How to Secure Your Website and Online Database from Hackers in 2025
The 2016 US election cycle made international hacking part of the global conversation. Hacking is now one of the most widely discussed threats across all professional sectors. While Russian hacking dominated the political sphere, Chinese hacking is proving to be the biggest threat to corporations. Each successive hack reported in the news has made companies increasingly aware of the vulnerabilities in their systems.
Hacks can have a significant economic impact on a company's profits, but it doesn't usually make or break the business. Large companies have the resources to withstand a dip in sales or large lawsuit. However, smaller companies may find that even a small security breach can take down their entire operation.
Any company, large or small, should be committed to making sure their websites and databases are secure, both for the sake of their business and for their customers. No one wants to see their entire infrastructure taken down by a malware attack, nor do customers want their data to be exposed to the world. Hacking is an ever-changing threat that can seem difficult to prevent. However, enacting efficient cybersecurity measures isn't as daunting as it may seem.
How A Hack Can Ruin Your Business
Smaller companies may believe that their unknown status protects them from hacks. Even if you aren't harboring cutting edge trade secrets, small-time hacks can have a large impact on your revenue. Not all hacks are the same, even if they contribute to similar outcomes.
Hackers employ a number of strategies depending on their ultimate goal. The most basic hack your business can experience is simple identity theft; for example, stealing your company credit card and running up fraudulent charges. If you run an e-commerce business, website hacks can lead to thousands of lost customers. When hackers have easy access to your system, they can start by redirecting your site to one of their own.
Here's another example. If your main revenue stream is generated through ad placement on your page, a hacker can steal your revenue by redirecting your site to one with their own ads. While consequences for users are relatively minor in this case, it may still undermine their trust in your site.
Most hackers are far more malicious. They set up dummy sites that look like yours to trick customers into sharing their private credentials. From there, they can easily exploit customers' data.
With all of your customers' data in their own databases, hackers can not only compromise consumer trust in your business but also steal directly from the consumer. Often, customer credentials from one site can help a hacker gain access to several other accounts.
Hackers can use these techniques to steal from you and your customers in multiple ways. Having your site go down even for a few hours can cause a significant decrease in sales. When Sony and Microsoft were hit by a DDoS, or Distributed Denial of Service, attack in 2014, they supposedly lost as much as $40,000 an hour. While this was a big hit for the tech giants, they had the resources to bounce back. For a small business, the consequences would be devasting.
Hackers aren't just looking to steal a person's identity or shut down their system for a few hours. Theft of intellectual property and trade secrets is on the rise. Last year, a former Tesla employee admitted to stealing company secrets before passing them to outside parties. He accomplished this by writing a program that hacked Tesla's software. Experts estimate these kinds of hacks are already responsible for losing millions of dollars of revenue.
There's another caveat to consider. Since 2018, any website operating under the jurisdiction of the EU must comply with the GDPR (General Data Protection Regulation). If the EU discovers that you haven't taken appropriate measures to secure your website, you can be forced to pay a steep fine on top of the losses your business takes because of the hack.
This is why securing your website and databases is one of the most important things you can do to protect your business.
You may think that the costs of securing your website are too high. However, it costs significantly more to be hacked than it does to secure your network. Staying secure is an ongoing challenge, but it's well worth the investment if you want to protect your assets.

Hacking In The Real World
According to a January 2019 report by Cimcor Inc, nearly 60% of small businesses close within six months of being hacked. That's a grim reality for business owners. But small businesses are far from the main targets. Business Insider revealed in August 2018 that 80-90% of login attempts on any retail website are hackers using stolen credentials. In fact, as we revealed in March, 1 in 4 Fortune 500 companies experienced some form of hack in 2018. 20% of these companies experienced more than one hack.
These hacks range from phishing attempts to malware attacks and data leaks. Small companies may appear more vulnerable, but the data shows the opposite to be true. 70% of the top 10 Fortune 500 companies experienced a hack in the past decade. These companies include top banks and insurance firms; in other words, companies whose databases hold sensitive information about their customers.
There's a good reason large companies are more likely to be hacked. Because they have more infrastructure, hackers have a larger "attack surface." This means they have more opportunities to find an opening into their system. Their systems are also more complex than those of smaller enterprises. The more complex a software system, the more bugs there are. More bugs mean more ways for hackers to exploit the system for their own gain.
