Report - Dalil Data Breach: 5+ Million Users' Data Exposed by Unsecured App
Dalil is the biggest phone directory in Saudi Arabia.
With more than 5 million downloads, Dalil is the 13th most popular communications app in the Kingdom. For context, this is where Viber and Telegram rank in the US. 96% of its users are in Saudi Arabia; the remainder are in Egypt and other Arab countries.
The app works like Truecaller, helping users identify unknown numbers. In theory, this offers protection against cold callers and other unwanted contact.
However, reality tells a different story. Led by Noam R., a well-known white hat hacker and activist, VPNMentor's research team discovered a major security breach in Dalil's database. Instead of protecting users, this breach means complete sets of data for 5 million+ users are open and accessible to the entire internet.
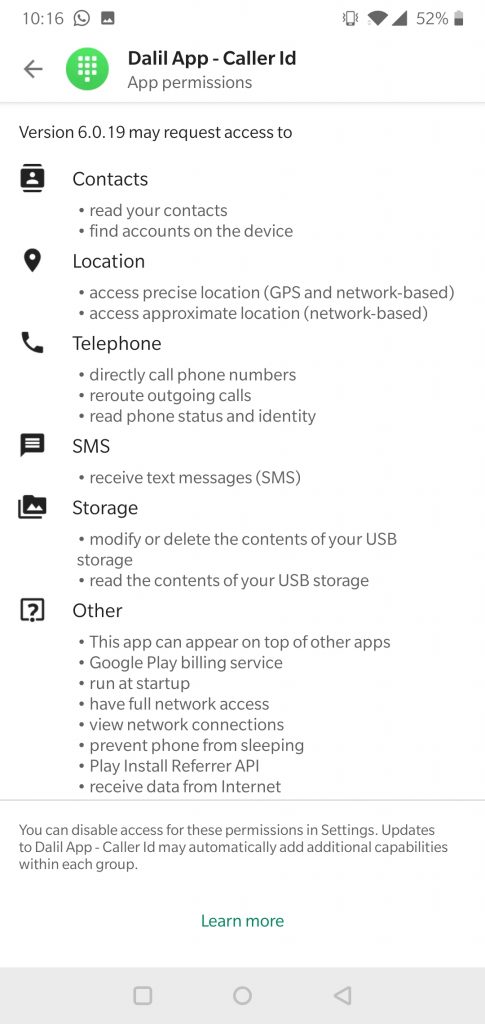
App Permissions
Like all apps, Dalil has a list of permissions requests users must agree to before downloading and installing the program. Some permissions are to be expected; for example, a caller ID app needs to read contacts. Other permissions seem more suspect, like reading and modifying your phone's stored files, rerouting calls, and tracking your location.
Dalil's Database is Unsecured
However suspicious some permissions may seem, they are not the root cause of Dalil's security issues.
All the user data gathered by the app is stored in an unsecured and unmonitored MongoDB database. It's reachable without authentication, giving hackers password-free access to millions of people's data.
As well as the application log, this database includes both harvested and voluntarily-submitted personal information. The User Journey below shows how much data the app can access:
By default, the app collects users':
- Cell phone number
- IP address (internal and external where applicable)
- Device model, token, serial number, and operating system
- IMEI (the device's specific identification number)
- Sim card and network provider information
- GPS and network location information
When users create their profiles, they are prompted to add additional information, including their:
- Personal email account
- First and last name
- Gender
- Profession
Again, this data currently appears on a completely open database. Our team found it: this means anyone else who wants to look for it could, too. And while our hackers are not malicious, we cannot guarantee others' motivations.
Sample Profile
As demonstrated above, the app collects large amounts of information. This allowed us to create a profile for one Dalil user from hacked data. While we've redacted any crucial identifying information, it shows how dangerous this data could be in the wrong hands.
As well as the user's phone number, IMEI, and network data, we can also see plenty of personal information.
