Report: African Mobile Internet Users Exposed in Huge Data Leak
Led by cybersecurity analysts Noam Rotem and Ran Locar, vpnMentor's research team discovered a data breach in a database belonging to South Africa ICT company, Conor. The breached database contained daily logs of user activity by customers of ISPs using web filtering software built by Conor. It exposed all internet traffic and activity of these users, along with their PII data. This included highly sensitive and private activity, including pornography, Not only did Conor expose users to embarrassment by revealing such browsing activity, but they also compromised the privacy and security of people in many countries.
Conor Company Profile
Based in South Africa, Conor is an information and communications technology (ICT) company that develops software products for clients in Africa and South America. They create a range of solutions for businesses in numerous industries, including finance, mobile internet, SMEs, and data monetization. Conor boasts 80 million mobile subscribers to their products, with some high profile clients, including Vodafone and Telkom.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what's at stake or who's leaking the data. Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness. Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true. In this case, our team’s web scanner picked up the database on the 12th of November. It was clear the database contained a huge amount of data from many different sources, in various countries. However, the function of the database wasn't initially clear, nor its relationship to the different ISPs and Conor. The database was later reviewed and better understood, along with its connection to a web filter app built by Conor. We then reached out to the company to offer our assistance.
Example of Entries in the Database
Conor states in their privacy policy, regarding data security: We value your trust in providing us your Personal Information, thus we are striving to use commercially acceptable means of protecting it. But remember that no method of transmission over the internet, or method of electronic storage is 100% secure and reliable, and we cannot guarantee its absolute security. Based on our team's discovery of this database, Conor's commercially acceptable means weren't enough to keep this private user data hidden. Our team was able to access this database because it was completely unsecured and unencrypted. We viewed constantly updating user activity logs for the last 2 months from customers of numerous ISPs based in African and South American countries. In total, this resulted in 890+ GB of data and over 1 million records. The database belonged to a proprietary software developed by Conor, rather than the ISPs themselves. The software seemed to be a Web filter developed for ISP clients to restrict access to certain websites and types of online content. We found entries from users viewing porn for example, as well as their social media accounts. Aside from the websites visited, this allowed our team to view a range of private personal user data every time someone logged onto the system. This included:
- The index names: allowing easy identification of daily activity
- MSISDN: a code that identifies a mobile phone user within their provider's network, via their phone number
- IP address
- Duration of connection or visit to a website
- The volume of data (in bytes) transferred per session
- Full website URL
- If a website had been blocked by the filter or not
Some of these can be seen in the following example:
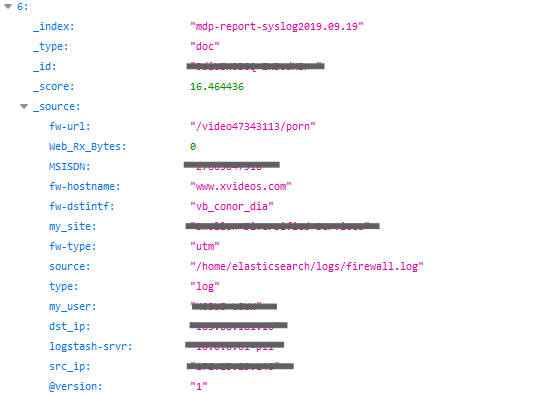
Because the database gave access to a complete record of each user's activity in a session, our team was able to view every website they visited - or attempted to visit. We could also identify each user. A person's internet browsing is always personal and expected to be private. However, that was not the case in this instance. In the following example, our team was able to view a user's activity on a porn website. This was a common occurrence in entries across the database, compromising the privacy of the affected users in the most intimate way.
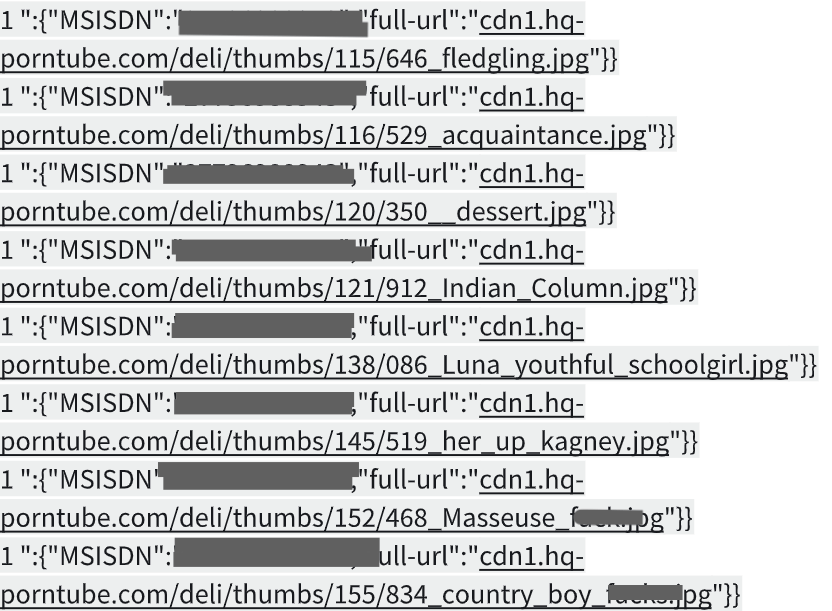
In another example, on the following record, a username is clearly visible. With a quick search on Facebook, we found this person’s personal profile, along with additional personal information revealed in their bio.
