Report: Massive Fraud Network Uncovered, Targeting Groupon & Online Ticket Vendors
vpnMentor’s research team, led by Noam Rotem and Ran Locar, recently exposed a massive criminal operation that has been defrauding Groupon and other major online ticket vendors at least since 2016.
As part of a larger web mapping research project, we discovered a cache of 17 million emails on an unsecured database. Our initial research suggested the data breach was the result of a vulnerability in a ticket processing platform used by Groupon and other online ticket vendors.
Upon further investigation, however, we began to suspect a wider criminal enterprise might be at play. We’ve worked on many similar database breaches, and certain aspects of this one didn’t add up. After contacting Groupon with our concerns, the full extent of what we’d uncovered was revealed.
The database belonged to a sophisticated criminal network. Since 2016, They have been using a combination of email, credit card, and ticket fraud against Groupon, Ticketmaster, and many other vendors.
Groupon has been trying to shut this operation down ever since it started, but it has proven resilient.
Working together with Groupon’s security team, we may now have the key to closing the criminal operation down once and for all.
Discovery and Investigation Timeline
Our investigation of this database, in collaboration with Groupon, has been ongoing for several weeks now. This is to be expected for a discovery of this size and seriousness.
It happens sometimes that the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what's at stake or who's leaking the data.
In this case, we initially suspected a vulnerability in Neuroticket, a mailing system linked to the database. It took our team quite a while to find any data on the program, as there was no trace of it anywhere on the internet, except for an authentication page and inside the database.
