Report: Popular Christian Faith App Exposes Millions of People to Fraud and Online Attack
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered that the Christian faith app, Pray.com, has been leaking years' of private data collected from users.
Pray.com offers daily prayer guidance and similar faith-based audio content and has proven incredibly popular since launching in 2016.
However, Pray.com’s developers failed to properly secure vast amounts of data collected from the app, potentially exposing millions of people to fraud and online attacks.
In fact, most people exposed in Pray.com’s data breach don’t even use the app.
Data Breach Summary
| Company | Pray Inc. |
|---|---|
| Headquarters | California, USA |
| Industry | Android, iOS, and web app; Media subscription service |
| Size of data in gigabytes | 262 |
| Suspected no. of files | 1.19 million |
| No. of people exposed | 1-10 million |
| Date range/timeline | 2016-present |
| Geographical scope | Worldwide |
| Types of data exposed | Photos, phone contacts, donation lists |
| Potential impact | Phishing, fraud, identity theft |
| Data storage format | Amazon S3 Buckets; Cloudfront CDN |
Company Profile
Pray.com is a Christian faith app launched by four founders in 2016.
Currently based in Santa Monica, California, Pray.com is available on iOS and Android. It claims to be the “#1 App for daily prayer and biblical audio content” and is “trusted by over 1 million Christians.”
We can confirm the app has been installed at least 1 million times on Android alone.
The app's audio content includes podcasts and religious recordings from Kristen Bell (Veronica Mars, The Good Place), James Earl Jones (the voice of Darth Vader and Mufasa in The Lion King), and well known religious leaders like televangelist Joel Osteen.
Timeline of Discovery and Owner Reaction
- Date discovered: 6th October 2020
- Dates vendor contacted: 7th October 2020; 9th October 2020; 12th November 2020; 17th November 2020
- Dates Amazon Contacted: 9th & 25th October 2020
- Date of Response: 17th November
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, our team discovered four misconfigured Amazon Web Services (AWS) S3 buckets and quickly identified Pray.com as their owner. AWS S3 buckets are a popular cloud storage solution for many apps and websites, but users must set their own security protocols.
Pray.com’s developers overlooked basic security protocols on the S3 buckets, leaving many of the files stored within them publicly accessible to anyone with access to the bucket’s URL (easily obtained).
Through further investigation, we learned that Pray.com had protected some files, setting them as private on the buckets to limit access.
However, at the same time, Pray.com had integrated its S3 buckets with another AWS service, the AWS CloudFront content delivery network (CDN). Cloudfront allows app developers to cache content on proxy servers hosted by AWS around the world - and closer to an app’s users - rather than load those files from the app's servers.
Doing so speeds up the app’s performance considerably.
Pray.com seemingly overlooked installing proper security measures on its CloudFront account. As a result, any files on the S3 buckets could be indirectly viewed and accessed through the CDN, regardless of their individual security settings.
Pray.com’s developers accidentally created a backdoor that gave complete access to all the files they had tried to protect.
Once we confirmed all the details of the breach, we reached out to Pray.com and presented our findings.
After our first two attempts at contacting Pray.com failed to elicit a reply, we contacted AWS directly to notify them.
AWS confirmed they had informed Pray.com of the breach a few days later, but there remains no evidence that the company has attempted to resolve the issue.
Five weeks after our initial attempt to contact Pray.com, the buckets remained unsecured, but the contacts files were removed.
On November 17th, after three attempts by us to reach out to Pray.com, we finally received an answer from Pray.com's CEO. His email contained one word: "Unsubscribe".
Note: Amazon isn’t responsible for the misconfigurations in this report. It provides detailed instructions on how to use AWS products and services. The owner of the data is the only liable party.
Example of Entries in the S3 Bucket
By not implementing robust security across its AWS infrastructure, Pray.com exposed a massive amount of data to the world.
