Report: Indian e-Payments App Exposes Millions of Users in Massive Data Breach
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a massive amount of sensitive financial data leaking from a website connected to India’s mobile payment app BHIM that was exposed to the public.
The website was being used in a campaign to sign large numbers of users and business merchants to the app from communities across India. All related data from this campaign was being stored on a misconfigured Amazon Web Services S3 bucket and was publicly accessible.
The scale of the exposed data is extraordinary, affecting millions of people all over India and exposing them to potentially devastating fraud, theft, and attack from hackers and cybercriminals.
Data Breach Summary
| Company/Website | http://cscbhim.in/ |
|---|---|
| Located | India |
| Industry | Mobile banking; e-payments; personal finance |
| Size of data in gigabytes | 409 GB |
| Estimated no. of files | ~7.26 million |
| No. of people exposed | Millions |
| Geographical scope | Nationwide across India |
| Types of data exposed | PII data, |
| Potential impact | Identity theft, fraud, theft, viral attacks |
| Data storage format | AWS S3 bucket |
App and Company Profile
BHIM stands for Bharat Interface for Money, an Indian mobile payment app launched in 2016 by the non-profit business consortium, the National Payments Corporation of India (NPCI).
Part of a more extensive drive towards cashless transactions in India, BHIM was developed to facilitate instant e-payments and money transfers between bank accounts from a user's phone.
The app is based on the Unified Payments Interface (UPI) technology, also developed by the NPCI to facilitate better inter-bank transfers in India. UPI assigns individual users a unique ID number that is then used to send and receive money on any associated financial app.
Transactions can occur between private individuals, businesses, and other commercial parties.
By 2017, there were approximately 12.5 million BHIM users across India, set to grow over the next few years. By 2020, the NPCI recorded over 136 million downloads of the BHIM App.
Based on our research, the BHIM website in question was developed by a company called CSC e-Governance Services LTD. in partnership with the Indian government.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data exposed and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes time and careful attention. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, the data was stored on an unsecured Amazon Web Services (AWS) S3 bucket. S3 buckets are a popular form of cloud storage across the world but require developers to set up the security protocols on their accounts.
The exposed S3 bucket was labeled “csc-bhim”, and our team was quickly able to identify the developers behind the website “www.cscbhim.in” as the owners of the data.
Given the seriousness of the data breach, we contacted India’s Computer Emergency Response Team (CERT-In), which deals with cybersecurity in the country.
After some time, it appeared CERT-In hadn’t intervened, so we reached out to the website’s developers to notify them of the misconfiguration in their S3 bucket directly and to offer our assistance. however, we also received no reply from the developers.
Many weeks later, we contacted CERT-In a second time. Shortly thereafter, the breach was closed.
- Date discovered: 23rd April 2020
- Date CERT contacted: 28th April 2020
- Date of Response from CERT: 29th April 2020
- Date Company contacted: 5th May 2020
- Date of 2nd contact with CERT: 22nd May 2020
- Date of Action: approx. 22nd May 2020
Example of Data Entries
It appears CSC established the website connected to the misconfigured S3 Bucket to promote BHIM usage across India and sign up new merchant businesses, such as mechanics, farmers, service providers, and store owners onto the app.
It's difficult to say precisely, but the S3 bucket seemed to contain files from a short period: February 2019. However, even within such a short timeframe, over 7 million files had been uploaded and exposed.
