Apperian – Managing and Securing Corporate Mobile Apps
- Please tell me a little bit about yourself and your background.
- Your product is a mobile application management platform. That is a relatively new concept. What are its main components?
- Most security companies focus on restrictions – you focus on adoption.
- You say that all of your functionality is available without modifying any application code, because you wrap the original apps. However, I see that you do also provide a set of APIs. What are those APIs for?
- How do you define your market? Who is your specific target audience within that market?
- Whom do you see as your main competitors?
- How do you see your tools as different and/or better than theirs?
- What methods do you normally use to attract and engage with new customers?
- How many employees do you have today? Where are they located?
- How do you see mobile technologies and the apps market evolving in the coming years?
- Earlier this year Apperian was acquired by Arxan. What can you tell me about that?
- What are your future plans for Apperian?
- You are the also co-founder of the Boston TechJam – what exactly is that?
- You are quite involved with Boston startups in general – right?
- What general advice would you offer today’s startups?
- How many hours a day do you normally work? What do you like to do when you are not working?
"As the age of the workforce drops, employees expect all work-related functions and corporate information to be available on their phones or other mobile devices.” Perhaps more than anything else, this statement sums up the current state of corporate mobile computing today. However, as Mark Lorion, President and General Manager of Apperian, tells us, many users do not want their phones or other mobile devices to be controlled by their corporate IT department.
In order to address these seemingly contradictory challenges, Apperian takes a different approach to managing and securing corporate mobile applications. Rather than securing mobile devices, they secure mobile apps, and they do so without requiring modifications to the application’s code.
Please tell me a little bit about yourself and your background.
I spent most of my career in marketing and product management, eventually moving more into sales and all business functions. I have been with Apperian for over four years. Before that, I was Vice President of Marketing at a company called Spotfire, which was purchased by TIBCO. As a result of that acquisition, I continued to run Marketing for the Spotfire group and also took on leadership of several other marketing teams throughout TIBCO.
Your product is a mobile application management platform. That is a relatively new concept. What are its main components?
Our product is actually a combination MAM (Mobile Application Management) and security platform. Its purpose is to enable companies to distribute their enterprise mobile apps privately and securely.
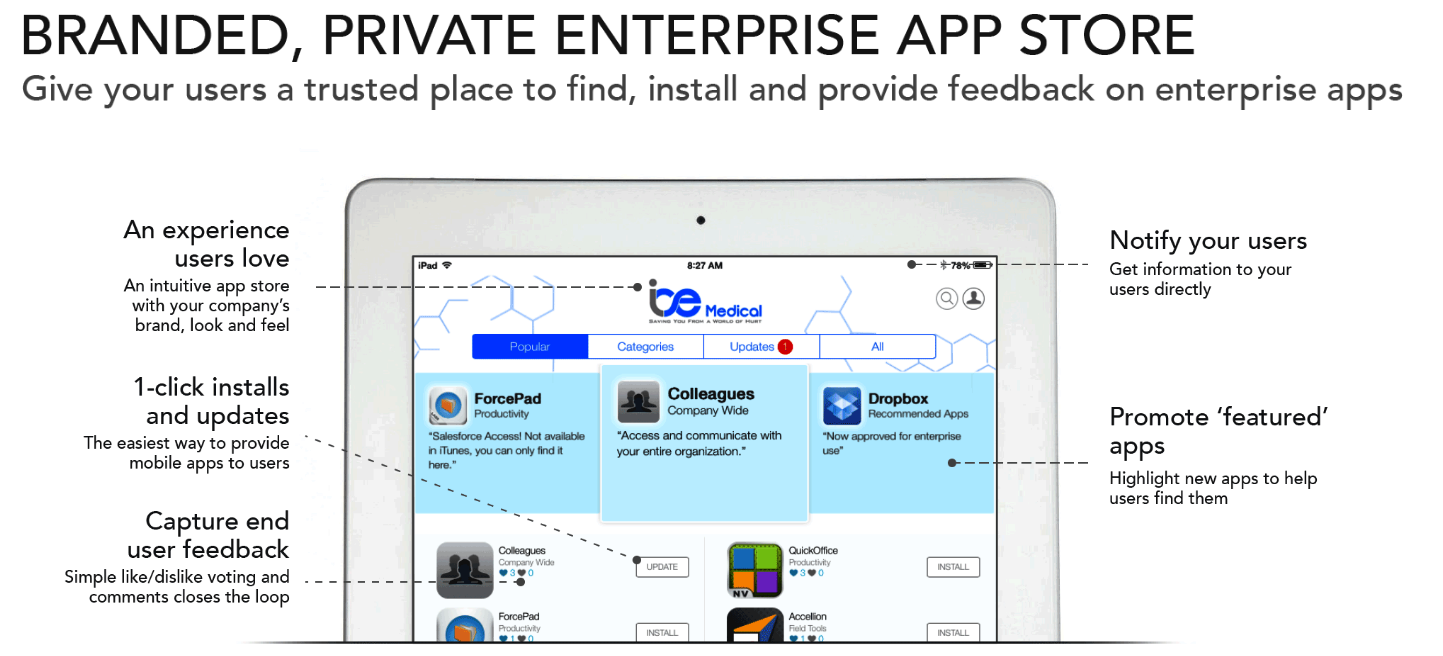
We provide companies with a branded and private enterprise app store for the custom apps they build for their employees and/or partners. Companies do not want their proprietary apps in the iTunes or Google Apps store. In addition, having these in-house apps in the public iTunes or Google Apps store would be confusing to customers, since these apps are not meant to be used by them.
