What Is Onion Over VPN? Is It Safe to Set Up and Use in 2024?
- What Is Onion Over VPN and How Does It Work
- Benefits of Onion Over VPN
- Drawbacks of Onion Over VPN
- Quick Guide: How to Use Onion Over VPN in 3 Easy Steps
- Best VPNs for the Onion Over VPN Setup in 2024
- ExpressVPN — Best Overall VPN for Safe and Fast Onion Over VPN Browsing
- CyberGhost — Quarterly Transparency Reports to Prove Your Data Is Safe
- NordVPN — Dedicated Onion Over VPN Servers for Fast and Convenient Connections
- Safety Tips and Best Practices for Using Onion Over VPN
- FAQs on Onion Over VPN
- Use Onion Over VPN Safely in Minutes
Despite Tor's anonymization capabilities, it still leaves room for certain privacy issues. For instance, your ISP can see you're using Tor, which can attract unwanted attention. Onion over VPN is a method that combines the privacy benefits of The Onion Router (Tor) and the security offered by Virtual Private Network (VPN). However, finding a reliable VPN to pair with Tor can be frustrating due to the many choices.
In order to alleviate these concerns, my team and I tested over 50 VPNs, focusing on relevant features like security, privacy, compatibility with Tor, and overall performance. Additionally, this guide will provide a comprehensive understanding of how Onion over VPN works, outlining its advantages and limitations.
My top recommendation for an Onion over VPN setup is ExpressVPN. Its excellent security features (including military-grade encryption and an audited no-logs policy), seamless compatibility with Tor, and impressive speeds make it stand out. Better yet, you can try ExpressVPN without risk as it’s backed by a 30-day money-back guarantee. Getting a refund is hassle-free if you don’t like the service. Editors' Note: Expressvpn and this site are in the same ownership group.
What Is Onion Over VPN and How Does It Work
Onion over VPN (also known as Tor over VPN) has emerged as a popular technique to protect your online data from snoops. It combines the privacy and anonymity of the Tor network with VPN encryption. This setup aims to provide an additional layer of privacy and security.
An Onion over VPN configuration requires only 3 components: a stable internet connection, a VPN service, and the Tor Browser or an alternative method for accessing the Tor network. When you use Onion over VPN, your internet traffic goes through two layers of encryption. First, a VPN encrypts your data and hides your IP address. Then, the Tor network encrypts your traffic in multiple layers as it passes through different Tor nodes. This double encryption makes it extremely difficult for anyone to monitor your online activities or trace your identity.
Here's how to use Onion Over VPN and how it works step-by-step:
- Connect to the VPN server using the VPN client or app provided by your VPN service.
- The VPN server encrypts your internet traffic and assigns you a new IP address.
- Open the Tor browser on your device.
- When you access websites or online services through the Tor browser, your internet traffic is first routed through the VPN server.
- From the VPN server, the encrypted traffic enters the Tor network (the first node is the relay node).
- Within the Tor network, your data gets encrypted in multiple layers (onion routing) and is relayed through several Tor nodes (guard and middle).
- After passing through the last Tor node (exit node), your data finally reaches the destination server on the internet.
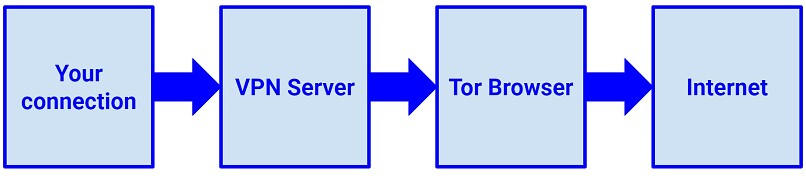 Onion over VPN routes your connection through multiple security tunnels
Onion over VPN routes your connection through multiple security tunnels
By using Onion over VPN, your traffic appears to originate from the VPN server rather than directly from the Tor network. This can help bypass certain website restrictions that target Tor users. Additionally, this VPN-Tor hybrid protects against potential risks associated with malicious exit nodes within the Onion network.
