Auth0 – Making it Easy to Implement Identity Features
- Please tell me a little bit about yourself and your background.
- Your product focuses on authentication and authorization. Let’s start with a high-level overview.
- You state on your web site that “Traditional Identity Infrastructure is Obsolete” – what do you mean by that?
- Your web site lists eight different products. Are they each available separately, or are they just different components of a single offering?
- A WordPress Plugin – that sounds interesting. Please tell me more about it.
- What are the differences between the different plans that you offer?
- Do you offer any sort of onboarding or consulting services to help integrate and configure your products?
- How do you define your market? Who is your specific target audience within that market?
- What methods do you normally use to attract and engage with new customers?
- How many active customers do you have today? Where they are mainly located?
- How would you describe your current typical customer?
- Who are some of your biggest customers?
- Who do you see as your main competitors?
- How do you see your tools as different and/or better?
- How do you see authentication and authorization evolving in the coming years?
- What are your future plans for Auth0?
- How many employees do you have today? Where are they located?
- What can you tell me about the startup community in Argentina?
- How many hours a day do you normally work? What do you like to do when you are not working?
There is no doubt that user identity, authentication, and authorization is becoming increasingly critical to application development today. Most developers still implement these functions by building them from scratch or using very primitive identity frameworks. Matias Woloski, the CTO & Co-founder of Auth0, wants to make it much simpler to not only implement, but to also manage an application’s users and authorization. Auth0 has developed a platform comprised of both a set of high-level building blocks as well as a platform dashboard to achieve these goals.
Matias also shares with me what he sees as current industry challenges and emerging trends.
Please tell me a little bit about yourself and your background.
Before starting Auth0, I founded a software consulting company. I worked with Microsoft as a product evangelist for the.NET platform and for the Patterns and Practices team. In 2008, I was working with Patterns and Practices and we were looking at the whole user identity issue. We started to notice the shift to the cloud and we realized that the classic firewall was not enough to protect the network. A user’s identity was becoming the firewall, as access was being decided based on a user’s identity. I got deeply involved in this topic and even wrote a book on claims-based identity and access control.
Your product focuses on authentication and authorization. Let’s start with a high-level overview.
At a high level, it is actually pretty straightforward. It is a SaaS (Software as a Service) solution that offers an extensible and easy to integrate platform that solves most complex user identity use cases. We provide building blocks for developers that handle authentication, authorization, and single sign-on for applications. Our mission statement is simple but says it all: “Zero-friction authentication and authorization for developers.”
You state on your web site that “Traditional Identity Infrastructure is Obsolete” – what do you mean by that?
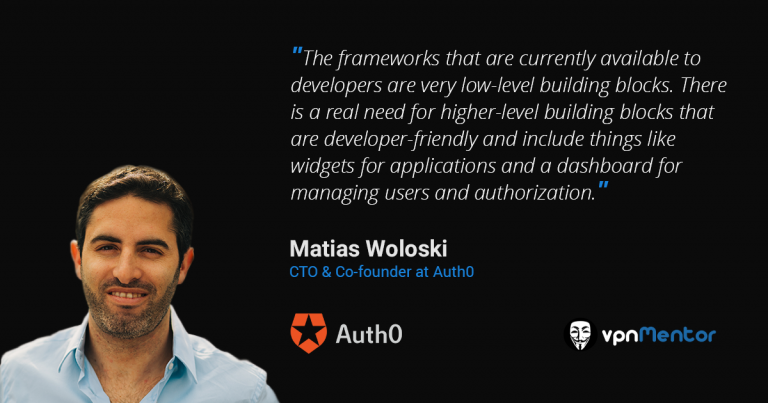
Our architecture allows you to do a lot of the things that you can’t do easily – or at all – today. The frameworks that are currently available to developers are very low-level building blocks. There is a real need for higher-level building blocks that are developer-friendly and include things like widgets for applications and a dashboard for managing users and authorization. Also, once you have all of your authentication and authorization in a single place, it opens up support for many new scenarios besides single sign-on. One example would be an authorization server to protect access to your APIs.
Your web site lists eight different products. Are they each available separately, or are they just different components of a single offering?
Most of them are just different components that are part of our platform. This includes:
- Platform Dashboard
- Enterprise Identity Provider Integration
- Embeddable Login Form (desktop, tablet, and mobile devices)
- Passwordless Login
- Breached Password Detection
- WordPress Login Plugin
There are two additional components. Multi-factor Authentication is an add-on to our Developer Pro and Enterprise plans. Webtask is a separate product that is an offshoot of our extensibility model and allows you to write serverless applications where you don’t need to worry about hosting or scaling. This is similar to recent offerings by Amazon Web Services, Google Cloud, and Microsoft Azure.
A WordPress Plugin – that sounds interesting. Please tell me more about it.
It is a WordPress plugin that wraps the functionality of our main components for simple integration with a WordPress website. It replaces the built-in login form and then allows you to have single sign-on with other applications or between multiple sites. It also allows the user to login with their social media accounts and supports multi-factor authorization.

