VMRay – The Hypervisor-Based Sandbox That Cannot be Detected
- Please tell me a little bit about yourself and your background.
- You have founded and been involved in several security startup companies. How has the security startup landscape changed over the years that you have been involved in it?
- Let us start discussing your VMRay Analyzer platform with the statement from your website that says “VMRay Analyzer is the 3rd generation in advanced threat detection.” What are those three generations of threat detection?
- What are the main features of your platform?
- I found it interesting that you lay out four different use cases for your software. Can you discuss that a little bit?
- How do you define your market? Who is your specific target audience within that market?
- What methods do you normally use to attract and engage with new customers?
- How many active customers do you have today? Where are they mainly located?
- How would you describe your current typical customer?
- Who are some of your biggest customers?
- Whom do you see as your main competitors?
- How do you see your tools as different as and/or better than theirs?
- What are your top three security tips for businesses today?
- How do you see security threats, and the tools developed to protect against them, evolving in the coming years?
- What are your future plans for VMRay?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
Carsten Willems, the CEO & co-founder of VMRay, has been developing malware detection sandboxes for many years. During that time, he has seen many different approaches, each with their inherent flaws or limitations. However, his latest VMRay Analyzer uses an agentless hypervisor approach that is both fast and very difficult to be evaded by malware. The sandbox can be used for threat protection, threat intelligence, and/or incident response.
Carsten also shares how the motivation for attacks changes over time and what he sees as the next big security challenge.
Please tell me a little bit about yourself and your background.
I am 41 years old and live in Germany. I studied computer science at a well-known German university, although at that time they did not have a real security curriculum.
For my diploma thesis, I developed a malware detection sandbox, which later evolved into a commercial product known as CWSandbox. The back-story is that I was invited to Las Vegas to present my thesis by a company called Sunbelt Software. They subsequently sold and promoted the product worldwide and eventually acquired the source code from me. CWSandbox product is still on the market today under a different name.
After that, I went back to university to get a PhD in cybersecurity. During that time, I met my co-founder Ralf Hund. We did a lot of academic work together in the field of malware analysis, vulnerability research, and hardware hacking. After finishing our PhDs, we co-founded VMRay.
You have founded and been involved in several security startup companies. How has the security startup landscape changed over the years that you have been involved in it?
In the very beginning, when I first got attracted to cyber security, there was no real cyber security industry – just hackers writing viruses for the Commodore 64. In the late 1990’s and early 2000’s, we saw the arrival of cyber criminals. Today, all of our worst fears have become reality with nation states and terrorists leveraging malware to reach their goals.
The attack surface today is growing and growing, not only in terms of data, but also in terms of devices. We are always going to have security threats and will therefore always need protection solutions that keep up with them. This is an awesome time to be in cyber-security!
Let us start discussing your VMRay Analyzer platform with the statement from your website that says “VMRay Analyzer is the 3rd generation in advanced threat detection.” What are those three generations of threat detection?
Our VMRay Analyzer is a malware sandbox, where software can be submittedboth manually and automatically into the sandbox for analysis. The original idea is based on my diploma thesis that, in 2006, became the first commercial malware sandbox. By the time I completed my doctorate in 2013, there were already many commercial sandboxes on the market.
However, those existing sandboxes had two fundamental problems. First generation sandboxes use simulators that were extremely slow and are not scalable. Second generation sandboxes use hooking approaches, which are much faster, but they are easier for attackers to evade.
With VMRay Analyzer, we have a third generation technology that uses an agentless hypervisor approach, so that it is both very fast and scalable. However, unlike earlier approaches, it is also very difficult to evade, since the software being analyzed does not realize that it is running within a sandbox.
What are the main features of your platform?
As I just described, we focus on providing the fastest and most evasion-proof sandbox – that is all we do!