It's important to use reputable VPN services when employing Onion Over VPN for the best protection. While Onion over VPN offers improved privacy, it may reduce internet speeds due to the multiple encryption and routing processes involved. I recommend choosing a VPN that offers excellent speeds, like ExpressVPN.
It’s also advised to use Onion over VPN when anonymity is crucial, direct access to the Tor network isn’t possible, or if you're a journalist, whistleblower, or activist needing enhanced online privacy. However, it’s better to avoid it for casual internet browsing, accessing identity-linked websites like social media, or when browsing speed is a primary concern.
Benefits of Onion Over VPN
Onion over VPN offers several benefits for users seeking enhanced online privacy and security. Here are some of its main advantages:
- Enhanced privacy. The multi-layered routing through both VPN servers and the Tor network creates a complex path for data, increasing security against surveillance and interception. For example, journalists, human rights activists, and researchers in authoritarian countries face imprisonment risks due to their online activities, and they can use Onion over VPN for extra security.
- Access to the Tor network in restricted regions. A VPN can help bypass local restrictions or censorship, allowing access to the Tor network even in countries where it is restricted or monitored.
- Protection on public WiFi. Unsecured public hotspots often lack strong encryption, making your personal data vulnerable to interception. Onion over VPN encrypts internet traffic, making it much more difficult for hackers on the same network to intercept and understand your data.
- Protection against traffic correlation attacks. By first routing traffic through a VPN, the likelihood of attackers correlating traffic entering and exiting the Tor network to de-anonymize users is reduced.
- No direct connection to Tor entry nodes. Since the connection to the Tor network is made through the VPN, your ISP can't see that you're using Tor, adding an extra layer of privacy.
Drawbacks of Onion Over VPN
While Onion over VPN offers numerous benefits, it's important to consider some potential disadvantages:
- Reduced internet speed. Using Onion over VPN can slow down your internet speed because of the multiple encryption layers and routing through the Tor network. How much it affects your performance depends on factors like the VPN provider, server location, and overall network conditions. It’s not recommended for gaming or streaming.
- Possible VPN logging. Using Onion over VPN might not offer complete anonymity depending on the VPN's logging policy. Some VPN providers may keep logs of users' online activities, potentially compromising user privacy if the logs are accessed or shared with authorities or third parties. It's essential to select a reliable VPN provider with an audited no-logs policy.
- Limited Tor network exit nodes. The Tor network relies on a limited number of volunteer-operated exit nodes, leading to potential speed slowdowns and congestion during peak times. This limitation may also result in geographic restrictions and limited access to certain websites.
- Malicious exit nodes. Nodes are volunteer-operated, which can be risky since some might be insecure or malicious, potentially compromising data security (if run by hackers). Using HTTP with Onion over VPN exposes your traffic between the exit node and the web server, making it visible to potentially malicious exit nodes. In contrast, HTTPS encrypts your traffic even after it leaves the exit node.
- Complex setup. Setting up Onion over VPN, which involves configuring both the VPN and Tor clients, can be more complicated than using a standard VPN or the Tor browser separately. Nonetheless, it's manageable and not excessively difficult. You also might have to adjust the Tor browser's network settings to use the existing VPN connection for its traffic.
- Limited access to some services. Due to the multiple relays and encryption involved, some websites and services might restrict access to users utilizing Onion over VPN. These services might interpret the multi-hop traffic as suspicious behavior and block or limit access.
- Changing your IP address in the Tor network isn’t user-controlled. Tor randomly selects server paths, including the exit node that determines your IP. This means that obtaining a specific exit IP address depends largely on chance. Each time you request a new circuit in Tor, the network randomly chooses a new path, making it challenging to control or predict the exit IP address.
Quick Guide: How to Use Onion Over VPN in 3 Easy Steps
- Download a VPN. I recommend ExpressVPN because of its impressive speeds, robust privacy features, and Tor compatibility. You can try ExpressVPN risk-free (it’s backed by a 30-day money-back policy).
- Download and install the Tor browser. You can download it from the official Tor Project website, if you don’t have it installed yet.
- Connect to a VPN server and launch the Tor browser. Open your VPN app and choose a server that allows Tor traffic. Now you can enjoy secure browsing of.onion sites via the Tor browser.
