Wombat Security Technologies – Security Training to Change Behavior
- Please tell me a little bit about yourself and your background.
- What is the story behind the company’s name “wombat?”
- You offer several different types of educational and assessment products based on the Wombat Security Education Platform that your team developed. Please describe these different products.
- Which product is the most popular?
- How do you define your target audience?
- What is your pricing model? Can smaller companies afford your products?
- As the Chief Architect, what are some of your biggest challenges in the development of your platform?
- What methods do you normally use to attract and engage with new customers?
- How many active customers do you have today? Where are they mainly located?
- How would you describe your current typical customer?
- Who are some of your biggest customers?
- How do you see your products as different from other training products?
- What are your top three security tips?
- How do you see the security training market evolving in the upcoming years?
- What are some of the future plans for Wombat?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
- Is there anything else you would like to share with our readers?
While there is no question in anyone’s mind that companies must provide increased amount of security training to their employees, it is not always obvious what is the best way to do that. In this interview, Kurt Wescoe, the Chief Architect at Wombat Security Technologies, explains his company’s specific approach to security training. Their methodology begins with a skills assessment of end users and includes benchmark measurements of knowledge and skills obtained after the training.
Kurt also shares with us his company’s biggest challenge in developing and maintaining their training platform, as well as what he sees in the future for security training programs.
Please tell me a little bit about yourself and your background.
I have been with Wombat for almost ten years. Before that, I was teaching at Carnegie Mellon University together with some of the company’s founders. What I love about Wombat is that we use the best of science, psychology, and technology to address the problem of security awareness and training.
What is the story behind the company’s name “wombat?”
Wombats are short-legged, muscular animals that are native to Australia. They are intelligent, have thick skin, and are particularly aggressive when protecting their family against predators.
The Wombat’s characteristics represented the same intelligent and fiercely defensive posture against cyber security threats that we want to provide for our customers.
You offer several different types of educational and assessment products based on the Wombat Security Education Platform that your team developed. Please describe these different products.
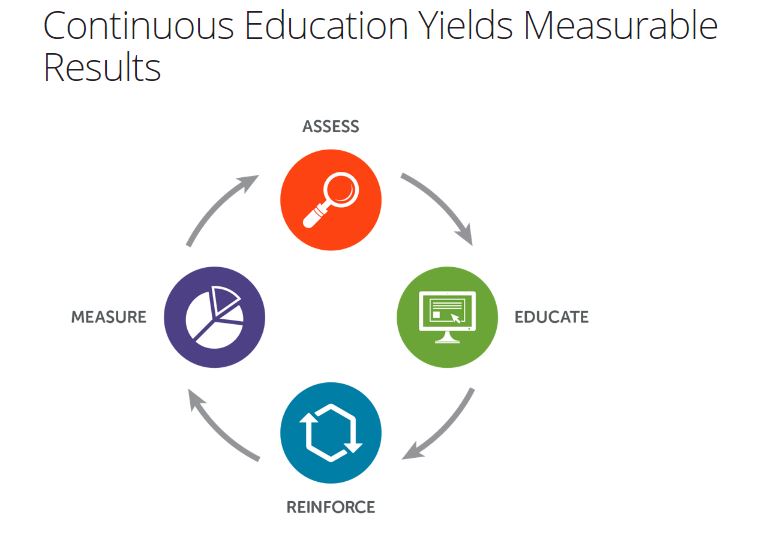
Our products fall into three main categories:
- Assessments –Live/contextual simulated attacks to evaluate what knowledge and skills employees do or do not have.
- Training – Continuous educational program where specific training modules are assigned to individual users every quarter.
- Awareness materials – Staying in touch and reminding users on a regular, ongoing basis.
Which product is the most popular?
Our most popular offering is our Anti-Phishing Training Suite. The suite offers a combination of ThreatSim® simulated phishing attacks, which allows companies to assess how susceptible their employees are to phishing and spear phishing attacks, along with targeted interactive training modules that help to educate employees on how not to fall for a phishing attack. The offering is rounded out with our PhishAlarm® email reporting tool that allows employees to apply their phishing knowledge and report a suspected phishing email with a single mouse click from their email inbox.
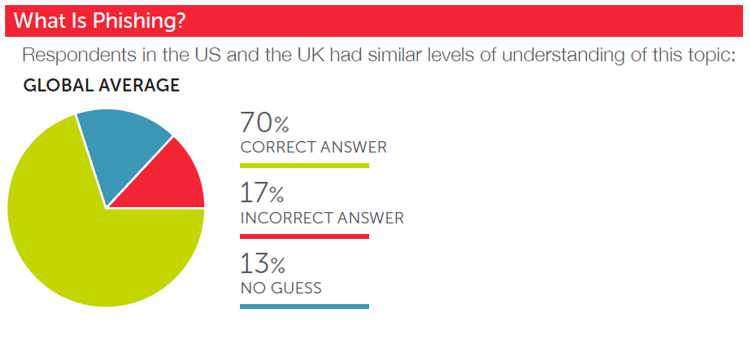
How do you define your target audience?
