Accellion – Securing and Sharing Your Documents Wherever They May Be
- Please tell me a little bit about yourself and your background.
- What are your top three tips for secure business collaboration (besides buying your product)?
- Please give me an overview of your kiteworks product, touching on each of its main capabilities.
- kiteworks has a particularly close integration with Microsoft products – correct?
- What are some of the other products that kiteworks is integrated with?
- How do you address mobile users?
- How do you define the market that you are targeting (i.e. size, vertical, special needs)?
- You seem to pursue a strategy of both direct enterprise sales and sales via partner VARs and resellers. Is that correct? What percentage of revenues comes from each sales channel?
- How many active customers do you have today? Where are they mainly located?
- How would you describe the typical customer that you have today (i.e. size, vertical, special needs)?
- Who are some of your biggest customers?
- Whom do you see as your main competitors?
- How do you see your tools as different and/or better than theirs?
- What are some of the lessons or insights you gained from the WannaCry ransomware attack?
- Is the growing use of cloud technologies making life easier or harder for Accellion and kiteworks?
- To what degree is the Iot (Internet of Things) starting to affect you and your customers?
- What are your future plans for Accellion?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
- Is there anything else you’d like to share with our readers?
More and more companies today are subject to strict compliance and regulatory requirement regarding much of the data that they store in their system. In general, data privacy is becoming a greater concern for most enterprises. Cliff White, the CTO of Accellion explains how his company’s kiteworks platform secures these documents, while at the same time allowing necessary sharing and collaboration. While Accellion has a close relationship with Microsoft and its technologies, kiteworks integrates with many other popular systems.
Please tell me a little bit about yourself and your background.
Currently, I am the CTO here at Accellion. Over the past almost six years, I have architected the development of Accellion’s flagship enterprise product, kiteworks. In a nutshell, kiteworks is a collaboration platform that enables organizations to securely share sensitive content with the external world while maintaining complete control and visibility. Most of my career before Accellion was spent developing software, including business applications, and deploying the network infrastructure to support them.
What are your top three tips for secure business collaboration (besides buying your product)?
- Get Control of your Data. One of the first things that any organization needs is control over the data being exchanged in and out of the organization. That means being able to administer who has access to what information and having the ability to allow or disallow any exchange of information based on the policies developed by the enterprise.
- Maintain Visibility. Visibility is key for governance and auditability. The ability to demonstrate what information is shared throughout the organization is crucial when maintaining compliance in regulated industries like healthcare, financial services and government. This means having a complete audit trail of every instance of information exchange to demonstrate only authorized users have access.
- Ensure Usability. Giving end users a simple, intuitive way to exchange information from whatever devices they use is a must. If a solution requires extensive training for end users to be productive, or only works on some of their systems, then the temptation to turn to insecure shadow IT solutions will limit widespread adoption of an otherwise better (more secure), sanctioned solution.
Please give me an overview of your kiteworks product, touching on each of its main capabilities.
- Secure File Transfer
- Secure External Collaboration
- Governance and Compliance
- Enterprise Integration
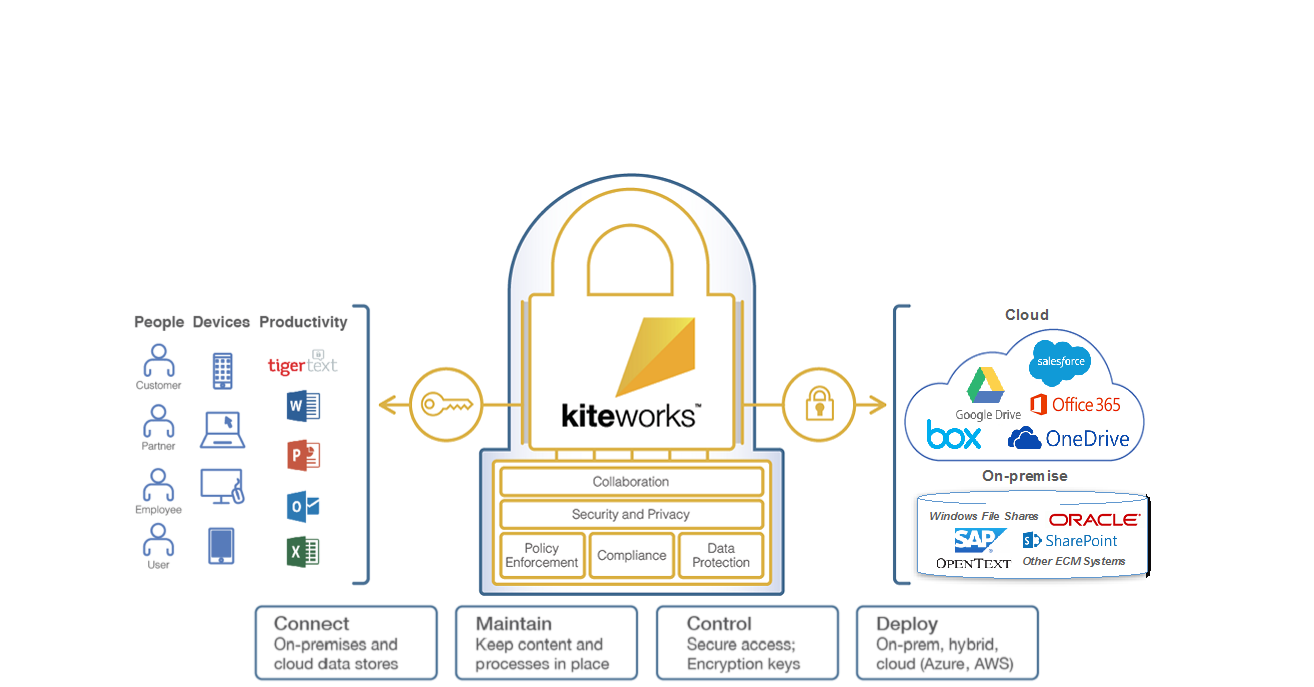
Most enterprise organizations have the need to provide their end users with the ability to securely exchange information with internal and external users. kiteworks provides the means to share sensitive content securely and efficiently, no matter where it is stored, no matter where you are presently located, and no matter which device you’re using to access the content.