This report's focus is on a single S3 bucket that contained various forms of private data collected from the Pray.com app. The remaining buckets consisted of technical data about the Pray.com app, which posed no risk to Pray.com users or the public - only the company itself.
Across both the unprotected and ‘protected’ files stored in this S3 bucket, Pray.com exposed millions of people's data. Most of these people didn’t use the app, and many weren’t even living in the USA.
Unprotected Files
Most of the primary S3 bucket's files - approximately 1.8 million - were completely unsecured, leaving them accessible to anyone with basic knowledge of the internet.
Pray.com Website and App Content
The S3 bucket contained various kinds of branded media from the Pray.com app and its promotional website, such as image files, podcast recordings, and other forms of audio.
Most of these, we believe, were exclusively available to people who signed up for the app’s paid membership plan.
Social Media Marketing Content
Alongside the multimedia content, Pray.com’s bucket also contained considerable amounts of branded content, such as images with motivational messages. We suspect these were used in social media marketing efforts.

User Profile Photos
Pray.com also left photos uploaded by the app’s users completely exposed. These were most likely profile photos and avatars for Pray.com’s private Communities social network - a feature on the app.
Some of the photos belonged to minors, most likely uploaded without their parents’ permission. By exposing these photos, Pray.com has made itself vulnerable to considerable backlash from families.


Church Attendee Lists
The most serious of the publicly accessible files were several CSV files from churches using the app to engage with members.
The CSV files contained long lists of individual churchgoers belonging to churches across the US. They contained considerable amounts of Personally Identifiable Information (PII) data for every individual listed, including:
- Full names
- Phone numbers
- Home addresses
- Marital statuses
- Email addresses
- Much more
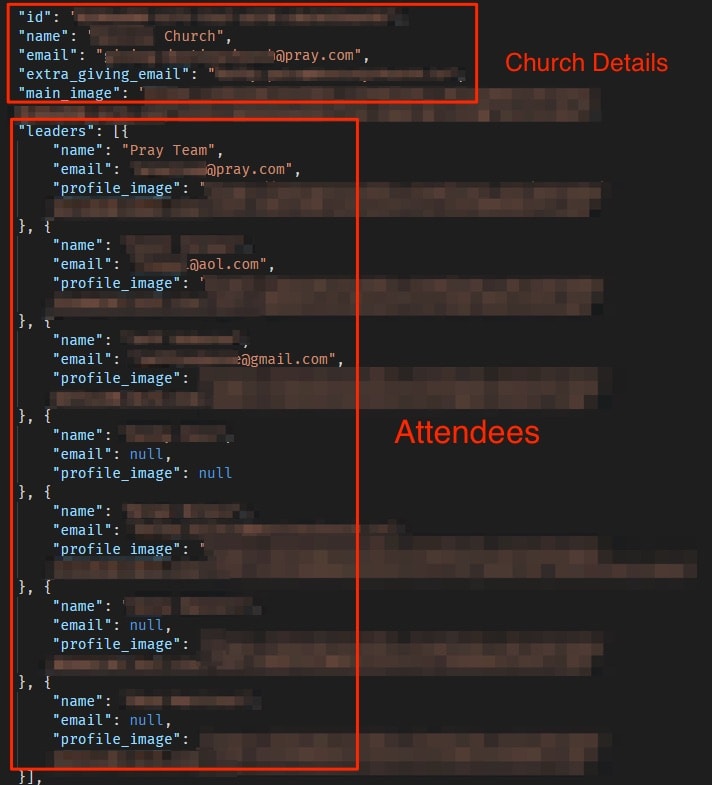 List of church attendees exposes their PII data
List of church attendees exposes their PII data
‘Protected’ Files
Pray.com did implement some basic privacy settings on the remaining files to protect the most sensitive data stored in the buckets.
A little over 80,000 files were made private, only accessible to people with the right security permissions.
However, Pray.com failed to replicate these security measures on its Cloudfront CDN, which remained publicly accessible.
