Report: US Medical Training Company Exposes 10,000s of Students to Fraud in Massive Data Breach
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a massive, incredibly damaging data breach from Phlebotomy Training Specialists.
Phlebotomy Training Specialists is a medical training platform connecting people who are hoping to get certified as phlebotomists with training centers across the USA.
Unfortunately, the company was storing the complete records of 10,000s of students nationwide on a single, open cloud account. By failing to implement basic data security measures, Phlebotomy Training Specialists exposed each individual to a wide range of potentially devastating online attacks and fraud.
Data Breach Summary
| Company | Phlebotomy Training Specialists |
|---|---|
| Headquarters | Los Angeles, California, USA |
| Industry | Medical training |
| Size of data in gigabytes | 157 GB |
| Suspected no. of files | 199,612 |
| No. of people exposed | 27,000 - 50,000 |
| Date range/timeline | Data backed up from September 2020 to present; Files created before this time |
| Geographical scope | USA |
| Types of data exposed | PII data; national ID cards; academic records; much more |
| Potential impact | Fraud; identity theft; phishing; much more |
| Data storage format | Misconfigured AWS S3 bucket |
Company Profile
Phlebotomy Training Specialists is a nationwide private medical training company that operates across the USA.
The company provides hands-on training programs for people hoping to get certified in phlebotomy - the process of intravenously taking blood samples from patients.
The company was founded in 1993.
Timeline of Discovery and Owner Reaction
- Date discovered: 4th September 2021
- Date vendors contacted: 7th September 2021
- Date of 2nd contact attempt (if relevant):8th, 15th
- Date Amazon contacted 15th September 2021
- Date USA-CERT contacted: 20th September 2021 (replied the same day)
- Date of response: N/A
- Date of action: 8th-11th of October 2021
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue is quickly resolved. But rare are these times. We often need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, Phlebotomy Training Specialists was using an Amazon Web Services (AWS) S3 bucket to store data it collected from students, staff members, and people applying to its courses. S3 buckets are an increasingly popular enterprise cloud storage solution. However, users must set up their security protocols manually to protect the data stored therein.
Phlebotomy Training Specialists failed to implement any security measures on its S3 bucket, leaving the contents totally exposed and easily accessible to anyone with a web browser and technical skills.
Upon discovering the exposed cloud account, we quickly identified Phlebotomy Training Specialists as the owner.
Once we confirmed that Phlebotomy Training Specialists was responsible for the data breach, we contacted the company to notify them and offer our assistance. After two attempts at contacting the company and receiving no reply, we reached out to AWS to see if it could assist in closing the breach as the host company.
However, this also proved unsuccessful, so we contacted the United States Computer Emergency Readiness Team (US-CERT). While they replied the same day asking for more information, that was the last we heard from them. A few weeks later, US-CERT closed our support ticket on their website.
Example of Entries in the S3 Bucket
Phlebotomy Training Specialists was using the unsecured S3 bucket to store records related to students taking its courses from September 2020 to the date of publication (October 2021). This means students at this time may also be affected by the data breach.
Despite the short time, at least 27,000 students (past and present) were exposed - based on enrollment records.
Furthermore, due to the strict vetting requirements for people working in any medical profession, the records exposed vast amounts of data for each person affected.
Lastly, there were many more records uploaded by course instructors, Phlebotomy Training Specialists staff, course applicants, and more. In total, we estimate up to 50,000 people were exposed - many of whom had no relation to Phlebotomy Training Specialists beyond applying for one of its courses.
In the following sections, we’ll break down the various files, documents, and Personally Identifiable Information (PII) data exposed in Phlebotomy Training Specialists’ account.
ID Cards and Driver Licenses - 1,900+
These were most likely submitted by course applicants.
They expose:
- Names
- Dates of birth
- Photos
- Addresses
- Physical descriptions


Resumes and CVs - 2,500+
Each document revealed a massive amount of information about a person’s life, including:
- Names
- Phone numbers
- Email addresses
- Professional and educational summaries