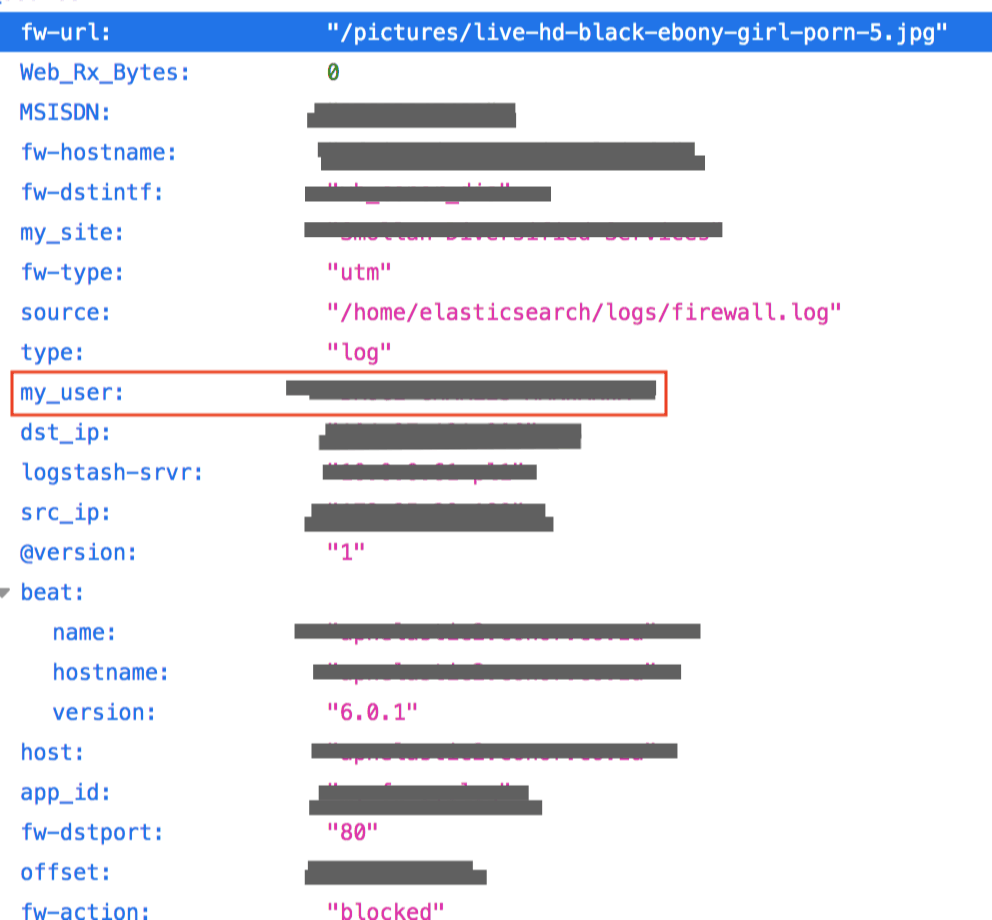
Our team viewed data entries from numerous mobile ISPs, such as Tshimedzwa Cellular and Flickswitch in South Africa, MTN in Kenya, and others. There were also entries from South American countries, such as the following example from Bolivia:

Also identifiable in the database were apps being used, for example:
- iCloud
- Google apps (Maps, Account, etc)
- Microsoft apps (Outlook)
These can be seen in the next two example code snippets: 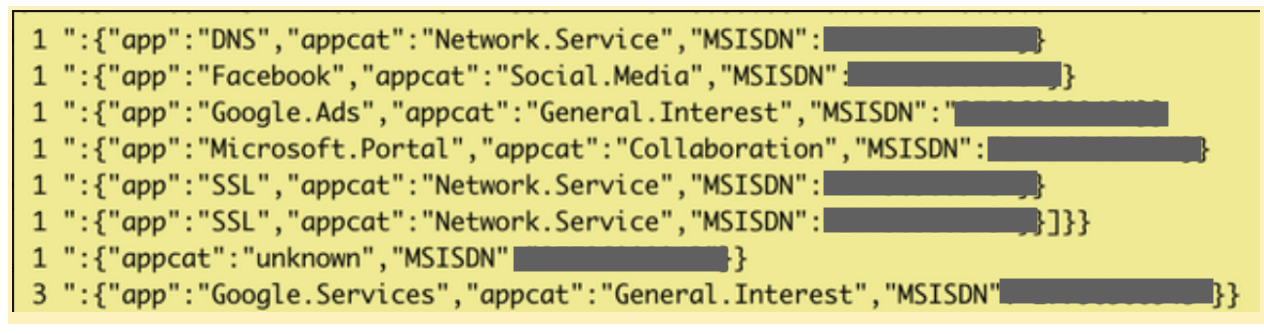

Data Breach Impact
A data breach of this size and nature - exposing so much data on user activity and identities - has serious implications for all involved.
