Report: Dating App Leaks Explicit User Messages & Other Private Data
vpnMentor’s research team recently discovered a data leak of dating app JCrush’s database.
Security researchers Noam Rotem and Ran Locar - key members of vpnMentor’s research team - discovered the breach, which exposed up to 200,000 users’ PII, preferences, and (sometimes explicit) private conversations within the JCrush app. JCrush is part of the Crush Mobile family of dating apps (1.5 millions users), which was acquired in 2018 by Northsight Capital, Inc. (OTCQB: NCAP).
Our team discovered 18.454 GB of unencrypted records on the Mongo database. As of publishing, the database is no longer accessible and the leak seems to have been stopped.
Editor's note: Neither vpnMentor nor the security research team wanted anyone to exploit this data, which is why we immediately contacted JCrush upon its discovery. We did not look deeply into any of the leaked data; our team simply found and confirmed its existence.
Timeline of Discovery and Reaction
| Data Breach Discovered | May 30, 2019 |
|---|---|
| vpnMentor Team Contacted JCrush | May 31, 2019 |
| Data Leak Fixed | May 31, 2019 |
| No reply from JCrush; Contacted Northsight Capital | June 2, 2019 |
| Northsight Capital Replied | June 4, 2019 |
Information Included in the Database
The severity of this leak is impactful, due to the nature of the data released. Included in the leak were all of the private correspondence between users, unencrypted. Many of these conversations were laden with explicit messages and also private details, along with personally identifying information.
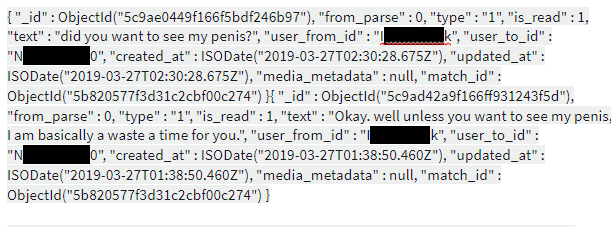
In addition to the private messages among JCrush users were additional data, including full profiles and photos, private media, Facebook profiles and tokens, and more.
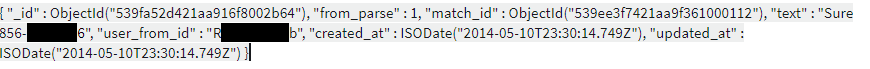
So, what does this mean in real-world terms? From the leak, we found sensitive user data and correspondence that includes:
- First and Last names of users
- Email addresses
- Facebook tokens, which can be used for log in
- Full user profiles
- Profile pictures
- Private - sometimes very intimate - messages and sensitive photos sent in those messages
- How many ‘swipes’ a user received per month
- When and where they last logged in from
JCrush - according to their Privacy Policy - records and stores the following data on their users, all of which were susceptible in this latest breach:
- FOUND Users’ mobile device unique ID numbers
- FOUND Users’ mobile device geographic locations while the app is actively running
- FOUND Users’ computer IP addresses
- FOUND Technical information about users’ computers or mobile devices (such as type of device, web browser or operating system)
- FOUND User preferences and settings (time zone, language, privacy preferences, product preferences, etc.)
- FOUND The URL of the last web page users visited before coming to the JCrush site
- FOUND The buttons, controls and ads users clicked on (if any)
- FOUND How long users used JCrush and which services and features users have used
- FOUND The online or offline status of JCrush
The Impact of the Data Leak
While going over the data, we stumbled upon the full user details and messages of multiple government employees, including those employed by the US National Institute of Health, US Veterans Affairs, the Brazilian Ministry of Labor and Employment, the UK’s cultural department, Israel's Justice Department, and more. This leak easily puts those individuals and any others similarly in a public role at risk for extortion by malicious hackers.

JCrush offers a special ‘incognito mode,’ where users can pay a premium to hide their profile to all users until they have ‘swiped right’ on them. This leak can potentially expose those who wish to remain anonymous in their dating endeavors - including individuals in the public spotlight or members who are married.
This data breach sheds light on the kind of information that could be at risk for various cyber threats, illustrating how it can impact the lives of hundreds of thousands of individuals who are vulnerable to the actions of digital criminals.
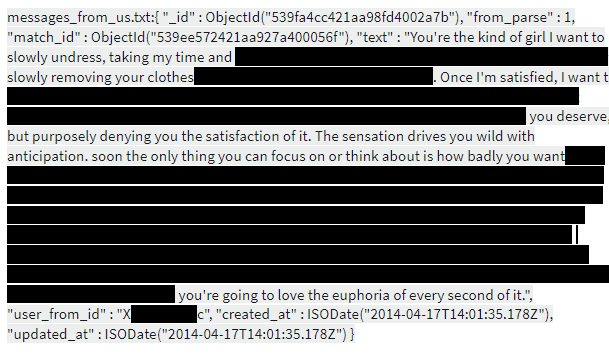
Other dating and hook-up apps, such as Tinder, admittedly record and store users’ private information and messages. This is a prime example of what can be made accessible to the public - with or without malintent.
How We Found the Data Breach
vpnMentor’s research team is currently undertaking a huge web mapping project. Using port scanning to examine known IP blocks reveals gaps in web systems, which are then examined for vulnerabilities, including potential data exposure and breaches.
Tapping into years of experience and know-how, the research team examines the database to confirm its identity.
After identification, we reach out to the database’s owner to report the leak. Whenever possible, we also alert those directly affected. This is our version of putting good karma out on the web – to build a safer and more protected internet.
Advice from the Experts
Could this data leak have been prevented? Absolutely! Companies can avoid such a situation by taking essential security measures immediately, including:
- First and foremost, secure your servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
For more in-depth information on how to protect your business, check out how to secure your website and online database from hackers.
Check Out More Data Leaks We’ve Discovered
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
We recently also discovered a hotel group’s cybersecurity data leak, as well as a data breach that exposed more than 80 million US households. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
Please share this report on Facebook or tweet it.



Please, comment on how to improve this article. Your feedback matters!