Report: Israeli Telecom Company Exposes Customers in Leaked Support Chats
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a breach in a database belonging to Israeli telecommunications company Annatel.
The leaking database was exposing private conversations between Annatel customers and company agents. Throughout these conversations, Annatel customers provided sensitive personal data and access credentials to their online accounts with the company.
All this information was being leaked publicly, exposing both Annatel, and its customers to fraud and attack.
We also have reason to believe that another system belonging to Annatel was hacked in a separate incident, based on the conversations exposed as part of this leak.
Company Profile
Founded in 2004, Annatel provides telecommunications products and services to French- and English-speaking people living in Israel.
It offers a wide range of products for connecting their customers to family and friends outside Israel, along with internet and phone packages within the country.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake and who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the Firebase database was labeled with the company’s name, “Annatel”. Furthermore, every conversation is between “Annatel” and another party.
As a result, confirming Annatel as the owner of the database was straight forward. Once we confirmed the nature of the leak, we shared our findings with Annatel directly. While the company replied to our initial emails, the database remained open and vulnerable.
After a couple of days without action, or a suitable response from the company, we notified the Israeli cybersecurity authority of the issue. They responded immediately, and the leak was closed a few hours later, on March 11th.
- Date discovered: 5th March 2020
- Date vendors contacted: 9th March 2020
- Date of Response: 9th March 2020
- Date of 2nd contact attempt: 10th March 2020
- Date of contact with Israeli cybersec authority: 11th March 2020
- Date of Action: 11th March 2020
Example of Entries in the Database
The leaking database was hosted on Google’s Firebase platform, containing Annatel chat records with their customers. Firebase is a platform for web and mobile apps, that also provides cloud storage.
The database was leaking over a thousand chats, without any dates, and mostly in French.
The private personal user data being exposed through the leaked chats included:
- Full names
- Email addresses
- Login credentials for Annatel accounts, when shared by customers
- Personal information, relating to customer support queries
- IP address
- Personal phone numbers, when shared by customers
- Order numbers relating to Annatel accounts and purchases, when shared by customers
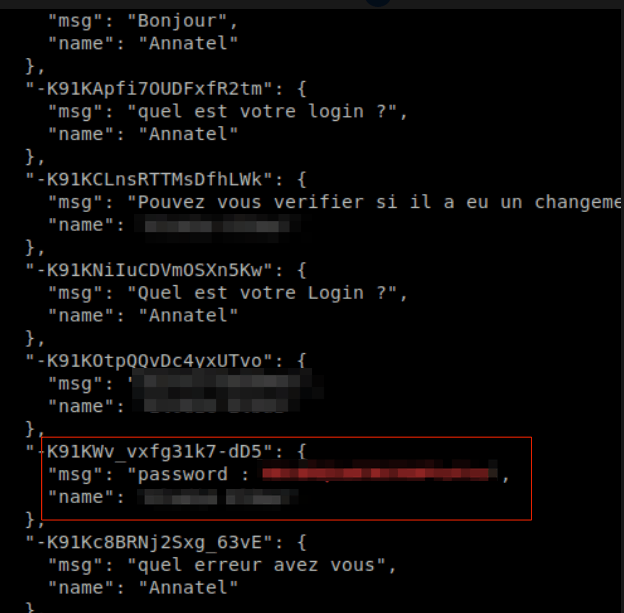
In the following chat extract, an Annatel customer provides her name, along with her account login credentials.
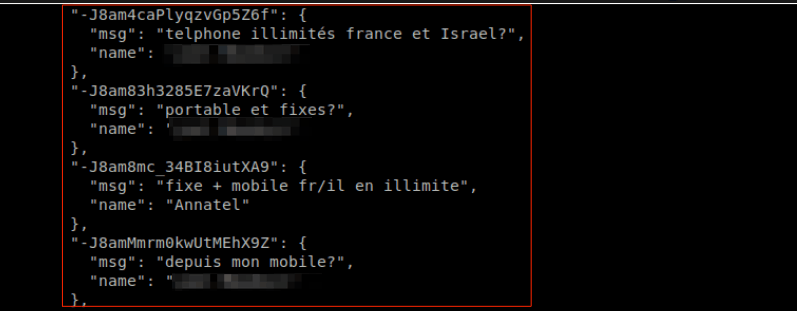
In the next, somebody is merely making an inquiry to Annatel (not yet a customer) and provides his full name.