Conor Solutions
It's remarkably negligent for an ICT and software development company to not safeguard this data. Conor's shortfall in data security could result in tangible issues for those exposed. Even though Conor wouldn't be directly susceptible to attack or fraud, they could experience considerable harm to their reputation and erosion of trust within their field. Other ICT businesses might be hesitant to engage Conor in the future, while existing clients could insist on corrective measures or compensation. The breached database also divulged the workings of Conor's web filter and its content blocking rules. Individuals could exploit this knowledge to circumvent the filter, rendering it useless and obsolete. Both consequences could lead to a decline in Conor's business and decreased revenue, stemming from a loss of clients who no longer have faith in their software or its benefits.
Conor's Clients
While Conor developed the web filtering software linked to this database, it's their ISP clients who would experience most of the negative reaction. Customers of ISPs compromised in this leak would most likely target the ISPs for criticism and compensation, leading to significant reputational and trust issues for the ISPs also. Likewise, they could be vulnerable to loss of business or legal action. It's also likely the ISPs have been advertising the web filter software as a value proposition to customers and charging them for it. If people could use the exposed database to bypass the web filter, ISPs would be at a further loss, their offer no longer an effective advertising tool.
Customers of the Affected ISPs
The greatest risk in this breach is to the people whose data was exposed. The database contained live traffic logs of all their online activities, along with PII of users. This means there is zero privacy for those affected. The leak made them vulnerable to a wide range of online attacks and fraud. These could have devastating effects, both personally and financially. As previously mentioned, not only was our team able to view a user's online activity but with the PII revealed in the database, we were able to find their social media accounts. This is known as doxing: using known data about a person to discover and expose their identity. Doxing is often done with malicious intent, with the exposed person subsequently targeted for bullying and harassment. With access to a person's porn history, hackers and cybercriminals could target them for bullying, or worse, blackmail and extortion. Many people would be deeply embarrassed by their porn search history, and cybercriminals know this. By threatening to expose a victim's online porn activity to their families or work colleagues, criminals could extort large sums of money from them. In the case of Venezuela, a country that Conor works in, porn is illegal. While we didn't see any records from Venezuela, if an ISP was to reveal illegal porn browsing by a customer, they would be even more vulnerable. A victim could face legal repercussions by the government, or more severe blackmail and extortion.
Advice from the Experts
Conor could have easily avoided this leak if they had taken some basic security measures to protect the database. These include, but are not limited to:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn't require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For Conor's Clients
We recommend reassessing or auditing your in-house data security and privacy protocols. You should also thoroughly vet any 3rd party applications you adopt or contractors you hire to ensure they're following up-to-date data security best practices. In the meantime, contact Conor directly to find out how they have resolved this data leak and what steps they're taking to ensure something like this doesn't happen again. For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For Customers of the Affected ISPs
If you're concerned that you've been exposed in this data leak, contact your ISP to find out whether they have contracted Conor to build software for them in the past. They should be able to provide you with any information related to this leak and whether you were potentially exposed. The most effective action you can take to ensure you're compromised in this leak, or any other, is to download a VPN. The breached database contained logs of all a user's internet activity. The only way to stop this from happening again is with a VPN. Connecting to the internet via a VPN encrypts your data and hides your activity, even from your ISP. It also hides your location and IP address, so hackers have almost no identifying information about you. This means that even if your ISP or any other party leaks their customers' data, you will still be hidden and safe from hackers and cybercriminals. If you're concerned about data security and vulnerabilities, read our complete guide to online privacy. It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in Conor's databases as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test open holes in systems for weaknesses. They examine each hole for data being leaked. When they find a data breach, they use expert techniques to verify the database's identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach. Our team was able to access this database because it was completely unsecured and unencrypted. Conor was using an Elasticsearch database, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing the database schemata. The purpose of this web mapping project is to help make the internet safer for all users. As ethical hackers, we're obliged to inform a company when we discover flaws in their online security. This is especially true when the companies data breach contains so much private and valuable user information. However, these ethics also mean we carry a responsibility to the public. Users of Conor's software must also be aware of a data breach that impacts them.
About Us and Previous Reports
vpnMentor is the world's largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users' data. In the past, we've discovered a huge data breach exposing the data of millions of Ecuadorean citizens. We also revealed that a breach in Biostar 2 compromised the biometric data of over 1 million people. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 16.12.2019]



Please, comment on how to improve this article. Your feedback matters!