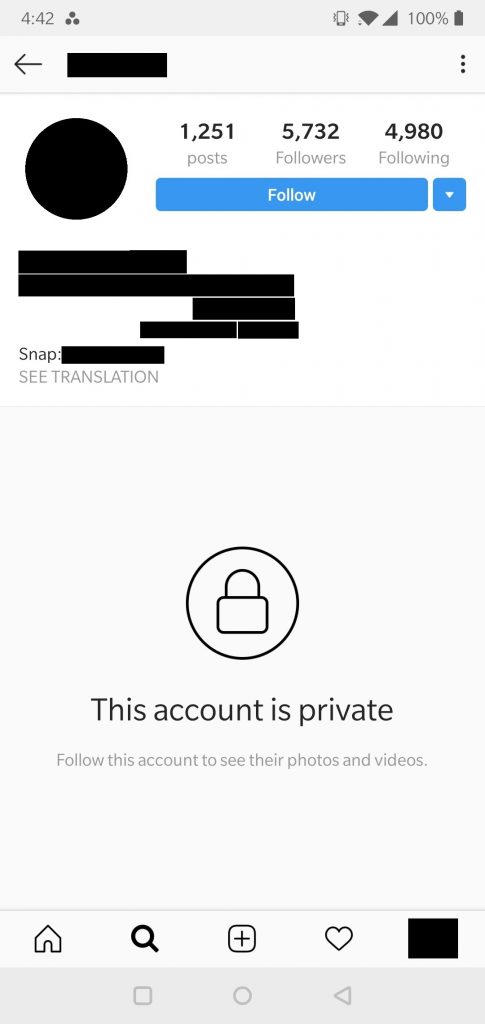
When we translated the Unicode from the database into Arabic lettering, we see the user listed his profession as the Ha'il Region, the area in which he lives. However, as both his email addresses are listed, we simply Googled his details. This gave us his professional Instagram profile:
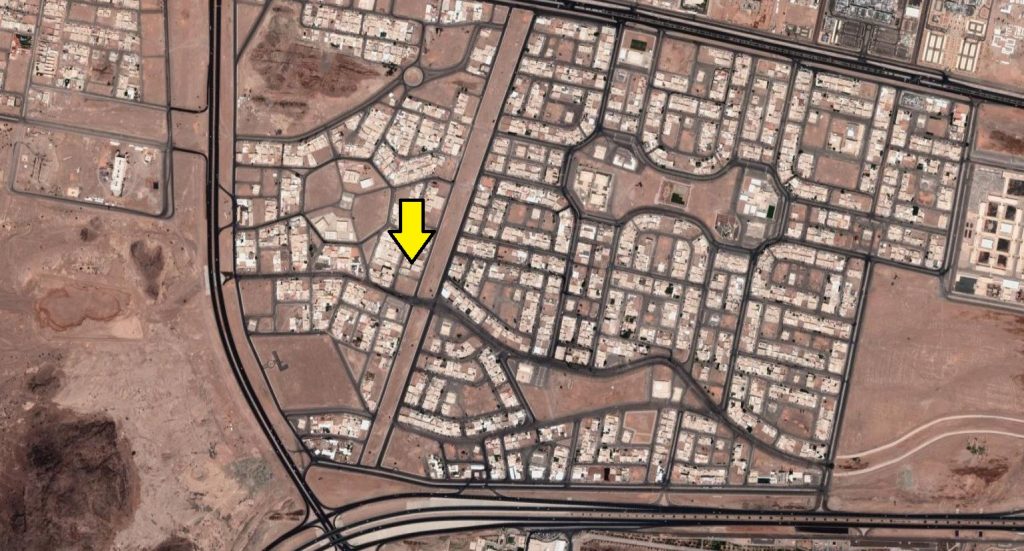
When we searched for the formatted address listed, we found this location:
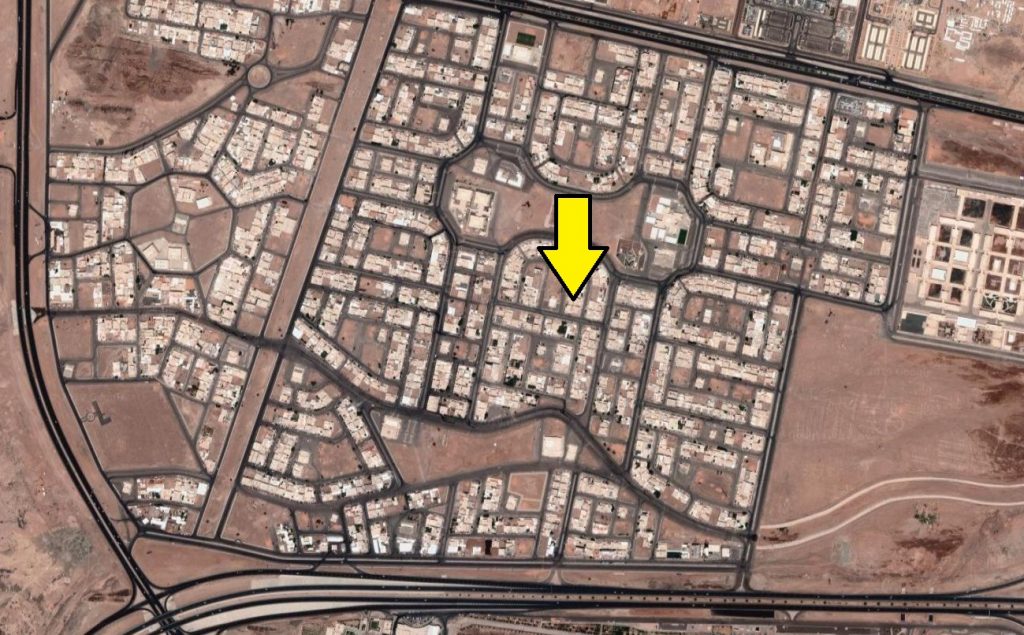
It's just two blocks over from the coordinates listed at the time of his last use, painting a very accurate picture of where this user can be found:
Security Issues
This presents two distinct security issues.
