Black Duck Software – Managing and Securing Your Open Source Software
- Please tell me a little bit about yourself and your background.
- As I understand it, the company's focus and product offerings have evolved over the years. Can you please tell me about the history of the company, before we dive into the specifics of the offerings?
- What exactly is the Black Duck Hub?
- It seems that everything is based on your KnowledgeBase – correct? How was that started and how is it maintained?
- What are the DevOps integrations that you offer?
- You offer several types of code audits - what are they? What have been the biggest surprises that you have found in these audits?
- How do you define your market? Who is your specific target audience within that market?
- How many active customers do you have today? Where are they mainly located?
- How would you describe your current typical customer?
- Who are some of your biggest customers?
- Who do you see as your main competitors? How are you different?
- You have a unique vantage point to view the overall open source community. What changes and trends are you seeing in terms of companies using open source software?
- Have you noticed anything in particular about startups and open source software?
- How do you see security and open source software evolving in the coming years?
- What are your future plans for Black Duck?
- How many employees do you have today? Where are they located?
- How did the company name Black Duck come about?
- What do you like to do when you are not working?
It is no secret that the use of open source software components is growing at a very rapid pace. This is true for both young startup companies as well as established enterprise developers. The developers that incorporate these open source components need to somehow stay on top of the many licensing issues and security vulnerabilities of these components. For more than 10 years Black Duck Software has been helping developers address these challenges and has accumulated the industry’s largest database of open source component information.
In my conversation with Mike Pittenger, VP for Security Strategy at Black Duck Software, we discuss the Black Duck KnowledgeBase and their Hub product that leverages all of its information. We also examine some of the most surprising findings that have surfaced in the course of Black Duck code audits as well as some of the trends Mike sees from his unique vantage point on the open source community.
Please tell me a little bit about yourself and your background.
I have been in the security industry for 17 years, working at companies such as Authentica and @stake (acquired by NortonLifeLock). I was also the co-founder of Veracode and led the spinout of this team from @stake. In 2009 I started my own marketing consulting company in the security space. Black Duck was a client of mine and at some point they made me an offer to join them full time. The company has a great product and a great management team, so I said yes and joined them as an employee in March 2015.
As I understand it, the company's focus and product offerings have evolved over the years. Can you please tell me about the history of the company, before we dive into the specifics of the offerings?
Black Duck Software was founded in 2003 and for the next decade it focused on solutions for open source license compliance and governance. It soon became the leader in the space and was quickly adopted by large companies, especially when they were performing their due diligence before acquiring another software company.
Starting in 2013, Black Duck shifted its main focus to managing open source security risks and in 2015 we released our flagship product, the Black Duck Hub.
What exactly is the Black Duck Hub?
Black Duck Hub is a complete open source management tool. At its core, it scans a project’s source code to discover all of the open source components. It then looks for relevant vulnerabilities in our open source KnowledgeBase. The Black Duck Knowledgebase is the industry’s most comprehensive database of open source information. We currently track over 2.5 million unique projects, with data compiled over the past 10 years, including coverage of:
- Vulnerabilities
- Full license texts and obligation
- Community activity
We have found that an average software application today contains about 35% open source code, which maps to about 150 unique open source components. These numbers are increasing rapidly.
Every year there are over 3,000 open source vulnerabilities reported. Traditional software testing and automated security testing tools are not effective at finding these vulnerabilities.
We describe the risks we address as follows:
- Security risk – Providing information on vulnerabilities reported in open source components. This information comes from public sources, such as the NIST (National Institute of Standards and Technology) National Vulnerability Database, as well as dozens of other sources that Black Duck monitors.
- License risk – This provides customers with information about open source licenses in the software that are inappropriate for the deployment model for a particular application (e.g., a distributed software application using a GPL license).
- Operational risk – A metric about how well supported an open source project is – the number of contributors, number of commits over the past year, whether or not newer versions are available. The goal is to help customers avoid using open source that has been effectively end-of-lifed by the community.
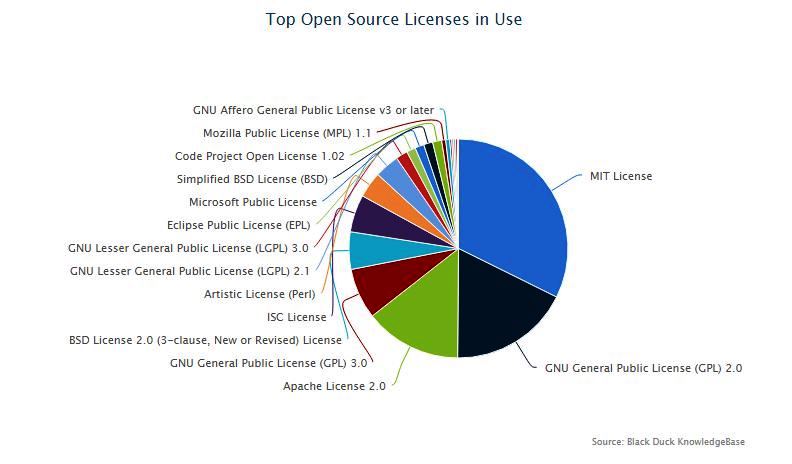
It seems that everything is based on your KnowledgeBase – correct? How was that started and how is it maintained?
Yes, the Black Duck KnowledgeBase in the key to the Hub and we have 50 people working on it. We started working on it in 2002 when the company was founded and have been enhancing it ever since. Many of the components that we added to the KB in our early days are no longer publicly available, making our KB unique in its ability to track these components. We monitor about 8,500 different sites on a daily basis for new open source software releases. We update the component information twice a day and we update the vulnerability data every hour.
A year ago we established the Center for Open Source Research & Innovation (COSRI). The goal is to provide cutting-edge research, innovation, information, and education to help ensure that the open source ecosystem remains vibrant and secure.
There are several components to the COSRI. In addition to the Black Duck KnowledgeBase, there is a group that focuses on machine learning and other advanced techniques to more granularly identify source code elements. There is also the Black Duck Open Hub, which is an online community and public directory of free and open source software for discovering, evaluating, tracking, and comparing open source code and projects. The Open Hub has 350,000 registered users and is editable by everyone, similar to a wiki.
What are the DevOps integrations that you offer?
We believe that it is best to integrate the Hub’s scanning of source code into a project’s build process. In order to enable that, we have developed integrations in popular tools for all stages of the build process. We offer all of these integrations for free to our customers and have made most of them available as open source software.
You offer several types of code audits - what are they? What have been the biggest surprises that you have found in these audits?
These are one-off audits that we call “Black Duck on Demand.” They are typically requested by a company during a due diligence process and comprise one or more of the following audit types:
- Open Source Audit
- Open Source Security Audit
- Code Quality Analysis
- Encryption Audit
The biggest surprise for me from a security perspective is that 2/3 of all applications that use open source software contained vulnerabilities in that software. On average, we found 27 vulnerabilities per application. Perhaps even more shocking is that the average age of the vulnerability – the time from the disclosure of the vulnerability to the audit – was greater than 4 years! Some were even as much as 9-12 years.