This diagram goes into some more of the specifics of our technology:
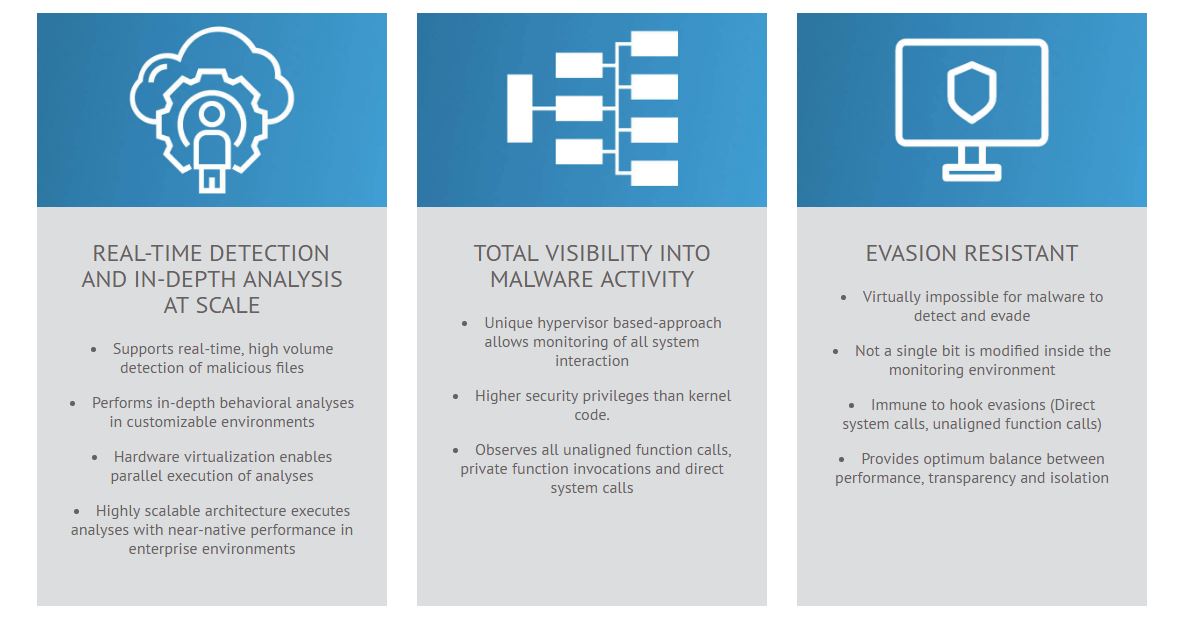
I found it interesting that you lay out four different use cases for your software. Can you discuss that a little bit?
Sure. We talk about these use cases for VMRay Analyzer:
- Incident Response – In addition to reporting whether submitted software is safe or not, we also extract and provide as much information about it as possible. This is our #1 use case right now.
- Threat Intelligence – In order to provide quality threat intelligence, you must analyze a lot of data. There are between 1 and 2 million new malware variants discovered every day! Since our engine is so fast and scalable, we are able (pretty much) to keep up with that pace.
- Protection – This is the ultimate goal. In order to really protect the network/company, you must integrate VMRay with other security systems. We focus on the engine and provide integration with other systems through our technology partners (such as Sonicwall) and external connectors.
- OEM Integration – VMRay can be embedded into Security Appliances and Cloud Security Solutions, providing the ultimate validation and analysis. In reality, OEM integration is really more of a way of using our software than a distinct use case.

How do you define your market? Who is your specific target audience within that market?
We see four target markets that would benefit the most from VMRay:
- Large Enterprises – Global 2000 companies, they have their own SIM (Security Information Management) and CSIRT (Computer Security Incident Response Team). They use VMRay to protect their own infrastructure.
- Law Enforcement and Government – They use VMRay for digital forensics, intelligence, and protecting their own systems.
- Cyber Security Companies – These are smaller companies that focus on cyber security tools themselves. They use VMRay internally to develop and test their own products. This also includes the “Big 4” accounting firms, since they also provide cyber security services to their clients.
- OEM Vendors – They embed our technology into their offerings.
What is common across all of these markets is that they are all cyber security experts.
What methods do you normally use to attract and engage with new customers?
We do not do many cold calls – when we do, it is together with our technology partners. We do attend and exhibit at security industry events like Blackhat and RSA and engage with potential customers there. We put a big emphasis on digital marketing, such as our blog and Twitter, and many customers contact us after reading our content, hearing about us in the media, and/or downloading one of our reports.

How many active customers do you have today? Where are they mainly located?
We currently have 50-60 active customers. Today, 40% of our revenue is from the US and we have a big customer base in Europe. We also have customers in Asia (mainly Japan).
How would you describe your current typical customer?
