Report: Popular Digital Wallet Exposes Millions to Risk in Huge Data Leak
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a data leak by the popular app Key Ring, that compromised the privacy and security of their 14 million users.
Key Ring allows users to upload scans and photos of membership and loyalty cards onto a digital folder on one’s phone. However, many users also use it to store copies of IDs, driver licenses, credit cards, and more.
A misconfigured Amazon Web Services (AWS) S3 bucket owned by the company exposed these uploads and revealed their owners’ private data. During our team’s investigation, they also found four additional unsecured S3 buckets belonging to Key Ring, exposing even more sensitive data.
These unsecured S3 buckets were a goldmine for cybercriminals, making millions of people across North America vulnerable to various forms of attack and fraud.
Company Profile
Key Ring offers users a “One-Stop Shopping Solution.”
Leveraging various technologies to create a digital wallet on their phones, users store virtual copies and scans of gift cards, membership cards, etc. within the app.
Founded in 2009, Key Ring claims to have 14 million users storing 60 million cards in 2019.
The app also includes more features designed to make shopping and participation in loyalty/membership programs easier.
The company no longer operates within the EU, as it was unable to comply with GDPR.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake and who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find and report is correct.
In this case, Key Ring was storing the files on an AWS S3 bucket. S3 buckets are a popular storage solution on AWS and offer robust security features. However, it seems Key Ring’s developers had misconfigured at least five of its S3 buckets, making them publicly accessible to anyone with a web browser.
We can’t confirm how long the buckets were open, but the first was picked up by our web scanning tools in January. At the time, we were undertaking numerous investigations into other data leaks and had to complete these before we could analyze Key Ring’s S3 buckets.
Once the details of the leak were confirmed, we immediately contacted Key Ring and AWS to disclose the discovery and assist in fixing the leak. The buckets were secured shortly after.
- Date discovered: January 2020
- Date Key Ring and AWS contacted: 18th February 2020
- Date of Action: 20th February 2020
Example of Entries in the Unsecured S3 Bucket
Key Ring does not include a Privacy Policy or outline of its data protection policies on the app’s website. Thus, we can’t say with certainty what measures Key Ring takes to keep customer data private.
Regarding the exposed database, it seems Key Ring was storing user media uploads on an AWS S3 bucket. However, the bucket's security settings were not configured properly, exposing the database to the public.
The result? Anybody with a web browser could have viewed over 44 million images uploaded by Key Ring users.

Example 1: A Target gift card with a value of $1,000
While Key Ring was primarily designed for storing membership cards for loyalty programs, users are also storing more sensitive cards on the app.
The private personal user data we viewed included scans of:
- Government IDs
- Retail club membership and loyalty cards
- NRA membership cards
- Gift cards
- Credit cards with all details exposed, incl. CVV numbers
- Medical insurance cards
- Medical marijuana ID cards
- Many more

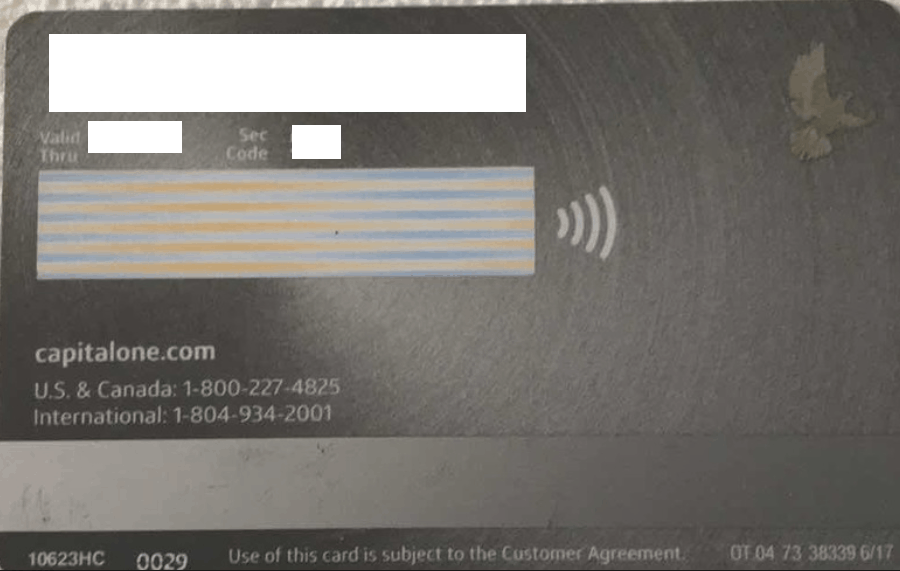
Example 2: Credit Card with all necessary information to make purchases online