Losing billions of dollars can be an extreme consequence of a big company being hacked. However, the situation can seem even more desperate when even major tech companies struggle to properly secure their data. Ethical hackers can help companies by finding vulnerabilities in their systems, but making these reports public can also highlight these weaknesses for malicious actors. Hackers can then exploit those weaknesses before the company closes the breach.
The financial repercussions of hacking are clear, but there are other ways that a data leak can deeply impact consumers. Most people worry about the financial fallout from having their account information exposed through a retail site. However, even when credit card information or addresses are obscured, simply exposing a buyer's retail history can be dangerous.
When we revealed a breach in Chinese online retailer Gearbest's database this past March, some of the most sensitive data we accessed were customers' order history and location. For example, we could easily see that a male customer in Pakistan had purchased several silicon dildos in various sizes. Many of the other sex toy purchases we found in the Gearbest database took place in sexually liberal countries. In Pakistan, however, that purchase is far more dangerous.
In Pakistan, both adultery and pre-marital sex are treated as criminal acts, with homosexuality being penalized in a similar manner. Therefore, this client could be subjected to drastic legal repercussions if Pakistani authorities were to uncover his buying history. The same breach also revealed his complete name, residential address, and IP address, facilitating his traceability for local law enforcement agencies. No organization desires to face criticism for subjecting its customers to potential legal proceedings.
Apart from the financial incentives, why else do hackers target companies?

Why They Do It: Understanding The Motives of a Hacker
There are a number of different reasons hackers expose company data. Many aren't looking to push law enforcement into punishing citizens. Some hackers just take pleasure in causing chaos. In these cases, it's more likely that state-sponsored hackers are targeting rival countries to push them into a political crisis. However, if we look at the 2016 American elections, Russian hackers appeared to have several goals.
For starters, this is not the first time Russians have caused a political mess for rival countries. Estonia and Georgia were both targets of DDoS attacks originating from Russia. While the Russians can't hack the voting booths themselves, many believe that their actions served to elect a government that was more sympathetic to Russian interests. Some believe that this chain of events served to weaken a rival country. Politics aside, the perception that a government is secure gets undermined when they're so easy to hack.
However, Russian hackers are far from the only national threat to Western interests. Chinese hacking efforts have continued to increase, despite a brief pause during the Obama administration. The targets of Chinese hackers are generally different than the Russians'. Overall, the Chinese have been behind major corporate hacks in recent years.
Unlike smaller hacks that take advantage of customer data, the Chinese prefer to exploit security vulnerabilities in order to steal trade secrets. Behind these data breaches is a Chinese government mandate called Made in China 2025. Its goal is to make China the frontrunner in global technology and engineering advances. A majority of corporate hacks can be traced to government-backed hacking agencies. These companies have managed to take advantage of security weaknesses to uncover top-secret design plans. Some of these hacks are so stealthy that companies only realize their data has been compromised when a Chinese competitor releases an identical gadget before the original product hits the market.
Even the United States Army isn't immune to Chinese meddling. Shortly after the military debuted two new fighter jets, the F-22 and the F-35, the People's Liberation Army began manufacturing the same jets for themselves. Chinese hackers have targetted every sector of technology including medical technology, aerospace engineering, and robotics. These security breaches might not have the same individual impact but can still lead to significant losses in revenue.
Hacking a company can come with several benefits in one package. In addition to the advantages listed above, the hackers undermine their competition in one key way: customers are less likely to trust a brand that's experienced a public data breach.
With so much at stake when it comes to cybersecurity, you must be wondering what steps you can take to lower your risk of being hacked.
Guide to Securing Your Websites and Servers
The steps to securing your online data vary in complexity, but that doesn't mean they're impossible. You may want to consult with a cybersecurity expert if your business relies on a larger amount of equipment, however, the basics remain the same. Here are some suggestions we advise you to follow to keep your chances of being hacked as low as possible. We'll start with the basics.
