Report: Biggest Baby Clothing Brand in the US Exposes 100,000s of Customers to Hacking and Fraud
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a data breach in an API used by baby clothing apparel giant Carter’s.
The biggest name in the US Baby’s apparel industry, Carter’s, was using a famous URL shortener tool for order confirmations on its USA e-commerce store. However, the company failed to implement proper authentication protocols on the store’s parcel tracking pages. By not doing so, it made these pages easily accessible to anyone online.
Due to the massive volume of sales Carter’s enjoys every year, this simple but drastic oversight exposed 100,000s of people to fraud, theft, and many other dangers.
Data Breach Summary
| Company | Carter’s, Inc. |
| Headquarters | Atlanta, Georgia, USA |
| Industry | Baby and Childrens’ apparel |
| Size of data in gigabytes | Unknown |
| Suspected no. of records | 410,000+ |
| No. of people exposed | 100,000s |
| Date range/timeline | 2015 - present |
| Geographical scope | USA |
| Types of data exposed | Purchase Orders for Carter’s products; Customer PII data |
| Potential impact | Fraud; Identity theft; Phishing; Corporate espionage |
| Type of Data Exposure | Shortened URL |
Company Profile
Carter’s is the biggest marketer of apparel for babies and young children in the USA. The company was founded by William Carter in 1865 and has grown into a global corporation.
In the US, Carter’s accounts for 25% of all baby apparel sales, while the company earns an estimated $3bn in revenue annually.
Linc (https://www.letslinc.com/) is a customer care automation platform that businesses use to improve the customer experience on their websites. Linc offers a range of tools to increase customer engagement, boost sales, and make a website more efficient.
Carter’s was using Linc to create shortened URLs to travel purchases made on its online store.
Timeline of Discovery and Owner Reaction
- Date discovered: 17th March 2021
- Date vendors contacted: 22nd March 2021
- Date of 2nd contact attempt (if relevant): 30th March 2021
- Date of Response: 30th March 2021
- Date of Action: between the 4th and 7th of April 2021
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. We often need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, our team discovered the data breach using specialized scanning software that detects data breaches and vulnerabilities in websites and databases.
We quickly identified Carter’s as the exposed and responsible party and contacted the company to present our findings. In the beginning, their security team didn’t accept our disclosure via email, asking us to report it on Bugcrowd instead and create an account there.
We disclosed to them directly once again and received the following reply from the company:
“We’ve discussed the vulnerability and I wanted to give you an update on where we are. At this time, we’d like to validate and assess impact to our customers. Would you please send us the reproduction steps and more samples of PII data that were exposed? We will reconvene internally as soon as I receive more information from you.”
We shared all the details of the vulnerability with them, which they had to discuss with Linc, the 3rd party providing them with the parcel tracking tool. In the meantime, it appears that Carter’s deactivated the shortened URLs. This modification made the previous URLs exposed in the data breach inaccessible. We hope they implemented the fix for future URL creation.
Example of Exposed Data
This data exposure occurred due to an oversight by Carter’s when automating purchases and deliveries for its US e-commerce store.
Any time someone made a purchase on the store, Carter’s sent them a shortened URL redirecting them to a purchase confirmation page.
However, there were three issues with this process:
- Those shortened URLs were easily discoverable to hackers due to a lack of sufficient entropy or compensating security protocols.
- Carter’s also put no authentication in place to verify that only the person who’d made the purchase could visit the confirmation page.
- The confirmation pages provided by Linc contained vast amounts of PII data and financial information for each person exposed.
- The links never expire. Anyone could use them to access data from orders made on the Carter’s website, no matter how old they were.
