Cyren – Taking Internet Security to the Cloud
- Please tell me a little bit about yourself and your background.
- What is Cyren’s mission?
- Please give me an overview of your platform and tools.
- What are the benefits of a 100% cloud-based security platform?
- One of the services I found interesting was your outbound antispam protection. Is that something relatively new that companies are paying attention to?
- How do you define your market? Who is your specific target audience within that market?
- Who do you see as your main competitors?
- How do you see your tools as different and/or better than theirs?
- What do you see as the top security threats that we currently face?
- What are your top 3 security tips for companies today?
- How do you see the security market evolving in the coming years?
- How many active customers do you have today? Where are they mainly located?
- Who are some of your biggest customers?
- What are your future plans for Cyren?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
Lior Samuelson has been around technology and businesses for many years, but he is particularly passionate about making the Internet a safer place for users – especially those who seek better security and those on the move with their mobile devices. Lior is the CEO and Chairman of Cyren, a leading provider of cloud-based security solutions.
In our recent conversation, Lior shared with me why a cloud-based approach is critical in today’s computing environment, how he sees the security market evolving in the next few years, and his top 3 security tips for companies today.
Please tell me a little bit about yourself and your background.
I studied in both Israel and the US and began my professional career with Booz Allen Hamilton. After that, I launched my startup career with a company that was sold in 1986. Since then I have been the Chairman and/or CEO of many different companies – eight altogether. I have also managed venture capital and private equity funds, so I understand startups from both the technology and financial aspects.
What is Cyren’s mission?
Cyren, as it is today, was really established 3-4 years ago, when we saw the need to fundamentally protect the Internet by building a security perimeter around the internet. We focused on building a totally cloud-based solution to provide enterprises with comprehensive, but simple to use, protection from the hazards of the Internet.
The way we think about it, regardless of the type or size of client you are and your security needs, all the security we provide originates from the same cloud platform and is based on the same core technologies and data. We are unique in that we only employ our own detection engines and data. We do not buy technology from other vendors.
Please give me an overview of your platform and tools.
We provide a set of true cloud-based enterprise security as a service solutions, as well as additional integrated threat intelligence services. Our solutions include:
Enterprise Security SaaS platform
- Web Security Gateway
- Email Security Gateway
- DNS Security
- Cloud Sandboxing (Sandbox array)
Threat Intelligence Services
- Anti-Spam Inbound
- Anti-Spam Outbound
- URL Filtering
- Phishing Intelligence
- IP Reputation
- Anti-Malware
- Malware Attack Detection
- Mobile Security
What are the benefits of a 100% cloud-based security platform?
The bottom line is you cannot provide effective security unless you utilize a true cloud-based solution.
The traditional approach to security is to install appliances such as mail or web gateways in an enterprise. If the enterprise is a bank, for example, you need numerous appliances – one for each branch or office. This approach is still the most common approach today, but it really doesn’t meet the needs of the modern corporate computing environment. It is virtually impossible to protect the mobile workforce of laptops and mobile devices with appliances – especially when most of the applications today are in the cloud.
Today’s attacks are fast, with shorter duration and many variants. The speed of detection and prevention of attacks is therefore of ultimate importance. If you cannot update your security environment virtually instantaneously, your protection is weak. You can only do that with a cloud. We can update our cloud network in 3-4 seconds from the time an unknown attack is detected.
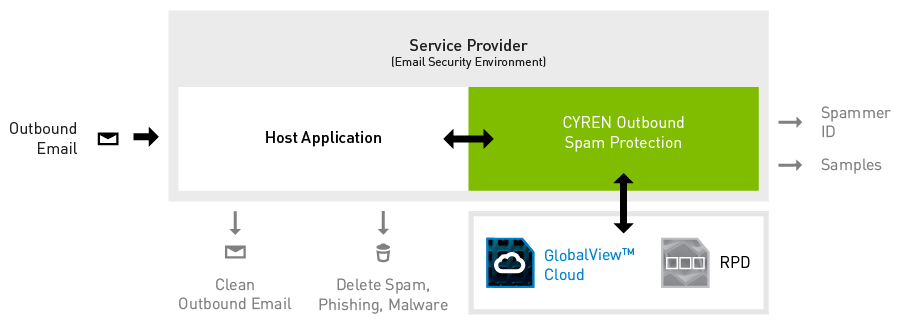
One of the services I found interesting was your outbound antispam protection. Is that something relatively new that companies are paying attention to?
