Report: Exercise App Exposes Private User Data in Massive Data Leak
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a data breach belonging to the exercise technology company Kinomap.
As a paid subscription service, Kinomap collects enormous amounts of data about its users, all of which was stored on an unsecured database. In total, the database was leaking over 42 million records, affecting people all over the world.
This leak represents a significant lapse in basic security measures by Kinomap. Had criminal hackers discovered the database, the impact on both the company and its customers would have been immeasurable.
Company Profile
Kinomap creates immersive workout videos for people exercising on rowing and cycling machines, and treadmills.
The videos are real recordings of popular running, cycling, and rowing tracks around the world, uploaded by Kinomap users and professional trainers. Kinomap also offers coaching videos similar to a workout you would do with a personal trainer.
All the videos are interactive and combined with the Kinomap mobile app. Users can build structured, dynamic home workouts imitating real-life outdoor environments in countries around the world.
Kinomap was founded in France in 2002 and now has an international user base spread throughout 80+ countries.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, Kinomap’s name was found throughout the database. There were also many links directed to the site. Further investigation quickly confirmed the company as the owner of the database.
With that, we reached out to the company and presented the results of our investigation. While awaiting reply from Kinomap, we also contacted the Commission nationale de l'informatique et des libertés, France’s independent data privacy regulator.
While we never received a reply from Kinomap, the data breach was closed sometime around the 12th of April. We suspect this was due to an intervention by the CNIL.
- Date discovered: 16th March 2020
- Date vendors contacted: 18th March 2020
- Date of 2nd contact attempt (if relevant): 30th March 2020
- Date of contact with CNIL: 31st March 2020
- Date of Response: N/A
- Date of Action: Approx. 12th April 2020
Example of Entries in the Database
The exposed database contained over 40GB of data, approximately 42,000,000 records.
This is an enormous amount of data.
It also seemed to affect Kinomap’s entire user base, as the data originated from countries across the globe. Many of these countries consider the data security of their citizens a top priority, including the following:
- Belgium
- Finland
- Hungary
- Portugal
- France
- Germany
- The USA
- Canada
- Australia
- Japan
- South Korea