The private personal user data we viewed on the confirmation pages included:
- Full names
- Physical addresses
- Email addresses
- Phone numbers
- Shipping tracking IDs and links
- Price paid for purchases, etc
Each order confirmation also contained details of the transactions:
- Breakdown of items ordered
- Tracking ID’s
- Zipcodes
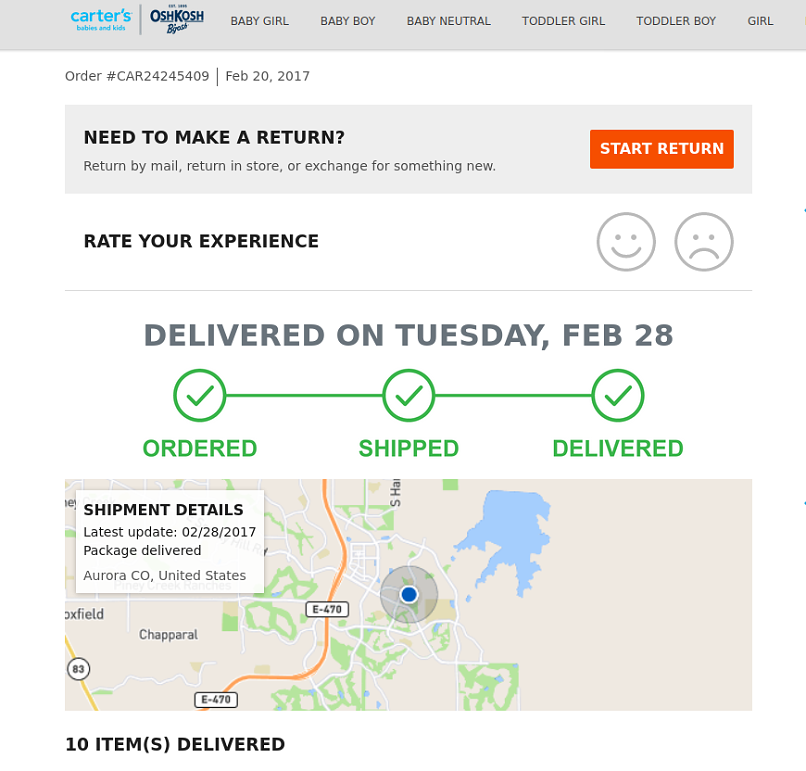 Carter’s delivery confirmation exposed in the data breach
Carter’s delivery confirmation exposed in the data breach
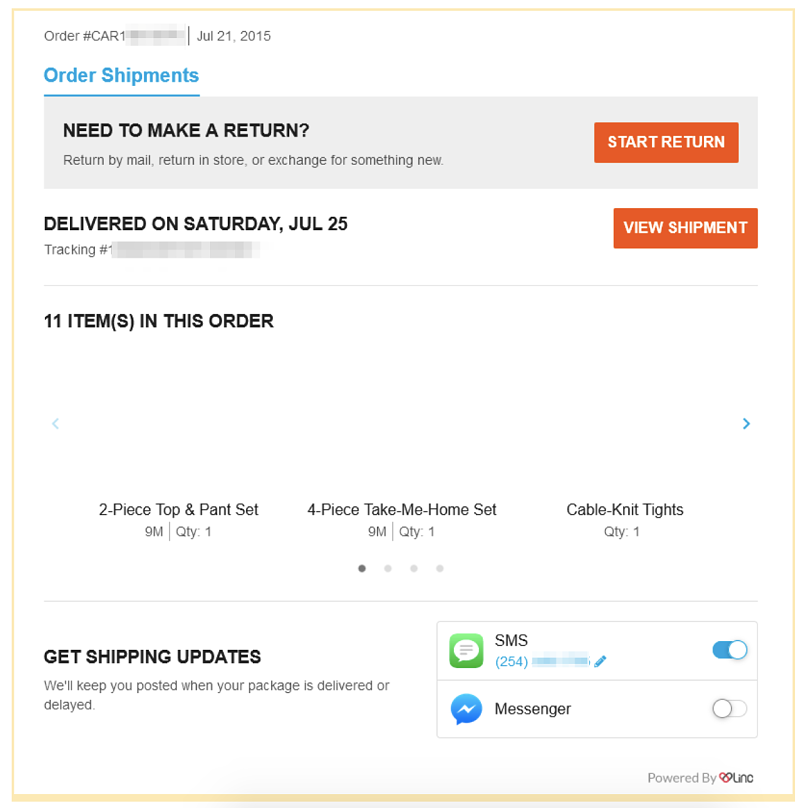 Carter’s delivery confirmation exposing the customer’s phone number
Carter’s delivery confirmation exposing the customer’s phone number
Furthermore, by modifying the Linc URLs (to which the shortened URLs were redirecting), it was possible to access backend JSON data, which revealed even more personal information about customers that wasn’t exposed by the confirmation pages, such as:
- Full names
- Full delivery addresses
- Phone numbers
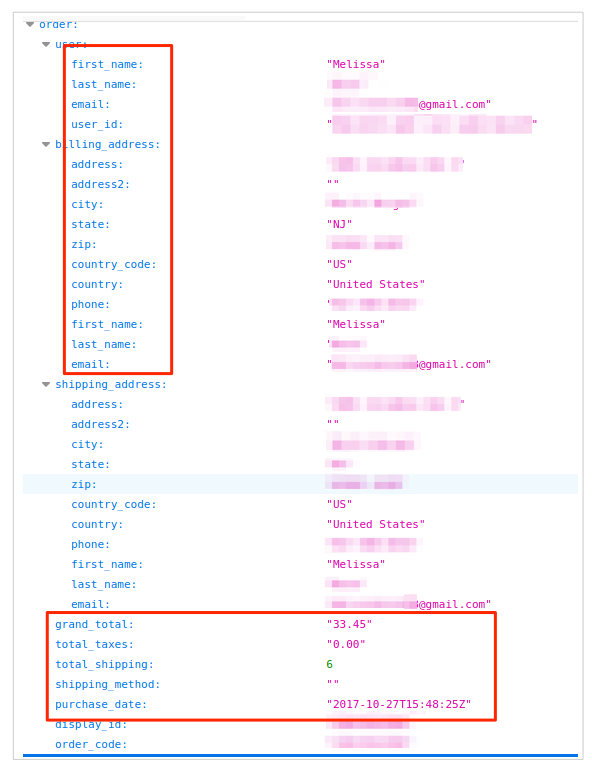 Carter’s customer PII data
Carter’s customer PII data
Data Breach Impact
This data breach could have had severe consequences for 100,000s of Carter’s customers, many of whom may not have interacted with the company for over five years.
Had malicious hackers discovered the vulnerabilities in the company’s URL shortening process, they could have exploited the exposed PII data and purchase orders to target individuals in a wide range of crimes.
Using the details stored in confirmation orders, hackers could easily create fraudulent phishing emails posing as Carter’s and tricking customers into providing additional information, such as credit card numbers or bank account information. Simultaneously, the hackers could entice victims into clicking links embedded with malware, spyware, or various other forms of viral attacks.
For more recent orders, hackers could simply ring up a Carter’s customer to discuss purchases made and pose as couriers or customer support, building rapport with the target and ensnaring in criminal schemes.
Finally, for any purchases still on their way to a customer, hackers could redirect deliveries and steal them, reselling any Carter’s stolen products online.
Impact on Carter’s