We’ve actually had that feature for quite a while, although the technology and sophistication of the algorithms get updated over time. The reason outbound spam protection is important is because of the way attackers operate today. They don’t attack with their own machines - they use other people’s machine. Many of our clients use the technology as an “anti Bot” service. This protection prevents our clients’ machines from being blocked or blacklisted.
How do you define your market? Who is your specific target audience within that market?
We are in the Internet security market and provide a perimeter around the Internet that protects users. Our platform and services are intended and appropriate for almost anyone. This includes small, medium, and large companies as well as internet service providers, managed security providers, telecom carriers, and other security companies.
Who do you see as your main competitors?
There are a lot of different competitors in the market, mostly appliance vendors. There are a few other cloud security providers. No one else to my knowledge has a multi-product cloud platform. Each of the competitors has one cloud product. We specifically target businesses that are still using older technology, still depending on hardware appliances, and/or need improved quality of protection.
How do you see your tools as different and/or better than theirs?
The barrier to entry for cloud-based security solutions is very high due the cost and expertise required. Also, we have developed sophisticated ways of detecting unknown threats that have proven to be very effective. We are a third-generation company in a world dominated by first-generation competitors. We believe we have the best platform in the market. Our prevention and detection algorithms are based on both behavior and big data and we capture 25 BILLION security transactions per day.
Other unique benefits of our solutions include:
- Native and completely cloud-based platform.
- Easy and quick client on-boarding, sometimes through our website.
- No need for hardware appliances or numerous IT professionals.
- Monitor and manage everything in real-time from a single console.
As I mentioned earlier, we are unique in that we only employ our own detection and engines and data. In fact, many well-known security providers have partnered with us to use our technology.
What do you see as the top security threats that we currently face?
The major problem today is that the threats and attack vectors are continuously changing. Attackers change their methods often. We as an industry must be able to not only improve our detection technology, but also simplify the consumption of security by our clients.
What are your top 3 security tips for companies today?
This might sound a little self-serving, but…
- Move to the cloud (don’t protect with appliances).
- Approach to security must be professional and current.
- Don’t implement security only for regulatory/compliance reasons.
How do you see the security market evolving in the coming years?
The size of the security industry is growing rapidly every year. Industry analysts expect the market to reach a size of $100-$150 Billion by the year 2020.
I believe that three significant things are going to happen:
- Big emphasis on moving to the cloud. Those who don’t will be in trouble.
- Efforts to develop more sophisticated and faster solutions will continue for the foreseeable future. This is necessary because the threats are changing and becoming more sophisticated.
- There will be consolidation in the security industry and companies that are no longer relevant will disappear altogether.
How many active customers do you have today? Where are they mainly located?
We currently have thousands of customers. The breakdown would be 44% North America, 44% Europe, and the remainder in the rest of the world (primarily Asia).
Our corporate customers range in size from 200 seats to hundreds of thousands of seats. We also have customers who are service providers and use our software to service their own clients.
In total, either directly or indirectly, we protect 600 million users per day.
Who are some of your biggest customers?

What are your future plans for Cyren?
Our plan is to become a dominant player in the Internet security industry. We are investing heavily in development – more than half of our employees are in R&D.
How many employees do you have today? Where are they located?
Our workforce comprises approximately 220 employees, strategically distributed across various locations. Our Research and Development (R&D) centers are situated in Israel, Germany, and Iceland, collectively accommodating 155 employees. Additionally, we maintain a few smaller sales offices in the United States and London.
How many hours a day do you normally work? What do you like to do when you are not working?
I was afraid you would ask that… [smile]. I basically work whenever I am not sleeping. I do take some time off to ride a bicycle and usually commute to the office by bicycle as well.



Please, comment on how to improve this article. Your feedback matters!