Lastline – Keeping Everyone Safe in a Bigger Sandbox
- Please tell me a little bit about yourself and your background.
- Before we get into the specifics of Lastline’s products, can you share your top three tips for businesses and users to protect themselves from cyber-attacks?
- You currently offer three products: Lastline Breach Defender, Lastline Enterprise, and Lastline Detonator. Can you run through each of those products and what they do?
- Who is your target audience for these products?
- How do the sales/revenues break down percentage-wise between the three products?
- How many active customers do you have today? Where are they mainly located?
- Whom do you see as your main competitors?
- How do you see your tools as different and/or better than theirs?
- What methods do you normally use to attract and engage with new customers?
- What are some of the lessons or insights you gained from the WannaCry ransomware attack?
- How do you see cyber-attacks – and the methods of detection – evolving in the next 2-3 years?
- What are your future plans for Lastline?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
What started as a university research project has evolved into a leading commercial product for Chris Kruegel, the co-founder and Chief Executive Officer of Lastline. Alternating between academia and industry, Chris has enhanced and evolved his original malware detection sandbox and engine into a full-fledged enterprise breach protection platform.
In addition to describing the Lastline Breach Protection platform, Chris tells us how Lastline was immediately able to detect the recent WannaCry ransomware attack. He also shares with us the basic security mistakes people are still committing, as well as how he sees the future of security attacks and prevention methods.
Please tell me a little bit about yourself and your background.
I have spent most of my professional career bouncing in and out of academia. I first got involved in the security industry through work that I did during college and I completed a PhD in security in 2002. I enjoyed academia, so I continued on to do a postdoc at the University of California (UC), Santa Barbara.
I always thought I would end up in Vienna, so I returned and spent a few years teaching at the university there. However, I really liked the U.S. university system so I jumped at the opportunity to return and teach back at UC Santa Barbara.
Throughout my professional career, I have always been working on the problem of malware detection. My first effort was a simple portal with a sandbox for analyzing programs, that I developed with Drs. Giovanni Vigna and Engin Kirda, and it became very popular. I quickly realized that this was a core technology that people wanted and needed.
In 2011, I decided to take the technology, and myself, out of the university and into the real world in order to commercialize the analysis engine(s) that Engin, Giovanni and I had developed. This was the beginning of Lastline Inc.
Before we get into the specifics of Lastline’s products, can you share your top three tips for businesses and users to protect themselves from cyber-attacks?
That is a common question and I have a standard answer:
- Keep your systems updated and patched.
- Be careful about how you manage passwords and credentials.
- Adopt a solid degree of awareness and caution.
You currently offer three products: Lastline Breach Defender, Lastline Enterprise, and Lastline Detonator. Can you run through each of those products and what they do?
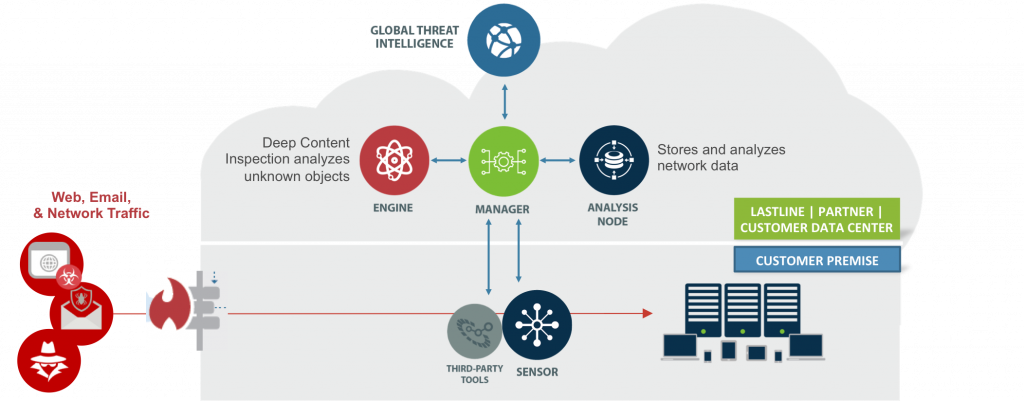
Before I do that, let me describe the elements of our platform. Lastline’s Breach Protection Platform delivers visibility into a breach by generating what we describe as a dynamic blueprint of movement of the attack as it unfolds across your network. The Lastline platform consists of six main components:
- Malware Analytics – Deep visibility into malware behaviors.
