Report: e-Learning Platform Exposes Private Data of Students Across the Globe
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a data breach belonging to the Spanish e-learning platform 8Belts.
8Belts is a popular language-learning platform used around the world to teach various languages.
By our estimates, the breach - which originated from a misconfigured Amazon Web Services S3 bucket - affected 100,000s of people across the globe, exposing their private data, and making them vulnerable to dangerous attacks and frauds from cybercriminals.
By not securing its user data, 8Belts compromised the safety and privacy of its users and the future of the company itself.
Data Breach Summary
| Company | 8Belts |
|---|---|
| Located | Madrid, Spain |
| Industry | e-learning |
| No. of people exposed | 100,000s |
| Geographical scope | Global; records originated from almost every country in the world |
| Types of data exposed | Names, email addresses, phone numbers, dates of birth, national ID numbers |
| Potential impact | Identity theft, phishing, financial fraud, viral attacks |
| Data storage format | Unsecured AWS S3 bucket allowing directory listing |
8Belts Company Profile
8Belts was founded in 2011 and is based in Madrid, Spain.
The company offers Spanish speakers online language courses in English, German, French, and Chinese.
8Belts guarantees students can learn any of the four languages within eight months and boasts a 100% achievement rate. It uses modern technology like algorithms and language mapping to innovate language learning and attain such high goals.
While focused on Spanish speaking countries, 8Belts has a global reach, with learners logging in from across the world.
8belts was partly financed by the European Union’s European Regional Development Fund (ERDF) and Spain’s Ministry for Energy, Tourism, and Digital Agenda. It also works with numerous high profile multinational corporations, including BBVA, Huawei, Inditex, and Santander.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the data was stored on an Amazon Web Services (AWS) S3 bucket. AWS S3 buckets are an increasingly popular form of cloud storage, but require users to set their own security protocol. It appears 8Belts had misconfigured its user permissions, exposing all data on the S3 bucket.
Once we confirmed 8Belts as the owner of the data, we reached out to the company and presented our findings. We also offered our assistance in closing the breach before malicious hackers discovered it.
While waiting for a reply from 8Belts, we also contacted AWS directly to notify them of the misconfiguration in the S3 bucket, so they could inform 8Belts of the breach directly.
While we didn't receive a reply, a few weeks later we verified that the vulnerability had been closed.
- Date discovered: 16th April 2020
- Date vendors contacted: 20th April 2020
- Date of 2nd contact attempt (if relevant): 22nd April 2020
- Date of Response: N/A
- Date of Action: 28th May 2020
Example of Data Entries
The breached S3 bucket contained many different forms of data relating to 8Belts users and the platform's internal processes.
The S3 bucket was still live at the time of our investigation, with new records being created even as we were determining the severity of the breach and verifying 8Belts as the bucket’s owner.
The earliest records stated from 2017 and included long lists of 8Belt user details. Stored in CSV format, each of these lists contained the different forms of Personally Identifiable Information (PII) data for individual 8Belts users.
In one list alone, the PII data of over 150,000 people were exposed. Altogether, these lists compromised 100,000s of people.
The PII data exposed in these lists included:
- Full names
- Email addresses
- Phone numbers
- Dates of birth
- Country of residence
Other files in the S3 bucket exposed even more PII of 8Belts users, including students and potentially teachers, such as:
- National ID numbers
- Skype IDs
All of these private data could be combined and exploited in various ways to target those exposed for fraud, theft, and online attack.
While most of 8Belts’ users reside in Spanish-speaking countries, people from all over the world were exposed. Records included data from residents in almost every country on the planet, across six continents.
From the USA to Uzbekistan, Australia to Angola, Belgium to Barbados, this data breach covered the entire globe.
The following screenshot, taken from within 8Belts’ S3 bucket, shows a snippet of a CSV file listing the private data of 1,000s of 8Belts users, along with what appears to be the email addresses of 8Belts employees.
