Why Using HTTPS is so Important for Your Website
Anyone who's gone to a website has probably noticed that the URL starts with http or https. You may have also seen a green lock icon with the word 'secure' written beside it. Have you ever wondered what those letters and that lock sign mean?
HTTP Tells Your Browser How to Communicate with Websites
HTTP (Hypertext Transfer Protocol) is an application protocol that runs on top of the TCP/IP (Transmission Control Protocol/Internet Protocol) suite, which is used to transfer all sorts of files – such as text, images, sounds, and videos – over the World Wide Web. All the information on the internet is transferred between the client and the server in the form of hypertext, which is where HTTP gets its name. HTTP resources across the internet are located using Uniform Resource Locators (URLs), which are unique for each resource.
HTTP Can Make You Vulnerable to Cyber Attacks
Nevertheless, relying solely on HTTP exposes your device to various forms of security attacks, which encompass the following:
- Garbage flood
In a garbage flood attack, a connection to the HTTP port is opened in order to send garbage binary data through it. Most of the time, these attacks are not noticed, as it is assumed that the incoming data is valid HTTP traffic. The primary purpose of this attack is to glut internal buffers and queues in the web server. - Reverse bandwidth floods
A reverse bandwidth flood attack causes the server to send traffic to the LAN or to the internet as a whole in such a way that it will saturate the uplink of the server. In other words, the attacker will send as many requests as possible in an attempt to flood the server's uplink connection. - Access to unauthorized users
When unencrypted data is sent over the communication line, it is prone to man-in-the-middle attacks. In these type of attacks, hackers capture data packets that may contain sensitive information such as the user's credentials, which can allow them unauthorized access to the user’s data. - Vulnerabilities that arise due to cookies set by HTTP
Cookies are small files stored on the client side that allow the server to deliver a page tailored exclusively for a particular user. Sometimes, the page itself can have some script embedded within it that uses the data from the cookie to carry information while going from one website to another. HTTP cookies have the potential to cause security problems when managing their HTTP state, as they do not provide isolation by port. If a cookie is readable/writable by a service on one of the ports, it is also readable/writable by a service on another port belonging to the same server. As a result, an attacker can acquire access to private information from the victim's current session.
These security risks are the reason for the existence of HTTPS (Hypertext Transfer Protocol Secure). Below, we will review the most important concepts related to HTTPS.
HTTPS Provides an Extra Layer of Security
HTTPS is basically a secure version of the Hypertext Transfer Protocol (HTTP), which is used by your browser to communicate with websites. The S at the end of HTTPS stands for 'secure.' With HTTPS, standard HTTP protocol is coated with an SSL/TLS protocol. SSL, which stands for Secure Sockets Layer, creates a secure layer for transmission of data between the web server and the web browser. If you are using Content Management System (CMS) like WordPress or Joomla, HTTPS is necessary.
Until recently, HTTPS security encryption was only used by e-commerce sites for their web pages that require users to enter their credentials, such as payment and login pages. However, today it is much more widespread. If you have your own website, it is likely that you have been advised to get HTTPS encryption.
Often, people switch to HTTPS because their site’s Google ranking is adversely affected without it. However, they are not aware of the security benefits of HTTPS. In fact, the reason HTTPS could improve your Google ranking is because Google checks the trust and authenticity of a website when comparing websites with equivalent content.
The fact that security is a priority for Google can be seen in the fact that at the Google I/O conference in June 2014, a goal was set to fully incorporate HTTPS, and to make all communications over the internet secure by default.
Beyond Google rankings, using HTTPS can also improve user trust in your website. For instance, according to GlobalSign, around 80% of the users choose not to proceed with a purchase if the website does not have HTTPS.
Moreover, as mentioned above, HTTPS prevents intruders from attacking the communication line between a user's browser and a website. Intruders can sometimes be lawful parties, such as ISPs, that seek to bypass the network in order to display advertisements on web pages. However, they can also be malicious attackers seeking to install malware on a user's computer. This malware can flood the computer with undesirable advertisements that tamper user experience and generate security loopholes, such as backdoors that provide the hacker constant access to the victim's activities.