We currently sell to enterprises and cyber security experts, who feed suspicious or unknown files into the sandbox for analysis and get a report if it is malware or safe. This is done either manually or automatically via our REST API.
Who are some of your biggest customers?
Some of our largest and well-known customers include:
- SonicWall
- Carbon Black
- Cloudmark
- Deutsche Bahn
Whom do you see as your main competitors?
Every big security vendor (e.g. Cisco, NortonLifeLock) includes a sandbox in its offering. However, their offerings are broad and multi-faceted, with many moving parts. We focus on doing just one thing and we make sure that we do it very, very well.
How do you see your tools as different as and/or better than theirs?
We have one very specialized, tool with unique characteristics that make it capable of handling very sophisticated malware and very sophisticated attacks. Our competitors focus on “regular” attacks.
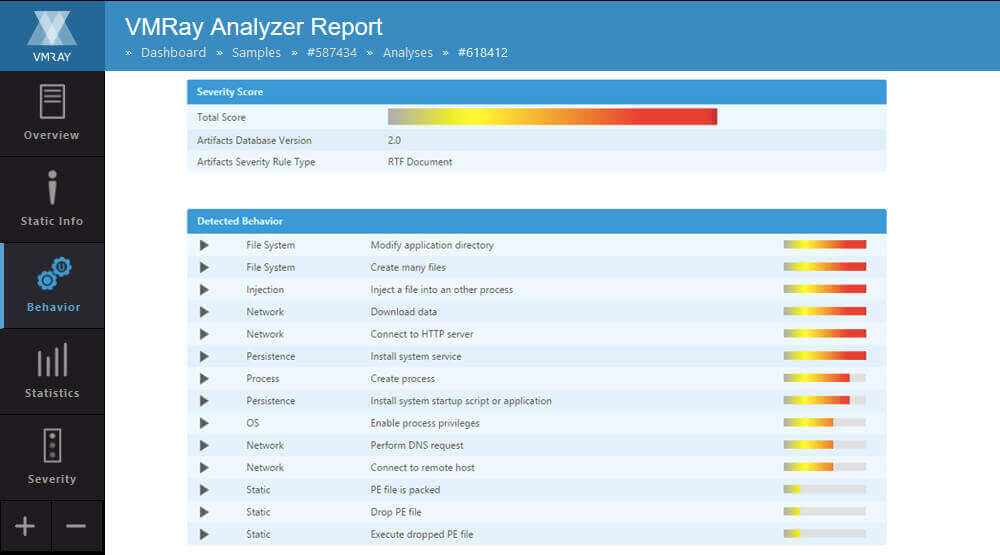
Our USP (Unique Selling Proposition) is based on the following characteristics of our sandbox:
- Scalability
- Evasion-Proof
- Deep, detailed reporting
What are your top three security tips for businesses today?
My top three security tips for today’s businesses are:
- Patch your systems.
- Train your staff to be aware and sensitive to social engineering attacks.
- Choose effective security solutions and deploy as your budget allows.
How do you see security threats, and the tools developed to protect against them, evolving in the coming years?
The motivation for attacks changes over time. At first, it was just for fun, then it was for money, and now we also need to be concerned about attacks from nation states.
I think that the next big security challenge is going to be the Internet of Things (IoT). I am very concerned about how this is going to affect us. The places where we will need to have security solutions will be everywhere – cellphones, smart phones, industry, manufacturing, homes, etc.
The security “arms race” of attackers versus protectors will continue.
Hypervisor-based security is the way of the future, since attackers cannot detect it.
What are your future plans for VMRay?
Our primary emphasis right now is to transform VMRay from a niche product into a broader solution that is easier to integrate, deploy, and use. This will enable us to get wider adoption and to grow the company.
Of course, we will continue our efforts to ensure that our sandbox is still the most evasion-proof sandbox available.
How many employees do you have today? Where are they located?
As a multinational and multicultural organization, our company boasts a diverse workforce. Specifically, we have a team of 30 employees based in Germany, alongside an additional four sales and marketing professionals operating in Boston.
How many hours a day do you normally work? What do you like to do when you are not working?
I work a lot – just like any other entrepreneur. Since it is fun, I enjoy it very much. I do not really have a lot of free time, but when I do, I enjoy cooking and playing/watching soccer.




Please, comment on how to improve this article. Your feedback matters!