Our target audience is primarily medium and large sized organizations. Many of the features in our system address the needs of larger organizations, such as enterprise integration and customization.
What is your pricing model? Can smaller companies afford your products?
Wombat continues to add items to our product offerings based on market needs. Organizations of many different sizes – small or large – can find a program that not only fits their budget but also effectively educates their unique end users.
As the Chief Architect, what are some of your biggest challenges in the development of your platform?
Our biggest challenge is the content development process. The content that we deliver must be both accurate and engaging for the user. We also translate it into multiple different languages. It can be quite a challenge to find the right people who can correctly address and balance all of those needs. They must have gaming skills, creativity, and strong writing skills.
A big difference between our solutions and other training programs is that we tie everything back to skills, not just knowledge. That means that in addition to presenting information, we need to be able to measure and assess the skills actually acquired.
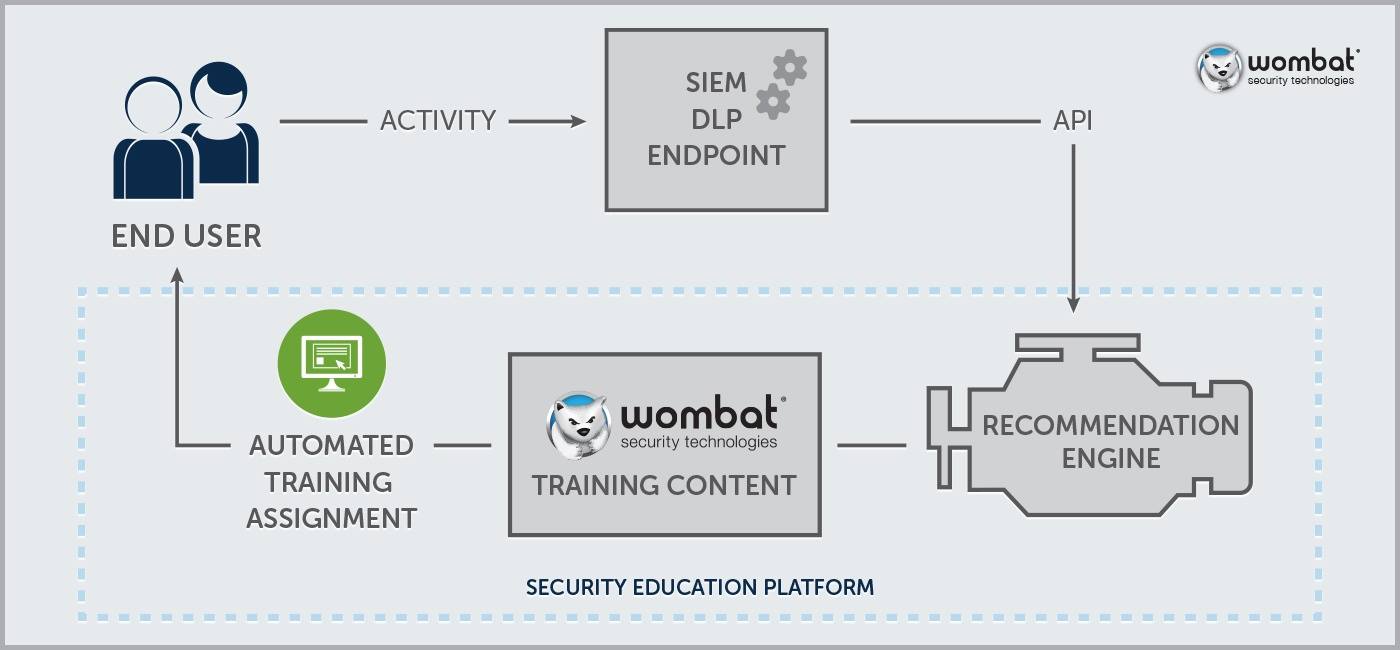
What methods do you normally use to attract and engage with new customers?
One of the things we do to attract and engage with customers (potential, new, and existing) is our annual Wombat Wisdom Conference. This will be our third consecutive year hosting this conference. It is open to both customers and non-customers and offers insights from the Wombat team, current customers and outside experts about how to run an effective security awareness and training program.
We invite Infosec professionals to join us for two days to learn from some of the brightest minds in security, who will offer ideas and actionable concepts around the continuous improvement of cyber-security education programs. Last year, our audience included more than 150 security awareness practitioners.