Attackers may try to trick the user by making a forged request appear genuine. For example, a classic GET request to transfer $100 from one bank account to another may look like this:
GET http://www.somebank.com/transfer.do?acct=SomePerson&amount=$100 HTTP/1.1
However, an attacker might modify the link in such a way that the amount is transferred to his/her own account. Then the GET request will look like this:
GET http://www.somebank.com/transfer.do?acct=Attacker&amount=$100 HTTP/1.1
The attacker can then embed this request in an innocent looking hyperlink like this:
And he or she might even hide the malicious script in an image with no width and height like this:
Now, all the attacker needs to do is spread the link to a lot of users and hope that they click on the URL while they are logged into their bank account. If they do, it will result in them accidentally transferring $100 from their bank account to the attacker's bank account.
This is just one simple example of how an attack can occur using Cross-Site Request Forgery. Cross-Site Request Forgery, also known as XSRF, Sea Surf, or Session Riding is an attack vector that forces the user to execute an unwanted action while they are logged into an application.
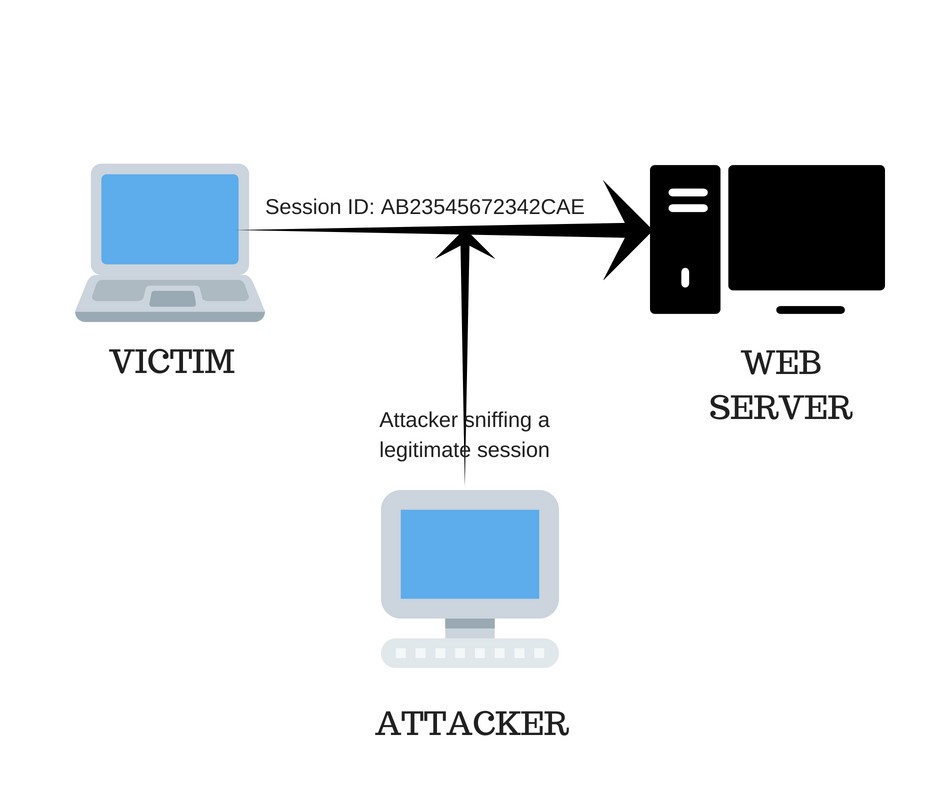
Attackers generally use images, cookies, scripts, and HTML to exploit users. Often they use session hijacking (sometimes also referred to as cookie hijacking), which is a man-in-the-middle attack that allows an attacker to insert commands into an active communication between two nodes by impersonating one of the authenticated users. They generally use sniffers to grab the data while it is being transferred via the communication line.
Almost every device on a network, (e.g., your computer or your router) is at a risk if you visit unsecure HTTP pages.
How HTTPS Works
Now that you have an idea of what HTTPS is and why it is important, let's take a deep dive into how it works.
First, let's define a few key terms:
- Digital certificate: a digital certificate, also known as a public key certificate or identity certificate, is an attachment to an electronic message that is used to verify the identity of the sender, as well as provide the receiver with a way to encode their reply. This certificate is issued by a Certifying Authority (CA), which retains the applicant's public key, along with other identification details. The public key of the CA is openly available on the internet.
- Digital signature: A digital signature is a means of ensuring that the contents of the message of an online document have not been tampered with during transmission.
- Symmetric encryption:In symmetric encryption, the same key is used for both the encryption and the decryption of the data. Both the sender and the receiver need to have the shared key in order to encrypt and decrypt the messages that are exchanged between them.
