waw.pl/en/publikacje/osw-commentary/2014-01-14/nsa-impact-wiretapping-scandal-german-american-relation
Your online activity may be visible to the sites you visit
Your IP Address:
216.73.216.23
Your Location:
US, Ohio, Columbus
Your Internet Provider:
Some sites might use these details for advertising, analytics, or tracking your online preferences.
To protect your data from the websites you visit, one of the most effective steps is to hide your IP address, which can reveal your location, identity, and browsing habits. Using a virtual private network (VPN) masks your real IP by routing your internet traffic through a secure server, making it appear as though you're browsing from a different location. A VPN also encrypts your connection, keeping your data safe from surveillance and unauthorized access.




Please, comment on how to improve this article. Your feedback matters!