Report: Popular Gambling App Exposed Millions of Users in Massive Data Leak
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a data breach on casino gambling app Clubillion.
The breach originated in a technical database built on an Elasticsearch engine and was recording the daily activities of millions of Clubillion players around the world.
Aside from leaking activity on the app, the breached database also exposed private user information.
With this information publicly available, Clubillion’s users were vulnerable to fraud and various online attacks with potentially devastating results.
Company Profile
Clubillion is a free online casino game available for iOS and Android, offering players 30+ free slot games. While each app is listed under a different developer - Ouroboros on iOS and T7 Games on Android - these are most likely owned by the same company.
Both versions of Clubillion were released in 2019 and became instant hits. Each is now ranked the #1 ‘social slots’ casino app on Google Play and the App Store, with a 4.8 star on both.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the database are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the database was built on Elasticsearch and hosted on Amazon Web Services (AWS), with Clubillion’s name on its apps, and links to assets owned by the company.
Once Clubillion was confirmed as the owner of the database, we reached out to the developers. While awaiting a reply, we also contacted AWS with details of the leak. It was closed a few days later.
- Date discovered: 19th March 2020
- Date vendors contacted: 23rd March 2020
- Date of contact with AWS: 31st March 2020
- Date of Action: Approx. 5th April 2020
Example of Entries in the Database
Clubillion’s exposed database contained technical logs for millions of Clubillion users around the world, on both iOS and Android devices. Every time an individual player took any action on the app, a record was logged. Examples of records include:
- "enter game"
- "win"
- "lose"
- "update account"
- "create account"
During our investigation of the database, new entries continued to appear continuously. We estimated an average of approximately 200 million records per day - and sometimes, considerably more.
In total, this amounted to over 50GB of exposed records in the database every single day.
Within many of these records, were various forms of user Personally Identifiable Information (PII) data, including:
- IP addresses
- Email addresses
- Winnings
- Private messages
The following code snippets demonstrate how the email addresses of users were exposed:

This data breach was truly global, with millions of records originating from Clubillion’s daily users all over the world. The following list is just a sample of countries affected, along with the average number of daily users from each country:
- USA - 10,000+
- UK - 2,475+
- France - 1,650+
- Israel - 408+
- Germany - 1,582+
- Spain - 1,026+
- Italy - 2,407+
- Netherlands - 622+
- Australia - 6,251+
- Canada - 7,792+
- Brazil - 3,859+
- Sweden - 191+
- Russia - 547+
Other countries affected included Uzbekistan, India, Poland, Romania, Vietnam, Lebanon, Indonesia, Philippines, Pakistan, Thailand, Austria, Hungry, and Latvia.
The following screenshot shows an entry from Paris, France:
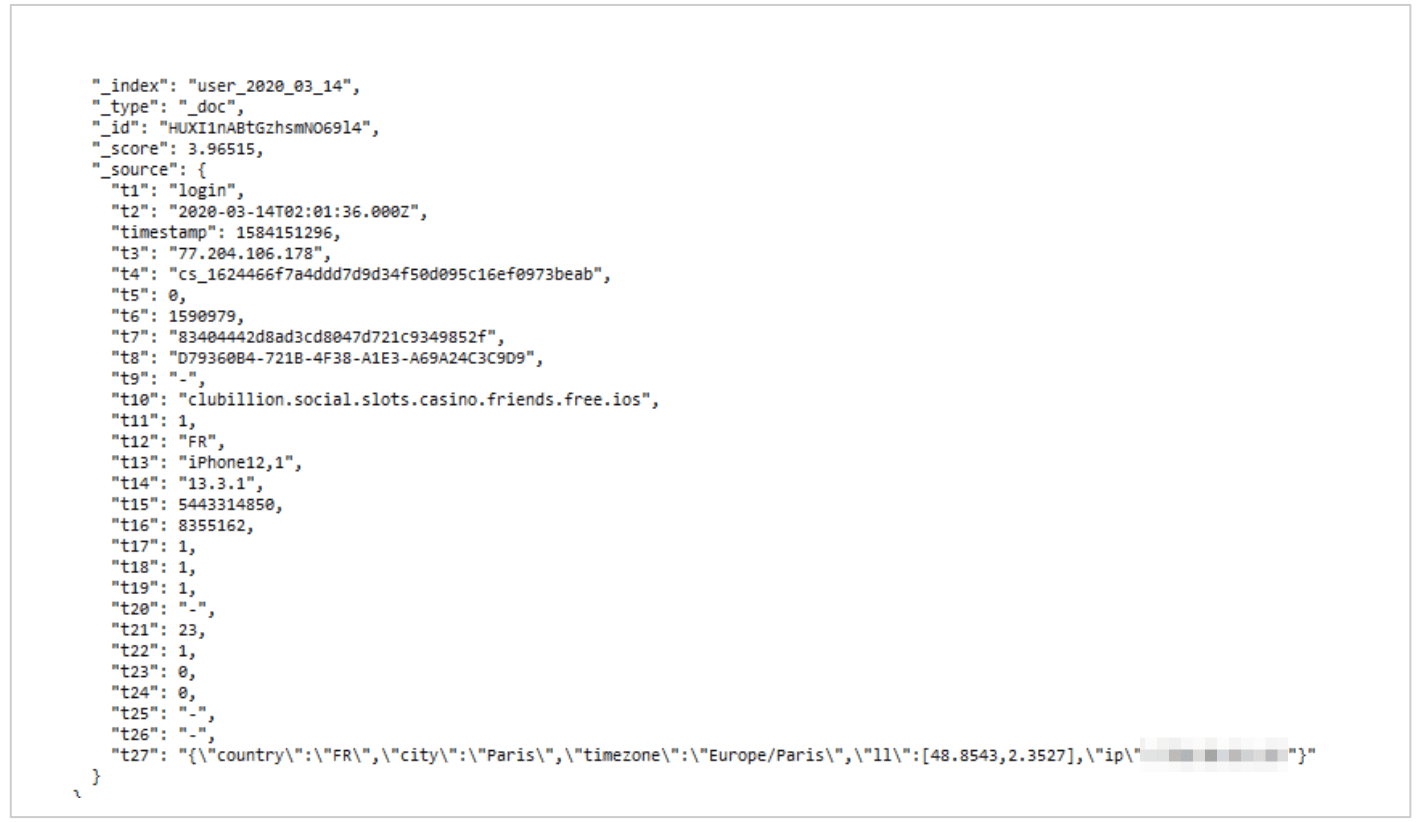
As you can see, on a single day, 10,000s of individual Clubillion players were exposed. Each one of these players could be targeted by malicious hackers for fraud and cyberattacks - along with millions more whose records were also contained in the database.