Example 3: A professional ID card

Example 4: a National Rifle Assoc. Of America membership card
Key Ring also works as a marketing platform for many of North America’s most prominent retail brands.
As such, the bucket also contained CSV files detailing membership lists and reports for many of these businesses. These lists contained the Personally Identifiable Information (PII) data of millions of people.
Examples of companies affected, and the number of customer entries included:
- Walmart/Kleenex list: ~16,000,000
- Kids Eat Free Campaign: ~64,000
- Unknown marketing campaign report: ~86,000
- La Madeleine Bakery chain: ~6,600
- Footlocker: Unknown amount of records
- Mattel ~2,000
In the following example from La Madeleine Bakery, numerous PII data were exposed. This list is similar to many we viewed:
- Full names
- Email addresses
- Membership ID numbers
- Dates of birth
- Locations and Zip Codes
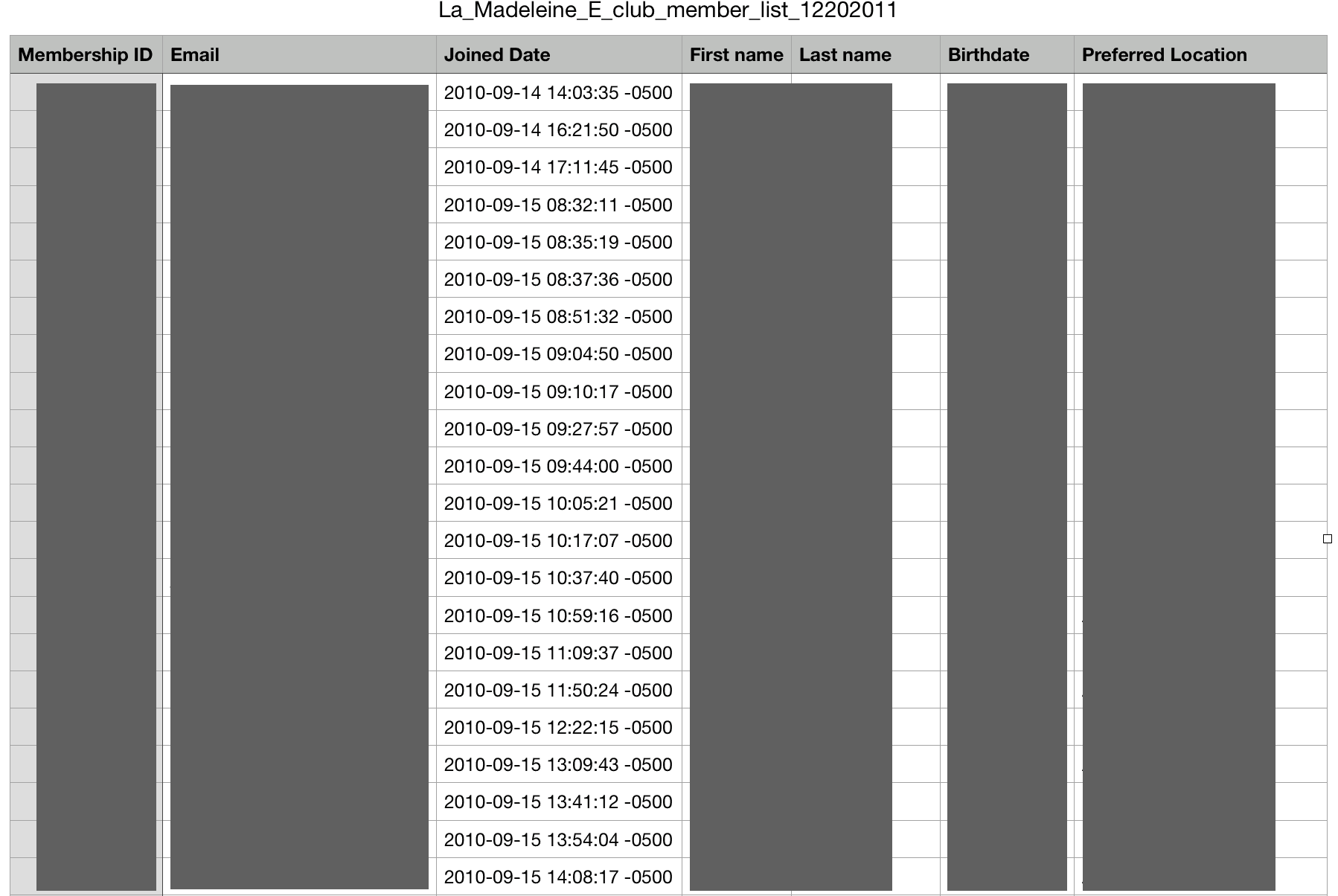
Example 5: Membership list for La Madeleine loyalty program
Additional S3 Buckets Discovered
While investigating Key Ring’s first S3 bucket, our team discovered four more buckets holding even more private data.
In these buckets, we found a snapshot of the company's database, which includes highly sensitive information about its users.
Although the snapshot is not new, it held millions of records that were never meant to be exposed:
- User emails
- Home addresses
- Device and IP address information
- Encrypted passwords and the “salt” randomized data used to encrypt them
- Much more
In total, five S3 buckets belonging to Key Ring were exposed, all containing valuable, private information that could have serious security implications for millions of people.
Data Breach Impact
Two aspects of this leak made it especially dangerous:
- The sheer volume of files exposed, impacting millions of people across North America
- The value of the exposed data to criminal hackers
Aside from the CSV files, over 44 million images of personal cards were uploaded to the database by Key Ring users. These uploads exposed their credit card details, social security numbers, and much more.
Had malicious hackers discovered these buckets, the impact on Key Ring users (and the company itself) would be enormous.
In fact, we can’t say for certain that nobody else found these S3 buckets and downloaded the content before we notified Key Ring.
If this happened, simply deleting the exposed data and securing the S3 buckets might not be enough. Hackers would still have access to all the data, stored locally, offline, and completely untraceable.
For Key Ring App Users
The implications of this leak for the people whose cards and PII had been exposed are far-reaching.
The exposed database contained completely unsecured scans of credit cards, government IDs, driver licenses, and various other forms of ID.