- Network Analytics – Detect anomalous network traffic.
- Threat Intelligence – Malware characteristics and behaviors of every malicious object detected by all Lastline customers and partners.
- Breach Analytics – Correlates data from malware and network analytics and threat intelligence to create blueprint of a network breach.
- Breach Response – Manual and automated responses to breaches early in their lifecycle.
- Integration – Our open architecture was designed to complement legacy security investments and optimize existing workflows.
You can see how these components inter-operate in the following diagram:
The different products are really just four different ways of packaging and offering the same core platform:
- Lastline Breach Defender – Our complete solution.
- Lastline Enterprise - Detects and provides deep visibility into advanced malware
- Lastline Detonator – The sandbox and analysis engine along with APIs (for integration into existing workflows and security products).
Who is your target audience for these products?
We do not target any specific verticals. We have found that malware attacks can happen in any vertical, however, large financial services, manufacturing, pharmaceuticals, high tech and retail tend to be more at risk due to the information they must protect.
Our strategy is to promote our products to large enterprises, which typically have 1,000+ users and have an existing security team and SOC (Security Operations Center).
We target Lastline Detonator to OEM vendors and technology partners, and we target Lastline Breach Defender and Lastline Enterprise to large enterprises that have security procedures and staff in place and need an additional layer of breach protection.
We generally target the SMB (Small and Medium Business) market through OEMs and channel partners.
How do the sales/revenues break down percentage-wise between the three products?
Lastline Breach Defender is new and therefore currently a small portion of our revenues, while Enterprise and Detonator are each about half of our business.
How many active customers do you have today? Where are they mainly located?
We currently have several hundred direct enterprise customers and several thousands of smaller companies that buy our software through our partners. We are seeing growth in both of these markets, without them interfering with each other.
Most of our customers are in North America and Europe, each with about 45% of our sales. The remaining 10% of sales is from the Asian region.
Whom do you see as your main competitors?
Our competitors are mainly the big network security vendors, such as FireEye and Palo Alto Networks.
How do you see your tools as different and/or better than theirs?
I think that we differentiate ourselves in three main areas:
- Best core technology – Studies and test have confirmed that Lastline is able to inspect traffic and files much deeper than other approaches.
- Providing context – We are able to combine knowledge and correlate different events in order to provide more context and better enable security analysts.
- Advanced Architecture – Lastline is a modern, software-based solution that is scalable and cloud-ready. It is easy to deploy and to integrate with existing solutions and/or infrastructures.
What methods do you normally use to attract and engage with new customers?
Since we are selling enterprise security solutions, we have a traditional enterprise direct-sales model. We rely on our Marketing organization to create brand awareness and generate interest and leads. Leads are created through a range of marketing campaigns that include outbound emails, webinars, seminars and social media efforts. We also engage with potential customers by attending and speaking at industry conferences.