Data Breach Impact
Studies have shown that free gambling and gaming apps are especially prone to attacks and hacking from cybercriminals. They are routinely targeted for theft of private data and embedding malicious software on users’ devices.
Despite their popularity, gambling and casino apps often lack transparency, and it can be impossible to know what steps they’re taking to prevent cybercriminals successfully targeting their users.
One study of 23,000 free gambling apps found that: 3,200 posed a ‘moderate risk’ to users; 379 had known security vulnerabilities; 52 contained malicious software.
Any of these issues could be exploited to target app users in a wide range of frauds and cyberattacks, and Clubillion is no different.
With the exposed user PII and knowledge of their activity on the app, hackers could create elaborate schemes to defraud users. For example, some entries also included transaction errors for attempted card payments on Clubillion.
With the information in these transaction errors, hackers could target users with phishing campaigns, with the following aims:
- Trick them into providing their credit card details
- Trick them into providing additional PII to be used against them in further fraud
- Clicking a link that embeds malware, spyware, or ransomware onto their device.
If cybercriminals used Clubillion to embed malware or similar onto a user’s phone, they could potentially hack other apps, access files stored on the device, make calls, and send texts from the hacked device. They could even access a user’s phone contacts and steal the PII data of their friends and family.
Worse still, as people across the globe now find themselves under quarantine or self-isolation, as a result of the Coronavirus pandemic, the impact of a leak like this is potentially even more significant.
Clubillion stands to gain many new users, along with regular users playing more frequently. Hackers will be aware of this and looking for opportunities to exploit any vulnerabilities in the data security of such a massively popular app.
Had criminal hackers discovered Clubillion’s database, they could have targeted millions of people around the world, with devastating results.
Impact on Clubillion and it’s Developers
The most immediate risk for Clubillion is the loss of players. Data security is a growing concern for everyone these days, and this leak could turn many players off the app. Clubillion is not unique, and players have plenty of other choices for free gambling apps.
With fewer players, Clubillion will lose advertising revenue and reduced profits.
As many of Clubillion’s players reside within the EU, the app is under the jurisdiction of GDPR. The rules of GDPR also apply to apps, and Clubillion will need to take specific actions to ensure the regulatory body in charge doesn’t reprimand it.
Finally, Clubillion could also potentially be removed from Google Play and the App Store. Both Apple and Google are clamping down on apps that pose a risk to their users, removing apps embedded with malware, and taking data leaks much more seriously.
Each of these outcomes has a different likelihood of happening, but they would all negatively impact Clubillion’s revenue and business.
Advice from the Experts
Clubillion’s developers could have easily avoided this leak if they had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing their servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For Clubillion Users
If you play on Clubillion and are concerned about how this breach might impact you, contact the app’s developers directly to find out what steps it's taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
During a significant web mapping project, the research team at vpnMentor identified a breach within Clubillion's database. Our investigative experts utilize port scanning to scrutinize specific IP blocks and assess various systems for potential weaknesses or vulnerabilities. Each detected weak point is then thoroughly inspected for any signs of data leakage.
Our team was able to access this database because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the owner of the database, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Clubillion’s developers, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. Clubillion users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
Introducing The Leak Box
To ensure our mission has the most significant impact possible, we’ve also built The Leak Box.
Hosted on the dark web, the Leak Box allows ethical hackers to anonymously report any data breach they find online. We then verify and report any submission deemed a legitimate threat to the public’s safety.
We never sell, store, or expose any information we encounter during our security research. This includes any information reported to us via The Leak Box.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak exposing the data of 100,000s of people across North America. We also revealed that a company owned by European hotel giant AccorHotels compromised the privacy and security of hotel guests around the world. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 07.07.2019]



Please, comment on how to improve this article. Your feedback matters!