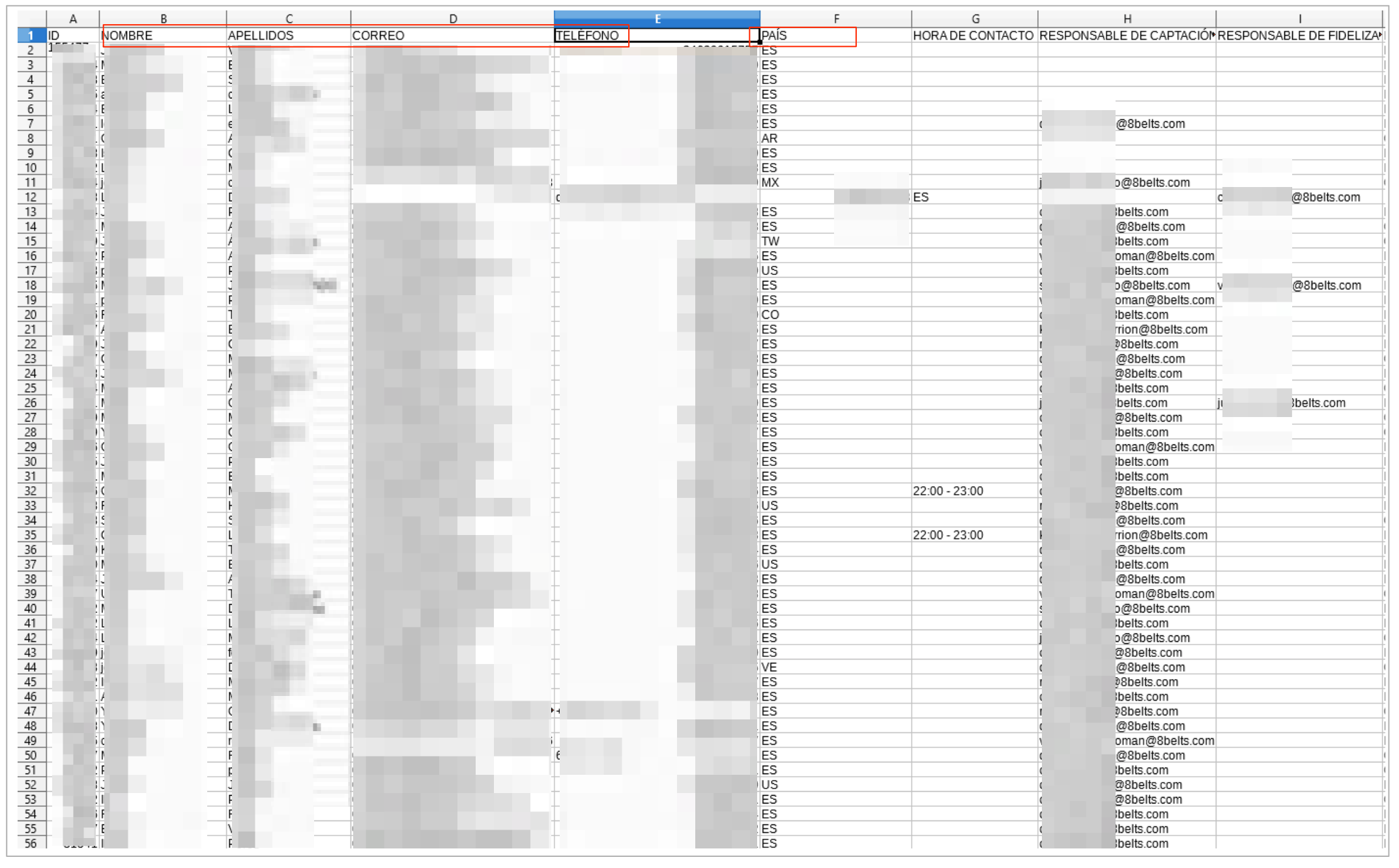
Example #1: CSV file exposing 8Belts user data
Aside from PII data, details of students’ account details, course history and performance were also exposed, including the courses they’d taken, account user IDs, their evaluation scores, and certificates of completion. Virtual 8Belts gift cards to be shared with friends were also accessible via the exposed S3 bucket.