Best VPNs for the Onion Over VPN Setup in 2024
1. ExpressVPN — Best Overall VPN for Safe and Fast Onion Over VPN Browsing

Tested May 2024
| Best Feature | Lightway protocol provides exceptional speeds, ensuring fast Tor browsing |
| Average Speed | 84Mbps (a 16% drop from my base connection) |
| Security and Privacy | Military-grade encryption to keep your online activity private |
| Dark Web Mirror Website | Yes |
ExpressVPN's impressive speeds are ideal for Onion over VPN usage. Its Lightway protocol is designed to be lightweight and reduce latency, enhancing connection speeds and overall performance — crucial when dealing with the additional encryption layers of Tor. The results were notable when testing ExpressVPN servers. Even with the extra encryption from Tor, browsing.onion websites was seamless, with no noticeable delays.
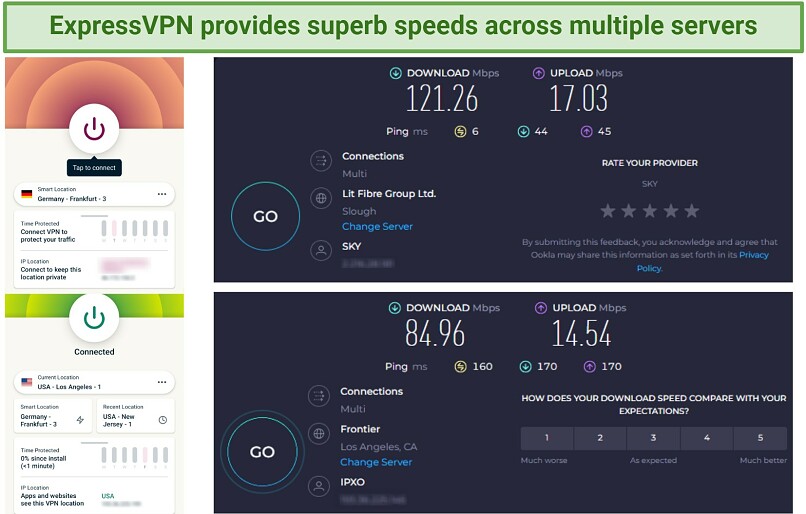 Using ExpressVPN servers with Tor let me browse the web without interruptions
Using ExpressVPN servers with Tor let me browse the web without interruptions
Military-grade encryption scrambles your traffic while you browse through Tor. Besides, Network Lock (a kill switch) ensures no data leaks to the dark web if your VPN connection unexpectedly drops. The VPN also features solid leak protection, keeping your online identity under wraps during Onion over VPN sessions.
ExpressVPN strictly follows a no-logs policy, verified for full compliance by multiple independent firms, including KPMG and PwC. Thanks to RAM-only servers, no data is ever stored on hard drives. Being located in the British Virgin Islands, outside the 5/9/14 Eyes Alliances (intelligence-sharing agreements between several countries), finally ensures that the VPN doesn’t store and share your data with any third party.
Even though the VPN’s monthly plans come with a higher price tag, ExpressVPN frequently provides discounts and special offers to reduce overall expenses. Opting for the 12-month plan, I received 49% off and 3 extra months for free, for a final price of just $6.67/month. Additionally, ExpressVPN is backed by a 30-day money-back guarantee, so you can try it with confidence.
Useful Features
- All servers are compatible with Tor. A vast network of 3,000 servers across 105 countries provides more entry points to the Tor network when using Onion over VPN. This makes it more challenging for adversaries to trace a user's traffic back to its source.
- Server obfuscation. ExpressVPN automatically obfuscates your connection to counter Deep Packet Inspection (DPI). In some countries or organizations, DPI is used to detect Tor usage. This helps to safeguard your browsing activities and maintain your privacy by making it difficult for snoops to identify your Tor usage.
- Easy-to-use apps. ExpressVPN's apps are designed with user-friendliness in mind, making the setup process for Onion over VPN more straightforward. The apps typically provide clear instructions and options to enable Onion over VPN functionality without requiring advanced technical knowledge.