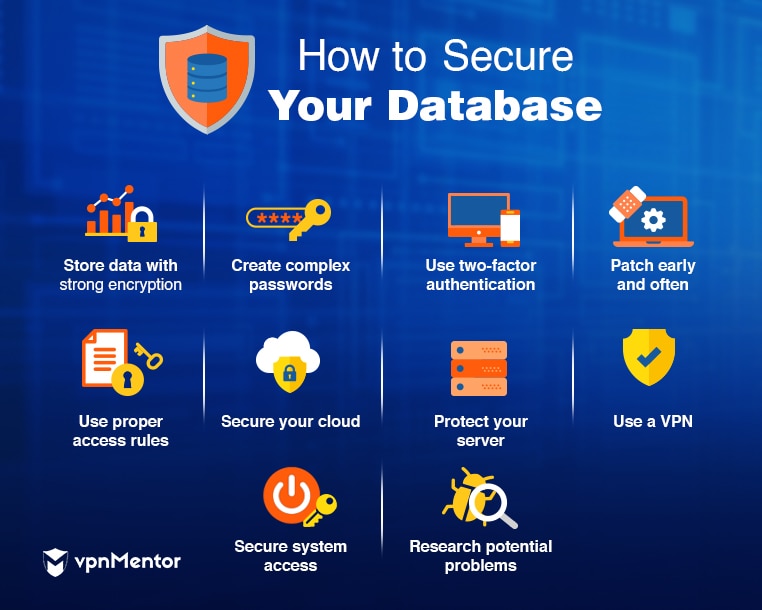
1. Always store your data with high levels of encryption. You may think simply encrypting your data is enough, but there are a number of websites that make it easy to decode low levels of encryption. The higher the level of encryption, the more secure your data will be.
The highest level of encryption currently available is AES 256-bit encryption. This is the standard level that the military uses to safeguard highly classified data. AES-256 is frequently chosen because it's strong but it isn't too computationally intense for the internet. RSA, on the other hand, is also strong, but much slower.
2. Create passwords that are difficult to crack. You may even be better served by a passphrase. A passphrase is a full sentence that can be used in place of a single word. Its length and complexity can make them more difficult to interpret. Passwords should always be longer than eight characters and include a variety of numbers and special symbols. Repeating sequences, such as 123123 are too easy to crack. You should avoid using any identifying information like a birthday in your password.
It's also extremely important to choose unique passwords for every account you have. Using a single password for several accounts can compromise multiple systems if that information falls into the wrong hands. For this reason, it's also a good idea to use a secure password manager or keep your passwords recorded with pen and paper.
In addition to choosing a secure password, you can also use biometric factors like your fingerprint or facial recognition. The unique pattern that makes up a person's fingerprint helps to ensure that others can't just recreate it to unlock your accounts.
3. Employ two-factor authentication. Two-factor authentication requires a second step on top of a password to access a given account. This generally requires you to have a second device that will give you a one-time, temporary code that helps limit access to the account. This way, even if a hacker gets ahold of your password, they are less likely to have the second piece of authorization.
4. Patch early and patch often. Regularly deploying software patches to close up potential attack channels is one of the best ways to keep both your hardware and software safe. Delays in patches can create openings to exploits and published CVEs, which is why it's important to keep your programs as updated as possible.
5. Securing your cloud server: Creating a singular security protocol for cloud servers can be difficult due to the variety of designs. However, they've also proven to be some of the most vulnerable to leaks. You should never assume that the default settings are enough to keep your data secure. Here are some active measures you can take, no matter the server you use, to keep your data protected.
- Assign different access rules if possible.
- Use two-factor authentication.
- Choose strong and unique passwords.
- Create protocols for signing in and out so that an account can't be left open.
- Restrict the devices that can access the accounts, also known as whitelisting.
- Research the vulnerabilities and security procedures of the cloud server you're using. If you choose certain Amazon servers, for example, you need to be aware of whether or not access restrictions are in place before uploading your data.
6. Securing your servers: This is probably the most technical portion of this guide, but it's also one of the most important.
- Sanitize the input in your application. You want to avoid the potential for application vulnerabilities like SQLi, XSS, CSRF. This helps to safeguard against code injection via any inputs or parameters in the site.
- Developers should be knowledgeable about the different kinds of hacking techniques that are used in their specialized areas. This includes understanding common issues and design patterns that can leave the code more vulnerable to hackers.
- Use HTTPS. There are a number of guides for developers that explain in further detail why HTTPS is so important.
- Keep your operating system up to date. This goes hand in hand with software patches.