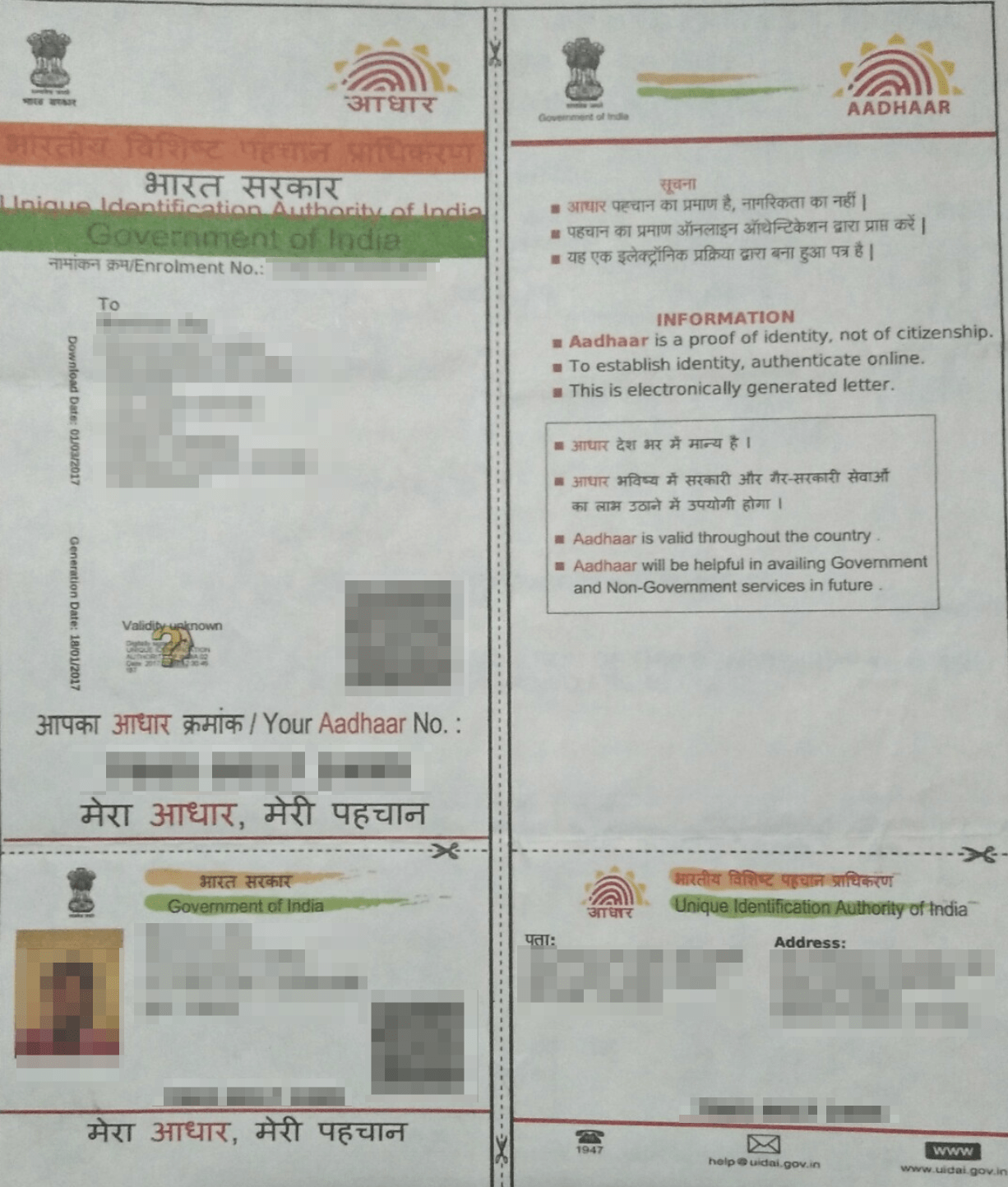
These files are highly sensitive, including many documents needed to open an account on BHIM, such as:
- Scans of Aadhaar cards - India’s national ID
- Scans of Caste certificates
- Photos used as proof of residence
- Professional certificates, degrees, and diplomas
- Screenshots taken within financial and banking apps as proof of fund transfers
- Permanent Account Number (PAN) cards (associated with Indian income tax services)
The private personal user data within these documents gave a complete profile of individuals, their finances, and banking records:
- Names
- Dates of birth
- Age
- Gender
- Home address
- Religion
- Caste status
- Biometric details
- Profile and ID photos, such as fingerprint scans
- ID numbers for government programs and social security services
Based on our research, the S3 bucket also contained documents and PII data for minors, with some records belonging to people under 18 years old.