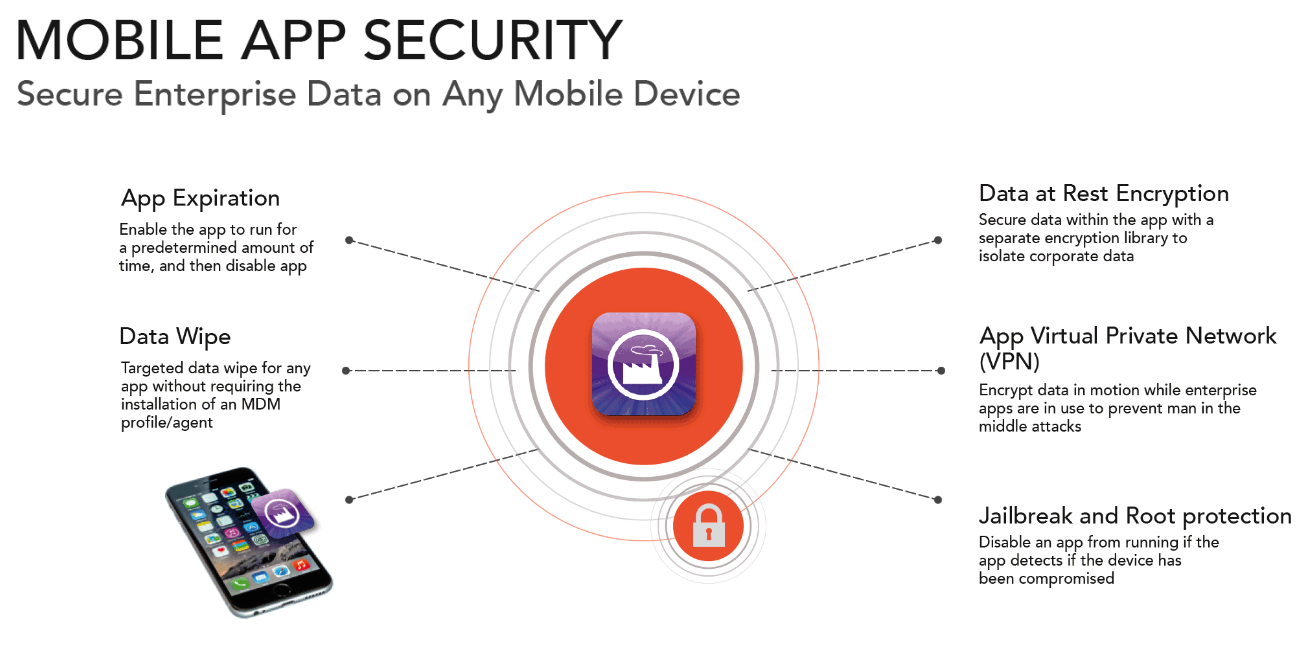
Our platform also includes a policy engine. For example, a centralized administrator can apply a variety of security and management policies to the company’s mobile apps. One such policy can enable an administrator to delete all the data on a particular enterprise app and on a specific user’s device if necessary, such as when they are terminated or resign.
Most security companies focus on restrictions – you focus on adoption.
That is absolutely correct. An IT department should not care if a user is using a pirated version of Angry Birds on their phone. However, they should be concerned about securing the specific apps that the company owns and about implementing controls and restrictions at the app level. Once those elements are in place, they should definitely promote and encourage the adoption of those apps.
Many employees/users do not like IT taking control of their devices. Our approach is to control and protect the company’s apps running on user devices. We secure apps, not devices.
You say that all of your functionality is available without modifying any application code, because you wrap the original apps. However, I see that you do also provide a set of APIs. What are those APIs for?
We apply security and management policies around each of the company’s apps. We apply the policies to a company’s app “binaries”, which are completed apps, via a wrapper-based approach and without requiring that the app developer modify the app’s code. This policy wrapper then communicates with the hosted Apperian platform for ongoing and centralized administration.
The APIs that we offer provide access to functionality within our hosted platform. This allows administrators to integrate our platform with other existing systems and processes. This might entail automatically publishing app builds from a common build management system, such as Jenkins, or integrating into a corporate reporting system for monitoring app usage and adoption.
How do you define your market? Who is your specific target audience within that market?
The companies that we target are usually larger companies with over $1 billion in revenues and several thousand employees. These companies typically have many mobile workers and many custom mobile apps.
