Report: Marketing Company Fails to Secure Client Data and Exposes 1,000s to Fraud
Led by Noam Rotem, vpnMentor’s research team recently discovered a data breach from telemarketing company CallX.
CallX sells marketing services and software to enterprise clients, allowing businesses to track the performance of their media buying and telemarketing operations.
Unfortunately, CallX failed to adequately secure audio recordings and text chat transcriptions from its clients. As a result, over 100,000 private files were publicly accessible, compromising thousands of people’s privacy and safety.
Data Breach Summary
| Company | CallX |
|---|---|
| Headquarters | California, USA |
| Industry | Marketing software and services |
| Size of data in gigabytes | 485GB |
| Suspected no. of files | 114,000+ |
| No. of people exposed | 10,000-100,000 |
| Date range | 2014-2020 |
| Geographical scope | USA |
| Types of data exposed | Voice recordings; text messages; PII data |
| Potential impact | Fraud; phishing; regulatory actions and legal issues |
| Data storage format | Misconfigured AWS S3 bucket |
Company Profile
CallX was founded in 2015 and is currently based in Walnut Grove, California, USA.
The company markets technology and services to help businesses track and improve their media buying and inbound marketing operations.
CallX buys advertising and media space on Google, Facebook, and other big websites, funneling leads to its clients’ inbound marketing and chat teams.
From there, leads are directed to book a phone call with a representative from CallX’s client, who markets their products, services, etc. directly on the phone.
CallX’s software provides detailed analytics so clients can track the performance of their marketing campaigns and teams.
CallX appears to be a small company, despite its age. It only has three employees listed on Linkedin, and its website is incomplete. Numerous pages contain ‘Lorem Ipsum’ placeholder text or simply don’t work.
However, the company still boasts plenty of clients, including some well-known brands in the US.

Timeline of Discovery and Owner Reaction
- Date discovered: 24th December 2020
- Date analyzed: 31st December 2020
- Dates vendor contacted: 3rd, 12th, and 25th January 2021
- Dates Amazon Contacted: 6th, 25th January 2021, and 16th February 2021
- Date US CERT Contacted: 22th February 2021
- Date of Response: -
- Date of Action: 7th March 2021
Sometimes, the extent of a data breach and the identity of the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, CallX was using an unsecured Amazon Web Services (AWS) S3 bucket to store audio client files. AWS S3 buckets are a popular form of enterprise cloud storage, but users must set up their own security protocols. Many companies using AWS are not aware of this.
