Report: 10,000s of Online Shoppers Exposed by Popular Shopify App. Personal Data, Credit Cards, And Much More
Led by Noam Rotem, vpnMentor’s research team discovered a data leak originating from a 3rd party Shopify app popular in the dropshipping industry.
While we can’t confirm the identity of the app responsible for the leak (or its developers) with absolute confidence, evidence strongly suggests it was the popular automation tool Topdser.
Dropshipping stores hosted on Shopify use Topdser to connect with suppliers on Alibaba and automate numerous aspects of managing their stores.
Whoever was responsible failed to secure data being processed from Shopify stores using their app.
As a result, data from 100,000s of purchases made on at least 17,000 Shopify stores using the app was exposed.
The exposed data included significant Personally Identifiable Information data and even some credit card details that could be used to defraud and steal from 10,000s of people across the globe.
Data Breach Summary
| Company | Topdser |
|---|---|
| Headquarters | China & USA |
| Industry | e-Commerce |
| Size of data in gigabytes | Over 95GB according to Shodan (13 GB when we discovered it) |
| Suspected no. of records | Over 233 million according to Shodan (~17.5 million when we discovered it) |
| No. of people exposed | 80,000-100,000 when we discovered it |
| Date range/timeline | 1-21 November 2020, according to Shodan |
| Geographical scope | Worldwide |
| Types of data exposed | Order details; PII data; masked CC details; password reset requests; Shopify store admin APIs |
| Potential impact | Fraud; ID theft; phishing; e-commerce account takeover |
| Data storage format | Elasticsearch |
Topdser App Profile
For the reasons outlined below, we believe Topdser, a popular Shopify dropshipping app, was responsible for the data leak. Topdser is used by people running dropshipping stores on Shopify to automate purchase orders and payments made on their stores.
What is Dropshipping?
Dropshipping is an e-commerce model in which the store you purchase products from doesn’t actually stock anything. Instead, it sources its products from 3rd party suppliers, usually in China. When you purchase from a dropshipping website, the store forwards the order to the supplier, who delivers the product(s) directly to you.
Shopify is the most popular platform with dropshippers, with an easy setup and 1,000s of integrations to help run a successful store.
Per our research, the leak originated from Topdser, an independent 3rd party app that facilitates orders for dropshippers operating Shopify stores. The app takes orders from the Shopify storefront and automatically places an order with stores on cheaper platforms for the same product.
Timeline of Discovery and Owner Reaction
- Date discovered: 21st Nov 2020
- Date Shopify contacted: 21st Nov 2020
- Date Topdser contacted: 22nd Nov 2020
- Date of Response: -
- Date of Action: 24th Nov 2020
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. We often need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So we need to be thorough and make sure everything we find is correct and accurate.
In this case, we couldn’t conclude with 100% certainty that Topdser was responsible for the data leak, although there’s considerable evidence to suggest it was.
Links embedded in the data were directed to Topdser’s website. It would be impossible for another company to obtain access or permissions needed to create these. The company’s name was also found throughout the leaking database.
We notified Shopify immediately after examining the data leak, as the exposed data originated from stores running on its platform, although the company is not liable for the leak. We also contacted Topdser in case it was responsible for the leak so it could close the vulnerability and secure the data.
While Shopify acknowledged our disclosure, Topdser failed to respond.
One day after contacting the company, however, the database was taken offline.
Example of Entries in the Database
The data leak was absolutely massive, with over 17.5 million records exposed.
Furthermore, the exposed records only detailed transactions, purchases, and other activities logged by the app on a single day in November 2020.
There is proof that the database originally contained considerably more data dating back to at least the beginning of November 2020, but these entries were deleted before we analyzed the database.
Shodan search engine shows earlier records in the database with significantly more data dating back to November 1st 2020
The 17.5 million records that were accessible when we found the server compromised the security of up to 100,000 people shopping on stores that use the app, along with the owners of 17,000 stores.
Invoices for Store Purchases
Many of the database’s records included invoices for purchases made from Shopify stores processed by the app.
Each order contained various pieces of Personally Identifiable Information (PII) data for the person making the purchase, along with detailed information about the purchase itself. This information included:
Buyer Details
- Full name
- Phone number
- Email address
- Home Address (incl. country, state, and zip code)
Purchase Details
- Order IDs
- List of items
- Individual prices
- Item links
- Tracking numbers
Transaction Details
- Cost of purchases
- Delivery costs
- Payment methods
- Payment timestamps
- Masked credit card data (including last 4 digits and BIN number)
Invoices could be viewed as raw data or accessed via the exposed URLs of the files (with the authentication tokens required to do so also exposed).