- Asymmetric encryption:In asymmetric encryption, a pair of keys (one to encrypt the data and the other to decrypt the encrypted the data) are used. The one used to encrypt the data is called the public key and the one used to decrypt the data is called the private key.
How is an SSL Connection Established?
First, an SSL connection between a client and a server is set up by a handshake. In this case, the browser is the client and the website is the server. A handshake is basically an agreement that establishes the details of how the connection between the two parties will proceed. It is done to ensure that the client connects to the right server, and works by employing a particular encryption algorithm. The handshake decides what cipher suite will be used, verifies the server, and ensures that a secure communication is in place before the actual transfer of data begins.
The handshake consists of three main phases – Hello, Certificate Exchange and Key Exchange. Let's discuss each phase one by one.
1. Hello – The process begins with the client sending a ClientHello message to the server. This message gives the server all the instructions that are necessary for it to connect to the client via SSL. In a similar manner, the server sends a ServerHello message containing the information required by the client. In addition, the ServerHello message also contains vital information regarding the client's preferences for the version of SSL that will be used.
2. Certificate Exchange – To prove its identity to a client, the server uses its SSL certificate, which contains information such as the name of the owner, the property it is attached to (e.g., its domain), the certificate’s public key, the digital signature, and information about the certificate’s validity dates. Certain sensitive applications also require the client to send a certificate to the server to prove its identity.
3. Key Exchange – The client and server exchange random numbers, as well as a special number called a Pre-Master Secret. Then the client and the server create their shared secret key, called the Master Secret. This is done by combining these numbers with some additional information. The client and the server then use the Master Secret to generate the write message authentication code (MAC) secret and the write key. The write MAC secret is used for hashing and the write key is the session key used for encryption.
The key that is required for the asymmetric algorithm is generated by the client. The key then encrypts it using the server's public key and an algorithm that was decided during the Hello phase. This encrypted key is sent to the server, which decrypts it using its own private key. Thus, a successful connection is established, and both the parties are assured that they are communicating with the right user. The HTTP requests that are in the plaintext format are thus encrypted and sent over the network. Only the receiving party has the key to decrypt this message. Therefore, man-in-the-middle attackers are unable to intercept the communication.
How is Trust Established?
Almost all browsers come loaded with trusted SSL certificates. These certificates are issued by Certificate Authorities (CAs) and are regulated by certain trustworthy organizations like Godaddy, Comodo, and NortonLIfeLock.
In order to establish a secure connection, the public key is distributed as part of the certificate. In contrast, the private key is kept secret. This pair of asymmetric keys is then used by both parties to encrypt and decrypt the data. The symmetric key is encrypted by clients by using the server's public key, whereas it is decrypted by the server using its private key. Alternatively, a legal authority can sign a certificate and encrypt its contents by using their private key. Now, this newly generated ciphertext is attached to the certificate as a digital signature. Using the authority's public key, anyone can easily decrypt the signature and verify it with the expected decrypted value. However, it should be noted that only a certified authority can actually encrypt content using the private key. In other words, a valid signature can only be generated by an authority.
To Stay Secure the SSL Protocol Needs Constant Updates
Even though it has way more security benefits than HTTP, HTTPS is not wholly secure. The SSL protocol needs to be constantly upgraded as newer and newer types of attacks get discovered. Here are some attacks that can occur while using older versions of SSL:
- In October 2004, the Padding Oracle On Downgraded Legacy Encryption (POODLE) attack was created to exploit the vulnerabilities in SSL v3.0. While initiating the handshake, the client sends the list of supported SSL versions. During this step, a man-in-the-middle attacker impersonates the server until the client agrees to downgrade the connection to the less secure SSL 3.0. Now, since communication between the client and the server is based on a vulnerable version of SSL, the hacker can easily perform the POODLE attack.
- In September 2011, the Browser Exploit Against SSL/TLS attack (BEAST) was published. This attack affects both SSL 3.0 and TLS (Transport Layer Security) 1.0. The BEAST attack is a man-in-the-middle attack performed on the client side. Because of the vulnerability in the implementation of the Cipher Block Chaining (CBC) mode in TLS 1.0, the attacker can perform a chosen plaintext attack and decrypt the data exchanged between the two parties.
Despite these flaws, however, HTTPS is still one of the most convenient and secure ways to transmit data over a network without worrying about others seeing your messages.





Please, comment on how to improve this article. Your feedback matters!