Coronet – Allowing You to Safely Use Any Wi-Fi or Cellular Network
- Please tell me a little bit about yourself and your background. This isn’t the first company that you have founded, right?
- Coronet is a platform to protect users from wireless network threats. What is unique about those threats?
- Why aren’t I safe if I connect via a VPN?
- Do you think that in general people today are aware of the risks of connecting to available cellular and wireless networks, such as those in coffee shops?
- What are the main elements of the Coronet platform?
- If I use Coronet, do I still need to use a VPN?
- You offer a few different usage plans. What are the differences between them? How much do they cost?
- How do you define your market? Who is your specific target audience within that market?
- What methods do you normally use to attract and engage with new customers?
- Whom do you see as your main competitors? How are you different and/or better?
- How do you see computer security in general and communication security in particular, evolving in the coming years?
- What is some general advice that you would offer today’s startups?
- How do you see the world of startups changing in the next few years?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
Let’s be honest – how many of us think about security risks as we race into a coffee shop to check our email or the latest sports scores? Unfortunately, there are a lot of bad guys out there who know the answer to that question. They are waiting to take advantage of the situation and attack our computers or mobile devices should we fall to the siren call of a free wi-fi spot.
In my discussion with Dror Liwer, the co-founder and Chief Security Officer of Coronet, I learned about the less familiar security risks of wireless and cellular connections, the future faced by startups today, and his somewhat unusual hobby.
Please tell me a little bit about yourself and your background. This isn’t the first company that you have founded, right?
That’s correct. This is my sixth startup in fact. I started a venture capital firm and worked at a few larger companies as well. I don’t know if that makes me a serial entrepreneur or a masochist… After serving as CIO (Chief Information Officer) for the Israeli Military Police, I moved to the U.S. for two years – but ended up staying for 18 years. I founded Coronet three years ago with three friends.
Coronet is a platform to protect users from wireless network threats. What is unique about those threats?
Unlike corporate network threats, no one takes ownership of wireless/cellular threats, because there really isn’t any economic incentive for anyone to do so. While companies and vendors are addressing cloud and/or mobile device-based security threats, no one is addressing the threats of wireless networks. The protocols for seamless connectivity were designed many years ago, without taking security issues into consideration.
Over the past two years, the technology for infiltrating and imitating wireless networks has become very low-cost and readily available. Previously, the tools to penetrate wireless and cellular networks were prohibitively expensive, costing anywhere from $500,000 to $2.5 million. This made them really only available to organizations such as the NSA (National Security Agency), the Mossad, and police departments. Today, you can legally purchase the required hardware for about $500 bucks, make a few simple hardware modifications, and install widely available open-source software. Then, voila, if you’re ready to operate it and can do so illegally with malicious intent.
Using this technology, which was originally intended to boost a signal’s power, it becomes easy for a hacker to imitate a legitimate wireless or cellular network. The victims then connect to these devices, since they are seen as being the strongest tower or connection point for the network.
Why aren’t I safe if I connect via a VPN?
Unfortunately, using a VPN provides you with a false sense of security for two main reasons.
The first reason for a false sense of security is that a VPN requires an end-to-end connection, which means an attack can be carried out in the “VPN gap” – the time before this connection is actually established. An example of this is the DarkHotel attacks, which targeted executive-level guests at luxury hotels in Asia. You can learn more about it in our blog post DarkHotel: Give Us All Your Data and Enjoy Your Stay.
The second scenario, and the one that we actually see most often, is when hackers jam the VPN port. The users then think that the VPN isn’t functioning properly, so they decide to work without the VPN, in order to get their work done.
Do you think that in general people today are aware of the risks of connecting to available cellular and wireless networks, such as those in coffee shops?
In general, the answer is no – but most people will change their behavior after talking to me [smile].
Here are the most common places where people are at risk:
- Public Places - Hotels, airports, sports arenas, and food courts.
- Public Transportation - Trains, buses, airports.
- Corporate Offices - Both inside and around the facility.
- Home Networks
Once they gain access, cyber hackers can then create havoc in several different ways:
- Expose stored credentials
- Intercept and manipulate data traffic
- Place malware on the device
- Manipulate the device
- Use the device as a “Trojan Horse”
Coronet maintains a database of 140 million networks used around the world. We have found that 4% of the networks used are malicious. An even more shocking statistic is that 61% of Americans will conduct banking transactions on an open wireless connection!
