Report: 1/4 of Fortune 500 Companies Hacked in Last Decade
vpnMentor can exclusively reveal that more than a quarter of Fortune 500 companies were hacked in the last decade.
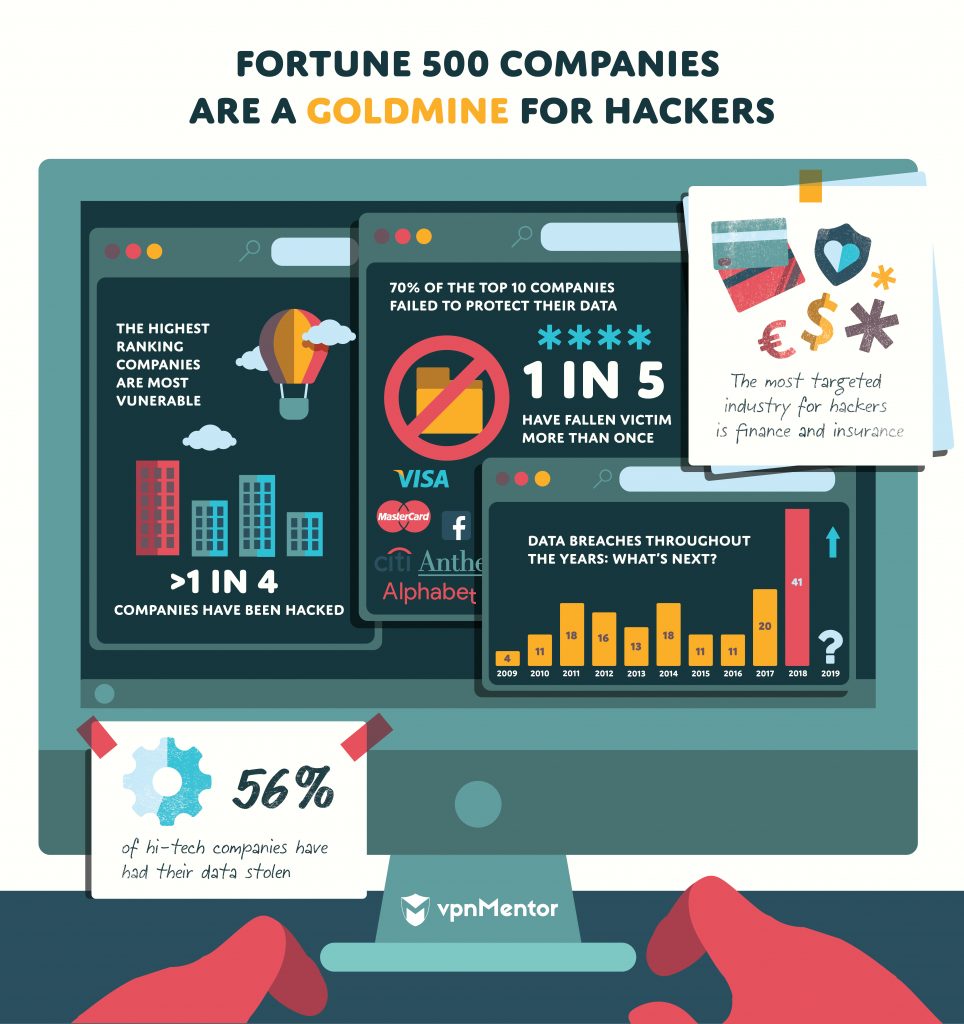
This peaked with a record number of hacks in 2018. Fortune 500 companies experienced 41 hacks in 2018 alone, more than double 2017’s record of 20.
Fortune 500 is Fortune magazine’s annual list of the 500 most profitable US corporations. As America’s largest and richest companies, they represent the crème de la crème of the business world, ranging from manufacturing companies to hotels and banks.
But do these companies put their profits to good use by investing in resilient cybersecurity measures? With over a quarter of Fortune 500 companies experiencing hacks and data breaches within the past decade, our report suggests not.
This raises another question. If huge companies with access to the world’s best data security can fall prey to phishing schemes, hackers, data breaches, and malware - what can the rest of us do?
Methodology
The goal of our study was to quantify how many Fortune 500 companies experienced hacks in the last decade.
We looked at public records of data breaches sourced from newspaper reports, public legal records, state websites, and online journals. We ran the subjects of these stories against the Fortune 500 list to identify the number of hacks since 2009.
We then divided companies into sectors using the North American Industry Classification System. This allowed us to see which sectors are most commonly targeted by hackers.
Which Companies Were Hacked?
Our analysis of public data revealed that 27% of Fortune 500 companies experienced data breaches in the last decade.
We found a somewhat surprising correlation: the higher-ranked a company is, the more likely it is to have been hacked. Our data shows that 70% of top 10 companies were hacked in the last 10 years, along with 65% of top 20 and 50% of top 100 firms.
Which Industry was Targeted Most?
When we analyzed hacked companies according to sector, even more interesting trends emerged. This revealed that Finance and Insurance is the most vulnerable sector, with close to 30% of all hacked companies belonging to this group.
In contrast, the safest sector appears to be Mining, Quarrying, and Oil and Gas Extraction: no companies in this group were hacked.
Our findings regarding the Finance sector are troubling for two reasons. Firstly, since these companies are customer-facing, data breaches impact the public as well. For example, a 2014 hack on JPMorgan Chase saw the release of account information impacting 76 million private accounts and seven million small businesses.
Secondly, by default, these companies are entrusted with safeguarding the public’s savings. If they can’t protect their information and customer data against cybercrime, what can the public do?
Additionally, 56% of 2018’s Fortune 500 companies in the Information sector fell victim to hacks in the last decade. This covers the hi-tech sector, which makes this finding particularly surprising.