At its core, kiteworks is a secure collaboration platform delivered in the form factor of a completely self-contained private cloud. Integrations with a number of on-premises and cloud-based content repositories like Microsoft SharePoint, OneDrive, OpenText, Box, Dropbox and others allow users to access, share and collaborate on content easily and securely without any need for content migration or duplication and with no disruption to existing business processes and workflows.
Therefore, with a single interface on my laptop or phone, I can access a file stored in any repository and share that file with you easily and securely:
- I do not have to move the file to a new platform.
- I do not have to search multiple repositories to find it.
- I do not have to worry about file size limitations because I’m only sending a link to the file, not the file itself.
- I can set permissions for what the recipient can do with the file (e.g. download it vs. just view it, permit access for only a set period of time, etc.).
Finally, my IT department has full visibility into who is accessing the file, when they are accessing it and what they are doing with it – which is critical for compliance.
kiteworks has a particularly close integration with Microsoft products – correct?
Yes, we are extremely proud of our deep Microsoft partnership. We have worked closely with them on several fronts. The first was our certified integration with Office365 both on iOS and through the web. We are unique in that kiteworks can be deployed completely in a private cloud. This means that an organization can host kiteworks 100% in their own infrastructure and still have all the benefits of the Office365 product line.
We have also worked with Microsoft to make kiteworks a premiere offering on the Azure marketplace. This means that customers can build out their kiteworks installation at the press of a button, hosted on Azure. This is exciting in that it allows both Microsoft and Accellion to offer a flexible hybrid product that solves a wide range of productivity problems while still giving full control and visibility into what is happening with enterprise data.
The third investment we have made with Microsoft is our native application extensions. With plugins, kiteworks users can share and collaborate on documents directly from Office, Excel, Power Point and Word. This is an extremely powerful offering and gets users securely collaborating directly from the Microsoft products that they are already using.
What are some of the other products that kiteworks is integrated with?
With kiteworks, end users can access content stored in their own storage and collaboration accounts, including: Windows CIFS shares, SAMBA shares, Dropbox, Box, Google Drive, SharePoint, SharePoint Online, OneDrive and more.
We also integrate with a range of security solutions, for example DLP or 2-Factor Authentication, giving the enterprise complete control to define access policies, and full visibility into what content is moving in and out of the system.
How do you address mobile users?
Accellion offers iOS and Android applications enabling secure access to all data that users would have access to in the kiteworks web browsing experience. Our mobile application provides control over what information is stored on the device through features like local encryption and remote wipe on demand capabilities.
How do you define the market that you are targeting (i.e. size, vertical, special needs)?
We are a good fit for organizations where sharing content beyond the traditional border is important, and when the information is of a sensitive nature, requiring greater levels of security and may be subject to compliance with industry regulations. When customers have content stored in multiple systems and enterprise applications, our ability to integrate tightly is a big advantage. As a result, we are very strong in healthcare, financial services, legal, and government markets.
You seem to pursue a strategy of both direct enterprise sales and sales via partner VARs and resellers. Is that correct? What percentage of revenues comes from each sales channel?
Indirect sales account for about 40% of our total business. Some customers have existing relationships with trusted VARs or preferred distributors and we work well with many of those channels. In certain regional markets, we have made the strategic decision to drive all revenue through partnerships as a local presence is important for the customer.