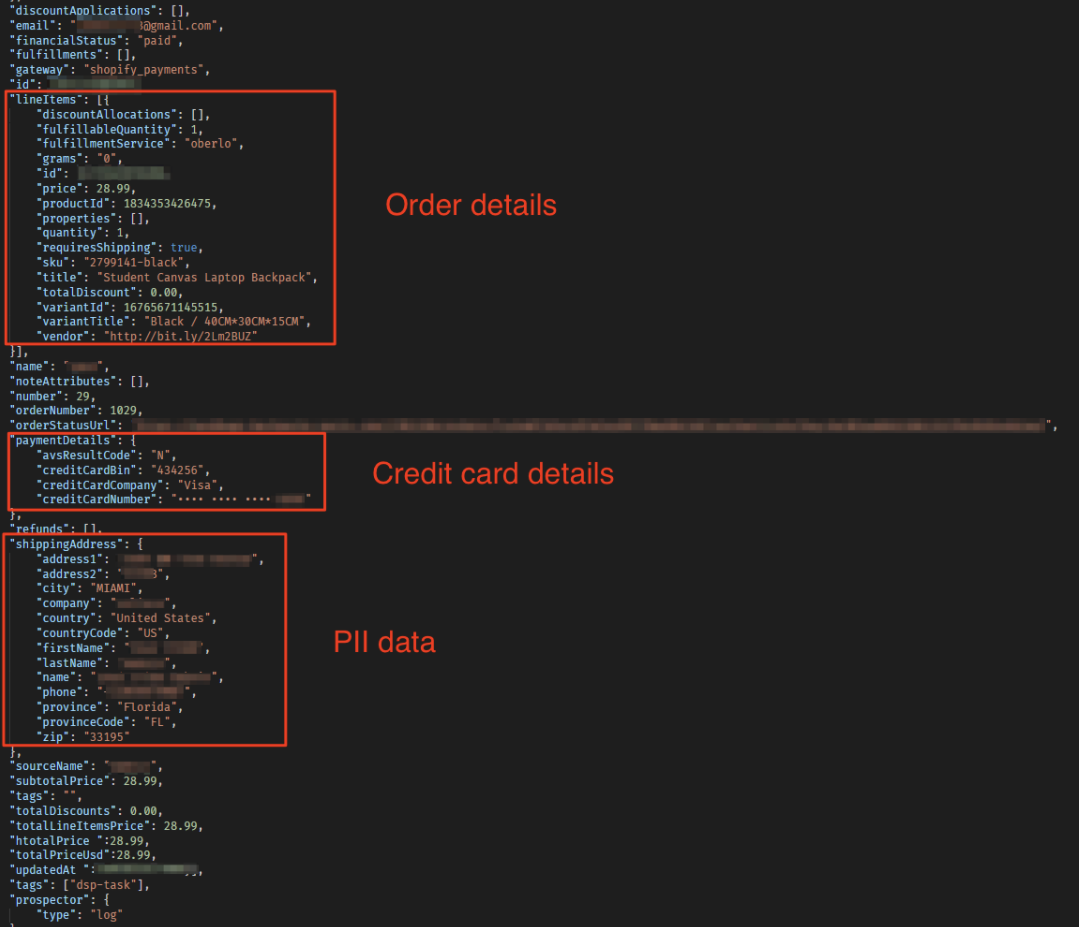 Raw data showing various forms of data from 1 purchase order
Raw data showing various forms of data from 1 purchase order
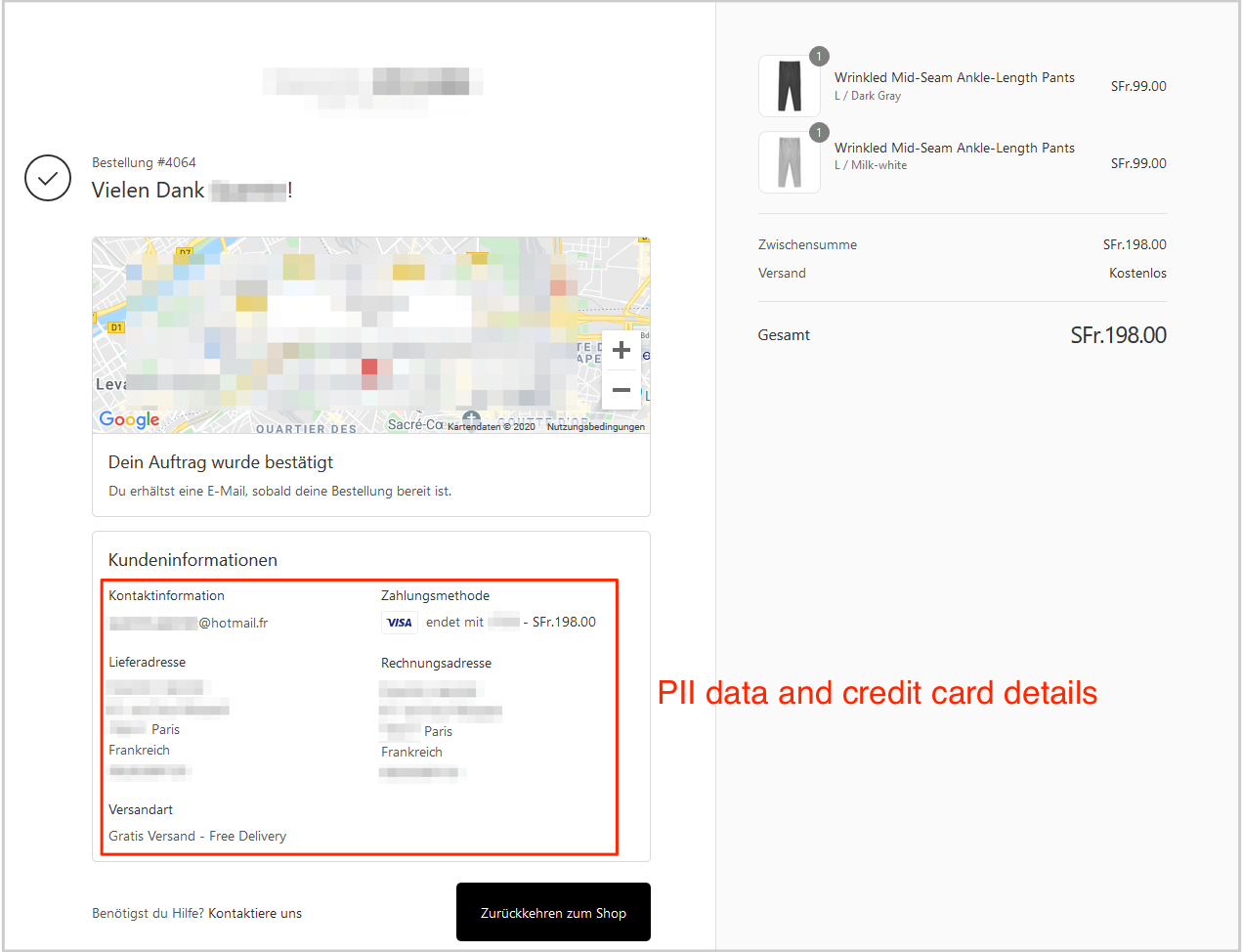 A private invoice downloadable via the breach in Topsder's app
A private invoice downloadable via the breach in Topsder's app
Password Reset Emails for Topsder Merchant Accounts
The exposed database also contained logs for password reset requests made to access private accounts on Topdser belonging to store owners. Each log entry contained a link to the account requesting the reset, a link to the password reset page for the relevant account, and the user’s email address.