Our team discovered CallX's S3 bucket and was able to view it due to insufficient security. We found an image of the company's logo amongst the files stored on the S3 bucket and, upon further investigation, confirmed the company as its owner.
We immediately contacted CallX to notify it of the vulnerability and provide guidance on securing an S3 bucket.
Example of Entries in the S3 Bucket
In total, CallX was storing over 114,000 files without adequate security.
Most of the files were audio recordings of phone conversations being tracked by the company’s marketing software. There were also transcripts from over 2,000 text chats.
These conversations were taking place between CallX clients and their customers. However, it appears that CallX was storing data from various clients all in one place.
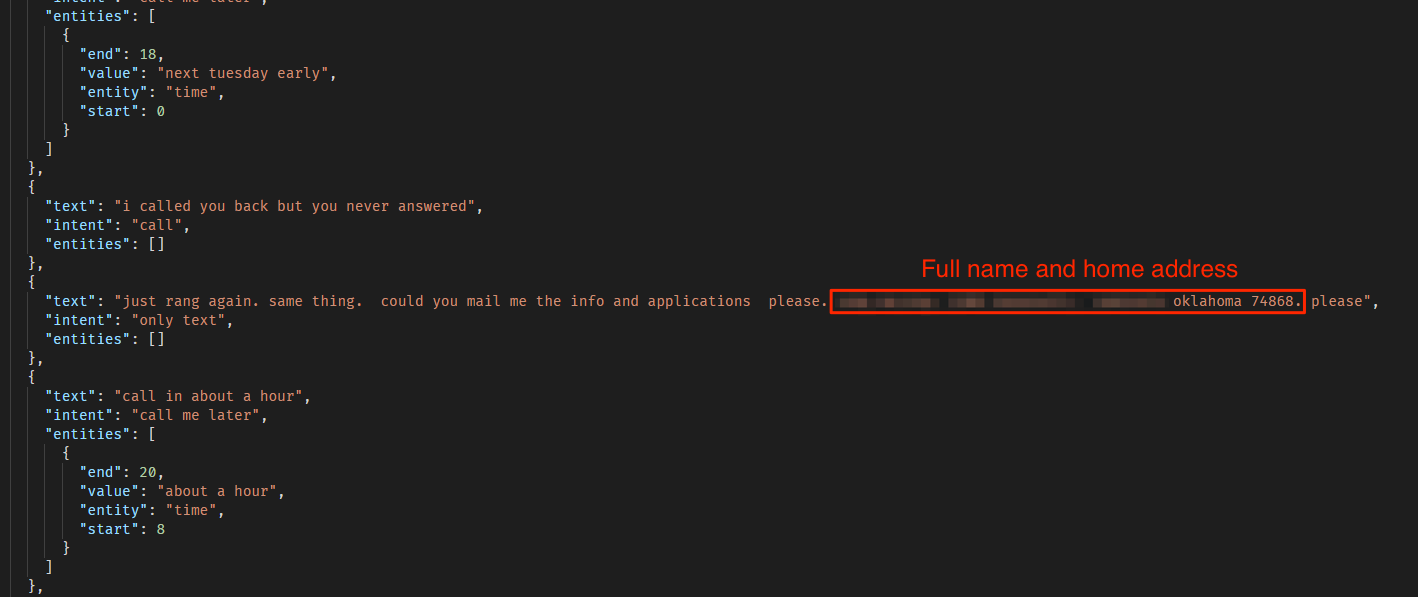
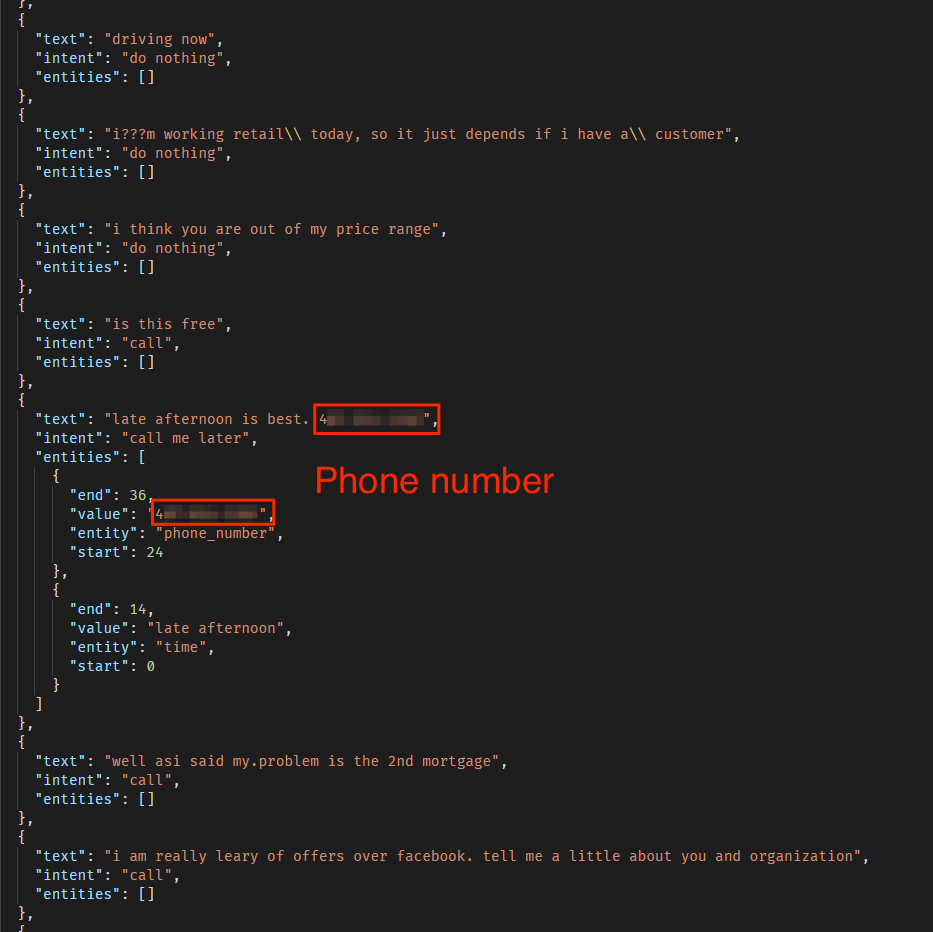
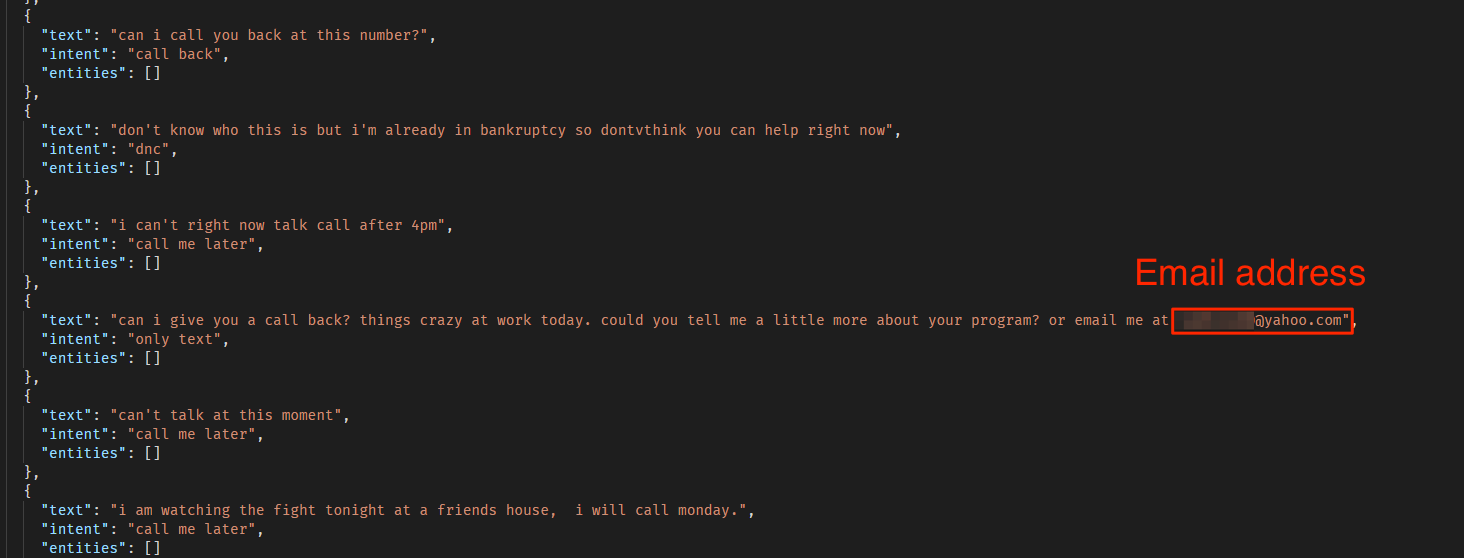
In both the audio and text conversations, customers revealed vast amounts of private data, including:
- Full names
- Phone numbers
- Home addresses
- Callback dates for phone calls
- Additional personal information
Examples from the text chats can be seen below:
It’s unclear how many people were aware that somebody recorded their conversations.
It’s also very likely they would never find out that the company they were speaking to was using CallX’s software. As a result, the people exposed in this data breach may never know their private data was exposed publicly.
Data Breach Impact
Had cybercriminals accessed CallX’s client data, they could have pursued various criminal schemes targeting 1,000s of people.
Each transcript stored on the exposed S3 bucket revealed sensitive Personally Identifiable Information (PII) data and other personal details that could be used in phishing campaigns, financial fraud, and much more.
Furthermore, if cybercriminals needed additional information, they could hijack calls logged by CallX and do fake ‘follow up’ phone calls or emails posing as a representative of the relevant CallX client company. Using the transcripts, it would be easy to establish trust and legitimacy with targets in such schemes.
As the people exposed have no apparent relationship to one another, by the time the fraud was discovered, it may be too late.
For CallX
CallX also faces several dangers as a result of the data breach.