Firstly: targeted adware and malware. While the database does protect some data (for example, user passwords are hashed), the available information allows us to create fairly accurate user profiles.
If the contents of this database were sold to third-party advertisers (or governments and terror organizations in the dark web), knowledge of users' genders, professions, and locations could allow them to create targeted ads (or hostile acts).
Additionally, and more worryingly, knowing the precise make and model of users' phones, as well as their operating systems, allows for highly specific malware placement. This could create huge personal and financial loss for millions of users across Saudi Arabia, Egypt, and other countries where Dalil is popular.
There is another, far darker reason that Dalil's unsecured database is potentially so dangerous. Saudi Arabia has some of the world's strictest censorship laws, which extend to monitoring and censoring phone calls made over approved apps. Should this database fall into the Saudi government's hands, they could easily identify users by their phone numbers and listen to their phone conversations.
This raises two red flags. Firstly, the permissions allow the app to reroute calls. Phone calls are automatically filtered through an allowed app, which allows Saudi officials to listen in.
The app also has permission to “find accounts on the device”. As shown in the user profile below, the app harvests information about users' Viber profiles. Rakuten's Viber is permitted in the Kingdom, meaning it's susceptible to surveillance.
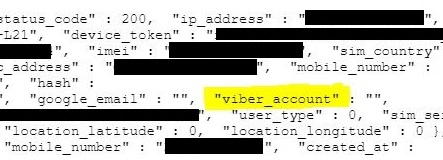
Additionally, the app permissions allow access to the device's stored media files and received text messages. While we didn't find any images, videos, or texts in the database, it's possible these files are stored elsewhere and can also be hacked.
We discovered that the app also records searches made through it. Although the contact's phone number was encrypted in the database, the names of contacts the user searches for are recorded.
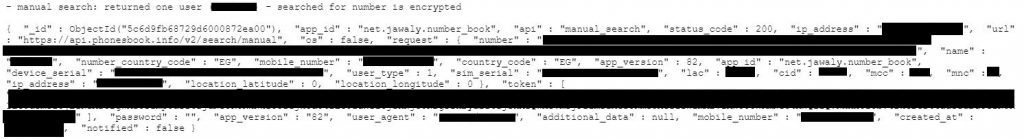
Strict censorship combined with the ability to track user locations (again, due to the app's permissions) could mean grave consequences for anyone caught contravening Saudi Arabia's laws. Should the Saudi Arabian government access this database, people whose professions leave them open to monitoring could experience real dangers.
For example, should a journalist search for - and speak to - a contact and arrange to meet, the government could theoretically identify this contact. This is especially likely if the contact was saved with an identifier (such as "Bob - Pizza" or "Sophie - Work"), and given that 15% of Saudi Arabia's population uses Dalil.
The app's location permissions mean that officials could trace the journalist (and their contact). They could follow him to a meeting, listen to everything reported, and arrest him immediately.
Ethical Hacking and Conclusion
We discovered this breach as a result of a web mapping project. Our hacker uses port scanning to examine particular IP blocks and test open holes in systems for weaknesses. They examine each hole for data being leaked. In this case, they installed the app and entered their own data. This allowed them to confirm both that their data was leaked, and the identity of the database.
We contacted Dalil to alert them to this security breach. Our information included the date on which we planned to publish this article, and gave them a few days to find and secure their database before this knowledge became public. At the time of publication, we had not yet heard back from them. As hackers can obviously find this database online - and may have already - it's important to share our findings with the public so they can take appropriate measures to protect their data.
Subsequent to reporting the issue to Dalil (and prior to publishing this report), it came to our attention that although some data on the server was encrypted, newly logged data remained unencrypted. This observation indicates the presence of at least one malicious actor accessing Dalil's user data. We emphasize the utmost urgency for Dalil to take swift action and ensure the protection of their users.
The lesson here is clear: popularity does not equal trustworthiness. Dalil's unsecured database is evidence that users need to be careful when agreeing to app permissions and entrusting unknown entities with their personal information as even the most well-regarded apps make mistakes.
Past Reports
You may also want to read our report of fake apps used in Iran to monitor users, VPN Leak Report and Data Privacy Stats Report.
Please share this report on Facebook or tweet it.






Please, comment on how to improve this article. Your feedback matters!