How do you define your market? Who is your specific target audience within that market?
For our Hub product we normally work with a company’s CTO (Chief Technology Officer) or CSO (Chief Security Officer) on the security aspects and with a company’s in-house counsel on the licensing issues.
For our audit services, we usually work with venture capital firms or companies acquiring other companies or software assets.
How many active customers do you have today? Where are they mainly located?
We now have more than 2,000 customers, mainly centered in the US. We also have a strong presence in Europe, the Middle East, and Asia Pacific.
How would you describe your current typical customer?
It varies. We have many customers who are ISVs (Independent Software Vendors) building commercial software products. We also have many enterprise customers who are writing a lot of software for their own use, e.g. financial services, insurance companies, and technology companies.
Who are some of your biggest customers?
We are proud to say that our customer list includes some of the world’s largest companies:
- Intel
- JPMorgan Chase
- Nintendo
- Samsung
- SAP
- ScienceLogic
Who do you see as your main competitors? How are you different?
In the last few years we have seen several new companies trying to address this problem by looking at what software components are being declared in the build process (only).
We take a three-pronged approach to identifying open source components and potential vulnerabilities:
- Package manager declarations
- What components are actually used
- Transitive dependencies
You have a unique vantage point to view the overall open source community. What changes and trends are you seeing in terms of companies using open source software?
We are seeing a significant increase in the number of companies using open source software. What is perhaps a little bit surprising is that we are seeing more and more companies contributing software back to the open source community. This is very important because it ensures a strong community and provides both growth and support.
In order to put numbers to it for you, let me give you an idea of how many open source projects we have tracked in the past few years:
| 2013 | 1 million |
| 2015 | 1.5 million |
| 2017 | 2.5 million |
Have you noticed anything in particular about startups and open source software?
I see a lot of startups through the audits that we perform. Startups today are using open source software to build as much as half of their product. This allows them to get to market faster and to also lower their development costs. The combination of speed and cost savings is a strong motivation to use open source software.
How do you see security and open source software evolving in the coming years?
There is a growing awareness of both of these elements and they are drawing a lot of attention. It is not just the vulnerabilities that are getting attention, but the solutions are also seeing good growth. Companies are increasingly taking actions to solve the problems, rather than just reporting issues.
What are your future plans for Black Duck?
Black Duck will continue to strive to be the leader in open source management and security. This goes beyond simply identifying open source components. It includes helping customers ensure that they are using open source code that meets their business needs, as well as their appetite for risk (e.g., zero vulnerabilities is not necessarily the goal for every application).
How many employees do you have today? Where are they located?
Black Duck currently maintains a workforce of over 300 employees, with the majority based at our headquarters in Burlington, MA. Our Belfast office in the UK stands as our second largest, closely followed by our offices in Theale, UK and San Jose, CA. Furthermore, we have established offices in China, Taiwan, and multiple locations across Europe.
How did the company name Black Duck come about?
That is the question we get asked most often… [laughs]. Black Duck was named after the founder’s childhood pet.

What do you like to do when you are not working?
My hobbies are fishing, biking, and woodworking.



Please, comment on how to improve this article. Your feedback matters!