The following are a small sample of the document scans stored in the misconfigured S3 bucket:


Additionally, the S3 bucket contained massive CSV lists of merchant businesses signed up to BHIM, along with the business owner’s UPI ID number.
Similar CSV lists of individual app users and their UPI IDs, with over 1 million such entries, were also exposed.
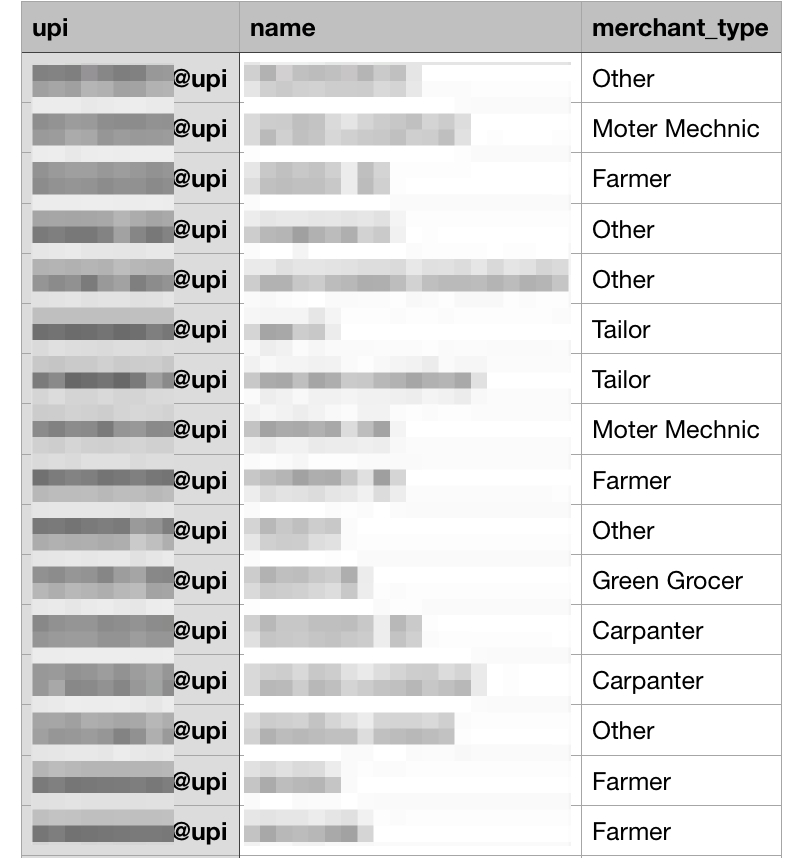
The UPI payment system is similar to a bank account in many ways. It would be incredibly valuable to hackers, giving them access to vast amounts of information about a person's finances and bank accounts. This data would make illegally accessing those accounts much easier.
The S3 bucket also contained an Android application package (APK), a file format used by Android’s operating system for the distribution and installation of apps. AWS Key pairs are the equivalent of admin user/password in Amazon’s infrastructure, potentially giving the holder of the key access to all data, the ability to start and stop servers, access the S3 bucket’s controls, and more. We did not test the credentials, but even their presence is an alarming sign of bad security design practices.
Data Breach Impact
The sheer volume of sensitive, private data exposed, along with UPI IDs, document scans, and more, makes this breach deeply concerning.
The exposure of BHIM user data is akin to a hacker gaining access to the entire data infrastructure of a bank, along with millions of its users’ account information.
Having such sensitive financial data in the public domain or the hands of criminal hackers would make it incredibly easy to trick, defraud, and steal from the people exposed.