How many active customers do you have today? Where are they mainly located?
We have over 2,500 active customer organizations that reach more than 15 million end users. Our business is definitely global, with significant installations in North America, Europe, the Middle East and Asia-Pacific.

How would you describe the typical customer that you have today (i.e. size, vertical, special needs)?
We have a broad range of “typical” customers, but there is a concentration in hospitals, banks, law firms, manufacturers, and government entities.
The elements they have in common are:
- A need to share content with external collaborators as part of a business workflow.
- Content that is of a sensitive nature, e.g. customer information, confidential business information, or intellectual property.
- Users who collaborate on content from remote locations using various devices.
- A requirement for visibility and control of activity, in order to demonstrate compliance with data governance policies.
Who are some of your biggest customers?
Some of our bigger customers include Verizon, CSX, L’Oreal, and New York Health & Hospitals.
Whom do you see as your main competitors?
Players in our space include Microsoft, Google, Box and Dropbox. Rather than directly competing with these vendors, we in fact integrate with and add value to their solutions.
For example, a customer can use Microsoft Office 365 and OneDrive, while a different department in their organization uses Box and yet another group uses SharePoint. Our solutions enable an end user to access content stored in any of these repositories from a single interface and to share it with external partners securely and in a compliant manner. None of these providers share our level of focus on security and integration. So again, we see kiteworks as extending or adding value to their solutions.
How do you see your tools as different and/or better than theirs?
If an organization is concerned about security & compliance, we are in a very strong position. The fact that we can be deployed either on-premises or in a private cloud provides customers with much greater control, as well as the ability to integrate with their existing security infrastructure. In addition, kiteworks provides a very granular administrative interface that gives system admins an extreme amount of control over who has access to content and what they can do with that content.
What are some of the lessons or insights you gained from the WannaCry ransomware attack?
One key insight is that the hackers will always be looking for new ways to get in, and while we all have to work hard to close the millions of potential vulnerabilities, they only need to find one way in. So, while organizations must continually strive for the best protection from ransomware attacks and other malware, sometimes it comes down to limiting the exposure in case of a breach and how you respond.
kiteworks can be a part of that, as our content is not mapped as a network drive so even infected systems will not have access in order to encrypt files. In addition, if simply wiping a user’s machine is the best route to remediation, all of the shared content is immediately accessible just as it was before the attack.
Is the growing use of cloud technologies making life easier or harder for Accellion and kiteworks?
Easier. Most companies are still struggling with how to use the cloud. That includes figuring out what cloud services to use and determining when to use cloud based virtual resources for some functions and SaaS services hosted in the cloud for others.
Many companies recognize that they can limit expanding a physical data center by instead expanding their footprint in a virtual cloud data center. This limits their investment in physical assets while still giving them control over their digital assets and information. This strategy is where Accellion provides a lot of benefit. For example, kiteworks can be deployed in both on premises physical data centers as well as in a cloud infrastructure. Deployment can also happen incrementally to facilitate a controlled migration from on premises to the cloud or simply to help maintain a hybrid presence. In either situation, kiteworks can help an organization control their destiny when embracing a cloud strategy.
To what degree is the Iot (Internet of Things) starting to affect you and your customers?
Every IoT device generates a ton of data and that data needs to be shared, analyzed, and often, collaborated upon (why else are you generating it?). Enterprises need a way to share this data efficiently and securely, and we enable this.
Along with the more common approach of exposing data and inputs through API’s, we are starting to see customers looking for very simple integrations. A great example of this is that kiteworks has had the ability to translate the SFTP protocol into a direct mapping of kiteworks assets in real time. This means that any of the common SFTP clients that customers have built integrations around are already capable of utilizing kiteworks out of the box with zero modifications.
What are your future plans for Accellion?
We will be expanding and improving on the secure collaboration features and capabilities that we see as our core, and adding integrations with additional systems. We will also continue to offer more ways for a CISO (Chief Information Security Officer) to have visibility into and control over how and when their organization’s information is being exchanged.
How many employees do you have today? Where are they located?
We have about 200 employees with offices in Palo Alto, CA; Providence, RI; Stuttgart, Germany; Singapore, and Ukraine.

How many hours a day do you normally work? What do you like to do when you are not working?
Definitely the vast majority of my waking hours are spent working. Outside of my job, I spend a lot of time with my wife and three children. I enjoy reading science fiction, exploring new technologies and, at the risk of sounding like a geek, programming.
Is there anything else you’d like to share with our readers?
Accellion is currently experiencing an immensely thrilling period, and I am honored to be a part of it. I eagerly welcome feedback from readers regarding their insights on the future direction of security and collaboration. It would be wonderful to hear your thoughts on this matter.




Please, comment on how to improve this article. Your feedback matters!