What Are the 5/9/14 Eyes Countries? Surveillance in 2025
- Important: Use a VPN With Headquarters Outside the 5/9/14 Eyes Alliances
- What Are the 5 Eyes, 9 Eyes, and 14 Eyes Alliances?
- What Impact Does the 5/9/14 Eyes Alliances Have on Citizens?
- Surveillance Systems Used By These Alliances and the Data They Collect
- How To Avoid Surveillance from 5/9/14 Eyes Countries
- FAQs on the 5/9/14 Eyes Alliance
- Conclusion
The Eyes Alliances collect data from your internet traffic, phone calls, emails, and other forms of communication. The collected intelligence is shared among member countries, collectively called the 5/9/14 Eyes.
Who are the 5 Eyes nations? Established in 1946, the Five Eyes network includes the US, the UK, Canada, Australia, and New Zealand. (Wikipedia, 2025)1. These countries monitor global internet traffic with their partners in the 9 and 14 Eyes, making online surveillance nearly unavoidable.
If you’re in one of these participating 14 countries, private conversations and images you share with friends or family are accessible to surveillance agencies. These agencies also monitor global tech companies like Google, Microsoft, Facebook, and Apple, so your data is being collected even if you’re outside the Eyes Alliances.
Important: Use a VPN With Headquarters Outside the 5/9/14 Eyes Alliances
Certain jurisdictions have laws allowing government agencies to secretly demand access to user information without public disclosure. While you can hide your online activity with a VPN, it’s important to choose a reliable provider that can’t be forced to share information under legal pressure.
What’s the best VPN based outside of the 14 Eyes Alliance? ExpressVPN is one of the best options to protect your online privacy, with over 18 independent audits that confirm its no-logs claims (ExpressVPN, 2024)2. It’s based in the British Virgin Islands and uses RAM-only servers, so your data gets deleted on every server reboot. VPNs based in Switzerland, Panama, and Romania are also good options with strict privacy laws that don’t require VPNs to store logs.
Editor's Note: Transparency is one of our core values at vpnMentor, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process.
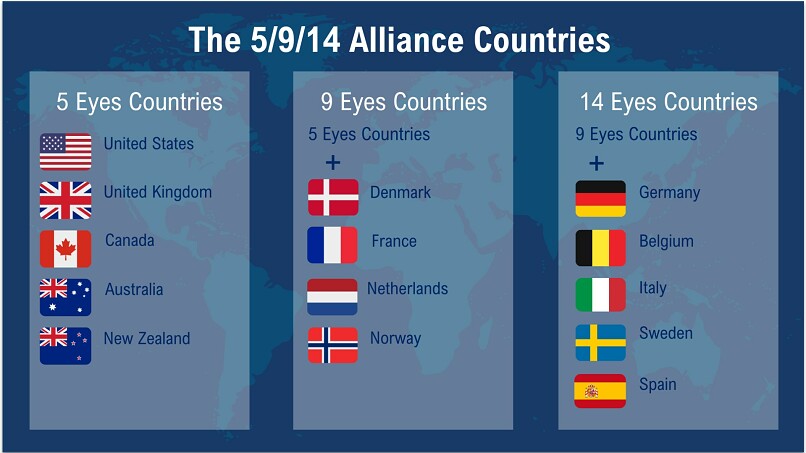
What Are the 5 Eyes, 9 Eyes, and 14 Eyes Alliances?
The 5, 9, and 14 Eyes Alliances are international intelligence-sharing networks that monitor digital communications. These countries have insights into your internet traffic, phone calls, and metadata, often bypassing domestic privacy laws by sharing intelligence.
Whistleblower Edward Snowden’s leaks in 2013 exposed the extent of these programs (The Guardian, 2013)3. They revealed mass monitoring of emails, browsing habits, and social media activity.