Cybercriminals could combine the data in many ways, with the following illicit goals:
Identity theft - Using a person’s PII data and banking records to adopt their identity and use it to apply for loans, make illegal purchases, commit crimes, and more.
Tax fraud - Similar to identity theft, using someone's tax details to falsify records and make fraudulent claims.
Theft - Hackers could access BHIM accounts via the app and withdraw large sums of money.
Fraud - Tricking a user into sending you money via the app, by sending texts or emails imitating businesses and friends.
E-payment platforms and their users in developing countries are popular targets for fraud and theft. Users generally lack financial education and awareness of how scams like those listed above work. They can be easily tricked and swindled by professional fraudsters and criminal rings.
Our research also suggested that some of the exposed BHIM users were minors, who would be particularly vulnerable to fraudulent schemes.
Considering the volume of data exposed - over 7 million files - and the overall size of BHIM’s user base, hackers and cybercriminals would only need to successfully defraud and steal from a small percentage of users for a criminal scheme to be profitable and worthwhile.
The exposure of private data may also contribute to a broader deterioration of trust between the Indian public, government bodies, and technology companies. Data privacy is a huge concern for people from all sections of society, and many people could be reluctant to adopt a software tool linked to such a scandal.
As the Indian government is actively involved in the adoption of UPI apps like BHIM across the country, they risk harmful exposure by association and further discontent from the populace.
For CSC and the BHIM App
The most immediate risk to CSC and the developers of BHIM is the loss of users if people no longer trust the companies involved to protect their data.
It may also be more difficult to sign people up to the service in the future if stories and rumors spread that the app is unsafe to use, despite this data breach coming from an independent website. India experiences many issues with the spread of false or exaggerated stories across platforms like Whatsapp, as has been evidenced throughout the coronavirus epidemic
While India doesn’t maintain strong data privacy laws and protections, CSC and BHIM could still face regulatory issues and investigations as a result of the misconfigured S3 bucket. Given the government’s involvement, they will undoubtedly want to minimize any potential damage and negative press.
BHIM is just one of many e-payment platforms operating in India, including Google Pay. This data breach will help many of its competitors attract customers, damaging BHIMs market share.
Potentially, the most damaging aspect of this data breach is the exposure of the S3 bucket's APK. Skilled hackers could use this to attack CSC’s BHIM cloud storage infrastructure and target it with malware, spyware, and more.
Such attacks could have a devastating impact on the BHIM app and its broader user base that is difficult to predict in size and severity.
Advice from the Experts
The developers of the CSC/BHIM website could have easily avoided exposing user data if they had taken some basic security measures to protect the data. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online databases from hackers.
Securing an Open S3 Bucket
It's crucial to clarify that open, publicly accessible S3 buckets are not a shortcoming of AWS. They typically occur due to an oversight by the bucket's owner. Amazon offers in-depth guidelines to AWS users to assist them in securing their S3 buckets and maintaining their privacy.
In this case, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For BHIM Users
If you’re concerned about how this breach might impact you, contact CSC e-Governance Services directly to find out what steps it's taking to resolve the issue and keep your data safe.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the misconfiguration in CSC’s S3 bucket as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being exposed.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach or similar issue, we use expert techniques to verify the owner of the data, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in its online security. We reached out to CSC, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. BHIM users must be made aware that so much of their sensitive was data exposed.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included a huge data leak exposing 1,000s of American energy sector workers to fraud. We also revealed that two Indian financial services companies were leaking sensitive data belonging to their customers. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Editor's Note:
Following clarifications by BHIM we would like to emphasize the following points:
- The source of the leak was not the BHIM app itself, but rather a website operated by CSC and displaying the BHIM logo, which was aimed at recruiting users to BHIM.
- The said website is operated by CSC, an Indian govt entity, and while CSC explicitly mentions it is working in partnership with BHIM and NPCI, the website does not belong to BHIM.
[Publication date: 29.04.2020]




Please, comment on how to improve this article. Your feedback matters!