By clicking the “reset password” link, hackers could change the password to someone’s Topdser account without using their email inbox. They could then change the password, take the email address from the database, log into the account, and take it over.
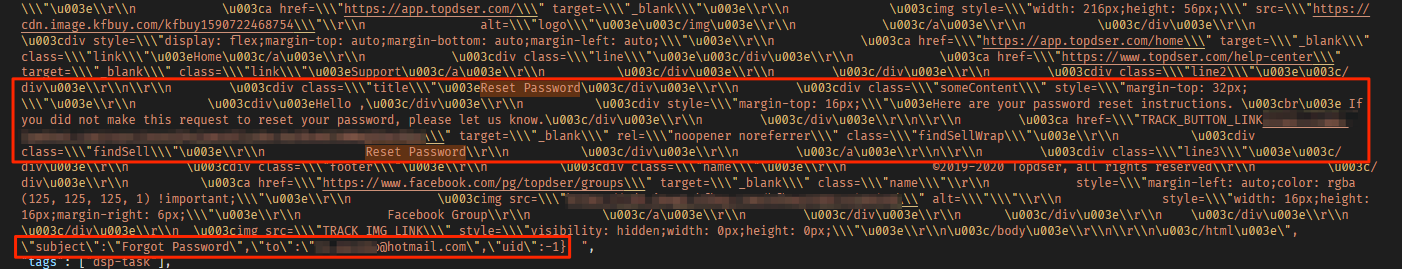 Technical entries in the database, including password reset links
Technical entries in the database, including password reset links
Shopify Store Admin Credentials
Authentication tokens containing access credentials to the APIs for Shopify stores using the app were also exposed.