Example #2: 8Belts course certificate of completion
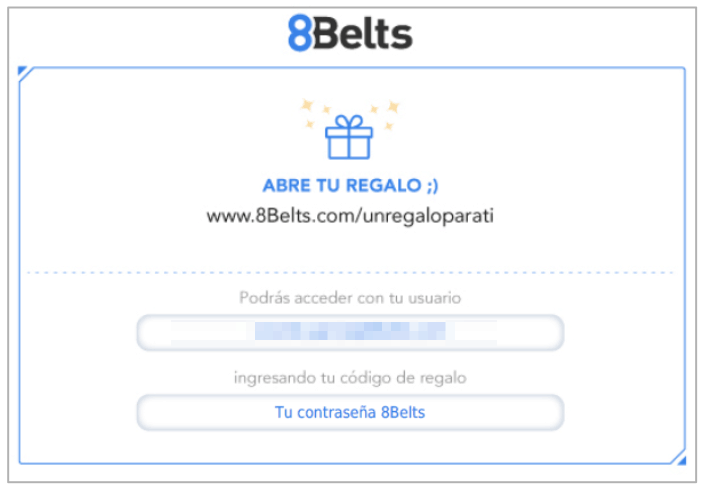
Example #3: Virtual 8Belts gift card
The exposed S3 bucket also contained site logs detailing how 8Belts integrates with external CRM systems. Along with exposing user PII data, these logs also revealed considerable technical information that could be exploited by hackers to gain further access to 8Belts’ platform.
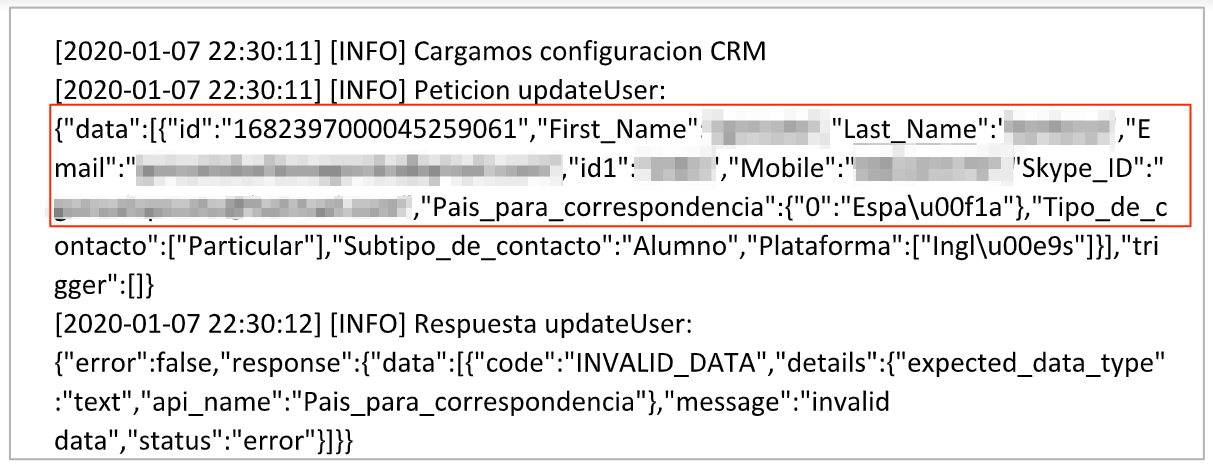
Example #4: A snippet from 8Belts’ site logs
Corporate Clients Affected
Aside from private users, 8Belts is also a popular e-learning platform for large corporations helping their employees learn new languages.
On its website, 8Belts boasts some of the biggest and most well known multinational companies as clients, including:
- Bridgestone
- Decathlon
- Deloitte
- Huawei
- Inditex
- PricewaterhouseCoopers
- Real Madrid
- Renault
- Santander
Just like with individual users, 8Belts stored the PII data of users from their corporate clients within the exposed S3 bucket. However, in this case, many people used their company work email addresses to sign up.
The exposed employee PII data could have created a significant security risk for the companies, as hackers could use employee emails to attack a company’s entire corporate network infrastructure.
By exposing their corporate clients through employee emails and PII data, 8Belts also made these companies vulnerable to crippling fraud and viral attacks from cybercriminals.
Data Breach Impact
This data breach represents a significant lapse in 8Belts’ security protocols.