Potential Criminal Hack
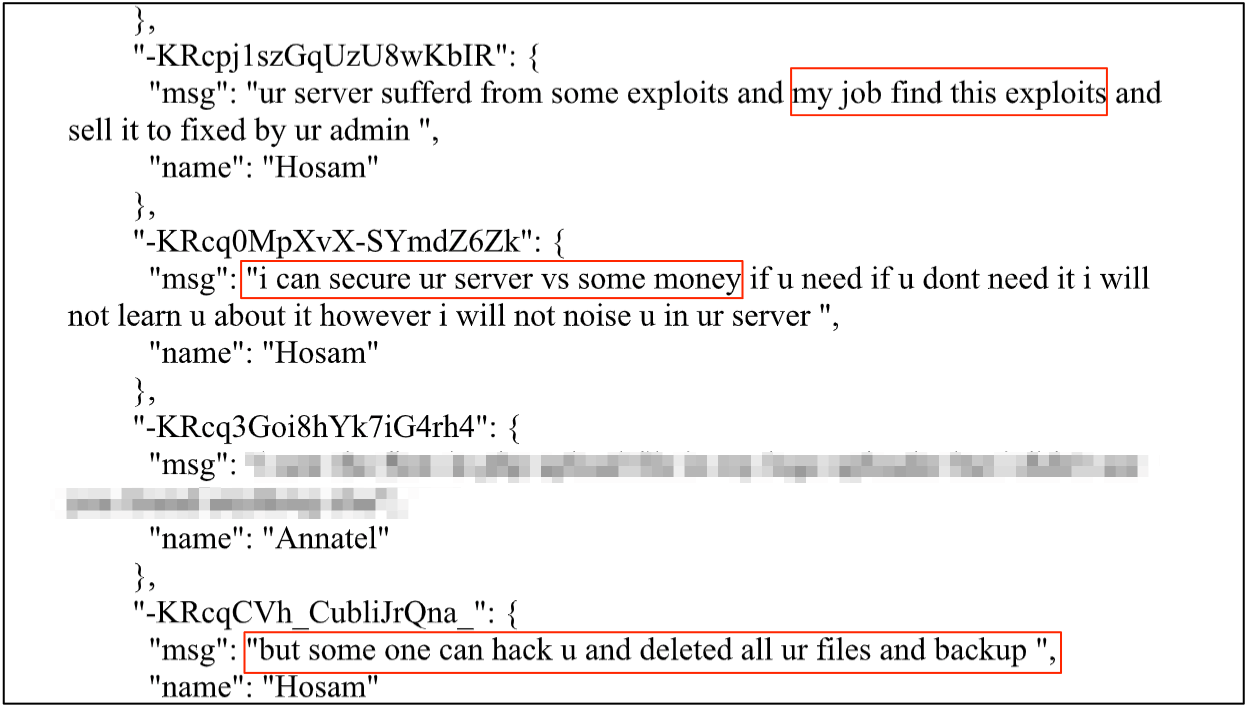
While investigating the database, our team also found a chat record that appears to be between a hacker and Annatel’s staff, including their IT Manager and CEO.
While it’s difficult to verify the details provided by the hacker, calling themselves “Hossam,” they claim to be an Egyptian penetration tester. They also claim to be based in either Hong Kong or mainland China.
Hossam claims to have valuable, sensitive information taken from another database belonging to Annatel, along with details of a vulnerability that gave them access to the database in the first place.

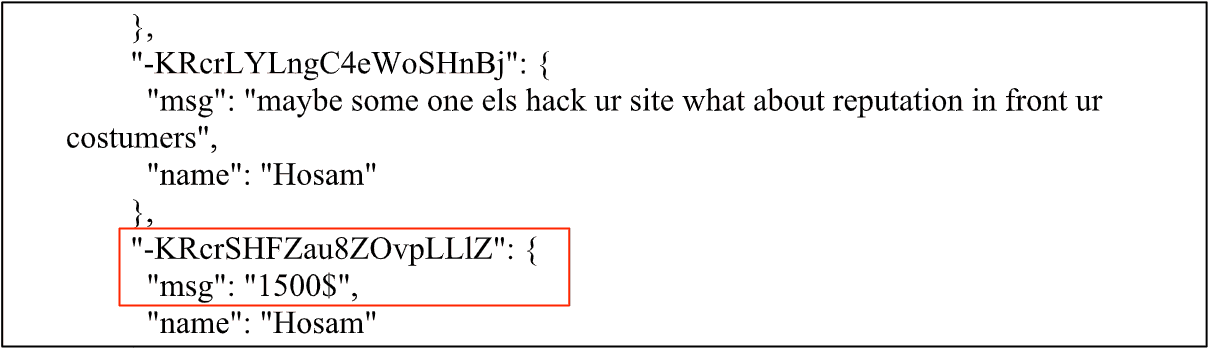
A demand for US$1,500 is made, in return for providing information on the vulnerability and not releasing the details publicly.