Even after we decided to follow this lead, we realized that most of the data didn't make sense. We decided to investigate further, even though we had already disclosed our findings to the hosting company and Ticketmaster, thinking they were aware of the issue.
In the end, we had to scrap our initial research results and write a whole new report, to reflect the scope of what we had discovered.
Understanding a breach and what's at stake takes careful attention and time. Some affected companies deny the facts, disregarding our research, so we need to be thorough and make sure everything we find is correct and true.
We work hard on publishing accurate and trustworthy reports, to ensure everybody who reads them understands their seriousness. This is why we decided to rewrite this whole report, to better reflect our weeks of investigation.
What We Discovered
During a routine web mapping project, Noam, Ran & the team discovered a breach in a massive database. It contained 17 million records and 1.2 terabytes of data - a huge amount of information.
The breach seemed to give access to personal details of anyone purchasing tickets from a website using Neuroticket. Initially, we believed this vulnerability compromised customers on these websites.
The leak included many small, independent events spaces and venues across the USA. These included:
Two of the internet's biggest ticket vendors were also affected: Ticketmaster & Tickpick.
However, 90% of the database involved records from popular coupon and discounts website Groupon, totaling 16 million altogether. This can be explained by Groupon’s newsletters and promotional emails, sent out up to 5 times per day, per customer.
Below are 2 examples of entries in the database:
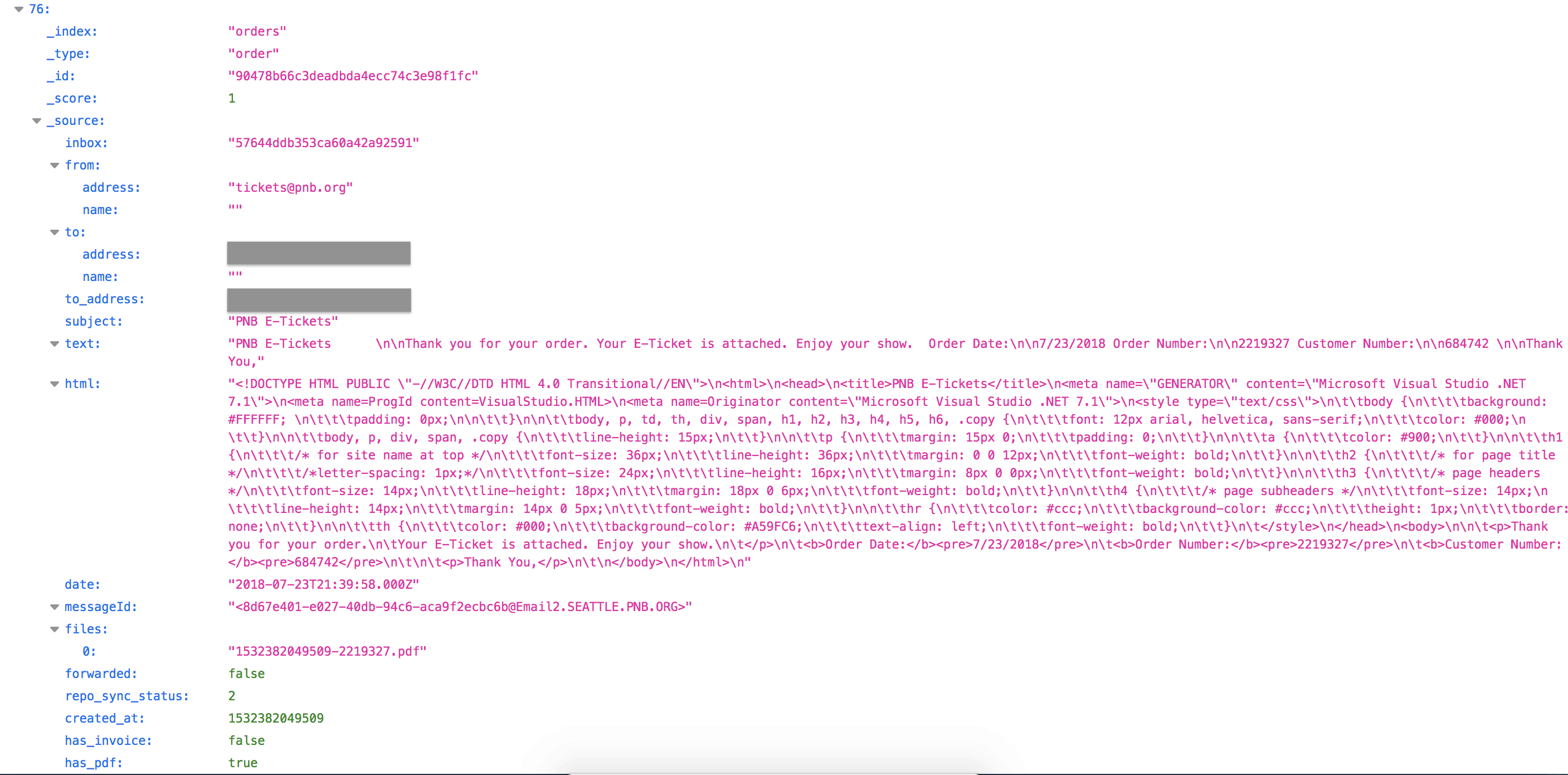
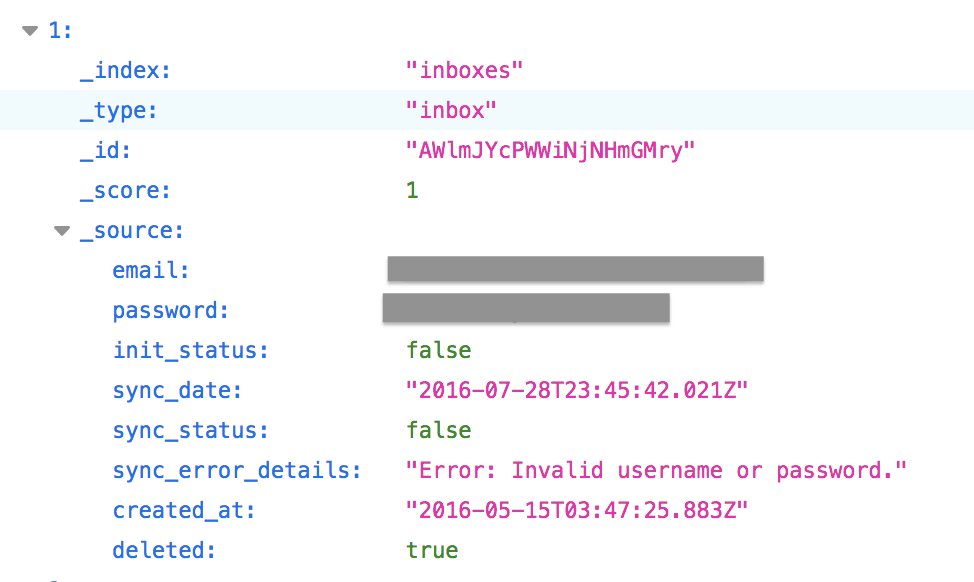
Suspicious Records
Finding any information on Neuroticket proved difficult. Considering it seemed a popular piece of software, it didn’t even have a website.