5 Eyes Alliance
Members: USA, UK, Canada, Australia, and New Zealand
Focus: Signals intelligence (SIGINT), mass electronic surveillance, and metadata collection
The Alliance was established to enhance collective security by sharing intelligence. However, they monitor not only potential threats but also regular people. Laws in these countries grant intelligence agencies extensive monitoring powers. Examples of national surveillance include:
- US. The PATRIOT Act allows the NSA to monitor phone calls, emails, and metadata without a warrant. Programs like PRISM collect user data from tech companies (Google, Apple, Microsoft, etc.). According to the ACLU4, by 2014, the NSA collected over a billion communications annually.
- UK. In the UK, your online activity is stored and accessible to government agencies for a year, as per the Investigatory Powers Act ("Snooper’s Charter"). Recent developments have seen the UK government ordering tech companies like Apple to provide access to encrypted data.
- Australia. The Data Retention Act forces ISPs to keep metadata for two years, which law enforcement can access without a warrant. This means that information such as the time, date, and recipients of emails and phone calls are stored and can be reviewed by authorities.
- Canada & New Zealand. Work closely with the NSA and GCHQ to collect and analyze communications data.
Do the 5 Eyes countries share immigration data? Investigations have revealed that up to 8 million checks for immigration data occur among Alliance members each year (Biometric Update, 2024)5, with no restrictions on data retention. The data-sharing protocol covers the personal data of any traveler, visitor, or migrant, encompassing 35 items of information, including family members, medical history, and travel records.
With the development of AI, the Alliance now has access to more personal data than ever. Due to the depth and personalization inherent in conversational exchanges, AI chat interactions can facilitate more detailed monitoring and profiling than traditional browser searches.
9 Eyes Alliance
Members: 5 Eyes + Denmark, France, Netherlands, and Norway
Focus: Expanded data-sharing agreements and broader surveillance programs
- France. The "Loi de Renseignement" allows authorities to monitor phone and internet activity without judicial oversight, especially after terror attacks. This means everyday citizens can have their communications intercepted even if they have no criminal ties.
- Netherlands. The "Sleepwet" or "Dragnet Act" permits bulk data collection, sparking public opposition due to its invasive nature. While officials claim it enhances national security, critics argue that ordinary people’s private conversations, browsing habits, and metadata can be indiscriminately swept up and stored.
- Denmark & Norway. Intelligence agencies actively cooperate with NSA programs, sharing intercepted digital communications. This partnership means citizens' emails, messages, and calls may be accessible to foreign intelligence agencies.
14 Eyes Alliance
Members: 9 Eyes + Germany, Belgium, Italy, Sweden, and Spain
Focus: Further expansion of intelligence cooperation across Europe
- Germany. The Federal Intelligence Service (BND) collaborates extensively with the US, sharing vast amounts of intercepted data. This partnership reportedly involved the NSA intercepting approximately 500 million communications, including phone calls, emails, and text messages, within Germany during 2012 and 2013 (OSW, 2014)6.
- Spain. The "Gag Law" enables government agencies to surveil citizens and prosecute individuals for certain online activities.
- Sweden & Belgium. Maintain strict laws on domestic surveillance but share intelligence with 5 Eyes members.
Third-Party Contributors
Several countries contribute to the 5, 9, and 14 Eyes Alliances without being formal members. They aren’t typically subject to the same oversight and accountability mechanisms that apply to formal members of the Eyes Alliances. However, it's advisable to hide your IP address to stay safe online in these countries.
- Japan. A close US ally with extensive intelligence sharing and has considered potentially becoming the "6th Eye"(The Japan Times, 2024)7. Japan’s surveillance laws allow authorities to monitor online activity and social media under counterterrorism measures.
- Germany. A 14 Eyes member with additional intelligence agreements with the US. The BND was revealed to have worked with the NSA to monitor European leaders and corporations.
- Israel. Shares counterterrorism and cybersecurity intelligence, particularly in the Middle East. Mossad has been linked to advanced spyware, such as Pegasus, which has been used to monitor journalists and activists worldwide.