By exposing so many customers to fraud and hacking, Carter’s has also made itself vulnerable to fines, legal action, and governmental intervention. Many of the people exposed were California residents, which means the data breach falls within the California Consumer Privacy Act’s jurisdiction.
In light of this, Carter's will have the responsibility of adhering to designated procedures for reporting the breach and taking necessary actions to prevent its recurrence.
Aside from that, the data breach could result in considerable negative publicity for the company and the loss of many customers. The baby apparel industry is a highly competitive space, and Carter’s customers will have plenty of options to shop elsewhere.
Advice From the Experts
Carter’s could have easily avoided this leak if it had taken some basic security measures to protect its customers’ data.
The company should have used a more secure URL shortener solution and seriously consider adding authentication or additional measures to ensure only the intended recipient of the data will have access to it.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For Carter’s Customers
If you’ve shopped online at Carter’s store and are concerned about how this breach might impact you, contact the company directly to determine what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the exposed database as part of a vast web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this data because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the data’s owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Carter’s, to let them know about the vulnerability and suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. Carter’s customers must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach exposing the data of 10,000s of online shoppers worldwide. We also uncovered separate scams targeting users on Facebook, Instagram, and Spotify. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
Leave a comment

Thanks for submitting a comment, %%name%%!
We check all comments within 48 hours to ensure they're real and not offensive. Feel free to share this article in the meantime.


Please, comment on how to improve this article. Your feedback matters!