How to Call Anonymously: Ways to Hide Your Identity in 2025
While anonymous calls can be associated with illicit activities, there are many legitimate reasons for hiding your identity when calling someone. For example, you might want to return a call you received from an unknown number but don't want to reveal your identity or information.
You may also use anonymous calls to submit reports to law enforcement or government agencies while protecting your standing as a private citizen. Whatever your reason — as long as it's ethical and legal — it's useful to learn how to call anonymously. The good news is that I researched and compiled all the ways you can do so in 2025. So, without further ado, let's dive in!
How to Make Anonymous Calls with a Caller ID
There are several ways to keep your identity hidden while calling someone. One of the easiest is by using lines or services that are not connected to your personal information. These methods are better for one-time or temporary communications, as they often involve disposable hardware or accounts. Here are your options:
Through a Payphone
Payphones are useful if you want to hide your identity from the person you’re calling but don’t mind revealing the number. Payphones are straightforward because you can easily select a phone, make a call, then walk away. While the receiver can try to call the number back, they won’t be able to trace the call back to you.
 Most payphones are old-fashioned telephone lines, which makes them prone to breakage or malfunction
Most payphones are old-fashioned telephone lines, which makes them prone to breakage or malfunction
The only problem is that payphones are rare nowadays; you might need to travel some distance to find a functional one.
Through a Burner Phone
Like payphones, burner phones will most likely display a caller ID, but there won’t be any way to trace the number back to you. The main difference is that you can buy them from most big-box or convenience stores.
Burner phones are not locked in network provider contracts, so there’s no paper trail tying you to the number you get. Plus, they are prepaid with a limited number of minutes for calls. Once the load runs out, you can buy more minutes or “burn” the phone by destroying or discarding it.
Also, a burner phone will allow you to send anonymous texts. So, if you’re planning to wait for a response, a burner is a great option because you have more control over when to discard the number.
Through VoIP
If you don’t know where to find payphones near you or don’t want to buy a burner phone, you can use Voice over Internet Protocol (VoIP). It’s a technology that uses the internet to transmit voice calls.
Not all VoIP apps allow users to call anonymously, and some will even require you to register using an existing number tied to an official phone carrier. But many other services offer clear-cut ways to mask or hide your identity while calling someone. You may get a private virtual number that’s not connected to your personal information and use it to place local or international anonymous calls.
However, remember that some VoIP services limit whom you can communicate with, so be sure to check if it lets you exchange calls with people who aren’t subscribed to the same app or platform.
How to Hide Your Caller ID During an Anonymous Call
You can take your anonymity one step further by hiding your number from the person you’re calling. There are several ways to go about this, and we listed them all below:
Using Prefixes
More technically known as vertical service codes (VSC), prefixes are number and/or symbol combinations you can use to activate or deactivate specific phone features. Some prefixes allow you to mask your caller ID before you hop on a call. Simply add the code to the beginning of the number you want to call, and it will automatically hide your number from the receiver.
 *67 is one of the most widely used and popular prefix codes
*67 is one of the most widely used and popular prefix codes
The prefix you need to use will depend on your location and phone service provider. Here are the common codes that hide your caller ID:
| Prefix | Country/Service Provider |
|---|---|
| *67 | United States (except AT&T), Canada (landline), New Zealand (Vodafone) |
| #31# | United States (AT&T), Canada (mobile), Australia (mobile), France, Germany, Israel (mobile), Italy (mobile), Spain (mobile), Netherlands (KPN), Denmark, Sweden, Switzerland (mobile), Greece (mobile), South Africa (mobile), Albania, Argentina (mobile), Bulgaria (mobile) |
| *31# | Germany, Switzerland (landline), Argentina (landline) |
| 1831 | Australia (landline) |
| 3651 | France (landline) |
| *31* | Netherlands, Iceland, Greece (landline), South Africa (Telkom), Romania |
| 133 | Hong Kong |
| *43 | Israel (landline) |
| *67# | Italy (landline) |
| 184 | Japan |
| 0197 | New Zealand (Telecom or Spark) |
| *9# | Nepal (NTC) |
| *32# | Pakistan (PTCL) |
| *23 or *23# | South Korea |
| 067 | Spain (landline) |
| 141 | United Kingdom, Republic of Ireland |
Using Phone Settings
While using prefixes is handy for keeping your caller ID hidden, it’s not foolproof. If you forget to input the code before making a call, your number is immediately exposed. To prevent this, you can hide your caller ID by default using your phone’s settings.