These companies recruit and employ the best talent in data analytics, computer programming, and technological innovation. That more than half of these firms cannot safeguard their data is truly shocking.
Data Breaches Across Different Industries
Healthcare
Healthcare details are typically guarded with great care as they are highly confidential. However, our study shows that several Fortune 500 companies allowed private healthcare information to be made public.
For example, a 2011 hack on Anthem Blue Cross, an American health insurance company, revealed the full health records of 612,000 people applying for coverage. Humana suffered a similar breach in 2018. All applicants were under the age of 65, meaning most were still part of the workforce. One sinister consequence of leaked healthcare information is that it has the potential to inhibit employment prospects.
Perhaps the most shocking healthcare privacy violation occurred at Aetna in 2018. A low-tech breach revealed the addresses of more than 12,000 patients receiving a letter headered, “Filling Prescriptions for HIV Medication.”
HIV and HIV-related illnesses are highly stigmatized, with patients suffering discrimination socially, economically, and even where their healthcare is concerned. Aetna’s hack saw them pay out more than $17 million in legal compensation.
Finance
In 2014, an investigation by Obama’s Financial Fraud Enforcement Task Force revealed that hackers gained unauthorized access to customer bank accounts from the USAA and 15 other global financial institutions. Three defendants were accused of defrauding American customers of more than $15 million.
Accommodation and Food Services
An attack on Marriott International saw hackers access personally identifiable information belonging to 500 million people in 2018. Marriott revealed that hackers had been accessing guest information from its Starwood line since 2014. Hacked data included: phone numbers, email addresses, passport numbers, reservation dates, and payment information including card numbers and expiration dates.
Manufacturing
In some instances, the severity of a hack was only discovered during an official investigation. For example, a hack affecting Ford Motor among other prolific companies (including DreamWorks Animation, Bank of America Corp, and Delta Airlines) ran for more than five years from February 2010 to August 2015.
The term “hack” is fairly broad and can’t be applied to every incident here. Our stats also include other data breaches. For example: in 2018, 8,000 sets of personal information were stolen from Coca-Cola. A former employee of one of Coca-Cola’s subsidiaries retained an external hard drive filled with member information. This information was leaked, prompting a legal investigation.
Transportation and Warehousing
As the USA’s largest domestic airline, Southwest Airlines has close to 58,000 employees. When it suffered a third-party breach in 2018, 36,485 employee accounts were leaked – including tax and insurance information, payroll data, and information that could be used to identify employees’ families.
Who Do Hacks and Data Breaches Affect?
When Fortune 500 companies are hacked, the victim isn’t always obvious. While the company itself may be harmed, in more than 97% of cases, hacks resulted in leaked personal data, affecting either employees or consumers.
There are instances where the company itself is the victim. For example, a 2015 hack on the Bank of America Corp saw nine people charged with insider trading and hacking. More than 150,000 confidential press releases were stolen from several high-profile companies before publication. The scheme generated more than $8 million.
Ethical hacking techniques may also obscure the target of hacks. For example, in October 2016, Google revealed a zero-day vulnerability in Microsoft’s Windows software. They alerted the company a week before publicly publishing their findings.
Google’s publication highlights the double-edged-sword aspect of ethical hacking. On the one hand, Google acted responsibly: they found and reported a vulnerability to Microsoft. That responsibility extends to the program’s users, prompting Google to publish their findings. However, when weaknesses become public knowledge, malicious actors have the opportunity to exploit unresolved issues. While Google was ostensibly helping Microsoft, they could have caused more harm.
Repercussions of Data Breaches
Data breaches carry implications that extend well beyond tarnishing the image of corporations. Such intrusions have tangible repercussions for both the business sectors and the end users.
National Security
In 2011, Forbes reported that Anonymous hacked into Booz Allen Hamilton, a consulting firm with a long-term contract with the Pentagon. When Anonymous hacked its servers, it revealed login details for 90,000 military personnel from a range of national security offices.
This data could allow hackers to act as personnel. In the wrong hands, it could have potentially lethal consequences.
Trade Details
In 2018, a former Tesla employee admitted to hacking the company’s confidential data and trade secrets and transferring stolen data to third-party groups. He also created software to hack into Tesla’s manufacturing operating system and used to it to steal confidential manufacturing media.
This shows that as well as directly impacting companies, this kind of information disclosure creates unfair market advantages. It could also lead to insider trading.
Account Details and User Privacy
When hackers access account details, it allows them to act as the account owner. They can change settings, steal payment methods, and make purchases undetected by either the site or the user. It’s a foolproof form of identity theft that could have disastrous consequences for users.
This can create relatively localized damage. For example, a 2017 Netflix data breach saw the details for an unknown number of user accounts appear on the dark web. Netflix advised account holders to log out of all devices and change their passwords to keep their user info and credit card data secure.
Of course, hacks present a much more significant risk to user privacy than exposing their Netflix passwords. While some hacks on Fortune 500 companies revealed just usernames and email addresses, more than 90% of breaches included credit card information, Social Security numbers, physical addresses, healthcare details, or a combination of the above.
Conclusion
Ordinarily, we advise our readers to take the utmost care when sharing data online. However, the Fortune 500 hacks detailed above prove that sometimes, user caution isn’t always enough. After all, while you can choose not to save your card details to Amazon or Netflix, it’s impossible to prevent your health insurance company from storing your health records.
Companies have a duty of care to themselves, their employees, and their customers. Large companies need to clean up their act and invest more resources in safeguarding sensitive consumer data. Mistakes don’t only cost customers. Corporations could pay millions in legal fees, and lose their reputations.
At the time of publishing, three major breaches had occurred in 2019. If 2018’s record stats are anything to go by, we expect this number to increase dramatically throughout the year.




Please, comment on how to improve this article. Your feedback matters!