- Check your server to see if there are any openings that shouldn't be there. Shodan.io is one website that can help you do this.
- Only communicate with the server with encrypted protocols.
- Change any default settings that the server may have been equipped with. This especially includes the admin credentials.
- Research the servers you use. This is a good way to discover any potential flaws in the system. You can only put procedures in place to bypass vulnerabilities and exploits that you know about.
- Whitelist admin panels to specific IP addresses.
- Employ WAF (Web Application Firewall), IDS (Intrusion Detection System), and IPS (Intrusion Protection System) for a multi-layered approach to security. These are multiple approaches to firewall configuration that work better together when used together than any one of them can when used alone.
- Test your website to see if any sensitive data is revealed through the most common attack methods. Hackers often grab information by trying the following techniques, which include banner grabbing, spidering the site, google dorking, and port scanning. Hackers use those methods in order to gather information as to how they can hack your site. If you're unsure of how to perform these tests, this is a good place to ask for help from a professional.
There is no singular way you can secure your servers, however, the more techniques you employ, the more difficult your data will be to grab. This is called "defense in depth" by cybersecurity experts. You may not be able to stop every hack, but you can slow them down by making your system more robust. For a more detailed list of advice on secure servers, you can reference this comprehensive list from rackaid.
7. Use proper access rules. Access rules are the way you can control how users and systems communicate with outside networks and systems. There are several basic rules that should be put in place to maintain a high level of security.
- Give the fewest privileges possible: Modules should only be able to access the information and resources that are necessary for their specific purpose.
- Deny undefined users and anonymous accounts: Limiting access to "good users" who you know and trust can help limit leaks.
- Enforce unsuccessful login limits. A good way to prevent or discourage brute force attacks is by suspending or delaying access to accounts that hit a certain number of failed logins.
These are all elements that should be considered when your system is first being designed. This will help protect your network from the start, rather than having to go back and implement security protocols only after realizing that your system isn't secure.
8. Never leave a system open to the internet without requiring authorization. A lot of easily accessible programs were designed to be used internally within a secure network. Their purpose is to be implemented into a specific system, which means that they aren't equipped with many of the above protocols by default. Many are still accessed from the outside, posing a security risk. To lower this risk, it's best to make sure they are configured without outside access unless it's absolutely necessary.
9. Use a VPN: In conjunction with the steps above, VPNs help protect your data in a number of ways. A good VPN will use its own private servers, so your data isn't exposed to public channels that can be easily exploited. They also encrypt any data traveling between your device and a server. That way, even if there is a leak, your activity will have an added layer of protection. For more information on how to choose a VPN for your business, we've published a helpful guide.
10. Research potential vulnerabilities on your own. The above steps are just the basics when it comes to keeping your system secure. You'll want to continue reading up on subjects such as new exploits and attack vectors. New research on how to find leaks is published regularly. The best way to secure your system is to be aware of the potential threats to your security, even when they may not seem immediately related to your system.
Summary
Having your website hacked or experiencing a database leak can be devastating to your business. When even the top companies have been victims of foreign hacking, it's important to be aware of the possible vulnerabilities in your own system. It's easier to start from scratch with a secure system than to go back and clean up after your protocols are already set. Moreover, if your system wasn't secure from the start, you may not know that you experienced a data breach.
While securing your system may seem like a daunting task, each step that you take makes a difference. You may want to employ a professional to help you implement these suggestions. Hacking techniques are always changing, so be sure to stay up to date on the security measures you've put in place. Being aware is always the best place to start. This guide will just help you to continue to lower your risk of exposure.
Feel free to share and copy this post or parts of it to your site, blog, or social networks. All we ask is that you attribute it to vpnMentor.com
Leave a comment
This is a lot of information that feels OVERWHELMING FOR OVERLOAD to start feels exhausting in confusion making it where wanting to not use the computer at all but it’s necessary for life which is frustrating I’m no where close to security and feel just as lost if not not more in inadequate of what to do there is SO MUCH information on here I didn’t finish responding to read it
Thank you for your feedback! We understand that the information here can feel overwhelming, especially for those new to cybersecurity. To make things easier, consider starting with the basics, like using strong passwords and enabling two-factor authentication—small steps that provide great protection. Your input is valuable, and we appreciate it!






Please, comment on how to improve this article. Your feedback matters!