On Android
- Open the Phone app.
- Select the menu button (three dots in the upper-right corner).
- Tap Settings.
- Scroll down and find the Call Settings category.
- Choose More settings.
- Click on Show my caller ID.
- Select Hide number.
On iOS
- Open the Settings app.
- Select Phone.
- Scroll down, then tap Show My Caller ID.
- Click on the toggle button to turn the function off.
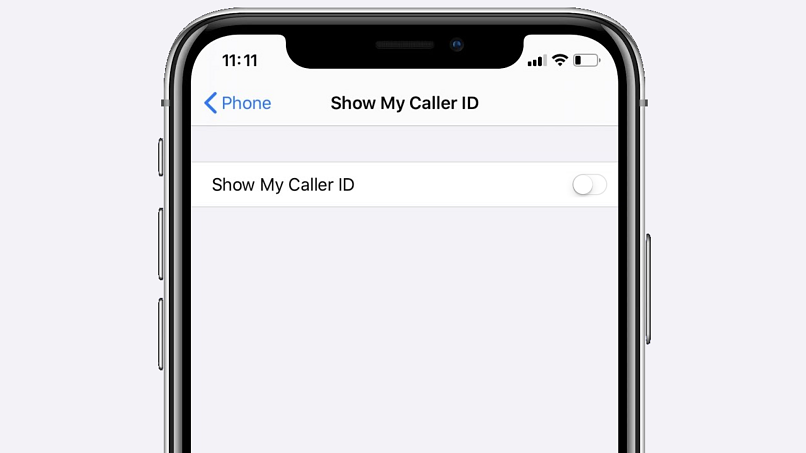 Caller ID is disabled if the toggle is white and on the left side
Caller ID is disabled if the toggle is white and on the left side
Using Google Voice
Google Voice offers users brand new US phone numbers for calling, texting, or leaving voicemails. It allows you to sync communications across smartphones and the web, transcribe voicemails, automatically block spam, and forward calls to any device. But for the privacy-conscious, one of its more attractive features is how easy it is to make anonymous calls.
You can conceal your caller ID for all calls made through Google Voice. When you make this your default setting, it applies to all devices using the same Voice account. This ensures you won’t accidentally reveal your number when placing a call using a different device.
You’re eligible for a Google Voice account if you’re either of the following:
- US-based Google Account owner
- Google Workspace customer based in the US, the UK, Canada, France, Spain, Portugal, the Netherlands, Sweden, Switzerland, or Denmark
Here’s how to permanently hide your caller ID on Google Voice:
On Android and iOS
- Open the Google Voice app on your device.
- Tap the Menu ≡ icon in the top-left corner.
- Select Settings.
- Toggle on Anonymous caller ID under Calls.
On a Computer
- Open your browser and go to https://voice.google.com/.
- Sign in using the Google Account linked to your Voice number.
- Go to the page’s top-right corner and click on the Settings ⚙️ button.
- Select Calls.
- Toggle on Anonymous caller ID.
How to Text Anonymously
Anonymous texts are handy if you expect multiple responses from the person you want to contact. Also, it allows you to extend your communication beyond just a few minutes or calls. To send text messages anonymously, follow the steps below.
On WhatsApp
WhatsApp doesn’t come with a feature to hide your account ID, which makes it hard to message someone anonymously. Still, you can contact someone without revealing your identity. You only have to use a number that won’t allow the other person to identify you. You can use any line that’s not saved on their contact list, but it’s better to use a brand-new number to reduce the chances of them tracing the call back to you.
 WhatsApp works on iOS 12 and newer versions
WhatsApp works on iOS 12 and newer versions
Using a Virtual Private Number
- Find a virtual private number provider online and generate a temporary number.
- Open WhatsApp and register using your temporary number.
- Wait to receive the verification code from your virtual private number provider.
- Enter the code on WhatsApp and finish setting up your account. Make sure you don’t enter any personal information that could identify you.
- Follow the instructions depending on your device’s operating system:
- For Android: Tap the message icon ? in the lower-right corner.
- For iOS: Go to the Chats section and tap the new chat icon ? in the top-right corner.
- Select the person you want to message from the list or create a new contact.
- Type your anonymous message and click on the send button.
Using a Burner Number
- Purchase a burner phone from your nearest convenience store or supermarket, such as Walmart.
- Open WhatsApp on your smartphone and register using your burner number.
- Wait to receive the verification code on your burner phone.
- Follow the same steps 4–7 as described above.
