Baffle – Protecting Your Databases From Breaches
- You have an impressive track record of founding successful startups and then selling them - usually to Cisco. Tell me about that.
- What is even more impressive is that they are all in different fields/technologies.
- Before getting into the specifics of Baffle, can you share your top three enterprise security tips?
- Baffle is in the security camp that assumes that security breaches will occur, and therefore the most effective, or critical, approach is to focus on protecting significant data. Please elaborate on that.
- So your Baffle product is Encryption as a Service for databases?
- Doesn’t the constant encrypting and decrypting of every bit of data have a negative impact on overall system performance?
- How do you manage to encrypt an application’s database and allow it to access that data, without requiring any changes to the application code?
- How do you define your target market?
- What does your pricing model look like?
- How many active customers do you have today? Where are they mainly located?
- How would you describe the industries or verticals of your current and target customers?
- Whom do you see as your main competitors?
- How do you see your tools as different and/or better than theirs?
- How do you see the security software market evolving in the next few years?
- What are your future plans for Baffle?
- How many employees do you have today? Where are they located?
- What changes have you seen, and what changes do you anticipate, in the world of technology startups?
- How many hours a day do you normally work? What do you like to do when you are not working?
As Ameesh Divatia, the co-Founder and CEO of Baffle, likes to say, we need to accept that data breaches are a fact of computing life today. However, his company’s goal is to make these breaches irrelevant by efficiently encrypting data wherever it may be, so that even if there is a security breach, the data will be unavailable and unusable.
Ameesh is not a newcomer to the technology startup world, having built several successful startups in the past. In addition to describing Baffle’s encryption as a service product, he shares his thoughts on the changes in today’s startups and the evolution of security software.
You have an impressive track record of founding successful startups and then selling them - usually to Cisco. Tell me about that.
It is true that I built several companies that were later acquired by Cisco. That was not really by design, but I am proud of the fact that every company was a success and provided Cisco with a new product line.
What is even more impressive is that they are all in different fields/technologies.
Yes, each company was in a different area of technology, but they all addressed computing infrastructure and networking. I like to always learn and do new things and I try to take the lessons learned in one area and then apply them to a different area.
Before getting into the specifics of Baffle, can you share your top three enterprise security tips?
Enterprises must currently consider and address three very critical emerging issues:
- Rise of insider threats – We used to be able to assume that the inside of the enterprise infrastructure was secure, but that is no longer the case
- Compliance regulations – The requirements are expanding to include privacy, meaning that you are legally liable if you lose data irrespective of how you protect it.
- IT Infrastructure is no longer in one place – They are no longer entirely local (on premise) nor totally in the cloud. They are hybrid and distributed, requiring new ways to integrate security in workflows.
Baffle is in the security camp that assumes that security breaches will occur, and therefore the most effective, or critical, approach is to focus on protecting significant data. Please elaborate on that.
Today, it is not enough to only protect the perimeter of the network or organization. Organizations need to be concerned about insider threats and compromised administrator credentials. Furthermore, data is often copied between systems and even made available to 3rd parties. Our goal is to make data breaches irrelevant by keeping the data encrypted wherever it is stored and/or used. By doing so, even if high-level credentials are stolen or a misconfiguration of access control occurs, the data is still protected.
So your Baffle product is Encryption as a Service for databases?
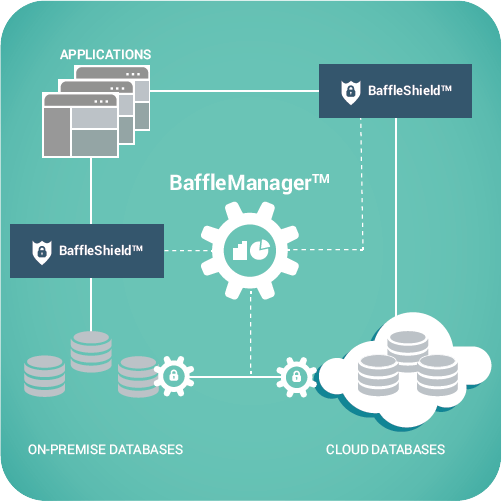
Yes, Baffle provides encryption as a service in the cloud, for both SQL and Non-SQL databases. From the very beginning, we built the platform for the cloud. It is implemented as a proxy for existing databases and it integrates very easily with existing workflows.
We currently support the Cassandra, MySQL, and MariaDB databases, and are planning to support MSSQL, Oracle, and PostgreSQL databases in the near future.
The following images show how we see the threat model for corporate database access and then how our security model – and our BattleShield ™ data access proxy – protects against those threats.