- South Korea. Collaborates on monitoring North Korea and cyber threats. Surveillance laws allow authorities to track the communications of individuals deemed national security risks.
- Singapore. Supports Indo-Pacific intelligence-sharing and cybersecurity efforts. It enforces strict internet regulations and monitors online activities under its national security framework.
- India. Strengthening intelligence ties with the 5 Eyes, especially in counterterrorism. Laws like the Information Technology Act allow broad government surveillance of digital communications.
What Impact Does the 5/9/14 Eyes Alliances Have on Citizens?
Without strict oversight, surveillance can be misused to suppress political dissent and activism. The FBI has been criticized for monitoring Black Lives Matter protesters, while China’s surveillance tools have been used to suppress journalists and activists. Intelligence-sharing Alliances like Five Eyes also enable countries to bypass domestic privacy laws. For instance, the UK’s GCHQ allegedly monitored US citizens on behalf of the NSA, avoiding direct legal restrictions.
The fear of constant surveillance affects individuals’ willingness to express their opinions freely. In authoritarian states, this has led to widespread suppression of speech, while even in democratic countries, privacy concerns have made people hesitant to engage in political discussions or online activism. This erosion of free expression threatens democratic principles and fundamental human rights.
Surveillance Systems Used By These Alliances and the Data They Collect
Governments and intelligence agencies use advanced surveillance systems to monitor communications and online activities. While some programs were initially designed to address security threats, they can now gather information on ordinary individuals. Below is a simplified overview of some of the most well-known surveillance systems, what they do, and why they matter.
- ECHELON. A global surveillance system that uses satellites and ground antennas to intercept communications like phone calls, emails, and internet traffic. It was first set up during the Cold War to keep an eye on the Soviet Union, but now it collects data from all over the world. Governments use it to search for specific keywords in the massive amounts of data it gathers.
- PRISM. Run by the US National Security Agency (NSA), PRISM collects internet data like emails, chats, photos, and more from big tech companies such as Google, Facebook, and Microsoft. While it’s mainly focused on people outside the US, it can also pick up information on Americans.
- XKeyscore. This powerful NSA tool can track almost everything you do online, from emails and browsing history to social media activity and even where you are. It became widely known in 2013 when Snowden revealed its existence.
- Tempora. Operated by the UK’s GCHQ, Tempora taps into undersea internet cables to intercept and store vast amounts of online communications, like emails, phone calls, and browsing history. The data is kept for up to 30 days and shared with other countries in the Five Eyes Alliance.
- MUSCULAR. A joint effort between the NSA and GCHQ, MUSCULAR secretly captures data as it moves between the internal networks of tech companies like Google and Yahoo. It grabs millions of records daily, including emails and search queries, often without the companies or users knowing.
- Stone Ghost (DNIE). This is a NATO-led system used to share defense-related intelligence, like intercepted communications, satellite images, and reports from field agents. It’s mainly focused on security and military operations.
How To Avoid Surveillance from 5/9/14 Eyes Countries
- Use a VPN. A VPN encrypts your internet traffic and hides your IP address, preventing ISPs, hackers, and government agencies from tracking your online activities. Look for features like obfuscation to bypass VPN detection.
- Secure browsers and search engines. Use privacy-focused browsers like Brave, Tor Browser, or Mozilla Firefox with extensions like uBlock Origin and HTTPS Everywhere. Secure browsers and search engines prevent tracking and minimize data collection.
- Secure and encrypted communication tools. End-to-end encryption allows only you and the recipient to access your communications, preventing interception by third parties.
- Practice good OpSec (Operational Security). Strong passwords and two-factor authentication (2FA) protect your accounts from unauthorized access. Keep your operating system and apps up-to-date to protect against vulnerabilities.
- Encrypt your data. Use full-disk encryption tools like VeraCrypt for data at rest, and always use HTTPS websites for data in transit. Tools like HTTPS Everywhere can enforce HTTPS connections.