As a result, because CloudFront had access to any file on the bucket but didn’t have the same security measures in place, any files supposedly ‘protected’ on the buckets were indirectly exposed by the CDN.
This glitch allowed indirect access to over 80,000 files containing various PII data for 10s of millions of people - and not just from Pray.com users.
Church Donation Records
Facilitating church donations appears to be one of the most popular features on the Pray.com app. Users can choose any church that has partnered with Pray.com and donate directly via the app.
Every time somebody donated to a church via Pray.com, the app logged this in the S3 bucket, along with the donation amount, the donor's PII data, and Pray.com’s fee for processing the donation.
All of this information was exposed.
The app also has no records of donations being forwarded to the respective churches. At least one angry Pray.com user raised this issue, claiming his church never received any donations sent via Pray.com.
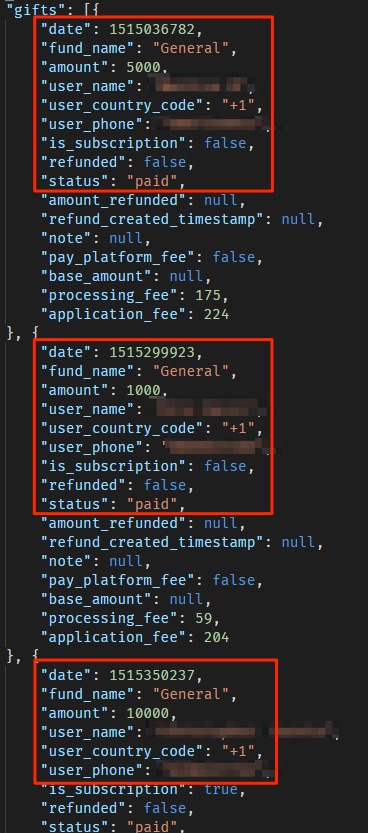 Lists of donations processed via Pray.com App
