Report: How We Uncovered a Phishing Kit Being Used to Scam Thousands of People
Led by Noam Rotem, vpnMentor’s research team has discovered two separate criminal schemes using slightly altered versions of the same phishing kit to scam people across the globe.
It appears the phishing kit was being used to target people mostly living in Israel and France by two separate criminal gangs. However, we believe these two groups operate phishing websites and SMS operations based on the same phishing kit, possibly obtained from the same source. In addition, at least one of them is potentially affiliated with the OpIsrael political hacking group.
What is a Phishing Kit?
A phishing kit is a set of software tools built to make it easier for people with limited technical skills to create and launch a phishing campaign.
‘Phishing’ is a scam in which the perpetrator sends fraudulent emails or text messages appearing as a legitimate business or organization. The goal is to trick potential victims into performing several actions that benefit the scammer somehow. These include:
- Clicking a payment link and entering their credit or debit card details.
- Providing Personally Identifiable Information (PII) data or login credentials to private accounts that can be used to commit fraud or identity theft.
- Clicking a link embedded with malicious software, such as spyware, malware, or ransomware.
In the past, phishing campaigns required specific technical skills to be convincing and successful. However, a phishing kit makes it incredibly easy to set up and send fraudulent emails and texts to huge numbers of people.
A typical phishing kit includes:
- Website software with a graphical user interface to build a fake website.
- Email or text templates with graphics and scripts to follow.
- For an additional fee, lists of email addresses, telephone numbers, PII data, and software for automating the entire process.
Phishing kits make cybercrime accessible to anyone with a laptop and internet connection. No technical skills are required. It’s basically a ‘plugin and play’ model for internet fraud and represents a significant escalation in the growing global proliferation of cybercrime.
Now, let’s take a look at how this phishing kit was being used.
Scam 1: Criminal Group Posing as UPS Courier Service
In the first scam uncovered by our team, a criminal outfit was using the phishing kit to send text messages appearing as the well-known global courier service, UPS.
Most of the targets were residents of Israel and were sent a text message claiming they had a package ready for collection. They were then directed to a payment page to pay for the delivery.
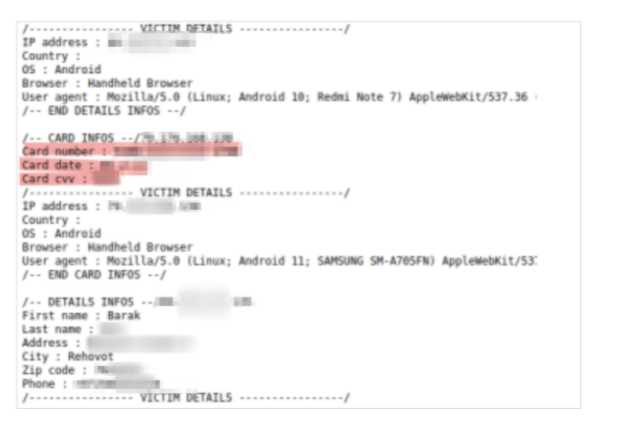
However, due to their lack of technical skills, the scammer(s) failed to secure their server and forgot to disable a 'directory listing' running the phishing kit. In doing so, they exposed and contained various file types (PHP, txt, JSON) storing the following records from the people targeted in the scam:
- Access logs, creating a record every time a victim clicked the payment link in the text.
- Lists of credit card details from people they successfully tricked into paying.
- Lists of PII data connected to a separate set of credit cards taken from another source.
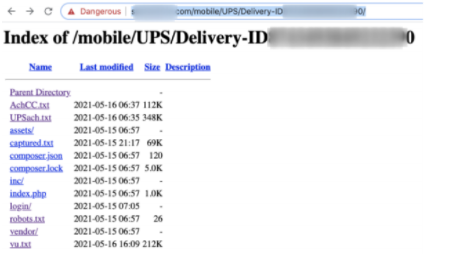 Various file formats storing sensitive data
Various file formats storing sensitive data
Of the 4,400 individuals whose records were stored in the directory listing, the majority were Israeli citizens. Other countries targeted include the US, Brazil, Saudi Arabia, and much of Europe.
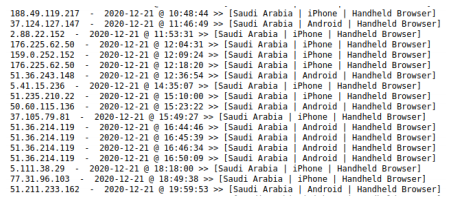 Log file showing the IP address, time, and type of device of a victim who clicked the phishing link
Log file showing the IP address, time, and type of device of a victim who clicked the phishing link
Who’s Behind The Scam?
The directory listing contained scripts for the text sent to Israeli targets, written in broken Hebrew. So, at the very least, we can most likely rule out an Israeli crime gang.