Although we do have plenty of smaller companies using our platform, you can say that we mainly target the Global 2000 corporations. One example that I can talk about is the US TSA (Transportation Security Agency) which uses our platform to distribute their custom apps to all gate agents in US airports.
Key verticals for us include:
- Healthcare
- Financial Services
- Manufacturing
- Retail
- Public Sector / Government
In terms of the people within a given organization, we tend to target the owners of specific mobile apps within the enterprise, e.g. sales team enablement apps, working training apps, or field service apps. We also work with LOB (Line of Business) executives who have responsibility for mobile apps. They are the ones who feel the pain of distributing mobile apps to their users. In most cases, the IT department also gets involved, but in more of a supporting role.
Whom do you see as your main competitors?
Our main competitors are providers of device management or device-centric enterprise mobility management systems – although we have significantly different philosophical and technical approaches. As I mentioned previously, our approach is to manage and secure applications, not devices. In an environment where the IT department does have control over the devices and likely owns the mobile devices, then a device-centric approach might be just fine.
However, such an approach does not work well in a BYOD (Bring Your Own Device) setting or in settings where companies employ a lot of contractors, consultants, contracted workers, dealers or other workers who need access to the corporate apps.
How do you see your tools as different and/or better than theirs?
The Apperian platform stands out in three main areas:
- Security is applied at the individual app level. The app travels with the security controls so that it is protected even when running on non-managed devices and devices not under IT control.
- Application code does not need to be modified. The existing app is wrapped with the security and policy information, which enables faster onboarding of apps from a wider range of sources and developers
- Fully extensible platform via robust APIs. The Apperian platform is covered by an extensive API that enables administrators to tightly integrate with existing enterprise systems and processes.
What methods do you normally use to attract and engage with new customers?
We provide a lot of valuable content on our web site, so that potential customers are drawn to us as they are researching ways to securely distribute enterprise mobile apps. In addition to standard marketing and sales efforts, we also work with several resellers and business partners in specific market segments.
How many employees do you have today? Where are they located?
The corporation employees nearly 200 employees located around the world. We have R&D centers in Boston, San Francisco, and Europe. We have sales and support offices throughout the US, Europe, and we work with partners throughout Asia.

How do you see mobile technologies and the apps market evolving in the coming years?
More and more work is being done on mobile devices instead of on desktop PCs or even laptops. As the age of the workforce drops, employees expect all work-related functions and corporate information to be available on their phones, tablets, and other mobile devices.
Mobile apps today are more complex and sophisticated than in the past and they are increasingly integrating with more back-end applications.
Earlier this year Apperian was acquired by Arxan. What can you tell me about that?
The official announcement of that acquisition was in January of this year [2017]. Arxan is an application protection company that puts security into apps (mainly consumer apps) and was looking to get more involved in the enterprise space. What started as a business development or partnership discussion evolved into a win-win acquisition.
Arxan recognizes that Apperian is an established brand with a proven technology. I am happy to say we are continuing to lead Apperian from our headquarters location in Boston and we are also operating with autonomy to pursue and support our customers and innovate our platform while also taking advantage of synergies.
What are your future plans for Apperian?
In the near future, we are going to focus on three main areas:
- Expand the available policies and security options available in the platform.
- Expand the scalability of the platform in order to better support our increasingly large deployments.
- Support and listen to our customers to ensure we are meeting their needs.
You are the also co-founder of the Boston TechJam – what exactly is that?
This is something that we founded five years ago. It started a way to bring the local Boston technology community together for an afternoon of fun and networking. It has been wildly successful and is now one of the more noteworthy events of the year for the Boston technology community. We are expecting 7,000 attendees at this year’s event, along with 300 companies and 3 live bands. You can find more information on the web site.
You are quite involved with Boston startups in general – right?
Yes, that is correct. I am both an adviser to VC (Venture Capital) firms and a mentor to startups in the Boston area.
When I was younger and just starting out, there were many people who offered to help me. I see this as my opportunity to pay it back. I help by answering questions, making connections, and pushing them to succeed. I hope that they will make it big and that they will then pay it back to those coming up behind them.
In the end, we all benefit when there are many successful businesses in the community.
What general advice would you offer today’s startups?
I guess my mantra is “Get close to customers.” It is very tempting to sit in an office and code or develop content for your audience. However, when you are disconnected from your customers, your code or content becomes less relevant. In today’s world, nuance matters and you need to be very targeted. It is better to be very sharply targeted instead of trying to be all things to all people.
How many hours a day do you normally work? What do you like to do when you are not working?
I am consistently occupied with work and rarely have moments of idleness. However, my family, comprised of my wife and children, holds great significance in my life. Hence, I prioritize dedicating quality time to them. I make a conscious effort to establish specific intervals where I disconnect from work entirely, allowing me to fully concentrate on nurturing my relationships with my spouse and kids. I firmly believe in preserving these connections without the interference of phones and tablets.




Please, comment on how to improve this article. Your feedback matters!