Lists of donations processed via Pray.com App
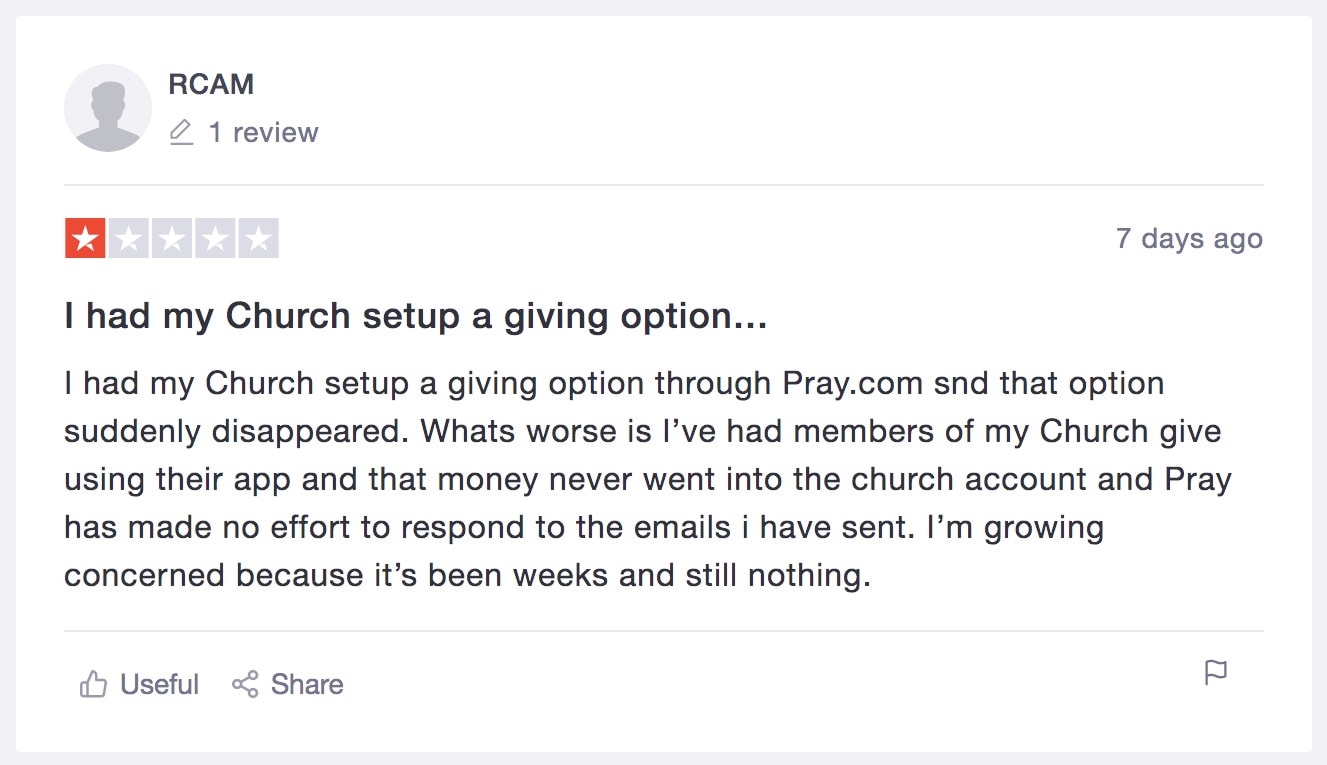 An angry Pray.com review claiming donations were never received
An angry Pray.com review claiming donations were never received
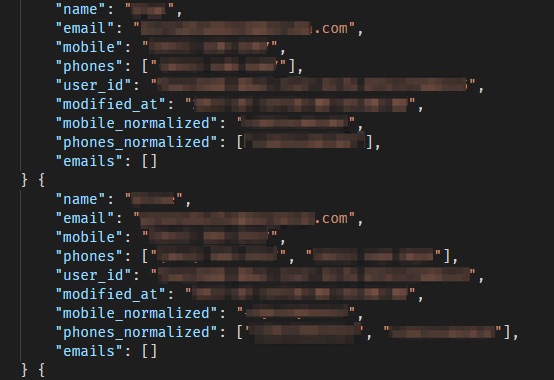
Phonebook Contact Lists
Pray.com has a built-in social network called Communities.
Every time someone installs Pray.com on their device and joins a Community, the app asks if they would like to invite their friends to join. If the user says yes, the app requests permission to access the user’s contacts.
If access was granted, Pray.com uploaded the user’s entire ‘phonebook’ from their device, containing every single contact saved within.
Many of these ‘phonebooks’ contained hundreds of individual contacts, each one revealing that person’s PII data, including:
- Names
- Phone numbers
- Email addresses
- Home and business addresses
- Sometimes, more details like company, family ties, etc.
We reiterate: the people whose data Pray.com had stored in these phonebook files were not app users. They were simply people whose contact details had been saved on a Pray.com user’s device.