- The UK
Amongst the millions of data files exposed were numerous forms of Kinomap user Personally Identifiable Information (PII) data. This kind of information, when in the wrong hands, can be used to target people in a range of frauds and online attacks.
The user PII data exposed in Kinomap’s database included:
- Full names
- Home country
- Email addresses
- Usernames for Kinomap accounts
- Gender
- Timestamps for exercises
- The date they joined Kinomap
The following screenshots demonstrate how some of this PII was being leaked through user records:
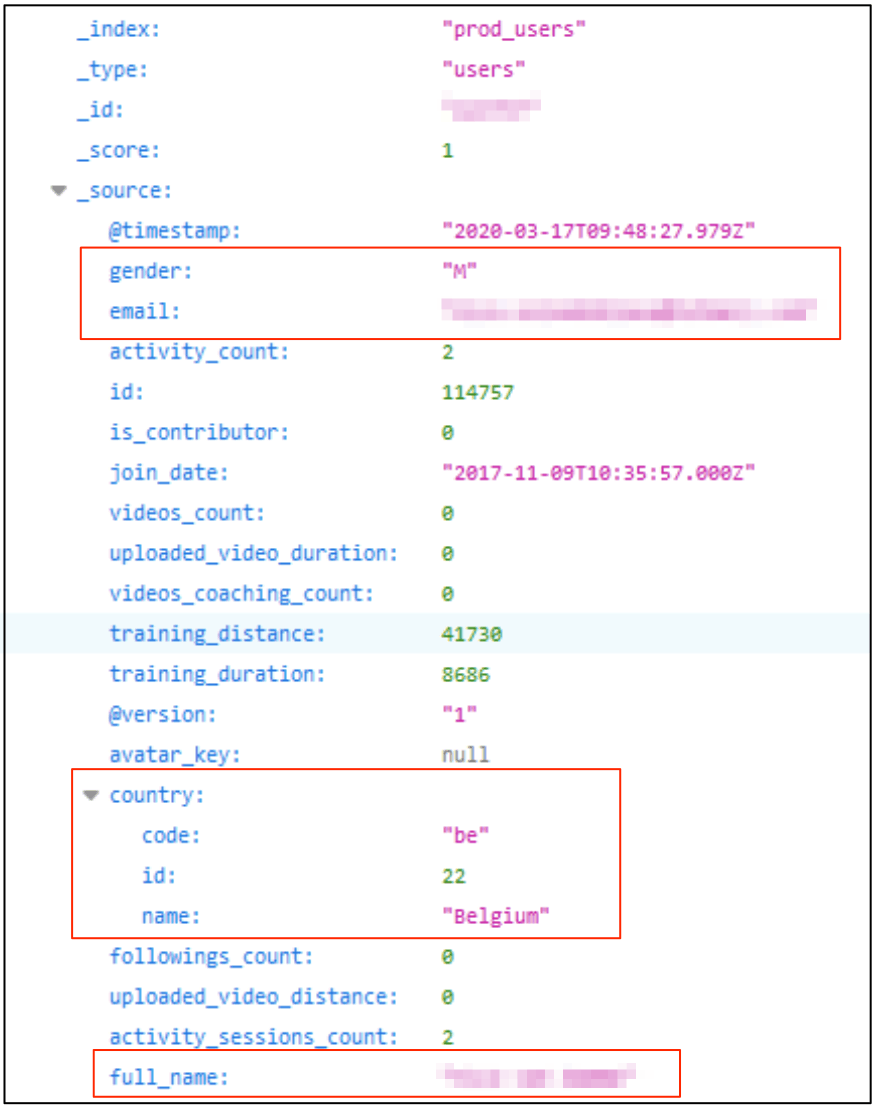
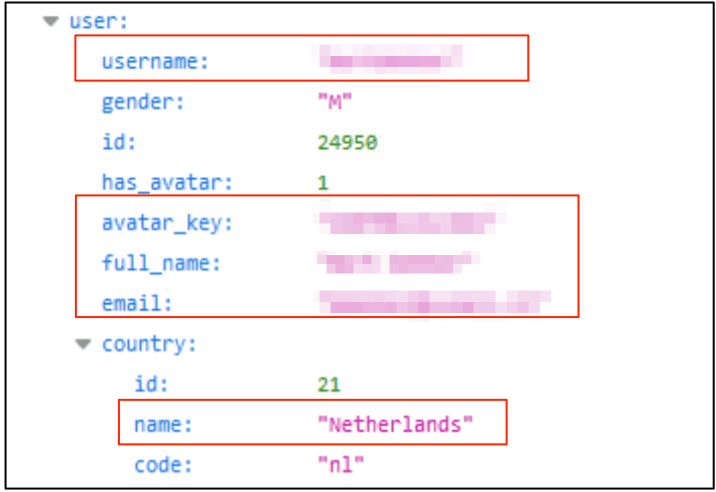
Aside from the PII data exposed, a great deal of personal data was also revealed indirectly.
Many of the entries contained links to Kinomap user profiles and records of their account activity. Similar to social media accounts, Kinomap profiles can reveal considerable personal details about a user.
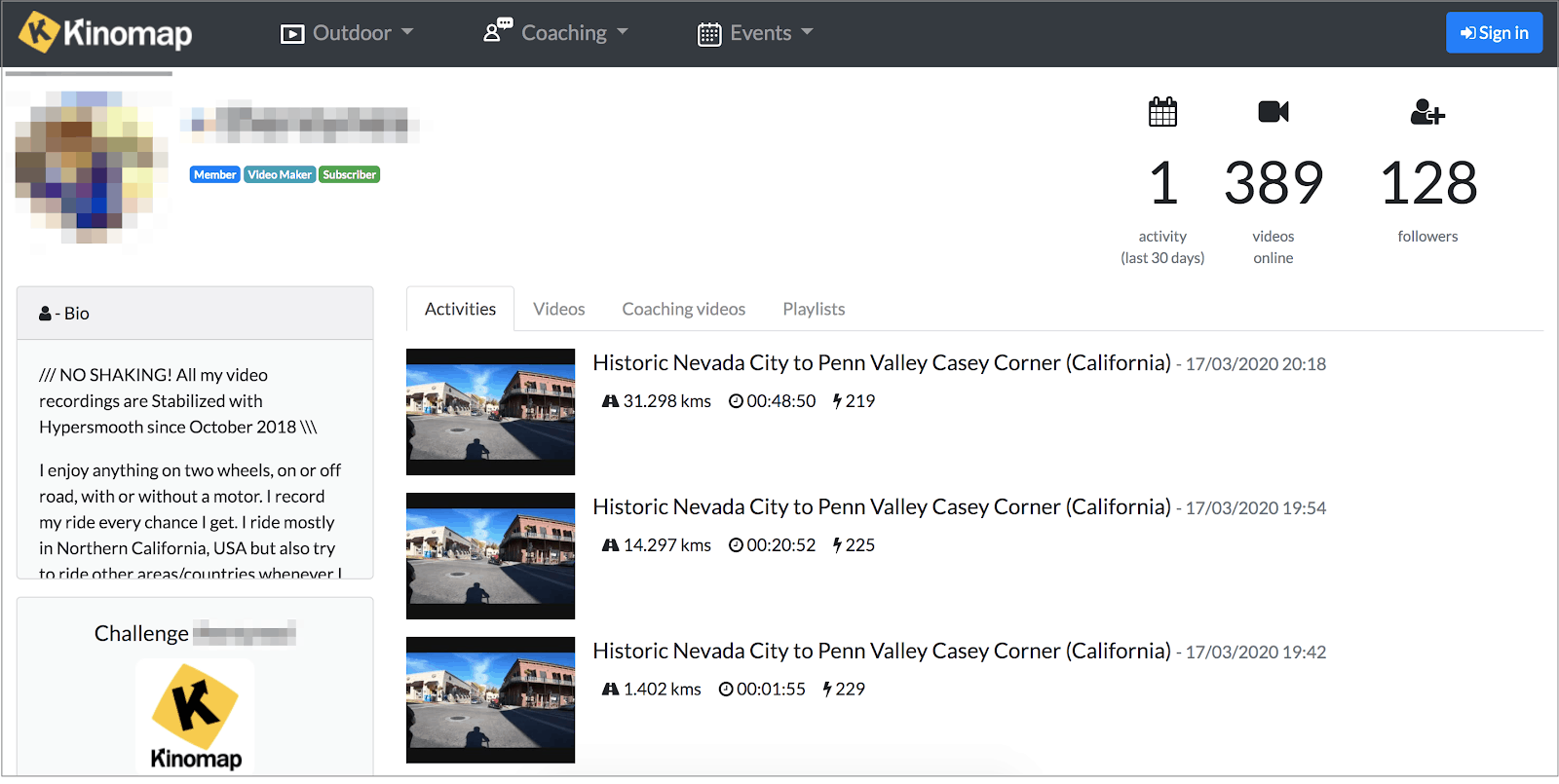
If a malicious hacker had discovered this database, they could easily combine the information contained within in numerous ways, creating highly effective and damaging fraud schemes and other forms of online attack.
They could also potentially take over certain user accounts on Kinomap, using information contained within the database. Many of the exposed data entries included the access keys for Kinomap’s API. With these keys, a hacker would have complete access to the related Kinomap account and could take full control, locking out the account owner.
Data Breach Impact
By not having more robust data security in place, Kinomap made its users vulnerable to a wide range of frauds.
With millions of people across the globe now under quarantine at home due the Coronavirus pandemic, the impact of a leak like this grows exponentially. Unable to access their usual forms of exercise, many people will be turning to apps like Kinomap to stay fit and upbeat during the crisis.
Hackers will be aware of this and looking for opportunities to exploit the increased user numbers on apps without adequate data security in place.
However, Kinomap itself was also vulnerable. A data leak of this nature could seriously endanger the health and finances of the company.
For Kinomap Users
The user PII data exposed could be used in many forms of fraud and identity theft.
For example, hackers and cybercriminals could use the considerable amount of information being leaked about individual users to create effective phishing campaigns. With knowledge of Kinomap users’ account history and their identities, they could send emails imitating the company and tricking users into the following:
- Providing credit card details or access to online financial accounts
- Clicking a link that embeds malicious software on their devices
- Providing additional PII that can be used to target them in unrelated attacks
Because Kinomap users download the app onto a phone or tablet, the consequences of having malicious software embedded on these devices could be devastating. It would allow hackers to target other apps on the phone and infiltrate every aspect of a victim’s life.
For Kinomap
Considering the seriousness of this leak for Kinomap’s users, the company faces several issues going forward.
Most immediately, it may lose customers if they feel the company is not protecting their data sufficiently.
Related to this, as Kinomap is based in France and under GDPR jurisdiction, it should report this leak. Whether Kinomap reports the leak or not, it could face investigation and potential fines by EU regulators.
This would be a time consuming and expensive process, regardless of the legal outcome.
Rivals might exploit the data leak to their advantage. Leveraging the understanding gained about Kinomap's product from this database, they might attempt to replicate or enhance the business strategy that has led to Kinomap's success.
Simultaneously, they could target Kinomap for negative marketing campaigns highlighting the dangers of using an app that leaks your data.
All these outcomes would have severe consequences for the health of Kinomap’s business in the foreseeable future.
Advice from the Expert
Kinomap could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing their servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For Kinomap Users
If you’re a Kinomap user and are concerned about how this breach might impact you, contact the companies directly to find out what steps they’re taking.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in Kinomap’s database as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
When we find a data breach, we use expert techniques to verify the owner of the database, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Kinomap, not only to let them know about the vulnerability but also to suggest ways in which they could make their system secure.
These ethics also mean we carry a responsibility to the public. Kinomap users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak exposing the photos of 1,000s of plastic surgery patients. We also revealed that a company owned by European hotel giant AccorHotels compromised the privacy and security of hotel guests around the world. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 21.04.2020]




Please, comment on how to improve this article. Your feedback matters!