- Avoid cloud services from 5/9/14 Eyes countries. Options like Google Drive, OneDrive, or Dropbox are subject to US jurisdiction and may be compelled to share data with government agencies. Use Switzerland-based services like Tresorit or pCloud instead.
- Use privacy-focused operating systems. These systems minimize data collection and tracking by default. For desktops, consider Tails, Qubes OS, or privacy-focused Linux distributions. For mobile, use GrapheneOS (Android) or iOS with careful configuration.
- Be wary of metadata. Even encrypted communications can reveal metadata, such as who you communicate with, when, and how often. You can minimize metadata by using burner devices and accounts, avoiding linking accounts together and using anonymous payment methods like cryptocurrency.
- Conduct regular privacy audits. Regularly check for IP/DNS/WebRTC leaks to confirm your VPN or other services are working properly. Review app permissions on your devices and revoke unnecessary ones. This helps identify and fix vulnerabilities that could expose your data.
- Don’t overshare. Avoid sharing personal or identifiable information online. Disable tracking services like browsing activity and location logging where possible.
- Stay educated. Privacy and security are constantly evolving. Stay informed about the latest threats and best practices to keep your digital footprint secure.
Best VPNs Outside the 5/9/14 Eyes Jurisdiction in 2025
- ExpressVPN — The best privacy VPN with RAM-only servers and a strict no-logs policy that has passed multiple independent audits.
- CyberGhost — A low-cost VPN with an intuitive interface that makes it easy to protect your data against third-party access.
- NordVPN — Advanced security features that make it harder for government agencies to get hold of your sensitive data.
Editor's Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: Intego, CyberGhost, ExpressVPN, and Private Internet Access. However, this does not affect our review process, as we adhere to a strict testing methodology.
FAQs on the 5/9/14 Eyes Alliance
Are the 5/9/14 Eyes Alliances the only international surveillance networks?
No, they're not the only ones, just the most well-known international surveillance networks. Several other intelligence-sharing agreements between nations may affect you to varying degrees. For example, other lesser-known surveillance networks and bilateral agreements between countries facilitate international data sharing for security and intelligence purposes.
Can the government tell you're using a VPN?
Yes, governments can detect VPN usage via Deep Packet Inspection (DPI), VPN IP blacklists, and traffic analysis, but decrypting VPN traffic is far more complex. However, some VPNs use obfuscation techniques to disguise VPN traffic as a regular internet connection and prevent detection.
AES-256 encryption, used by most VPNs, would take classical computers billions of years to crack. In theory, quantum computers could break RSA-2048 in hours, but practical large-scale quantum decryption is still years away. However, to protect against future quantum threats, ExpressVPN’s Lightway Turbo protocol integrates Kyber-768, a post-quantum algorithm selected by NIST.
Is Stone Ghost related to the Five Eyes Alliance?
Stone Ghost is not directly related to the Five Eyes Alliance. It is a separate intelligence network used primarily by NATO and partner nations to share sensitive information. While it involves countries that are also part of the Five Eyes, such as the United States, its scope and operations are distinct from those of the Five Eyes.
Can you completely avoid the 5/9/14 Eyes surveillance?
You can’t avoid 5/9/14 Eyes surveillance if you live in or communicate with individuals in these countries. However, you can mitigate exposure by using privacy-focused services and tools, such as VPNs based outside of 5/9/14 Eyes jurisdictions, encrypted communication apps, and privacy-focused browsers. While these measures enhance privacy, they do not provide absolute protection against sophisticated surveillance efforts.
Which countries are not part of any surveillance Alliance?
Many countries are not formally part of these specific Alliances. However, even countries not part of formal Alliances may still engage in intelligence-sharing agreements or cooperate on particular issues.
- Neutral or non-aligned countries. Countries like Switzerland, Austria, and Ireland have historically maintained neutrality and are not part of significant surveillance Alliances.