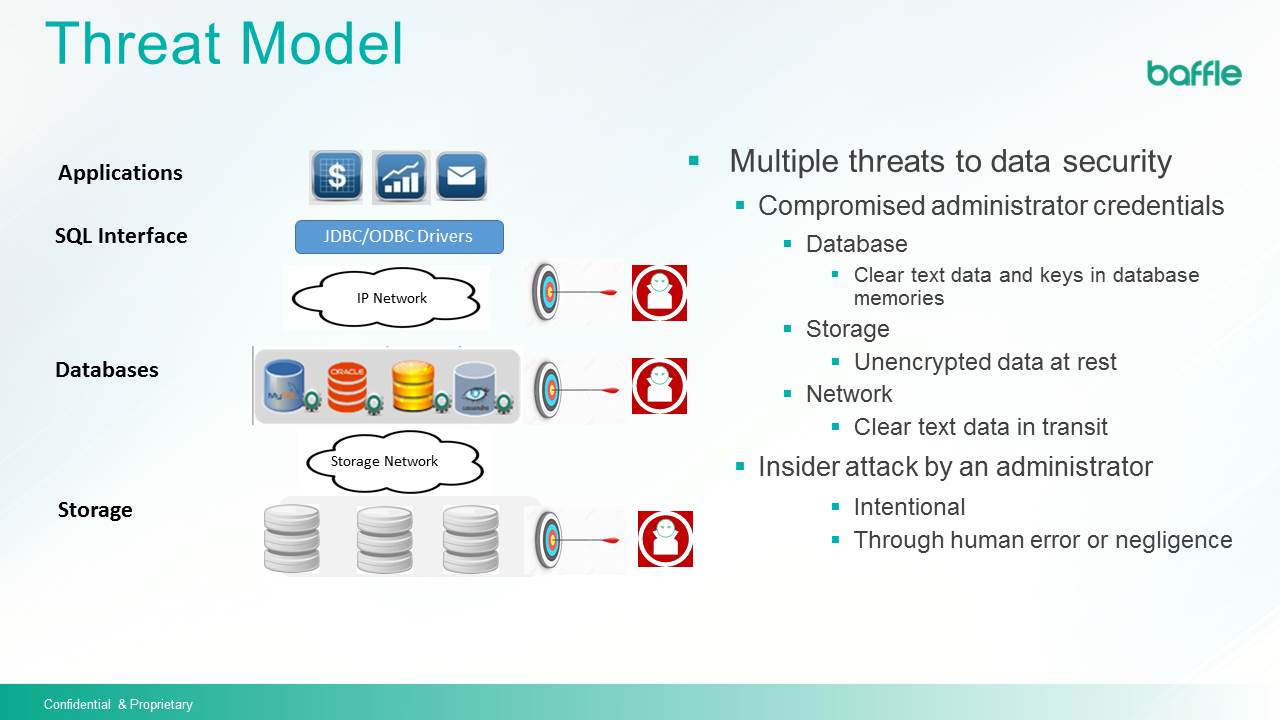
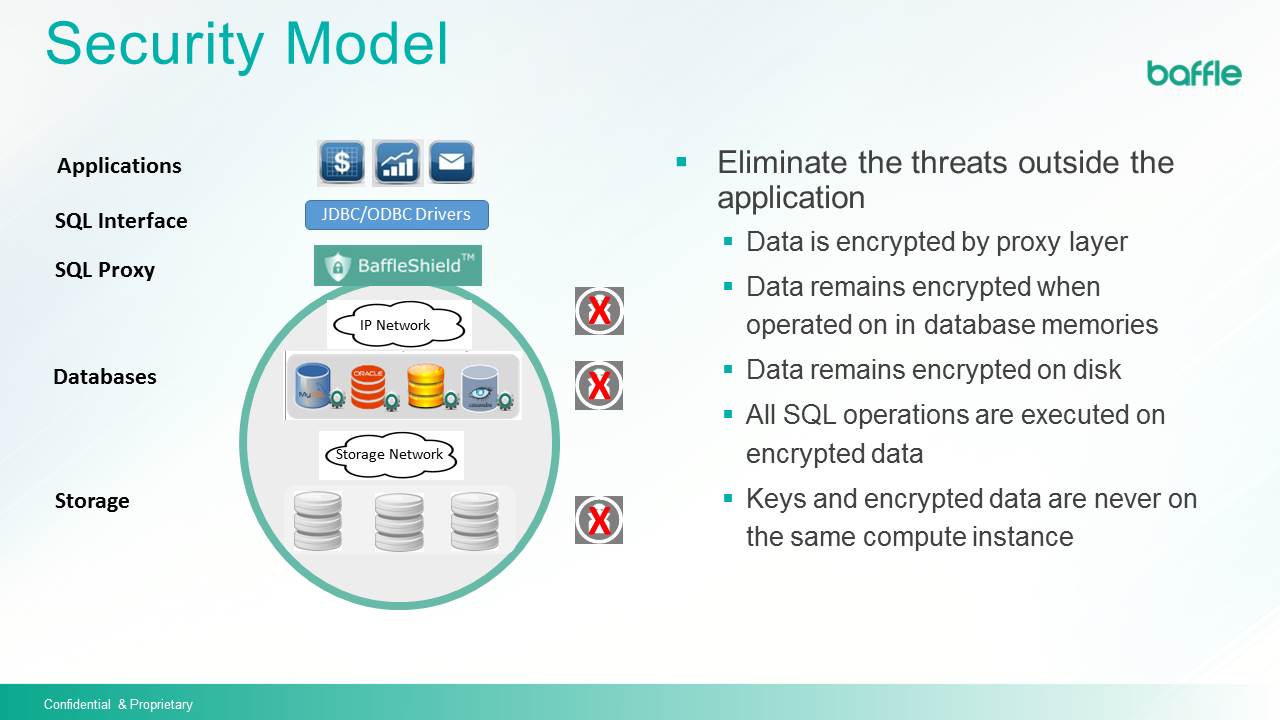
Doesn’t the constant encrypting and decrypting of every bit of data have a negative impact on overall system performance?
