Phantom – Automating Threat Response Across Devices and Applications
- In addition to working at companies like NortonLifeLock and McAfee, you have also founded several security startups – correct?
- How would you describe the differences and tradeoffs of working in large corporations versus startups? You have actually gone back and forth between them – which do you like better?
- The Phantom platform appears to be less of a pure security or preventive product and more of a sophisticated management tool – you describe it as a “security automation and orchestration platform.”
- It seems to me that the two core elements of the platform are Phantom Apps and Playbooks. Can you please explain those to me?
- You also emphasize that the Phantom Platform is “community powered.” What does that mean?
- How do you define your target market?
- What methods do you normally use to attract and engage with new customers?
- How would you describe your current typical customer?
- How do you see your tools as different and/or better than other similar tools on the market?
- Can you share your top three security management tips?
- How do you see the security software market evolving in the next few years?
- What are your future plans for Phantom?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
Just about every enterprise and organization today has in place a large assortment of security devices, software, and procedures to respond to security threats. What they are often lacking, however, is enough trained security personnel to execute the necessary actions. What they are really lacking is time – and when it comes to responding to security threats, time is everything.
Oliver Friedrichs, the founder and CEO of Phantom, describes how Phantom’s community-powered security automation & orchestration platform addresses these issues and drastically reduces the time it takes to respond to a security threat. His stated mission is to use device automation to enable security teams to work smarter, respond faster, and strengthen their organization security defenses.
In addition to working at companies like NortonLifeLock and McAfee, you have also founded several security startups – correct?
Yes, I am fortunate to have had many opportunities to work at great companies, as well as to start three other successful startups before Phantom.
How would you describe the differences and tradeoffs of working in large corporations versus startups? You have actually gone back and forth between them – which do you like better?
I often think that it is a situation where “the grass is always greener…”
The benefit of working at a big company is that it is more stable and there are more resources available. On the other hand, it is harder and slower to make changes within a big company.
The benefits of working at a startup include greater autonomy/flexibility and the fact that a single individual can make a huge impact. However, building something out of nothing requires endless, tireless work - you are the team. Even though we are now 80 people in the company and no one person is solely responsible, there is still a lot of pressure. There are days when it is very tough and you question what it is that you are doing. Then the next day you wake up and feel that you are really lucky to be doing this.
I think it comes down to a trade-off between stability/reliability versus building/controlling. I always like to be building something.
