Array Networks – Agility and Performance
- Let’s start with a little bit about yourself and your background.
- Please tell me about your different products. It seems to basically be a combination of CDN (Content Delivery Network) and firewall software.
- Unlike most companies in this space, you seem to fundamentally provide a hardware solution with associated software. Is that correct?
- How do you define your market? Who is your specific target audience within that market?
- How do you see cloud and mobile technologies affecting security products such as yours?
- What methods do you normally use to attract and engage with new customers?
- How many active customers do you have today? Where are they mainly located?
- Who are some of your biggest customers?
- Why is there no pricing information on your web site?
- How do you see your tools as different and/or better than those of your competitors?
- What are your future plans for your various products?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
Array Networks is a global leader in application delivery networking and security solutions. They offer enterprises the choice of either hardware solutions or functionally equivalent software solutions for deployment in their in-house data centers or in public clouds (i.e. Amazon Web Services or Microsoft Azure).
In my discussion with Array Networks’ Paul Andersen, we discussed the history of remote access VPN products, how cloud and mobile computing is changing the application security landscape, and how the recent platform product announced by Array Networks attempts to let their customers “have their cake and eat it too.”
Let’s start with a little bit about yourself and your background.
I have been in the networking and security space for about 20 years, working at both startups and large companies. After spending about 2 ½ years at Cisco, I am back at Array Networks for the second time. For the past five years here, I have been responsible for all aspects of the company’s marketing and communications efforts.
Please tell me about your different products. It seems to basically be a combination of CDN (Content Delivery Network) and firewall software.
That description is pretty close, but not 100% accurate. Our core product is ADCs – Application Delivery Controllers. These controllers, which evolved from classical load balancers, provide both performance enhancement and security. We were the first company to introduce this type of product.
We also introduced an enterprise-grade SSL VPN (Secure Socket Layer Virtual Private Network). At the time (2005), most SSL VPN products that were available didn’t need to be very “heavy duty” and were not very robust or scalable. Our VPN product is very scalable and fits well into corporate enterprise and mobility strategies.
Unlike most companies in this space, you seem to fundamentally provide a hardware solution with associated software. Is that correct?
It is true that our origins are with hardware solutions, but that has changed over the past five years, with the growing popularity of virtualization and public clouds. Customers now want the features that we provide in hardware to be available in software (only) solutions. We now offer all of our hardware functionality in software as well. You can even go to the AWS (Amazon Web Services) or Microsoft Azure store and buy our software products on a utility/consumption [pay as you go] basis.
In terms of revenues, hardware sales still dominate and are still 70-80% of our revenues. However, software components are the fastest growing part of our business, both via direct sales and via the public clouds.
How do you define your market? Who is your specific target audience within that market?
We have traditionally focused on the enterprise market, such as financial services, healthcare, and eCommerce. Our best fit seems to be with medium sized enterprises. Our products are generally too fast, functional, and expensive for small and medium sized businesses.
Our products are designed to be cost effective and very simple to manage. This makes it a better fit for organizations that don’t have a large IT staff and/or budget.
How do you see cloud and mobile technologies affecting security products such as yours?
When we first introduced our VPN product, there were only a small number of people using a network-layer VPN to work from home. These users were getting remote access to the corporate network and their home computers or laptops were actually connected to the network with their own IP address.
Since then, things have evolved in several ways:
- With the introduction of smart phones, tablets and other mobile devices, we need to provide VPN clients for all of those devices and to be able to lock down (secure) those devices.
- With the old VPN access method, only the tunnel of the VPN was secured, but once inside the tunnel, malicious software could then launch attacks on the network from that point.
- Today, companies rely more on providing access to web-based apps. This means that the remote user is using resources in the company’s headquarters, but does not have a direct connection to the corporate network, which is a much more secure access model.
- In addition to the use of VPNs to provide remote access for users, we are seeing a lot of companies moving to cloud data centers, meaning that they are moving their infrastructure and applications into the cloud. This creates a situation where both system administrators and users need access from anywhere. As a result, our VPN products are now being installed in many cloud data centers. This has created a new customer category for us – hosting companies.
What methods do you normally use to attract and engage with new customers?
We use a mix of everything…
- Media Outreach - Public relations, analyst relationships, etc.
- Web Presence – SEO, AdWords campaigns, and retargeting campaigns.
- Industry Events – Both small and large.
- Webinar Series – Minimum two per month, focusing on verticals, case studies, and/or explaining new technologies.

How many active customers do you have today? Where are they mainly located?
We are a truly global company, with customers all around the world. We enter a new market every 2-3 years. About a year ago, the last time we did an extensive study of our customer base, we had over 5,000 active customers under support contracts.
Sales of ADC and VPN products make up 90% of our customers. The breakdown is pretty interesting in that 1/3 of our customers purchase ADCs, 1/3 purchase VPNs, and 1/3 purchase both. In terms of revenues, the breakdown is approximately 65% ADC and 35% VPN.
Who are some of your biggest customers?
Some of the big names that you might recognize include:
- Oracle
- Amdocs
- State Bank of India
- Humana
- Binghamton University
- Software (IBM cloud)
Why is there no pricing information on your web site?
If we were in the SMB (Small and Medium Business) space, with all of our products priced under $10,000 and available for purchase online, there would be pricing on our web site. In our current markets, pricing, marketing, and distribution are all very different, making a standard online price list infeasible.
How do you see your tools as different and/or better than those of your competitors?
Our products and solutions offer rich enterprise class features and capabilities.
In addition, our products are:
- Very cost effective
- Simple to deploy
- Very scalable
What are your future plans for your various products?
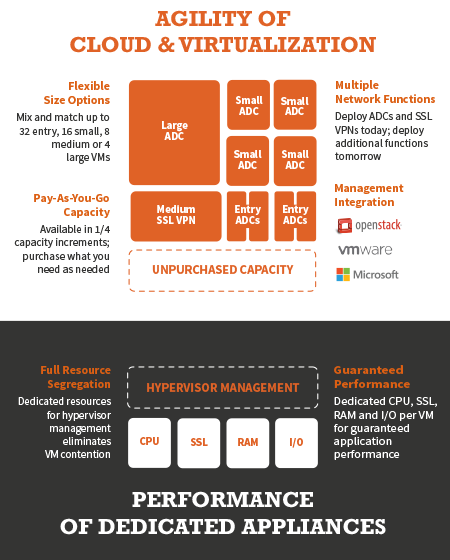
What we discovered in talking to our customers is that there are significant tradeoffs between hardware and software solutions.
Hardware – Tremendous performance and scalability, but not very agile.
Software – Offering exceptional flexibility and agility, our solution can be effortlessly deployed wherever and whenever it is needed. However, it operates on general-purpose computers, utilizing shared system resources, which significantly impacts its performance.
Of course, customers want both – agility and performance!
We have just released a brand new product – the AVX Network Functions Platform – that provides our customers with exactly that. This is a custom-built environment designed to host virtualized networking and security functions. It is an open platform that provides the best of both worlds – the agility of cloud and virtualization with the performance of dedicated appliances.
How many employees do you have today? Where are they located?
We currently have over 250 employees worldwide, as follows:
| North America | 100+ |
| China | 30-40 |
| India | 30-40 |
| Japan | 30-40 |
| Europe | < 10 |
How many hours a day do you normally work? What do you like to do when you are not working?
I normally work 50-60 hours each week. When I am not working, you can usually find me riding my Ducati motor bike.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.


Please, comment on how to improve this article. Your feedback matters!