Highschool Graduation Documents - 13,600+
These mainly consisted of photos of diplomas to prove applicants had graduated high school.
They exposed:
- Names
- The high school that the student graduated from

Enrollment and Tracking Forms - 27,000+
Based on the text in the documents, Phlebotomy Training Specialists is required to track its students after graduation.
These forms included vast amounts of data collected from Phlebotomy Training Specialists students by its staff. This information includes:
- Names
- Phone numbers
- Gender
- Home addresses
- Last 4 digits of a person’s social security number
- Email addresses
- Dates of birth
- Ethnicity
- And much more
![]()
Student Transcripts - 19,600+
The company also stored the transcripts of individual students progressing through its courses and recorded their results for various courses. Each one exposed the following PII data:
- Names
- Student ID numbers
- Home addresses
- Email addresses
- Phone numbers
- Complete course details and test scores

Training Certificates - 19,700+
These appear to have been issued by the company to successful students who completed various training programs. These exposed their:
- Names
- Date of graduation (or when the certificate was given)

CaPPT Documents - 3400+ Non-completed; 1800+ Completed
The “California Phlebotomy Practical Training” (CaPPT) appears to be a phlebotomy training program or regulation specific to the US state. Thousands of forms related to the CaPPT were also stored on Phlebotomy Training Specialists’ S3 bucket.
They included additional PII data, such as:
- Names
- Home addresses
- Phone numbers
- Training dates
- Laboratory in which a person trained
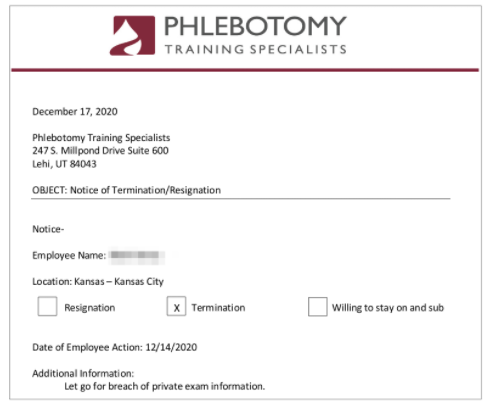
Internal Phlebotomy Training Specialists Documents - 1,200+
Aside from storing its student records out in the open, the company was using the same unsecured S3 bucket to store records and internal documents related to instructors. These included resumes, diplomas, termination/resignation notices, and much more - each of which exposed various forms of PII data for 100s of people connected to the company.
Course Vouchers - Approx. 1,000
The least harmful information it exposed were a collection of vouchers for Phlebotomy Training Specialists courses. While the impact of these would be limited, hackers and cybercriminals could find creative ways to use them in scams targeting the company or individuals.