Example 6: Patient ID for a medical cannabis program
Combined, they offered criminal hackers an absolute goldmine.
Key Ring’s database could have facilitated massive fraud and identity theft schemes targeting millions of people in America and Canada.
The following are just a few ways criminals could use the various IDs and bank cards stored on Key Ring for illegal means.
Identity Theft: An umbrella term for any time somebody uses your IDs or PII data to steal your identity, pose as you, and commit various types of fraud in your name.
Tax Fraud: Using your Social Security number and PII, criminals file fraudulent tax returns and claim refunds in your name.
Credit Card Fraud and Online Shopping Fraud: Your credit card details used to make online purchases, charged to your account.
Account Takeover: Criminals gain access and take control of your financial, credit, and bank accounts.
New Account Takeover: Similar to above, but this time new financial and credit accounts are opened in your name.
Criminal Identity Theft: Somebody gives your details when arrested or fined by the police, with any incidents added to your criminal record.
Loan Stacking: Criminals take out multiple loans in your name, from automated lenders, with numerous payments made before you become aware.
These are just a small sample of the countless ways hackers and cybercriminals could target and defraud millions of people through Key Ring’s database.
Every file we viewed could also be downloaded and stored offline, making them completely untraceable. Criminals could then target people over and over again, for many years to come. Alternatively, they could sell the data on the dark web to criminals around the world.
At that point, there’s no way of knowing how people’s identity would be used, creating serious security and privacy issues for the US and Canadian governments.
Phishing Campaigns
The information exposed in this database could also have been exploited further to gain even more information about Key Ring’s users.
By combining the scanned cards and IDs with user PII data, criminals could create complex user profiles for highly effective phishing email campaigns.
Criminals create phishing emails to imitate real, trustworthy businesses and organizations. The emails are sent to potential victims for the following purposes:
- Trick someone into revealing additional sensitive details, like usernames and passwords to secure financial accounts.
- Plant malicious programs and software such as malware, spyware, or ransomware on their devices or internet servers.
Falling victim to a phishing campaign can create many security and privacy issues for a victim, especially if they’re targeted in their workplace. The ripples could be felt far beyond the initial target.
For this reason, they’re one of the most popular, oldest, and dangerous forms of online fraud.
For Key Ring's Developers
The implications of this data leak are not reserved just for Key Ring users.
The company itself could have been in danger if this database had criminal hackers discovered the database.
Aside from losing users and partners, Key Ring would have been vulnerable to legal action, fines, and intense scrutiny from government data privacy groups.
Key Ring is already no longer operating in the EU due to the inability to comply with GDPR. With California enacting its data privacy law in January 2020 - the CCPA - Key Ring could still have faced investigation and fines from the state’s legislative bodies.
Given the scale and seriousness of this leak, the impact on the company’s finances, reputation, and market share would be unmeasurable.

Advice from the Experts
Key Ring could have easily avoided this leak if it had taken some basic security measures to protect it’s customer data. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules to servers and databases.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In the case of Key Ring, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For Key Ring Users
If you’re a customer of Key Ring and concerned about how this breach might impact you, contact the company directly to learn what steps they’re taking to resolve it.
Should you have utilized Key Ring for storing any form of identification, bank cards, or similar items, keep a vigilant eye on any corresponding bank statements or mail. Be on the lookout for any dubious transactions or activities that indicate potential unauthorized access to your private accounts or illicit use of your information.
Be vigilant for emails that appear to be from banks, etc. asking you to click a link and input/confirm any personal details. These may be phishing campaigns.
To learn more about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in Key Ring’s database as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
When we find a data breach, we use expert techniques to verify the owner of the database, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Key Ring, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. Key Ring users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak exposing the data of 10,000s of American restaurant diners. We also revealed that a company owned by hotel giant Best Western compromised the security of US military staff around the world. To learn more, read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 18.02.2020]




Please, comment on how to improve this article. Your feedback matters!