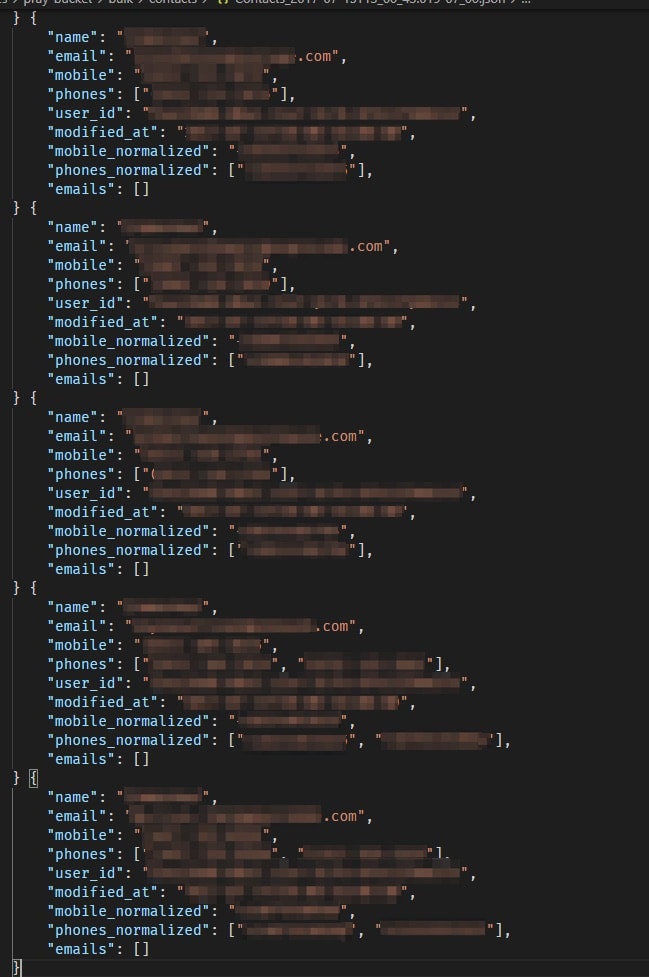 Contact lists uploaded from Pray.com users' phones
Contact lists uploaded from Pray.com users' phones
 More contact uploaded from Pray.com users' phones
More contact uploaded from Pray.com users' phones
In total, we believe Pray.com stored up to 10 million peoples’ private data without their direct permission - and without its users realizing they were allowing it to happen.
Furthermore, some of the files also contained login information for private accounts, such as usernames and passwords. Many people use their contacts list on their phone to ‘safely’ store such information.
Pray.com inadvertently accessed and exposed these also.
It appears that most of these phonebook files were manually uploaded by the app developers to the buckets over two days in 2019. We have no way of knowing where Pray.com had been storing nearly three years of private data before this.
This data harvesting represents a gross violation of Pray.com’s users' trust, along with the privacy of millions of people who’ve probably never even heard of the app. At no point in the app’s Privacy Policy or Terms of Service does it state that it will be collecting data on an app user’s contacts.
And by not securing all this sensitive data, Pray.com has exposed every individual affected in this breach - whether they use the app or not - to a wide range of dangers.
Data Breach Impact
By not protecting its users’ data - while also aggressively harvesting the data of their friends and family - Pray.com has exposed millions of people to various dangers.
The implications for the app's users, and the general public, should not be understated.
Illegal Phishing Campaigns
Cybercriminals could pursue highly effective phishing campaigns using their access to a Pray.com user’s PII data to send fraudulent emails to Pray.com users appearing as the app.
Furthermore, the long lists of donations processed by Pray.com would give cybercriminals invaluable insight into the finances of app users and an opportunity to contact them appearing as the app, querying a previous donation.
In doing so, they could successfully trick 10,000s of people into providing additional sensitive data - like credit card details - or clicking a link that embeds malicious viruses like malware on their devices.
The impact of a successful attack like this on a victim's personal and financial well-being could be devastating.
During our investigation into the contacts uploaded by Pray.com from users’ devices, we also found numerous “.gov” and “.mil” email domains. This suggests that Pray.com had harvested the PII data of US government and military personnel without their approval.
If cybercriminals gained access to these contacts, they would likely aggressively target the individuals exposed.
Government and military personnel are considered high-value targets by cybercriminals. With one successful phishing email sent to an army general, for instance, you could gain access and infect an entire military network.
Financial Fraud and Identity Theft
By combining the PII exposed by Pray.com with any additional information extracted through successful phishing campaigns, cybercriminals could pursue countless forms or fraud and cyber theft.
With enough data, they could even go so far as stealing a person’s whole identity, going unnoticed until it's too late, when a victim discovers their life is ruined.