What are the differences between the different plans that you offer?
In order to address the needs and budgets of both small and large development shops, as well as large enterprises with additional compliance requirements, we offer a few different plans. The plans differ in terms of the features and the number of active users (in last 30 days) included. We also have a free version for people who want to just try it out.
Do you offer any sort of onboarding or consulting services to help integrate and configure your products?
All paid accounts include ticket-based support to help you with any questions or problems you might have. We do also have solution architects to help with enterprise deployments, but professional services are a very small part of our revenue (single-digit percentage). The whole idea behind our approach is that you shouldn’t need much support or consulting services to be operational, but it is something we have available.
How do you define your market? Who is your specific target audience within that market?
It terms of the platform, it is appropriate across many different industries. To name just a few, our platform is used in:
- Healthcare
- Banking
- Finance
Within an organization, regardless of whether it is a startup or a huge company, our primary audience has been the developers, because they are the ones tasked with and struggling to solve identity problems. It then becomes a bottom-up sales process, starting from the developer who downloaded and installed our free version and quickly got it up and running.
What methods do you normally use to attract and engage with new customers?
We haven’t done any outbound marketing yet, but we do a great deal of content marketing. By publishing a lot of quality content on our web site, developers come to us and become inbound leads.
How many active customers do you have today? Where they are mainly located?
We currently have about 40,000 subscribers. They are located in 140 different countries all around the world.
How would you describe your current typical customer?
That is hard to say, but I can tell you what types of companies we see trending:
- Healthcare
- Media
- Moving to the cloud
- Modernizing their stack
Who are some of your biggest customers?
Who do you see as your main competitors?
Our biggest competitor today is DIY - Do It Yourself! Developers think that they can build it themselves from scratch or from primitive frameworks. This is an educational process and will take time for change, but we see this as our biggest opportunity as well. Amazon Web Services (AWS), Google, and Microsoft Azure have similar offerings, but we really don’t see them as our biggest challenge.
How do you see your tools as different and/or better?
I think that we stand out in three main areas:
- Simplicity – Easy to use and you can start immediately with our free version.
- Extensibility – Take the platform to wherever your needs are.
- Universal Deployment – Deploy on-premises, in public cloud, or in private cloud.
How do you see authentication and authorization evolving in the coming years?
It is clear to me that the issue of passwords is something that we need to address and solve as an industry. Something will soon replace passwords, probably one or more approaches from this list:
- Biometrics
- Multi-Factor Authentication
- Adaptive Authentication / Machine Learning
What are your future plans for Auth0?
We have achieved a lot of traction as a platform, but there are scenarios that we want to focus on and enhance, such as B2B, B2C, and B2E. We want to build specific components on top of our platform to provide complete solutions in these segments. We are also exploring opportunities in the serverless space for developers, based on our Extend product.
How many employees do you have today? Where are they located?
We currently have about 200 employees. 20% of them are in Argentina, 30% are in the US, and 50% are in the rest of the world. We are a very distributed company – even development is distributed throughout different locations. We want to hire wherever the best talent is located. Our headquarters are in Buenos Aires, Argentina and in Bellevue, Washington.

What can you tell me about the startup community in Argentina?
The startup community in Argentina is still in its infancy. There is a lot of local talent and good ideas, but there isn’t much venture capital and funding is hard to get - especially beyond a seed round. However, the government is starting to get involved and the situation is beginning to improve.
How many hours a day do you normally work? What do you like to do when you are not working?
During the initial stages, it was common for me to dedicate 15 hours a day to work. However, we have reached a juncture where I can strike a balance and lead a more well-rounded life by working approximately 11 hours daily. While it remains a substantial commitment, I no longer find myself working on weekends as frequently.
I come from a family of musicians and I love music. My instrument of choice is the keyboard which I really enjoy. I also enjoy playing soccer and just hanging out with my friends.



Please, comment on how to improve this article. Your feedback matters!