Aside from financial motivations, it appears Hossam could be targeting Annatel as a political act, too. At one point in the conversation, they claim solidarity with Palestine. Under such a context, it wouldn’t be surprising that an Egyptian hacker decided to target an Israeli company.
We can’t confirm any details of the chat we read, or how Annatel resolved the issue, as the conversation was quickly moved to email.
Data Breach Impact
If the chat exchange between “Hossam” and Annatel is genuine, it demonstrates the dangers of a company not securing its databases.
Hossam doesn’t explicitly extort or threaten Annatel. Instead, they suggest that unless the company pays them to share the vulnerability (so it can be closed), the exposed data could potentially end up in the hands of criminal hackers.
While Hossam claims to have no interest in letting this happen, the intention is clear.
If somebody shared a flaw in Annatel’s cybersecurity with malicious or criminal hackers, the company would be vulnerable to further attacks and more serious hacking. Likewise, its customers could also be targeted in numerous ways.
As Hossam rightly points out in the chat, this would severely damage Annatel’s reputation and market share. Its competitors can take advantage of the bad publicity Annatel’s brand is going to receive, and snatch their customers.
Competitors could go a step further. The chats exposed in this leak reveal the complaints and concerns of Annatel customers, along with their personal details. If a rival telecom provider came into possession of these chats, they could micro-target Annatel customers with ads addressing their specific issues.
A dishonest - maybe even illegal - strategy, yes, but an effective one.
Impact on Annatel Customers
If the information exposed in this leak reached criminal hackers, Annatel’s customers would be vulnerable to many forms of fraud and online attacks.
The Personally Identifiable Information (PII) revealed in the chats could be used to structure elaborate schemes targeting customers with different forms of identity theft. Furthermore, the login credentials and emails associated with Annatel accounts were openly shared in many chats.
Cybercriminals could use this to take over Annatel accounts and steal from both the company and its customers. If this happened, it would create massive headaches and financial risk to all parties.
By combining a customer’s PII with details of Annatel purchases and telecom packages, a hacker could build effective, targeted phishing campaigns to further inflict damage on their victims.
Using the details revealed in these chats, they could pose as Annatel, requesting additional information or credit card details from a customer. Simultaneously, these emails could embed malware, ransomware, spyware, and similar viruses on a victim's device.
Hackers could then target a single Annatel customer for fraud or theft over and over again, while being almost untraceable.
Advice from the Experts
Annatel could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing their assets.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For more information on how to protect your business, check out our guide to securing your website and online database from hackers.
Securing a Firebase Database
Firebase is a “Realtime Database” built on the Google cloud. It was created for developers building web and mobile apps, along with providing many additional features relating to these areas.
It’s important to note a flaw in Firebase did not cause this leak. Google provides detailed instructions to Firebase users on how to secure their databases and keep them private.
These include:
- Make the Firebase private and add authentication protocols.
- Follow Firebase access, security rules, and authentication best practices.
- Ensure the database has a security-optimized structure
- Create rules and permissions for public users interacting with the database(s)
- Use Firebase’s builtin Simulator to test the security and rules in your database(s)
Follow the instructions provided by Google from the very beginning, and your database should be secure.
For Annatel Customers
If you’re a customer of Annatel and concerned about how this breach might impact you, contact the company directly to find out what steps it is taking.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in Annatel’s database as part of a large web mapping project.
Upon discovering a data breach, our team employs specialized methods to confirm the identity of the database. We then notify the concerned company about the existing vulnerability. Additionally, if feasible, we aim to inform any other parties who might have been impacted by this breach.
Our team was able to access this database because it was completely unsecured and unencrypted.
The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Annatel, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics mean we also carry a responsibility to the public. Annatel customers must be aware of a data breach that affects them also.
We also never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak exposing the data of 10,000s of American restaurant diners. We also revealed that a company owned by European hotel giant AccorHotels compromised the privacy and security of hotel guests around the world. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 16.04.2020]




Please, comment on how to improve this article. Your feedback matters!