Using a Payphone
- Find the number posted on the payphone. If you can’t see it, call your personal phone using the payphone and note the number.
- Open WhatsApp on your smartphone and register using the payphone’s number.
- The verification will fail if you don’t enter the code after a few minutes. When that happens, it will offer the option to call the number. Select Call.
- Wait to receive the verification code via call on the payphone. Then, follow the same steps 4–7 as described above.
From a Computer
Many free websites allow you to send anonymous texts. Here are the common steps:
- Find a reliable, free text service online using your desktop browser.
- On the site, choose a destination country and/or enter the phone number of the person you want to text.
- Type your message, and click Send Text.
Most services only let you send single messages with no opportunity to receive responses. Some will allow you to leave your email address to get replies, but remember to avoid entering your real email address to prevent phishing scams or other cyberattacks. Instead, you can create a temporary address through secure providers or use online email address generators.
To prevent such incidents, avoid giving any personal data, such as your name, birthday, and address. Also, consider using a temporary email address.
Alternatively, you can email a phone number with these steps:
- Create a new email address using a secure provider like Proton Mail or Tutanota.
- Go to https://freecarrierlookup.com/ and enter the recipient’s country code and number.
- Copy the SMS/MMS Gateway Address into the To section of your email.
- Type your message in the email body and tap the send button when you’re done.
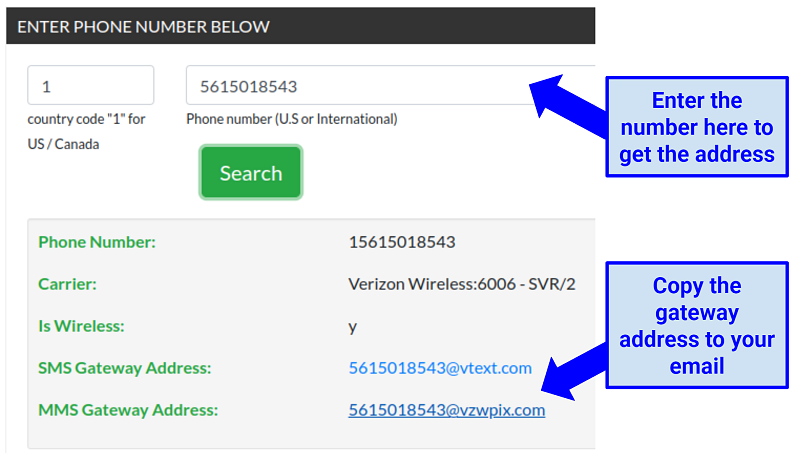 For some carriers, the SMS and MMS gateway addresses are identical
For some carriers, the SMS and MMS gateway addresses are identical
How to Protect Yourself from Scam Callers
While there are many practical uses and benefits to making anonymous calls, they can be used for illicit activities, such as scams or phishing attempts. To protect yourself against these attacks, follow the tips below.
1. Don’t Disclose Personal or Sensitive Information
“Don’t talk to strangers” is a saying that still rings true even with adults today. Scammers have many creative ways to get you to give details you wouldn’t normally share with people you don’t know.
Some gimmicks include pretending to be an agent from your bank and asking for your account and card details. Other times, someone may try to trick you into believing you’ve won a prize for a raffle. They would then ask you to send your bank information so they could deposit your winnings. In both examples, the key is to never give them information unless you’ve verified their identity.
2. Avoid Taking Calls From Unknown Numbers
It’s better to ignore unknown numbers if you’re not expecting a call or can’t think of why anyone would need to call you anonymously. Remember that financial, governmental, or other official institutions wouldn’t need to contact you through unknown or blocked numbers.
It’s no longer easy to recognize legitimate calls, as scammers have learned to use voice-to-text synthesizers or recorded messages to make the call sound more trustworthy. So, picking up the phone could open the door for scammers to use heavy social engineering tactics to manipulate you into performing certain actions. These may include providing personal details, divulging bank information, or wiring money to strangers.
Conclusion
In this highly digitized world, anonymity has become an almost relative concept. Information exchange boundaries are defined by how much you value your privacy and security, and your threshold may differ entirely from the threshold of the person next to you.
Still, there are many merits to learning how to hide or protect your identity when calling or messaging someone. This is especially true when you need to share or confirm sensitive information without compromising your safety. That said, it’s important to use our technical knowledge ethically and responsibly so that we contribute to making the digital space safer and more productive.



Please, comment on how to improve this article. Your feedback matters!