The Phantom platform appears to be less of a pure security or preventive product and more of a sophisticated management tool – you describe it as a “security automation and orchestration platform.”
For the past 30 years, we, as an industry, have been building detection and protection products, such as anti-virus software, firewalls, security gateways, endpoint products, and cloud security products. There are 20-40 different types of security products out there.
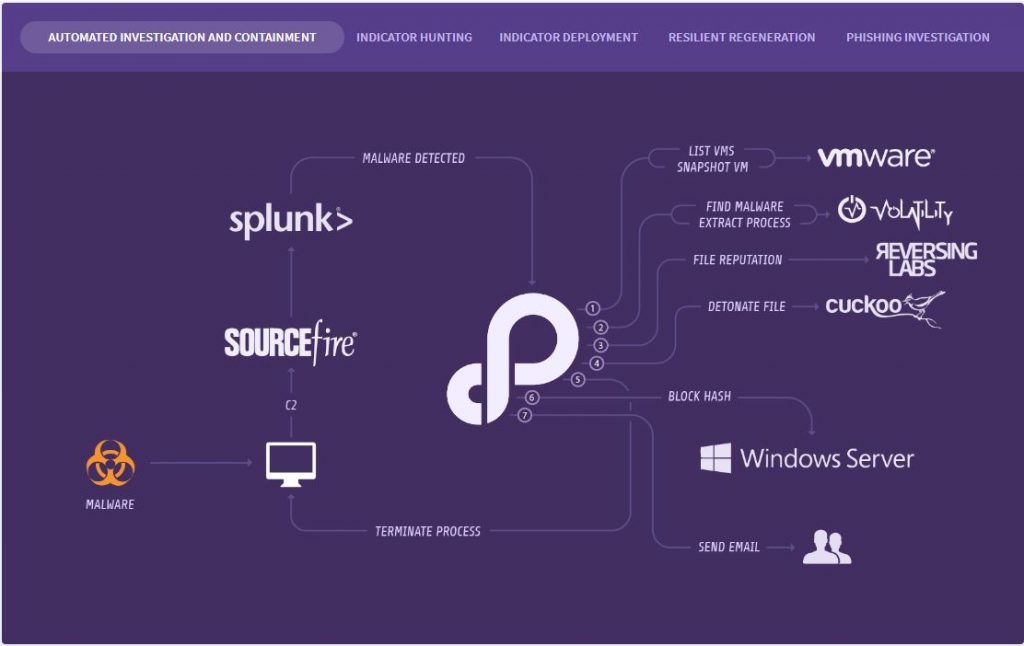
What the Phantom platform does is to provide a layer over all of these products so that they can work together more cohesively. When threats are detected, you need to know how to pivot and to run between the different products in order to address the threat. With our automation playbooks, companies can respond to more threats and respond faster to each one of them. Companies today are already hard-pressed to find and hire good security professionals. Our platform helps security professionals be more efficient and precise.
It seems to me that the two core elements of the platform are Phantom Apps and Playbooks. Can you please explain those to me?
Let us start with the playbooks. Phantom playbooks are simply the SOPs (Standard Operating Procedures) for the security team. They codify and automate the manual tasks that they already doing. By doing so, we can reduce the time it takes to perform those tasks from minutes or even hours down to seconds. For example, a customer might have a process that involves 8 different steps and as many security tools to investigate a malware alert. When they work the process manually it could take 45 minutes or more to pivot through all the security tools. They can also write an automation playbook that integrates with those same tools and executes the process in 30 seconds.
Phantom Apps are the software connectors that integrate our platform to security tools customers are already using. Right now, we support over 670 API’s across more than 135 different security products. There are no additional fees for deploying these apps.
You also emphasize that the Phantom Platform is “community powered.” What does that mean?
We provide well over 50 sample playbooks to the community and members can then share them with others. We get input from the community as well – companies describe their procedures to us in general, and we then formalize it into a playbook.
In terms of apps, about 30% of the apps are written by the community and not by us. We expect these contributors to work for a reputable vendor or to be known in the greater security community. We do our own code reviews of these third-party apps and we normally get the actual equipment into our lab to test it, before certifying it. We are seeing more and more customers wanting specific apps for their environments, so our open, extensible approach to community playbooks and apps has been really valuable.
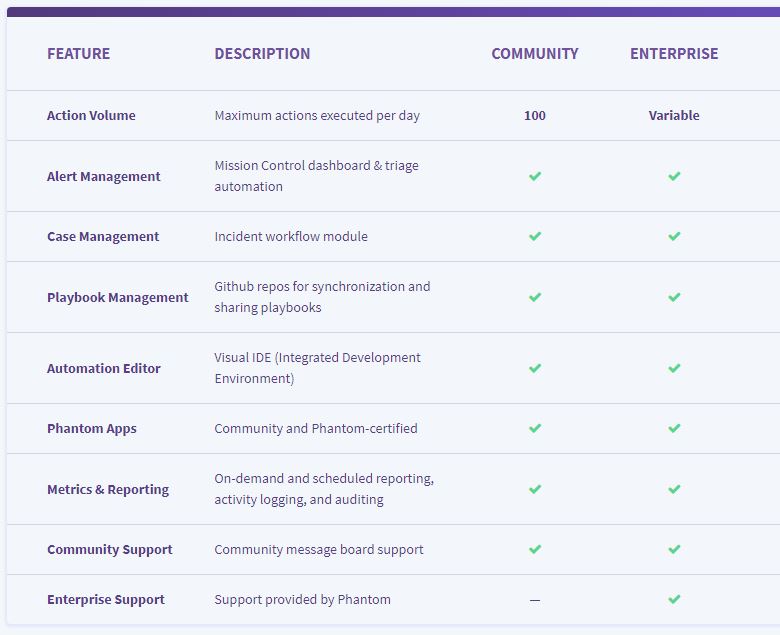
We also offer a free community version of the Phantom platform. This version has all of the functionality of the paid version, but it is limited in the maximum number of actions that can be executed per day. It give you enough free capacity to handle the same number of alerts than a single human analyst could manage. To date, over 5,000 people have registered for the community and downloaded the Phantom platform.