Meanwhile, we began to suspect many of the email addresses on the database were fake. To test this theory, we randomly selected 10 email address and contacted the apparent owners. Only one person replied to us.
Finally, we contacted Groupon, as they accounted for 90% of the emails on the database, presenting our findings and suspicions to their security team. It was then we learned the true nature of our discovery.
Uncovering The Network
After handing the results of our research over to Groupon, they were able to analyze the database themselves, cross-referencing it with information from their internal systems.
At this point, Groupon’s security team linked this database to a criminal network they had been chasing since 2016.
That year, a criminal operation opened 2 million fraudulent accounts on Groupon. With stolen credit cards, they used the accounts to buy tickets on the site, and then resell them to innocent people online.
Groupon had been able to close most of the accounts, but not all of them. The operation has remained resilient, despite excellent work by the company. Groupon’s Chief Information Security Officer (CISO) estimates the number of fraudulent accounts in the network we helped uncover to be as high as 20,000.
Working together with our research team, Groupon has been able to analyze the data and finally zero in on the entire criminal network.
From the beginning of this process, Groupon’s CISO has been incredibly co-operative, proactive, and professional. However, at some point they stopped replying, and we were left without answers.
How the Fraud Worked
The operation monitored their email inboxes linked to the fraudulent accounts, filtering relevant emails into the Elastisearch database for analysis. From there, they extracted tickets from the emails - in PDF form for Groupon, for example - and ignored any other irrelevant emails.
They would then, according to Groupon, resell these tickets to unsuspecting members of the public.
Also included in the breached database were support emails and chat logs from Groupon, regarding refunds issued to customers.
This was further evidence that the database was not in fact linked to the affected ticket vendors or Groupon. Instead, it suggested that the database was linked to email inboxes belonging to an independent party - in this case, the owner of the database.
An Ironic Twist
While conducting their research, our team found a peculiar ransom note embedded within the database.
Claiming to have extracted information from the database, it demanded a ransom of $400 in Bitcoin, in exchange for not releasing the stolen data to the public and subsequently deleting it.
It seems, at least one criminal hacker has already hacked the database. Not understanding what they discovered, they're trying to extort its owners.
This is a known issue with many open databases. It is usually triggered by automated scripts and not manually by humans.
Impact of the Fraud
Groupon has spent 3 years investigating and chasing this criminal network. In that time, they’re invested great time, money, and resources trying to shut it down.
The fraud being perpetrated using this database has no doubt cost the company significant revenue.
With the entire operation finally exposed, they can shut it down for good.
How and Why We Discovered this Data Breach
This data breach was identified as part of our continuous, extensive web mapping initiative. Ran and Noam perform scans of internet ports to detect familiar IP blocks, which they then utilize to uncover vulnerabilities in an organization's web infrastructure. Upon locating these weak points, the team searches for susceptibilities that could result in a data breach.
When they find leaked data, they use several expert techniques to verify the database’s identity.
As ethical hackers, we normally reach out to owners of the database or websites affected and outline the security flaws we discover. In this case, we decided to contact Groupon and the other ticket vendors.
We also carry a responsibility to the public. If possible, we will also alert any other parties affected by the breach, such as customers, clients, or a website’s users.
The purpose of the exercise is to help make the internet safer for everybody.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
We recently discovered a huge data breach impacting 80 million US households. We also revealed that a breach in Biostar 2 compromised the biometric data of over 1 million people. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Speaking of security and coupons, you may want to check out our "best VPN coupons" page. We can't unhack your site, but we can help you protect your PC.
[Publication date: 11.09.2019]




Please, comment on how to improve this article. Your feedback matters!