A company with such a large, global user base must take all necessary steps to protect its customers’ privacy and keep them safe from hacking or other forms of attack.
By not doing so, 8Belts jeopardized the security not just of its users, but also the company itself.
Impact on 8Belts Users
With so much of their PII data exposed, 8Belts users could be targeted by cybercriminals in many ways.
Cybercriminals could use their names, email addresses, phone numbers, and, in some cases, national ID numbers to commit identity theft against 8Belts users.
Victims would then be vulnerable to a wide range of credit, banking, tax, employment, and insurance fraud schemes, with devastating results.
Furthermore, with details of a user’s course history and activity on 8Belts, cybercriminals could create highly effective phishing campaigns to defraud users in other ways.
A phishing campaign involves sending a victim fake emails imitating a real business or organization - in this case, 8Belts. Criminals trick a victim into providing private financial information, credit card details, or clicking a link that embeds malicious software on their internet device.
8Belts is a paid service, so hackers could use this to easily trick students into providing their credit details or clicking a link relating to their subscription.
The misconfigured S3 bucket was exposing PII data belonging to 100,000s of people, so cybercriminals would only need to defraud a tiny percentage of those exposed for an illegal campaign to be financially rewarding.
Impact on 8Belts’ Corporate Clients
Hackers could also use the same tactics outlined above to target corporations with their employees signed up to 8Belts, with far worse consequences for all involved.
As many employees signed up to 8Belts with their company email address, hackers could target these employees with highly effective phishing emails embedded with malware. It would only take one person within a company to click a button in these emails and expose a company’s entire network to attack.
To confirm the reliability of the user data, we verified it by checking the details of several people within the files. In doing so, we were able to confirm that the data was correct, compromised the privacy of those affected, and exposed them (and their employers) to risk.
Phishing campaigns are one of the most popular forms of attack against private companies by criminal hackers. They know most workers aren’t trained to spot phishing emails and are easily tricked into exposing their company’s network to malware, spyware, and more.
The impact of a successful phishing campaign on a company and its employees can be devastating.
Impact on 8Belts
Given the potential severity of this data breach for 8Belts users, the company could also have been made vulnerable.
As 8Belts is based in Spain, the company falls within the jurisdiction of the EU’s GDPR.
Had any of the data been obtained by criminal parties, the company could have faced thorough investigations and security audits, potentially followed by significant legal action and fines.
Considering 8Belts was partly financed by the EU and the Spanish government, you could expect both bodies to respond to such a lapse in data security with even more scrutiny than usual.
Aside from legal or legislative actions, 8Belts risks losing users who no longer trust the company to keep their data safe and decide to cancel any memberships.
Competitors could also exploit the breach to damage 8Belts’ reputation and reduce its market share by enticing its customers to other platforms.
Additionally, if cybercriminals accessed the virtual gift cards stored on the S3 bucket, they could use these to gain free access to 8Belts’ learning platform.
All of these outcomes could have long term negative implications for the company, hurtings its position in the e-learning market, and damaging revenues long into the future.
Aside from potential legal and financial issues, 8Belts could also be targeted for hacking. The exposed site logs revealed could be exploited by hackers to gain further access to 8Belts’ platform, allowing them to plant malicious software or extract even more sensitive data than that which was already exposed.
The impact of such an attack would be immeasurable, and could happen at any time.
Advice from the Experts
8Belts could have easily avoided exposing its users’ data if it had taken some basic security measures to protect the S3 data. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of 8Belts, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For 8Belts Users
If you’re a customer of 8Belts and are concerned about how this breach might impact you, contact the company directly to find out what steps they’re taking.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
During an extensive web mapping project, the breach in 8Belts's cloud storage was identified by the research team at vpnMentor. Our investigative specialists apply port scanning to scrutinize specific IP blocks, probing various systems for potential vulnerabilities or weaknesses. Every identified weak spot is then thoroughly inspected for any signs of exposed data.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to 8Belts, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. 8Belts users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak exposing the data of 1,000s of American energy sector workers. We also revealed how a French technology company compromised the privacy and security of people undergoing plastic surgery around the world. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 01.06.2020]




Please, comment on how to improve this article. Your feedback matters!