The company is based in California, and many people affected by the data breach probably reside there. As a result, CallX is under the jurisdiction of the state’s CCPA data privacy law. If it doesn’t take adequate measures to resolve the breach, it could face further investigation, legal action, and fines.
Due to the bad publicity a data breach like this can create, CallX’s clients may distance themselves from the company and switch to rival software providers. Those same rivals could exploit the breach to lure CallX clients away through negative marketing campaigns.
Each of these outcomes could be detrimental to CallX’s business and revenue in the short term and long term.
Advice From the Experts
CallX could have easily avoided exposing its customers’ data if it had taken some basic security measures. These include, but are not limited to:
- Securing its servers
- Implementing proper access rules
- Never leaving a system that doesn’t require authentication open to the internet
- Storing data from each client separately
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of CallX, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For CallX Clients
Should you be a user of CallX's software and worry about the potential repercussions of this breach on you or your clientele, it's recommended to get in touch with the company directly. This way, you can ascertain the measures it's employing to ensure the security of your customer data.
We recommend thoroughly vetting all 3rd party software solutions you integrate into your operations to ensure they follow the strictest possible data security practices. Doing so reduces the risk of a data breach, leak, or hack that impacts clients and customers without your knowledge.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in CallX’s data as part of a huge web mapping project. Our researchers use large scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in its online security. We reached out to CallX to notify it about the vulnerability and suggest ways to secure its system.
These ethics also mean we carry a responsibility to the public. CallX users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence - and no way of knowing - whether the data in our reports have been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included uncovering potential criminal activities and scams targeting users on Spotify, Instagram, and Facebook. We also revealed that a group of free VPNs were secretly tracking their users’ activity and data and leaking it online.
You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect the Internet!
Introducing The Leak Box.
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Published on March 3rd, 2021]




Please, comment on how to improve this article. Your feedback matters!