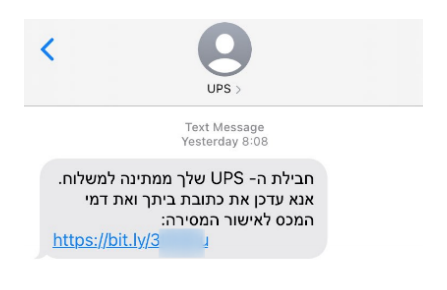 The text sent to Israeli residents posing as UPS
The text sent to Israeli residents posing as UPS
It appears that the party operating the phishing kit are based in Morocco. In the entry logs, we could see 5 entries from the same person based in Morocco, apparently testing the phishing kit from their browser. We suspect these entries belong to the scammer.
How to Spot the Scam
This phishing campaign had numerous red flags that would expose it as a fraud to people with basic awareness of cybercrime. These included:
Poor phrasing: The texts targeting Israeli residents contained numerous grammatical errors. For example, recipients were directed to “update home address and customs tax” instead of updating their home address and paying the customs tax.
False sense of urgency: Recipients were pressured into paying quickly to secure the delivery of their package.
The payment link was a bit.ly shortened URL: These are used to hide the fact you’re being directed away from a company’s actual website - in this case, UPS. Anyone who clicked the link was redirected to an internal page on an Indian news website that had been hacked and converted into a hub for phishing campaigns.
Scam 2: Targeting Customers of Crédit Agricole Bank in France
We also discovered a separate scam using the same phishing kit to target people in France via a hacked website.
The scam, which had been running since October 2020, targeted customers of Crédit Agricole - a French bank that is the world’s largest co-operative financial institute. The person (or people) behind the scam hacked a website unrelated to Crédit Agricole, changed it to mirror the company’s website, and inserted code for the phishing kit into it.
The phishing kit was then used to harvest Crédit Agricole customers’ data, including PII data, credit card numbers, and Crédit Agricole account credentials. All the harvested data was automatically sent to a Telegram account owned by the scammer to notify them any time someone input their details into the phishing kit.
We believe this phishing campaign successfully scammed up to 1,700 people in France.
Who’s Behind This Scam?
The person running this scam didn’t do a very good job of hiding their identity. Through various checks on both the hacked website and the Telegram account, we located them in Algeria, identified their phone number, and even their WhatsApp profile photo.
Implications of Our Discoveries
According to our research, the first scammer successfully collected 380 Israeli credit cards. That’s a conversion rate of over 8.5% - quite an accomplishment by phishing standards. Unfortunately, it’s a terrible score for the Israeli people and their government, who clearly needs to invest more in public education around cybercrime.
The scammer may have hoped to sell the credit card details to another party, rather than using them. Privacy Affairs research states that Israeli credit cards including CVV numbers could be sold for $65 each.
If they knew how to sell the details from all 380 cards, they could make $24,700 from the scam.
We currently don’t know how effective the second scam was.
However, as we’ve already notified the credit card companies affected by both scams, the files are redundant. Nobody could use them in a successful fraud any longer.
While the impact of these two scams has been relatively limited, the implications of our discovery are much broader.
The phishing kit we uncovered was probably used or acquired by many more wannabe internet scammers hoping to engage in small-scale fraud for quick, easy financial gain. This is becoming an increasingly popular form of cybercrime - ‘hobby hackers’ with minimal technical experience buying easy-to-use tools like phishing kits to try out cybercrime, often just for fun.
The fact that the first group using the kit could defraud 8.5% of their targets shows the risks this recent trend in cybercrime poses. Unfortunately, many people are uneducated on how to spot an internet scam. And as cybercrime becomes easier and more accessible to just about anyone, people will continue to fall victim.
The costs and dangers of ‘hobby hacking’ may not be as high as more sophisticated, high-profile cybercrime like the recent attack on SolarWinds in the US. But they will quickly add up.
To ensure this problem doesn’t escalate, governments need to:
- Educate the public on how to spot and report small cases of cybercrime and internet fraud.
- Give anti-cybercrime agencies better resources to tackle all instances of cybercrime, no matter how small they are.
- Introduce legislation, regulations, and financial penalties to hold tech companies facilitating these crimes accountable, such as Telegram.
Political Affiliations
We also found a link connecting at least one of the two criminal parties using the phishing kit in Morocco and Algeria with the political hacking group OpIsrael. OpIsrael is an annual event in which hackers conduct coordinated attacks on Israeli government bodies, private corporations, and NGOs.
One server we uncovered connected to the phishing kit was also being used for OpIsrael attacks.
If this link is valid, it shows the overlap between cybercriminals (even inexperienced ones) and politically motivated hacking groups. They often work hand-in-hand or complement each other due to shared interests and targets.
How We Discovered the Phishing Kit
The vpnMentor research team discovered the exposed phishing kits as part of a vast web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this phishing kit because the people using it were inexperienced and had left their files completely unsecured and unencrypted.
By exploiting these vulnerabilities, we were able to detect two distinct groups utilizing the phishing kit for separate fraudulent schemes.
As ethical hackers, we’re obliged to inform a company when we discover a scam or fraud happening in their name. We reached out to the credit card companies involved to let them know about the phishing kit and help them protect their customers.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included exposing the growing popularity of cybercrime groups on Telegram. We also revealed how a data leak by the biggest US baby apparel chain had compromised 100,000s of customers’ data. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.




Please, comment on how to improve this article. Your feedback matters!