Report: Adult Site Leaks Extremely Sensitive Data
The vpnMentor cybersecurity research team, led by Noam Rotem and Ran Locar, have uncovered a leaking S3 Bucket with 19.95GB of visible data on a Virginia-based Amazon server, belonging to PussyCash and its network.
PussyCash is an explicit ‘cam’ affiliate network that works with the brand ImLive and other similar adult-oriented websites. This leak has exposed more than 875,000 files and has high-risk, real life implications for those involved.
PussyCash Company Profile
The owner of ImLive and PussyCash is officially listed as I.M.L. SLU, a company registered in Andorra.
PussyCash hosts affiliation programs for multiple adult sites, paying webmasters for traffic sent to the sites through banners and exit traffic. They boast 66 million registered members on their webcam chat arena, ImLive, alone. Other sites include Sexier.com, FetishGalaxy, Supermen.com, Shemale.com, CamsCreative.center, forgetvanilla.com, idesires.com, Phonemates.com, SuperTrip.com, and sex.sex, among others.
Partners listed on the PussyCash website include BeNaughty, Xtube, and Pornhub.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s leaking the data.
Understanding a breach and what’s at stake takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true.
In this case, the initial discovery led us to believe that the leak was limited only to a few records on an ImLive bucket alone. However, we eventually found files indicating that PussyCash is ultimately the owner of the leaking Amazon Simple Storage Service (S3) bucket.
Date discovered: January 3, 2020
Date company (PussyCash & ImLive) generally notified: January 4, 2020
Data Amazon notified: January 7, 2020
Date of reply from ImLive: January 7, 2020
Date company (PussyCash / ImLive) notified with details: January 9, 2020
Date of action: January 9, 2020
PussyCash never replied to any of our attempts to contact them regarding the data leak, including their Data Protection Officer. ImLive finally responded to one of our emails, stating that they would take care of it and pass on the information to the PussyCash tech team.
As PussyCash doesn’t hire talent through their main website, it is plausible to assume that their leaking data is from one or more of their other websites, such as ImLive. This is an assumption that we cannot prove without digging further into the data leak. We also saw records specifically mentioning ImLive, which is why we have chosen to use that as an example for portions of this report, and not necessarily the other PussyCash brands and sites. However, it is worth noting that the Bucket itself is named after PussyCash.
Examples of Entries in the Database
Data Impacted
There are at least 875,000 keys, which represent different file types, including videos, marketing materials, photographs, clips and screenshots of video chats, and zip files. Within each zip folder - and there is apparently one zip folder per model - there are often multiple additional files (e.g. photographs and scans of documents), and many additional items that we chose not to investigate.
The folders included could be up to 15-20 years old, but are also as recent as the last few weeks. Even for older files, given the nature of the data, it is still relevant and of equal impact as newly added files.
Photographs and scans of full passports and national identification cards, including visible:
- Full name
- Birth date
- Birthplace
- Citizenship status
- Nationality
- Passport/ID number
- Passport issue & expiration dates
- Nationally registered gender
- ID photo
- Personal signature
- Parent’s full names
- Fingerprints
- Additional country-specific details (e.g. emergency contact information for UK citizens)

Model release and Chinese passport

Brazilian ID card with fingerprint
Photographs and scans of Driver’s Licenses, including visible:
- Driver’s License number
- Photo
- Date of birth
- Height/weight
- Registered gender
- Full address
- Signature
- Type of vehicle the individual is permitted to operate
- Additional PII, varying by country (such as organ donor status and visual impediments for US citizens)
California (USA) Driver’s Licenses, including organ donor status
US Uniformed Services Identification card:
- Branch of service (e.g. Army)
- Military rank
- Color coding (denotes the holder’s current status: retired, active, privileged, dependent of military servicemen)
- Full name
Photographs and scans of Credit Cards, including visible:
- Full credit card number
- Expiration date
- Cardholder name

Texas Driver’s License; Chase Bank-issued Visa Card
Release forms, including:
- Full legal name
- Professional aliases
- Signature
- Date of birth
- Address
- Phone number
- Passport/ID number
- Photographer's name and address
- Witness name and address
- Body measurements (height, weight, hips, bust, waist)
- Details of piercings, tattoos, and scars
- Rates