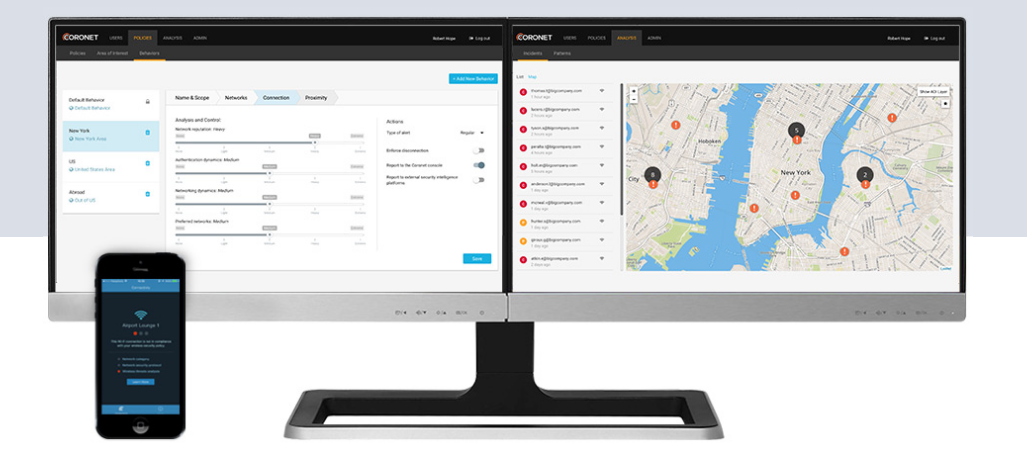
What are the main elements of the Coronet platform?
The Coronet solution consists of three components:
- Coronet Client - A lightweight software agent that runs on any device - MAC OS, Windows, Android, and iOS.
- Coronet Enterprise Dashboard – A platform that enables an organization to define wireless security policies and track threats in real-time.
- Coronet Intelligence Platform – A massive intelligence repository that captures network behavior data and continuously analyzes the data, searching for new attack vectors in real-time.
Coronet software client has three main functions:
- Detection – It identifies any attacks or compromises on the device, network, or cloud services.
- Prevention – It proactively warns and prevents a user from potential threats and enforces the specified corporate security policies.
- Intelligence – It anonymously gathers intelligence about networks and services in order to help identify new emerging security threats.
If I use Coronet, do I still need to use a VPN?
That depends. In a corporate environment, a VPN is used for two different purposes: data encryption and exposing internal services to the outside world. For data encryption, you don’t need to use a VPN, since most cloud services already use SSL for encryption. For safely exposing internal services, you should still use a VPN.
You offer a few different usage plans. What are the differences between them? How much do they cost?
We currently have two plans. The Personal plan is free, and includes the client agents, which will provide you with warning and alerts. The Enterprise plan includes the full Coronet platform that I described previously. The pricing is based on the number of users and we have closed deals that run more than $100,000 per month.
We are currently on target for our goal of 100 million installations by the end of 2017.
How do you define your market? Who is your specific target audience within that market?
Our target market is enterprise customers. These customers usually have more than 10,000 employees and a large mobile workforce. They can be located anywhere in world. Most of our current customers are concentrated in the U.S. and Europe, and we are starting to get good penetration in the Asia Pacific region.
What methods do you normally use to attract and engage with new customers?
We are very active in the cyber security community. We don’t do much outbound marketing - most potential customers come to us at conferences, briefings, or other events.

Whom do you see as your main competitors? How are you different and/or better?
We have several types of competitors:
- Devices – Mobile Threat Defense (MTD) companies
- Networks – Virtual Private Network (VPN) companies
- Cloud Services – Cloud Access Security Brokers (CASB) companies
We are unique in that no other single platform does what we do, end-to-end, to cover all of the pieces of the security puzzle. In addition, we are the only company in the world that is able to identify suspicious wireless/cellular networks and to then redirect the connection to a local safe network.
How do you see computer security in general and communication security in particular, evolving in the coming years?
I believe that security is done completely wrong today, because it is based on restrictions instead of enablement. Companies think that if they send out a security memo their employees will comply. But that is just not the reality of how employees choose to work today. In the average enterprise company, there are 600 cloud services that are used by employees – without the IT department being involved!
A more intelligent approach is necessary, only imposing restrictions on users when there is a genuine threat. Our examination of worldwide network connections reveals that 4% of these connections lead to malicious networks, while 13% are linked to "non-enterprise networks" within the enterprise. However, it is important to note that 42% of connections to public networks are entirely secure, and there is no justification for imposing restrictions on users accessing those networks.
In terms of policies and regulation, across the board, I’d say that we are behind on all fronts. Government regulations are based on old laws, corporate policies are based on outdated concepts, and individual users have become numb to the issues. I believe that individuals must assume more responsibility for their actions and personal security.
What is some general advice that you would offer today’s startups?
From my experience in multiple startups and as a venture capitalist I can tell you that the “secret sauce” for a startup’s success consists of:
- A killer team
- Real innovation/advantage – not fluff
- Choosing your partners more carefully than you choose your spouse
How do you see the world of startups changing in the next few years?
I see the world of startups changing already, but not for the better. As a backlash to the massive valuations of companies over the past 10 years, investors have become much more conservative. Investors’ dislike for real risk will have a strong, negative impact on the startup community.
How many employees do you have today? Where are they located?
We currently have 35 employees. Our R&D center is in Israel and we have additional offices in Frankfurt, New York, and North Carolina.
How many hours a day do you normally work? What do you like to do when you are not working?
I work as many hours as needed. That means sometimes 13 hours a day and sometimes 20 hours.
I travel extensively around the world. I currently spend about 60% of my time travelling. I don’t really have a time zone.




Please, comment on how to improve this article. Your feedback matters!