How to Create a Strong Password - 7 Golden Rules
- Having different passwords for different services is a must - Updating passwords frequently is a must - Using a (silly) phrase is a suggested as a way to create passwords. - Consider using two-step verification Share
05Looks like a load of mumbo jumbo?
We’ll explain why creating a riddle of a password can protect you from all sorts of online predators.
Before I began to investigate this subject more rigorously, I was quite baffled as to why anyone would want to hack into my online world. After all, I’m rather uninteresting; certainly not working as an undercover agent; in fact, I’m not even material for a stalker.
Truth be told, it doesn’t matter who I am. For whatever reason, there are people out there who pry on and exploit other people’s information.
After researching the subject extensively and chatting with various sources, I realized that I am as much a target as anyone else. Part of the issue with the online world is that we – as users – simply don’t realize the potential of what we input into that screen. As the internet becomes more advanced, so do professionals who very much know how to crack, hack and prowl around our business.
Hackers come in all shapes and colored hats, to be precise. There are 3 types of hackers and specific motivations for each:
1. First are the white hat hackers – the good guys who protect us from the black hat hackers who get paid to create computer viruses or hack into systems. Other hackers include green hat hackers, grey hat hackers, spy hackers, cyber terrorists.
2. Hackers aside, there’s also the government to consider when it comes to your security. The NSA, among other governments worldwide, are eager to plant legislation that gives them access to every individual’s emails, phone calls, web page visited. That’s certainly an enormous breach of rights. After all, why would the NSA want to know about my Facebook photos. I’m still not sure.
3. Finally, there are advertisers. While you might not be doing anything spy worthy or terribly criminal when online, you might just be the target for some seriously annoying adverts plastered on your web browser.
So whether you’re the subject of advertising, or caught up in a hacking conspiracy, the best advice out there is to change your passwords regularly.
After sifting through mind fields of information about this and chatting with experts, we concocted the 7 golden rules to protect you from all the web savages out there.
1. Create different passwords for different services:
Imagine if the same key opened your car door, your home, your office. The logic is rather obvious. If a hacker manages to get in one place, he or she can get in to another, and another. It’s essential to have a different key for a different lock.
2. Change your passwords regularly:
The same logic applies. Keeping the same lock on your door for years and years is really an invitation for a thief. At some point, the lock is tampered; the code is cracked. Change your passwords regularly. Some applications have settings to remind you to change your passwords frequently. For example, if you are using Windows, you can opt to change your Windows login password frequently by using the password options in Local Security Policy. Simply select Password Policy under Account Policies. Double-click Maximum password age in the right pane, enter the number of days you want to go between passwords, and click OK. Now that’s a clever little reminder.
3. Choose the right password:
Passwords should be at least 16 characters long, and contain a combination of numbers, symbols, upper case letters, lower case letters, and a space. They shouldn’t be repetitious at all, nor be an actual word or ID.
Sounds rather tricky doesn’t it? Not only is creating them hugely annoying, but so is remembering them.
One way of creating a mumbo jumbo password that you can actually remember is to extract it from a phrase: For example “I have 3 pink goats and 5 cats in the house.” Password generated: Ih3pga5cith. So while inventing new passwords, you might as well make for some comic entertainment out of it.
You can create highly secure passwords using this tool.
4. Opt for two step verification:
Gmail, along with Facebook, offers this seamless way of keeping your security intact. When signing in, it simply asks you to enter a code that it sends to your phone. Fast, clever and functional.
 5: Disable autocomplete for user names and passwords:
5: Disable autocomplete for user names and passwords:
Fundamentally, turning off the autocomplete feature equates to logging out when you're not at your computer. While it might be bothersome to repeatedly input your complex password each time you leave your computer momentarily, it's crucial when using a public computer or when the device is shared with others.
To disable the feature on Internet Explorer, click Tools > Internet Options > Content, and choose the Settings button in the AutoComplete section. Uncheck User names and passwords on forms. Click OK, and then choose the General tab, and click Delete > Delete Passwords. Click Close and OK. Uncheck User names and passwords on forms in Internet Explorer's AutoComplete Settings dialog box.
In Firefox, simply click Tools > Clear Private Data (or press Ctrl-Shift-Delete), check all the items, and click Clear Private Data Now.
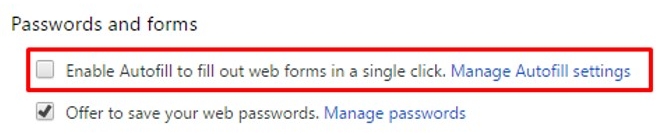
In Google Chrome, click on Chrome's menu button > Scroll all the way to the bottom of the settings page and click on Show advanced settings > Scroll down and locate the Passwords and forms section > Uncheck the mark next to the option labeled Enable Autofill...
 6: Team up with a password manager:
6: Team up with a password manager:
There are a plethora of password managers out there that simply store all your riddles and fill in your log ins. It’s sort of like having a little memory stick with you. Some great options include 1Password, LastPass, Roboform. All you have to remember is the master password to log into the password manager itself.
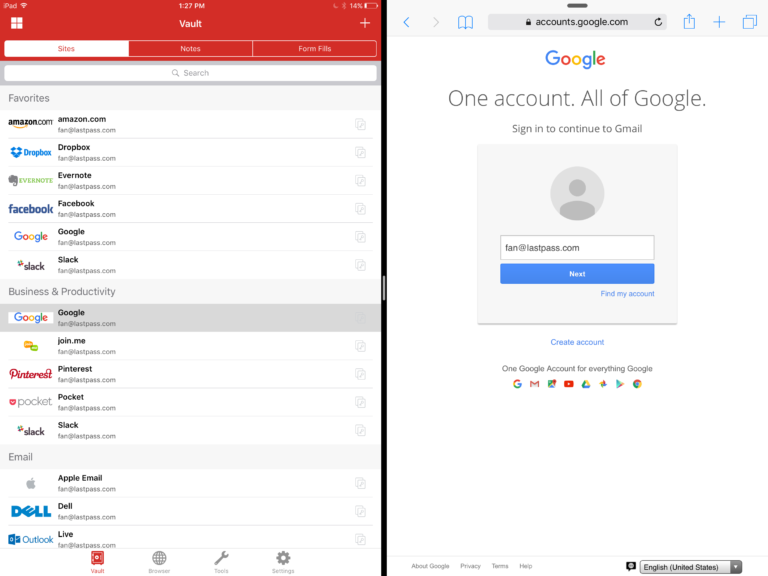 LastPass password manager
LastPass password manager
7: Don't send your password via e-mail or give it out over the phone:
That’s rather a given, but you never know when you might need a little reminder of the obvious.
Our advice: just do it.
So there you have it. Our guide to the essentials in password conundrums.
Imagine your house – the nest of all your possessions, memories, treasures. Now imagine if you just left the door unlocked for whomever to pass by.
Online passwords are like keys to your home. No matter what, you want to ensure that your world is securely locked.





Please, comment on how to improve this article. Your feedback matters!