Model release form indicating body measurements
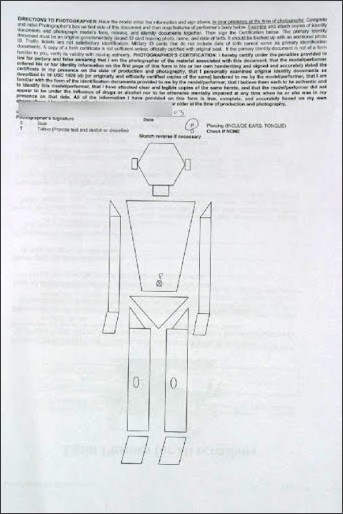
Model indicating body piercings, including places to mark scars and tattoos
Social Security numbers and card scans:

Social Security (USA) card
Photograph of model holding identification cards (often two forms):

Czech model holds two forms of identification
Marriage certificates:
- Full name
- Spouse’s full name
- Occupation
- Age
- Parents’ names
- Date of marriage
- Place of marriage
Birth certificate scans:
- Full birth name
- Birth gender
- Date of birth
- Place of birth
- Nationality
- Parent’s names

Birth certificate of a British citizen
Handwritten bios, including:
- Sexual preferences (ie attractions, fantasies, methods)
- Hopes and dreams
- Current occupation
- Favorites, from music to food to hobbies