- Developing nations. Many countries in Africa, Southeast Asia, and Latin America are not part of these Alliances due to limited intelligence infrastructure or geopolitical alignment.
- Isolated or authoritarian regimes. Countries like North Korea and Turkmenistan operate in relative isolation and are not part of such Alliances.
- Countries with independent policies. Nations like Brazil, India, and South Africa have independent foreign policies and are not formally part of these Alliances, though they may share bilateral intelligence.
Are there any safe email providers outside the 5/9/14 Eyes Alliances?
Yes, there are several email providers outside the 5/9/14 Eyes Alliances that prioritize privacy and security. Open-source providers are often more transparent about their security practices. Always use end-to-end encryption to prevent third parties from reading your emails. While no email provider can guarantee 100% security, these options are among the safest:
- ProtonMail (Switzerland): Safe due to end-to-end encryption, zero-access encryption, and Switzerland's strong privacy laws outside the 5/9/14 Eyes Alliances.
- Mailfence (Belgium): Offers end-to-end encryption and is based in Belgium, which has robust privacy laws and is not part of the 5/9/14 Eyes.
- Runbox (Norway): Prioritizes privacy with encrypted storage and is based in Norway, which is outside the 5/9/14 Eyes Alliances.
- CTemplar (Iceland): Provides end-to-end encryption and is based in Iceland, known for strong privacy laws and independence from the 5/9/14 Eyes.
Do the Five Eyes countries share immigration data?
Yes, the Five Eyes countries may exchange certain immigration-related information. While some surveillance systems and data-sharing practices of Alliances like the Five Eyes are well-documented and publicly acknowledged, the full extent of their data-collection practices remains unclear. However, these countries collaborate on matters related to border security, counter-terrorism, and transnational crime, which may involve exchanging biometric data, travel history, and other relevant information.
Conclusion
Why is it called Five Eyes? The original Alliance included 5 English-speaking countries (US, UK, Canada, Australia, and New Zealand) before expanding to 9 and then 14 nations. These countries form international surveillance networks that monitor and share personal data, including internet traffic, phone calls, and emails8 (Reuters, 2025).
To avoid monitoring by these Alliances, adopt privacy-focused tools and practices, such as using a VPN, disabling location tracking, and carefully managing app permissions. These steps are crucial in an environment where surveillance programs like PRISM and ECHELON collect vast amounts of personal data accessible to intelligence agencies.
References
- https://en.wikipedia.org/wiki/Five_Eyes/
- https://www.expressvpn.com/blog/kpmg-privacy-policy-audit/
- https://www.theguardian.com/world/2013/jun/06/us-tech-giants-nsa-data/
- https://www.aclu.org/news/national-security/five-things-to-know-about-nsa-mass-surveillance-and-the-coming-fight-in-congress/
- https://www.biometricupdate.com/202406/five-eyes-biometric-data-sharing-increases-by-over-100x-with-little-transparency/
- https://www.osw.waw.pl/en/publikacje/osw-commentary/2014-01-14/nsa-impact-wiretapping-scandal-german-american-relations/
- https://www.japantimes.co.jp/commentary/2024/11/30/japan/japan-six-eyes/
- https://www.reuters.com/world/what-is-five-eyes-intelligence-sharing-Alliance-2025-03-06/
Your online activity may be visible to the sites you visit
Your IP Address:
216.73.216.148
Your Location:
US, Ohio, Columbus
Your Internet Provider:
Some sites might use these details for advertising, analytics, or tracking your online preferences.
To protect your data from the websites you visit, one of the most effective steps is to hide your IP address, which can reveal your location, identity, and browsing habits. Using a virtual private network (VPN) masks your real IP by routing your internet traffic through a secure server, making it appear as though you're browsing from a different location. A VPN also encrypts your connection, keeping your data safe from surveillance and unauthorized access.




Please, comment on how to improve this article. Your feedback matters!