Another thing we do to show our commitment to our customers is to assign a Customer Success Manager to each account. We understand that developing and executing an effective security awareness and training program can be a daunting task for an organization, whether new or experienced. Our Customer Success Managers are long-time industry professionals who go beyond teaching customers how to use our platform.
They kick off with an introductory success strategy call with the program administrators to discuss program goals and best practices; they follow that with routine check-in meetings and work closely with administrators to develop and execute effective and measurable security awareness training programs. Our Customer Success Managers also work closely with our product management, development, and support teams to make sure that they are maximizing the latest and greatest Wombat solutions and strategies for the customers they work with.
Finally, our online Wombat Wisdom Community allows our customers to connect and communicate with one another, view Knowledgebase articles and documentation from our support team, keep up-to-date with product updates, and share ideas for new product development. This forum provides an additional line of communication to the Wombat Security team.

How many active customers do you have today? Where are they mainly located?
We have thousands of customers, many of which have headquarters in the US, with employees in countries all over the world. We have been growing our customer base in other regions due to the quality of our international features.
How would you describe your current typical customer?
I do not think we have a "typical" customer per se. We provide value to organizations from a very diverse range of industries, and each enterprise has unique awareness and training needs.
For example, we work with several organizations in the finance and professional services industries, such as law and accounting, but also have many customers in retail, hospitality and technology. And as I mentioned before, we also work with many different sizes of organizations, ranging from large consumer goods companies to smaller businesses with fewer employees. With different business models come different priorities from a cybersecurity education perspective. This is why we believe that a security training program must be adaptable to many types and cultures of companies to be most effective. In the end, hackers do not care if you are a small mom-and-pop or a global corporation, which is why we offer training solutions for all types of customers.
Who are some of your biggest customers?
We know that privacy is very important to our security audience, so we do not name customers without their explicit consent. We provide security awareness and training solutions to some of the biggest and well-known brands in the world.
How do you see your products as different from other training products?
Most of our competitors focus on only one single piece of what we do.
Our approach is far more integrated. As I mentioned, we tie everything back to measuring skills and awareness, both before and after going through specific training modules. I do not think any other training companies use extensive assessments like we do. We also have technologies in place to categorize our content and to auto-enroll employees for the training modules that they need. This allows the training program to get a level of personalization no one else in the market currently has since the training you receive is driven by your individual needs.
What are your top three security tips?
- Be aware that phishing attacks and social engineering attacks are the easiest ways into an organization.
- Develop situational and contextual awareness to notice if something does not look right.
- Organizations need to be thinking about how they can better leverage end users as part of their security plan.
How do you see the security training market evolving in the upcoming years?
I think that security training will become more and more personalized to the individual user. The security landscape is constantly expanding and changing, which means that users must be aware of many different topics and acquire many different skill sets. The training plan for an employee must include that which is most relevant to them right now, based on their current job function, knowledge, and skills.
What are some of the future plans for Wombat?
One thing we are looking to do is to be more integrated into existing security systems and tools. Traditionally incident response has been about technical solutions and cleaning up which is important, but is only addressing half the problem. We can clean up the mess, but if the user that created it does not understand what they should have done differently then they’re likely going to keep making the same mistake. I think this represents a great opportunity where we can make education part of the response process and have a more holistic approach that will ultimately be more effective.
You can also expect to see from us more personalization of the content being taught and customization of the learning experience to the end users’ needs. The decisions we make every day are indicators of our comprehension, so when we see someone making the same mistakes repeatedly, we need to be working to determine what they don’t understand and how to best educate them, rather than saying they “can’t be trained.” Ultimately, I believe the majority of users want to be secure and protect their company. It is our privilege to enable them to do that.
How many employees do you have today? Where are they located?
With a workforce numbering in the few hundreds, our company operates multiple offices across the United States, along with an additional office located in the United Kingdom.
How many hours a day do you normally work? What do you like to do when you are not working?
I work about 10 hours per day.
The five (5) parrots I welcomed into my life when I married my wife take up a lot of my free time. Interestingly, I end up leveraging with them the same behavioral training approaches I use at work - though typically not to train them to be more secure online. I’m also a big fan of BBQ and you can find me with my smoker and some ribs or a pork shoulder on many weekends.
Is there anything else you would like to share with our readers?
I just want to emphasize that it is critical that you define specific goals for your training programs, such as “reduce click rate on phishing attacks by 10%.” It’s very hard to make tangible progress if you don’t measure and you don’t prioritize.
Also – remember that training is an incremental process and that you need to provide training on a continual basis. Provide the training, measure the results, make incremental changes, and then repeat.




Please, comment on how to improve this article. Your feedback matters!