- Split tunneling. A particularly beneficial feature, split tunneling, lets you select which apps use the VPN and which don’t. This means you can direct your Tor browser through the VPN while keeping other applications on your regular internet, optimizing both security and speed.
2. CyberGhost — Quarterly Transparency Reports to Prove Your Data Is Safe
| Best Feature | Quarterly transparency reports show your data isn’t shared with any authorities |
| Average Speed | 79Mbps (a 21% drop from my base connection) |
| Security and Privacy | A no-logs policy ensures that CyberGhost doesn’t keep records of your online activities |
| Dark Web Mirror Website | No |
CyberGhost showcases its commitment to privacy by publishing quarterly transparency reports that detail all legal requests it receives for user data and its response. As the VPN doesn’t log any data, it’s unable to comply with such requests. It also comes with highly secure NoSpy servers based in Romania. CyberGhost owns and maintains these first-hand (no third-party has access), ensuring that your online activity remains safe from monitoring.
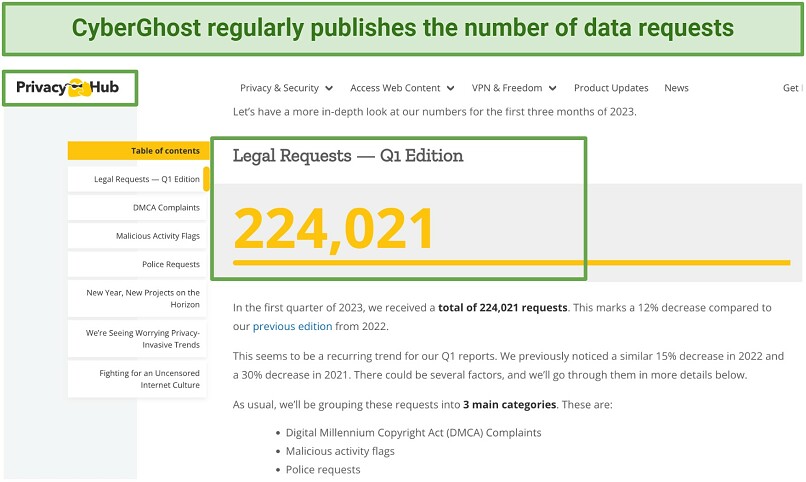 You can read the reports on CyberGhost’s Privacy Hub blog
You can read the reports on CyberGhost’s Privacy Hub blog
Your Tor browsing activity is also secured with AES 256-bit encryption and a kill switch. I didn't record any IP/DNS leaks during my tests, so my real IP address wasn’t revealed. Plus, Content Blocker helps prevent access to potentially malicious websites. It can also speed up your internet browsing experience by preventing the loading of unnecessary elements like ads and trackers.
Similar to ExpressVPN, CyberGhost lets you use a Tor over VPN configuration. My speeds were satisfactory, and I encountered no difficulties while accessing content on onion websites.
A minor gripe is that monthly subscriptions are expensive and offer shorter refund periods (only 14 days). But if you opt for a long-term plan, you can get CyberGhost for as low as $2.19/month. These plans also provide 45-day money-back guarantees that allow you to test the VPN for free.
Useful Features
- An audited no-logs policy. This important feature means CyberGhost doesn't store or track your online activities, including browsing history, traffic data, or DNS queries. Combined with Onion over VPN, this adds an extra layer of privacy, as neither the VPN provider nor the Tor network keeps track of your internet usage, greatly enhancing your online anonymity and privacy.
- Smart rules. CyberGhost's Smart rules enable automatic VPN connections with specific apps, enhancing privacy for Onion over VPN browsing by ensuring consistent, user-defined protection without manual setup each time.
- Perfect forward secrecy. CyberGhost adds a layer of security to the Onion over VPN setup by ensuring each session has unique encryption keys. This means that even if a key is compromised, other sessions remain secure, crucial for maintaining privacy and security on the Tor network.