Handwritten biography page of a South American model
Countries Affected
These are the countries that we found, but we did not open each file and it is possible that there are more nationalities affected by the leak.
- Africa
- Kenya
- South Africa
- Asia
- China
- Israel
- Kazakhstan
- Kyrgyzstan
- Thailand
- Australia
- Europe
- Bulgaria
- Czech Republic
- Denmark
- France
- Germany
- Great Britain (incl. Wales)
- Italy
- Netherlands
- Poland
- Russia
- Serbia
- Slovakia
- Switzerland
- Ukraine
- North America
- Canada
- USA
- Latin America
- Argentina
- Brazil
- Peru
Data Breach Impact
This leak represents a potentially severe threat to those whose data has been exposed. It has many implications, all of which could very well ruin the lives of the porn models/actors involved.
Identity theft
Within nearly each zip file that our researchers discovered was everything necessary for a criminal to easily assume the identity of another. This is also information that we regularly see being sold on the dark web, often at very attractive prices. With someone’s national identity number, a scan of their photo ID, their full address, credit card number, and even their parents’ or spouse’s name, you have the full identity theft package at your fingertips.
Scams
Using the likeness of high-profile adult actors and actresses, both unethical companies and scammers can con innocent individuals out of their hard-earned money. It’s also plausible that the images and videos of any of these models could be used for catfishing on dating apps/sites to commit fraud on those platforms.
Whether it’s by fraudulently using their image to promote a product or service, or even by impersonating the model and requesting money from personal connections, the threat of a scam looms with this sort of data at the fingertips of criminals.
Public humiliation and impact on personal life/relationships
For many individuals who make the choice to be on camera in a pornographic nature, it is their circumstances rather than their blatant desire to flaunt their nude image that leads them to such a decision. This means that in the vast majority of cases - as indicated by stage names and anonymity clauses in some contracts - they could potentially be devastated by being exposed to their loved ones, causing them irreparable embarrassment and distress.
Many files we found are 10-20 years old, and it might be that since engaging in the Adult industry, the individuals may have moved on to build professional and personal lives outside of the adult industry. For those who have tried hard to forget and hide the past, their family, friends, and colleagues may not know about this, and it can put their current relationships in great jeopardy.
Blackmail and extortion
Authorities career criminals, and individuals who hold personal grudges could all easily blackmail or extort the models by threatening to expose them, either publicly, professionally, personally, or any combination thereof.
Stalking by fans
For some, pornography can provide an important outlet; for a few, they can become obsessed with a particular actor and have a strong desire to meet them. There are those that would potentially follow through with this, thereby stalking the person, if they had enough information about them (such as real name, address, phone number, etc.).
Stalking is a gateway to a number of additional threats, including harassment, rape, kidnap, and even homicide.
Job loss and professional embarrassment
Upon discovery of a ‘side hustle’ or past full-time engagement in the adult industry, it is extremely plausible that this would pose a negative impact on the models. Threatening their jobs and professional reputation.
Exposing LGBTQ individuals
There is grave danger to LGBTQ models who’d be exposed. Around the world, there are about 70 countries where homosexuality is still criminalized - for example, up to 21 years imprisonment in Kenya. In many others, same-sex relations are seen as taboo and repugnant by a significant percentage of the population.
Many gay males and trans individuals are harassed by police, extorted, and blackmailed for bribes and sexual favors in exchange for freedom/security. Those who don't comply are frequently charged with trumped-up charges and sometimes raped instead. Because of this leak, their address is clearly made available - along with other PII - that puts them directly at risk.
Legal repercussions (depending on location)
Pornography laws can vary greatly by region. Approximately 30 countries ban internet porn entirely and nearly 80 ban the sale or distribution of porn. Penalties for violating these bans include various amounts of fines and jail time. Some more traditional societies are a given here, but there are also a few countries where it’s surprising that anti-porn laws still exist (such as Australia).
Breach of contract
By exposing a model’s real name and details - and also connecting it with their stage name - it is possible that the company and even talent agencies are in breach of contract.
Human rights and dignity
There is much that could be discussed in the way of human rights and human dignity in the adult industry. Is it reasonable to consider that it is belittling of models/hosts/actors from developing nations to require that they take pics of themselves next to two forms of identification? It’s also worth noting that much of the PII was not redacted by agencies, who apparently provided/transferred at least some of these documents and photos to PussyCash and/or its affiliated websites.
Many of the models live in or come from countries that are at more of an economical disadvantage. Their socioeconomic status may be, at least in part, a motive in choosing a traditionally taboo occupation.
Finally, we can give thought to the inherent psychological impact a data leak in this particular industry might carry. What might the reaction of the models whose personally identifying information, documents, photos, and videos be? It is important to note that we produce these reports of our findings for the sake of bringing awareness to the importance of safeguarding your own data, and for companies to take seriously the implications of cyber and information security threats. We cannot recommend enough that if you are in a circumstance where you need to virtually confirm your identity, that you redact as much information as possible before sending photos or scans of official documents.
Advice from the Experts
PussyCash could have easily avoided this leak if they had taken some basic security measures to protect the S3 Bucket. These include, but are not limited to:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size. For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
How and Why We Discovered the Breach
During a comprehensive web mapping endeavor, the research crew at vpnMentor identified a breach within Pussycash's database. Using port scanning, our team of investigators probes distinct IP blocks and scrutinizes system vulnerabilities through any exposed gaps. Each open point is thoroughly investigated for potential data leaks.
When they find a data breach, they use expert techniques to verify the database’s identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach.
We were able to access Pussycash’s S3 bucket because it was completely unsecured and unencrypted. Using a web browser, the team could access all files hosted on the database.
The purpose of this web mapping project is to help make the internet safer for all users. As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security.
However, these ethics also mean we also carry a responsibility to the public. This is especially true when the companies data breach contains such a huge amount of private and sensitive information.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
In the past, we’ve discovered a breach in LightInTheBox that compromised the data of its customers. We also recently revealed that a company owned by major hotel chain AccorHotels exposed over 1TB of guests’ data. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
PussyCash.com Comment: "Privacy and the protection of user data is a top priority and concern for us. For this reason, we acted promptly and removed public access to the open folder as soon as vpnMentor (the technological research firm) alerted us to this fact.
It must be emphasized that no information was leaked, with the exception of vpnMentor, we are certain that they will not use it for any purpose.
Also worth noting is that the folder in question is from 2013. It includes details of purchased marketing materials of professional actors who provided videos and images for marketing purposes, which were used to promote various websites. The files actually confirmed that all the actors are over the age of 18.
We must emphasize that the information included in the folder contains no information of any performers or members of any website promoted by PussyCash.com.
As mentioned above, the folder was promptly removed from public access and instructions were reiterated to the various technical departments regarding ongoing controls in respect to information storage."
vpnMentor Comment: Following Pussycash.com comment, we decided to replace the mentions of "cam models" with "porn actors/models. They state that the people in the bucket were "porn actors" and not "cam models", and since it was an assumption we decided to accept their claim.





Please, comment on how to improve this article. Your feedback matters!