These authentication tokens could potentially allow hackers to extract all the data from orders made on the store, along with the store owner’s private data (email address, phone number, business or home addresses, etc.).
The level of permission and the scope of access to the data granted depend on each token’s settings, much like the permission level of a logged-in user. Some would be read-only, but others could provide “write and modify” permission. This level of access could potentially grant changing the data on the orders, re-routing them, issuing refunds, and much more.
 Data entries exposing admin account credentials
Data entries exposing admin account credentials
Data Breach Impact
Phishing
In phishing campaigns, cybercriminals use stolen data to create emails imitating legitimate businesses. The emails are then sent to customers of that business (with details only the business should know) to trick victims into sharing even more private data - such as credit card details - or clicking links embedded with malicious software, like viruses.
If criminal hackers had discovered this database, they could have engaged in numerous phishing campaigns against Shopfiy customers.
The exposed data was also incredibly detailed, making it easy for cybercriminals to establish trust and credibility by posing as store owners.
For example, many purchase records displayed the BIN number and the final four digits of the credit cards used.
Fraudsters could combine this information with delivery orders to email victims querying purchases or claiming that there was a payment error. A simple message, like “There was an error with the credit card number ending in 1234. Please re-enter your card details to complete the order,” could trick many people into revealing their credit card details.
This is just one of the many ways cybercriminals could leverage the exposed data for phishing campaigns.
Given the data leak size, they would only need to successfully trick and defraud a small portion of the people exposed for it to be a highly lucrative operation.
Financial Fraud and Identity Theft
Aside from targeting the Shopify stores’ customers, cybercriminals could use any information extracted from the database and the successful phishing campaigns in a wide range of unrelated illegal activities.
With so much personal and financial data exposed, cybercriminals could pursue credit card fraud, bank fraud, mail fraud, tax fraud, and so much more.
In fact, they could easily pursue wholesale identity theft with devastating consequences for anyone successfully targeted.
Impact on Shopify Store Owners
The dropshipping stores exposed in the data leak are also vulnerable to a wide range of issues as a result.
The data leak revealed a massive amount of details about the stores affected as well as their owners.
Dropshipping is built on privacy and targeted marketing, and dropshippers are incredibly secretive about how they operate.
The leak undermined the privacy of over 17,000 dropshipping stores, revealing details about their revenues, best-selling products, target markets, geographical reach, and much more.
All of this information could be exploited by competitors to undermine their business by creating rival offers and replicating a store’s tactics.
The store owners themselves are also at risk. They could be targeted in phishing campaigns and fraud, just like their customers. Hackers could trick store owners into providing access to company credit and debit cards, bank accounts, and more.
The impact would be devastating for a business and its owners, potentially bankrupting them.
App Account Takeover
Visible password reset emails allow bad actors to send password reset requests and capture the reset link without having access to the email address inbox.
We believe these were for accounts on Topdser.
With access to a person’s account, hackers and cybercriminals could take over individual store accounts and potentially cancel deliveries, payments, change delivery addresses, etc., which could open a new opportunity for criminals.
Advice From the Experts
This data leak could have easily been avoided if the developers responsible had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
- Thoroughly vetting any 3rd party apps and integrations you adopt to ensure they meet the highest data security standards.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For Topdser Users
Should you be utilizing Topdser for your Shopify store and are anxious about how this breach could affect you or your clientele, it is recommended that you reach out to the company directly to find out the measures it is implementing to safeguard your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the exposed database as part of a vast web mapping project. Our researchers use large scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
The app was using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the database’s owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Shopify and Topdser to let them know about the vulnerability and suggest ways to secure their systems.
These ethics also mean we carry a responsibility to the public. Online shoppers must also be aware of a data breach that potentially exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
We’ve revealed that a hugely popular Christian faith app was harvesting millions of Americans’ private data without their knowledge and exposing it publicly. We’ve also uncovered huge scams targeting users of Facebook and Spotify.
You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and helps ethical hackers to anonymously report any data breach they find online. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.




Please, comment on how to improve this article. Your feedback matters!