How do you define your target market?
This type of security orchestration and automation is a new category of software that has not really existed previously. However, there are so many security products being used in enterprises that they are almost impossible to manage effective. That is why we think that our approach just makes a lot of sense. We saw this opportunity about three years ago and started working on it right away.
At about the same time, the US Department of Homeland Security (DHS) and the National Security Agency (NSA) initiated the IACD (Integrated Active Cyber Defense) project. IACD is a strategy for increasing the speed and scale of cyber defenses by leveraging automation to integrate the activities of multiple products and services to respond to threats in accordance with an organization’s business rules
It is hard to estimate the size of this market, but some of the analyst firms are saying it a $1 billion+ by 2020. We’ve certainly seen it grow very quickly.
What methods do you normally use to attract and engage with new customers?
We mainly sell directly to large enterprises. We do also have a number of partners and resellers – they are usually system integrators and VARs (Value Added Resellers) who work with customers to build playbooks and apps for their specific environments.
How would you describe your current typical customer?
We used to be very heavily weighted towards companies in the financial sector, but we now have a broader customer profile with well known brands in telecommunications, technology, healthcare, manufacturing, financial services, energy, and the federal government. Two very well-known companies that I can mention are Uber and Rackspace. This slide shows a few more.
How do you see your tools as different and/or better than other similar tools on the market?
The main distinction is that our philosophy and starting point is very different. Existing tools began as “point” products, addressing a specific application or device. We, on the other hand, started out from the very beginning as a platform to integrate with thousands of devices and software applications. As a result, our platform is extremely expandable and extensible.
Can you share your top three security management tips?
Sure. I would say that the following three elements are critical for any enterprise:
- Hygiene – Basic hygiene must be put in place, i.e. patches installed on infrastructure and endpoints.
- Visibility – Use an automated tool to collect security data and events in order to maintain visibility into your environment.
- Response Plan – Have a reasonable response plan in place in order to react to attacks and/or breaches.
How do you see the security software market evolving in the next few years?
I think that we will see a lot of consolidation in the market – and some companies will just die. We probably do not need yet another endpoint or anti-virus vendor. At the same time, there is a great deal of capital looking to invest in this space. There is still a need for additional security products, but they need to be innovative and solve real problems in new ways.
Technology will continue to get smarter – machine learning and AI (Artificial Intelligence) will help make security products somewhat more intelligent.
What are your future plans for Phantom?
Our 3.0 release is coming this summer. It is by far the most advanced evolution of our orchestration and automation platform and includes a lot of new never-seen innovation. With this release, and our future developments, we will continue to empower security analysts even more.
How many employees do you have today? Where are they located?
Our current workforce consists of 80 employees, primarily concentrated at our headquarters in Palo Alto, United States, accounting for approximately 90% of our total staff.
How many hours a day do you normally work? What do you like to do when you are not working?
I do not really keep count, because all I do is work… My average working day is probably 12-14 hours; although these days it is hard to even try to count, since a lot of time is spent researching and reading.
When I am not working, I spend time with my wife who loves to play golf. I also normally manage to get in a 5-mile run every morning.





Please, comment on how to improve this article. Your feedback matters!