3. NordVPN — Dedicated Onion Over VPN Servers for Fast and Convenient Connections
| Best Feature | Specialty servers to quickly set up an Onion over VPN connection |
| Average Speed | 77Mbps (a 23% drop from my base connection) |
| Security and Privacy | NordVPN’s HQ is in privacy-haven Panama, where there are no data retention laws |
| Dark Web Mirror Website | No |
NordVPN offers dedicated Onion Over VPN servers, which are specifically optimized for routing traffic through the Tor network. This means you can access the Tor network with increased privacy and without needing a separate Tor browser. However, some browsers (like Firefox) need a special setup for this to work.
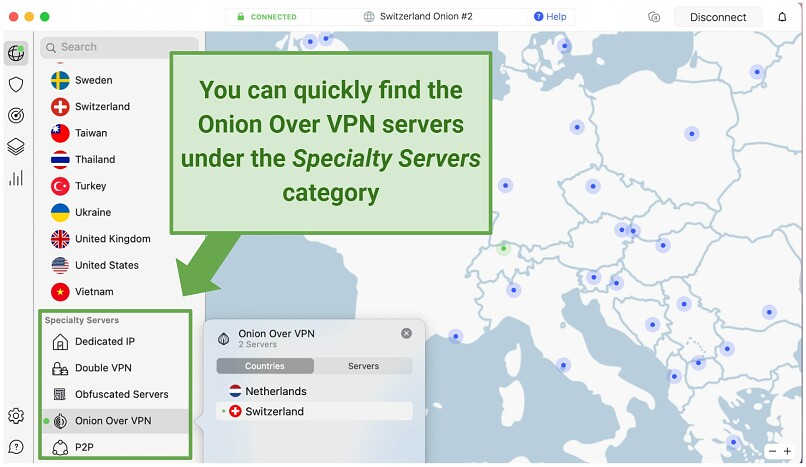 I recommend the Switzerland-based Onion over VPN server as it’s outside the 14 Eyes Alliances
I recommend the Switzerland-based Onion over VPN server as it’s outside the 14 Eyes Alliances
While not as fast as ExpressVPN, NordVPN is suitably fast for browsing.onion domains. During my tests, its proprietary NordLynx protocol provided the fastest speeds. Using it in combination with Tor, I experienced faster and more efficient network performance overall.
One drawback is that NordVPN might share data with foreign governments if legally required and in accordance with international norms. Yet, the likelihood of NordVPN identifying and providing specific personal details is extremely low. This is due to a policy of not logging browsing history, traffic information, or IP addresses, ensuring a high degree of anonymity even when requests for data are made.
You can get NordVPN for just $5.99/month. Opting for the 2-year plan offers the best value for your money in the long run. Thanks to a 30-day money-back guarantee, it’s also possible to try NordVPN for free.
Useful Features
- Dark Web Monitor. This feature actively scans the dark web for any leaks associated with the email address you used to sign up for NordVPN. In the event of a leak, you will be promptly notified, allowing you to take immediate action to secure your accounts.
- Double VPN. For maximum security, NordVPN also offers a Double VPN mode. This changes your IP address twice (in addition to the changes provided by the Tor network) and also applies two layers of encryption to your connection. However, it's important to note that this process significantly impacts your internet speed.
Editors' Note: Intego, Private Internet Access, Cyberghost and Expressvpn are owned by Kape Technologies, our parent company.
Safety Tips and Best Practices for Using Onion Over VPN
When using Onion Over VPN for enhanced privacy and security, it's important to follow certain safety measures. These practices help protect against common online threats and ensure a safer browsing experience, especially when venturing into less secure areas of the internet, like the dark web. Here are key guidelines to follow:
- Choose a reliable VPN. Opt for a VPN with robust security features like military-grade encryption, a kill switch, strong leak protection, and a strict no-logs policy to ensure maximum privacy.
- Install antivirus software. The dark web can contain harmful links and content. A good antivirus is essential as VPNs don't guard against viruses.
- Adjust the Tor browser security settings. The Tor Browser offers three security levels: Standard (default, enabling all site features), Safer (disables JavaScript on non-HTTPS sites and restricts some fonts, symbols, and media autoplay), and Safest (the most restrictive, blocking JavaScript on all sites, allowing only images and fonts).
- Safely navigate.onion sites. Stick to reputable.onion sites and avoid HTTP sites, which lack encryption, exposing you to potential surveillance.