Impact On Phlebotomy Training Specialists' Students
Identity theft
Had malicious hackers or cybercriminals discovered Phlebotomy Training Specialists’ AWS account lying out in the open, it would have been an absolute goldmine for wholesale identity theft.
By combining the thousands of IDs, high school diplomas, resumes, course transcripts, and more, they could have easily built a complete profile of the people it exposed and used these to steal their identities. It’s likely that any missing information, such as their social security numbers, could also be easily obtained using the information leaked by Phlebotomy Training Specialists - to even more devastating effect.
After successfully stealing a person’s identity, cybercriminals can engage in a wide range of illegal activities, making themselves rich at someone else’s expense - and the victim probably wouldn’t find out until it’s too late and their life was already thoroughly ruined.
However, due to the nature of this data breach, identity theft is far from the only risk to the people exposed.
Phishing
Even if the exposed data wasn’t sufficient to exploit for criminal gains, it could still be used to carry out complex phishing campaigns.
In a phishing campaign, criminals send victims fake emails and text messages imitating real businesses and organizations. By building the victim’s trust, they hope to trick them into any of the following actions:
- Providing additional PII data (i.e., social security numbers) or private information (i.e., bank account details) that can be used in the fraudulent activities listed above.
- Inputting debit or credit card details into a fake payment portal, so they can be scraped and used by criminals or sold on the dark web.
- Clicking a link embedded with malicious software that infects a user’s device, such as malware, spyware, and ransomware.
Due to the number of people exposed in this data breach, cybercriminals would only need to successfully scam a small percentage for any criminal scheme to be considered successful.
The risks of a successful phishing attack are heightened in this case because many of the people involved will now be working at medical facilities. Such facilities are considered high-value targets by cybercriminals, who can demand high ransoms by threatening to disrupt patient care, destroy records, and inflict devastating and potentially fatal damage. Cyberattacks on hospitals and medical institutions have been on the rise in recent years as a result.
Various Forms of Fraud
Upon successfully utilizing the leak, a cybercriminal could engage in a range of fraudulent activities, including but not limited to wholesale identity theft or phishing, enabling them to carry out any of the following fraudulent actions:
- Tax fraud
- Insurance fraud
- Mail fraud
- Bank account takeover
- Debit or credit card fraud
- Mortgage fraud
- And more…
Malicious hackers could also use the records stolen from Phlebotomy Training Specialists’ data to create scams posing as phlebotomists and convincing people to hire them. Aside from the financial risks of such a scam, there would also be a health risk to any victims provided an inaccurate or wrong diagnosis by someone fraudulently posing as a medical professional.
Selling the Data on the Dark Web and Telegram
Aside from using the stolen data themselves, cybercriminals could have profited by simply selling the data to other criminal parties online. The trade of stolen data on the dark web is enormous, with hackers selling various types of valuable data back and forth with almost no fear of punishment.
Even more insidiously, malicious hackers could simply give the stolen data away. As we’ve reported previously, the social network Telegram has become hugely popular for skilled and amateur hackers to share stolen data and tips on exploiting it.
Finally, much of the data exposed in this breach is permanent and can never be changed. For example, the victim of a hack can change their phone number, credit card, and email address. However, you can’t change the high school you graduated from, your social security number, or personal details like your date of birth.
Once this information is out in the open, it can be used against you repeatedly for the rest of your life.
For The Company
Phlebotomy Training Specialists also faces several negative outcomes from this data breach. Hopefully, we were the only parties to discover the exposed data, thus preventing any attack or fraud committed against the company by malicious and criminal hackers.
However, the Phlebotomy Training Specialists may face scrutiny from government regulators for leaking the data in the first place. As a considerable amount of the data came from California, the company may fall within the jurisdiction of the CCPA law, resulting in potential fines and legal action.
Former and current students may also threaten to sue the company for compromising their privacy and security.
Finally, Phlebotomy Training Specialists could lose a lot of business. Aside from the negative publicity generated by legal and regulatory actions, competitors may use the data breach to entice students and partners to rival training programs by claiming Phlebotomy Training Specialists is unsafe to work with. There are plenty of phlebotomy training schools in the US offering similar courses that will embrace any opportunity to chip away at Phlebotomy Training Specialists’ market share.
Each of these outcomes could inflict long-term damage on Phlebotomy Training Specialists and its ability to operate in the US.
Advice from the Experts
Phlebotomy Training Specialists could have easily avoided exposing its customers’ data if it had taken some basic security measures. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of Phlebotomy Training Specialists, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For Phlebotomy Training Specialists' Students
If you’ve trained with Phlebotomy Training Specialists and are concerned about how this breach might impact you, contact the company directly to find out what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered Phlebotomy Training Specialists’ data breach as part of a huge web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in its online security. We reached out to Phlebotomy Training Specialists to let it know about the vulnerability and suggest ways to secure its system.
These ethics also mean we carry a responsibility to the public. Phlebotomy Training Specialists' users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence or way of knowing whether the data in our reports has been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included exposing the growing popularity of cybercrime groups on Telegram. We also revealed how a popular Chinese game developer was leaking data from over 1 million people. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.




Please, comment on how to improve this article. Your feedback matters!