That is a very good question. Sure, it does have some impact on performance. We focused on minimizing that impact ever since the company started. Our approach to encryption is centered around the ability to perform computations in a distributed manner leveraging from multi-core compiler techniques. This ensures that our performance is similar to ‘at rest’ encryption although we also protect data ‘in process or use’.
However, a more reasonable comparison would be to existing approaches to application-based encryption, where the data has to be extracted into the application, decrypted, and then operated on. Our approach allows the operations to be performed on encrypted data in the database making it orders of magnitude faster.
How do you manage to encrypt an application’s database and allow it to access that data, without requiring any changes to the application code?
We do not require changes to application code because we supply a drop-in proxy for database access. We monitor the network commands for SQL commands and then encrypt/decrypt the data right there. It is totally transparent to the application.
Integrating encryption has traditionally been difficult and required developers to make changes to the application code. With our service, we do all of the hard work for our customers, making it an operational rather than a developmental task.
How do you define your target market?
Our main target is the traditional enterprise infrastructure market in general, and the database market in particular. The size of this market is approximately $50 billion. The size of the encryption market today is only about $1 billion. Microsoft and Oracle charge 20% of the overall database license fee for their encryption libraries, so there is still a lot of room for growth.
What does your pricing model look like?
The traditional pricing model for database encryption is based on the node cost. With cloud-based delivery mechanisms, the model will evolve so our plan is to offer two pricing options:
- For the traditional enterprise database market, we charge based on the number of database licenses.
- For the cloud-based database market, we charge based on the number of applications that we protect.
How many active customers do you have today? Where are they mainly located?
We are not yet in full production – we expect that to happen at the end of this quarter. Having said that - we do currently have multiple active customer engagements, mostly in the US.
How would you describe the industries or verticals of your current and target customers?
Our main industry segments are:
- Healthcare
- Fintech
- Database as a Service providers
Whom do you see as your main competitors?
Data-centric security is part of Gartner’s DCAP (Data Centric Audit and Protection) category with vendors offering solutions that protect data at the record level including encryption, masking and anonymization. This approach is different in the sense that operations are possible on encrypted data. We are often compared to encryption at rest and HSM (Hardware Security Module) vendors, none of whom protect data while it is in process.
How do you see your tools as different and/or better than theirs?
Our approach offers several advantages:
- It is an end-to-end solution, protecting data at all times - in process and at rest.
- It enable very fast application performance, even on encrypted data
- There is no need for SDKs (Software Development Kits) or changes to application code.
- It is a common solution that works for all SQL and NoSQL databases
How do you see the security software market evolving in the next few years?
I think that these trends are going to shape the security market for the next few years:
- New cloud-based delivery models will significantly simplify data protection along with comprehensive monitoring of data access.
- Increased adoption of privacy regulations that penalize companies that lose their customer’s data, prompting pro-active measures to protect data.
- A new class of security solutions is emerging, that protect data at the record level but do not interfere with application operation
- Big improvements in our ability to detect data access threats using technologies such as artificial intelligence.
What are your future plans for Baffle?
Our current product blueprint focusses on three main areas:
- Implementing support for additional databases
- Embedding our platform within the enterprise infrastructure and workflows
- Enabling secure data analytics environments in the cloud
How many employees do you have today? Where are they located?
Right now, we have ten employees. Two of them are located in Austin, Texas and the others are located in Santa Clara, California.
What changes have you seen, and what changes do you anticipate, in the world of technology startups?
I definitely see more startups focusing on the ability to analyze – and then modify – human behavior, as we saw with Uber and Airbnb. What drives these changes is greater ease of use. As technology gets more complex, the ability to get it adopted is where opportunities lie.
How many hours a day do you normally work? What do you like to do when you are not working?
That's quite a challenging question, and you might want to direct it to my wife [laughs]. My personal goal is to maintain flexibility and maximize efficiency in my work. Despite being part of a startup, I make a conscious effort not to exceed 12-14 working hours per day.
I actually have many different hobbies, including sports (golf is my biggest obsession) and music. I also enjoy spending time with my wife and two teenage children.




Please, comment on how to improve this article. Your feedback matters!