- Guard personal information. Use pseudonyms and secure email services like ProtonMail for interactions on the dark web to prevent data theft.
- Use cryptocurrencies for transactions. If purchasing on the dark web (not recommended), use cryptocurrencies for enhanced privacy and to avoid exposing credit/debit card information.
FAQs on Onion Over VPN
Is it legal to use Onion over VPN?
The legality of using Onion over VPN depends on the laws of your country. In most jurisdictions, using Onion over VPN is legal as it combines legitimate online privacy and anonymity tools. However, engaging in illegal activities while using Onion over VPN remains unlawful. Remember, VPNs are designed to safeguard your online data, not to facilitate illicit actions.
Several countries have restrictions or outright bans on accessing the Tor Network. Notable among these are China, Russia, and Iran. Additionally, countries like Saudi Arabia and the UAE impose restrictions on VPNs, which can affect the Onion over VPN setup. Ensure you use Onion over VPN legally and ethically, adhering to local laws.
What’s the difference between Onion over VPN and VPN over Tor?
They are different approaches to combining the features of a VPN and the Tor network. Onion over VPN involves connecting to a VPN and then to the Tor network. VPN over Tor involves connecting to the Tor network and then to a VPN. Both methods are designed to add an extra layer of privacy and anonymity, but they function differently and offer different benefits.
- Onion over VPN. In this configuration, your ISP won't know you're using the Tor network because it only sees the encrypted VPN traffic. Also, the Tor entry node will only see the IP address of the VPN server, not your actual IP. However, the main downside to Onion Over VPN is that the VPN provider can see that you're using Tor, and your real IP can be exposed if the VPN connection drops unexpectedly (unless you have a kill switch feature activated).
- VPN over Tor. In this configuration, the VPN server only sees the IP address of the Tor exit node, not your actual IP. This method can also allow you to access services that block Tor exit nodes, as these services will only see the IP of the VPN server. However, a significant downside to VPN over Tor is that your ISP can see that you're using the Tor network, which may attract scrutiny in some countries. Also, setting up VPN over Tor is complex and typically requires support from the VPN provider, limiting VPN options since not all support this setup. It's only recommended for technically skilled users, as incorrect configuration can compromise your data and security.
Is Double VPN better than Onion over VPN?
Whether Double VPN is better than Onion over VPN depends on the specific needs and concerns of the user. Double VPN offers enhanced security by routing your internet traffic through two different VPN servers, adding an extra layer of encryption and IP address masking.
On the other hand, Onion over VPN combines the security features of a VPN with the anonymity of the Tor network. This can provide better privacy, especially against network surveillance, but potentially at the cost of slower speeds due to the Tor network's architecture.
For users prioritizing maximum privacy, especially in high-surveillance environments, Onion over VPN might be more suitable. However, for those who seek a balance between security and speed, Double VPN could be the better choice.
Use Onion Over VPN Safely in Minutes
Onion over VPN combines VPN and Tor for enhanced privacy and security. It provides encryption, the hiding of your IP address, and access to Tor resources. When implemented correctly with trusted providers, it offers a secure browsing experience. However, it's important to note that not every VPN is suitable for Tor networks. Some may lack the necessary security features while others might not be as fast, making them an unreliable option for Onion over VPN setups.
For the best Onion over VPN experience, I recommend ExpressVPN. It has excellent speeds and powerful security features, providing seamless and safe Tor browsing. It's also backed by a 30-day money-back guarantee, meaning you can test ExpressVPN without risk. Getting a refund is hassle-free if you’re not entirely impressed with the service.
To summarize, these are the best VPNs for the onion over VPN setup...
Your data is exposed to the websites you visit!
Your IP Address:
Your Location:
Your Internet Provider:
The information above can be used to track you, target you for ads, and monitor what you do online.
VPNs can help you hide this information from websites so that you are protected at all times. We recommend ExpressVPN — the #1 VPN out of over 350 providers we've tested. It has military-grade encryption and privacy features that will ensure your digital security, plus — it's currently offering 49% off.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.



Please, comment on how to improve this article. Your feedback matters!