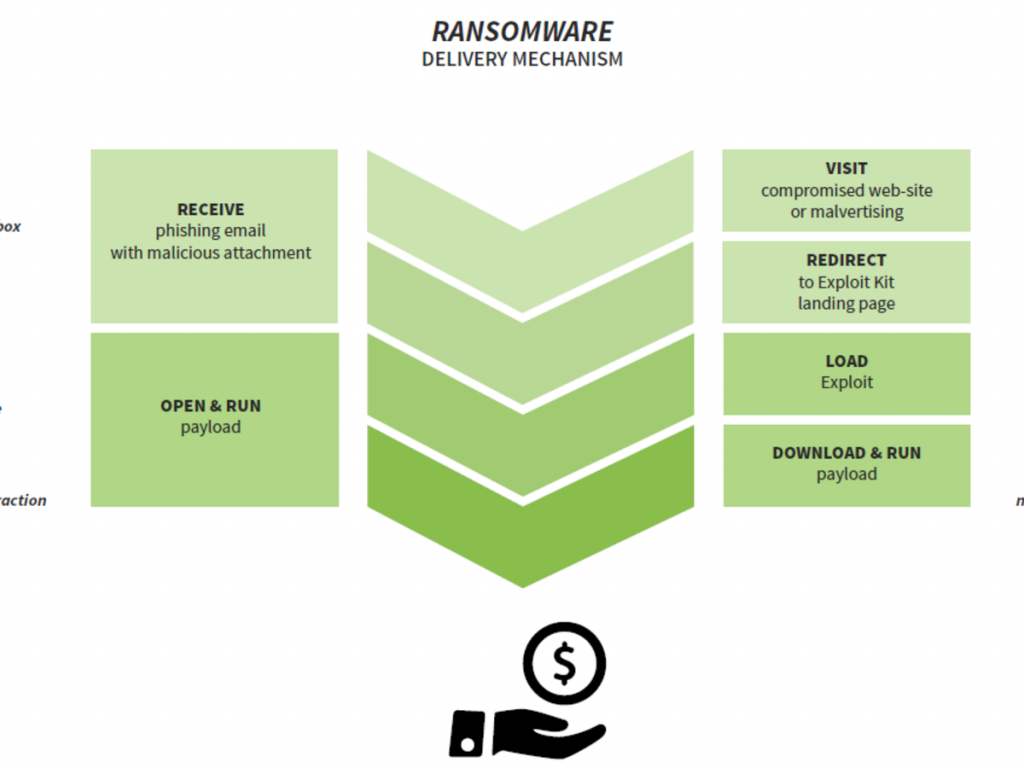
What are some of the lessons or insights you gained from the WannaCry ransomware attack?
I am happy to say that we were totally prepared for it, which made our customers and partners very happy! Our technology immediately detected the malware, so that anyone using our software was protected right from the start. That attack was actually a great proof point for us.
Taking a broader view, I would point out the following:
- WannaCry was an interesting crossover of worm attack and ransomware.
- People are still not following fundamental best practices, such as installing the latest software patches.
- It is surprising to see what makes the news and what does not. There was nothing particularly special about this ransom attack.
How do you see cyber-attacks – and the methods of detection – evolving in the next 2-3 years?
That is a difficult question to predict correctly, but I will do my best.
I expect that we will see the following:
- More use of automation by attackers.
- More IoT (Internet of Things) attacks and issues.
- More use of machine learning and artificial intelligence in the security space to analyze the tons of data that we gather.
What are your future plans for Lastline?
We wanted to move from being “just” a vendor with the best sandboxing technology to taking full advantage of the knowledge and experience that we have accumulated. The next step in our journey was to develop the leading “breach protection” solution that makes it easier for security professionals to recognize and react to security breaches.
This came to fruition with our recent announcement of Breach Defender, which I describe as a complete “breach reasoning” system that will make it easier for security professionals to fully understand and efficiently react to network breaches.
How many employees do you have today? Where are they located?
Our main office is situated in the San Francisco Bay region, while the majority of our workforce, totaling 100 employees, is based in Santa Barbara, California. Additionally, we boast a sizable development team in London, and our sales and support staff is dispersed across various locations globally.
How many hours a day do you normally work? What do you like to do when you are not working?
Good question. I typically work around 60 hours a week, but I do not find it effective to work beyond that.
When I am not working, I enjoy running, sailing, hiking, and just going out with my wife.




Please, comment on how to improve this article. Your feedback matters!