Account Takeover
It appears that many Pray.com users had stored the login credentials for private accounts within their phonebook. Once Pray.com uploaded these to its bucket, they were inadvertently exposed to the public.
If a criminal hacker discovered this bucket, they could use the logins to hack into peoples’ private accounts on other websites and take them over.
Doing so would open up even more possibilities from fraud and criminal activities that would be impossible to trace back to Pray.com.
Potential Impact on Pray.com
Given the severity of this data breach and the implications for its users, Pray.com has also made itself vulnerable in many ways.
Fines and Legal Action
Based in California, with many users from the same state, Pray.com is within the California Consumer Privacy Act's jurisdiction.
As such, it's required to take serious steps to mitigate this data breach's impact and ensure no harm will come to any of its users as a result. It will also need to guarantee that more robust security protocols are put in place to reduce the risk of any future data leaks.
If it fails in any of these areas, Pray.com may face legal action, audits, and fines as a result.
Many of the contacts uploaded to the Pray.com’s S3 buckets were also residents of EU states. This makes Pray.com also liable to GDPR, which could pursue similar actions to those listed above.
Bad Publicity and Loss of Business
There’s a lot to take away from this data breach:
- The exposure of millions of people’s data, most of it harvested and stored by Pray.com without anyone’s knowledge.
- The leaking of minors’ photos, endangering them online.
- The exposure of US military and government personnel data.
- Exposing a lot of negative, untransparent traits in Pray.com’s business model.
The app already receives frequent negative reviews on all platforms, with many people calling out unethical business practices and terrible customer support.
A data breach like this could further tarnish its reputation, causing people to trust it less and question the company’s true motivations, and ultimately damage Pray.com’s revenue for the foreseeable future.
There are plenty of genuinely free and cheap Christian faith apps for the faithful to choose from as an alternative.
Advice from the Experts
Pray.com could have easily avoided exposing its customers’ data if it had taken some basic security measures to protect it. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Ensuring all systems that are open to the internet require authentication.
- Not collecting more data than needed, and not retaining unrequired data.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of Pray.com, the quickest way to fix this error would be to:
- Make the buckets private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 buckets to further restrict who can access it from every point of entry.
Even if you have individual permissions set on your S3 bucket, ensure no overriding measures are being put in place when integrating it with another service. For example, allowing CDN without similar security in place access - or any other actions that may bypass the S3 bucket’s security.
For Pray.com Users
If you’re a Pray.com user and you’re concerned about how this breach might impact you, contact the company directly to determine what steps it takes to protect your data.
When using an app on any device, carefully review the permissions it's requesting and find out for what purpose they’re needed. If an app asks for access that doesn’t make sense, you can refuse.
If an app asks for access to your contact list, consider that by granting it, you could be putting your family, friends, and colleagues at risk also.
To learn about data vulnerabilities in general, read our complete guide to online privacy. It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
In the midst of a substantial web mapping project, the research team at vpnMentor identified a breach in Pray.com's data. Our investigators utilize port scanning to delve into specific IP blocks and evaluate diverse systems for potential weaknesses or vulnerabilities. Every weakness detected is scrutinized for any indication of data exposure.
Our team was able to access Pray.com’s S3 buckets because they were completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the data, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Pray.com, not only to let them know about the vulnerability but also to suggest ways to make their system secure.
These ethics also mean we carry a responsibility to the public. Pray.com users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence - and no way of knowing - whether the data in our reports has been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach exposing the data of millions of Indian COVID-19 patients. We also revealed that a group of free VPNs compromised the privacy and security of millions of people worldwide. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Help Us Protect The Internet!
Introducing The Leak Box
The Leak Box is hosted on the Dark Web and allows ethical hackers to report any data breach they find online anonymously. Alternatively, anyone can submit a breach here on vpnMentor, any time, from anywhere, without compromising your privacy.
[Publication date: November 19, 2020]





Please, comment on how to improve this article. Your feedback matters!