Report: Popular Online Retailer Exposes Customers in Worldwide Data Leak
Led by cybersecurity analysts Noam Rotem and Ran Locar, vpnMentor's research team discovered a leak in a database belonging to the online retailer LightInTheBox. A massive database, it contained over 1TB of daily logs and compromised the security of LightInTheBox customers across the globe. Not only is this a major breach in LightInTheBox's data security protocols, but it also creates real dangers for those affected.
LightInTheBox Company Profile
LightInTheBox is an online retailer based in Beijing, China and trading on the New York Stock Exchange as LITB. Founded in 2007, LightInTheBox ships internationally, with most of its customers in North America and Europe. The company focuses on three core retail categories: apparel, small accessories and gadgets, and home and garden. LightInTheBox is a huge business, generating over 12-million monthly visitors on its flagship website, along with several smaller subsidiary companies.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data are obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what's at stake or who's leaking the data. Understanding a breach and its impact takes time and careful attention. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and true. In this case, after identifying LightInTheBox as the database's owner, we contacted them to present our findings. While we didn't receive a reply from the company, the database breach was closed shortly after.
- Date discovered: 20/11
- Date vendors contacted: 24/11
- Date of Action: Approx. 24/11/19
Example of Entries in the Database
LightInTheBox does not provide specific details about their data security and storage practices or the measures they take to protect customers' data. According to their Privacy Policy, they protect user data with: ...administrative procedures to safeguard the confidentiality of your personal information, such as: *Safeguarding all financial transactions done through this Site with Secure Sockets Layer ("SSL") encryption *Granting only employees who are providing a specific service access to your personal information *Working only with third-party service providers who we believe adequately secure all computer hardware. While our business is designed with safeguarding your personal information in mind, please remember that 100% security does not presently exist anywhere, online or offline.
Based on our team's discovery, the measures they were taking were insufficient. The breached database contained over 1.3TB of data, totaling over 1.5 billion records. The database was a web server log - a history of page requests and user activity on the site dating from 9th of August 2019 to 11th of October. Aside from LightInTheBox.com, it also contained data from their subsidiary sites, including MiniInTheBox.com. The data breach affected customers around the world, with entries from many of their international sites, and in numerous languages. Through the web server logs stored on the database, we viewed private personal user data that included:
- Users' IP addresses
- Countries of residence
- Email addresses
- Destination pages and user activity on the website
The following code snippets show how 3 separate email addresses were exposed:
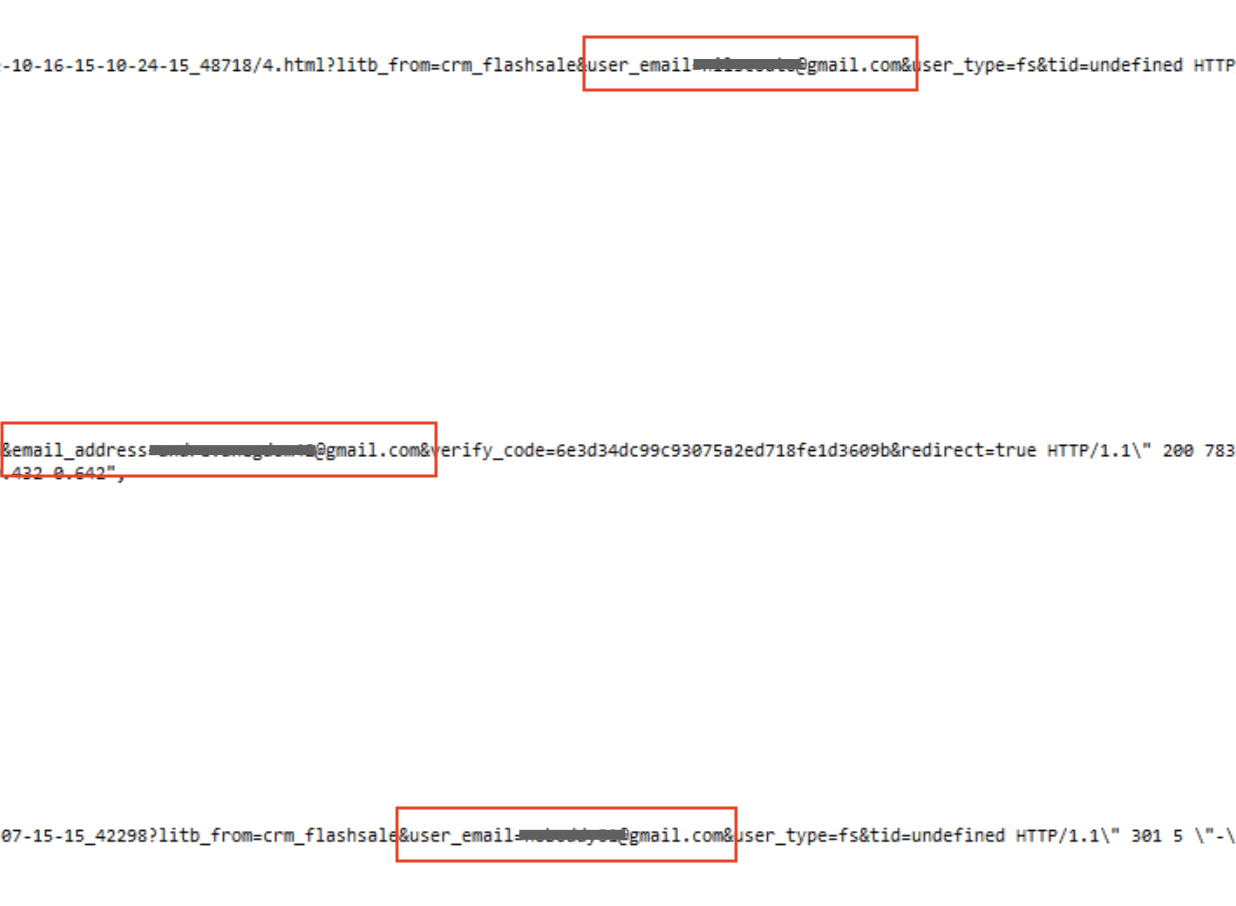 The database also included data from LightInTheBox's Google & Bing Ads advertising campaigns.
The database also included data from LightInTheBox's Google & Bing Ads advertising campaigns.
Data Breach Impact
The data breach signifies a significant failure in LightInTheBox's data security protocols. Despite the data leak not revealing crucial user information, some fundamental security precautions were not observed. Given the season — marked by high volumes of online shopping due to events like Black Friday, Cyber Monday, and Christmas — even a massive leak devoid of user Personally Identifiable Information could pose a risk to both the enterprise and its clientele.
LightInTheBox risks losing business at a crucial time if customers don't feel they can trust the company to keep their data private. Based on LightInTheBox's user reviews on Trustpilot, many customers are already unhappy with their experiences on the website. By exposing their data, LightInTheBox risks further loss of business that could negatively impact future revenues.
For LightInTheBox customers
The exposed data makes those affected vulnerable to many forms of fraud and online attacks. With access to user emails, cybercriminals could create convincing phishing campaigns with emails imitating LightInTheBox. With these emails, victims could be tricked into any of the following:
- Clicking a link that embeds malicious software on their device
- Revealing sensitive financial or personal information
- Providing login credentials for private online accounts
The impact on a victim could be devastating. There is also a physical danger. With a website user's IP address, we were able to identify their city of residence. If a criminal hacker had access to this, along with the other data exposed, they could trick a victim into revealing their home address, and target them for theft and home robbery The following example shows some of the additional information that can be found using someone's IP address: 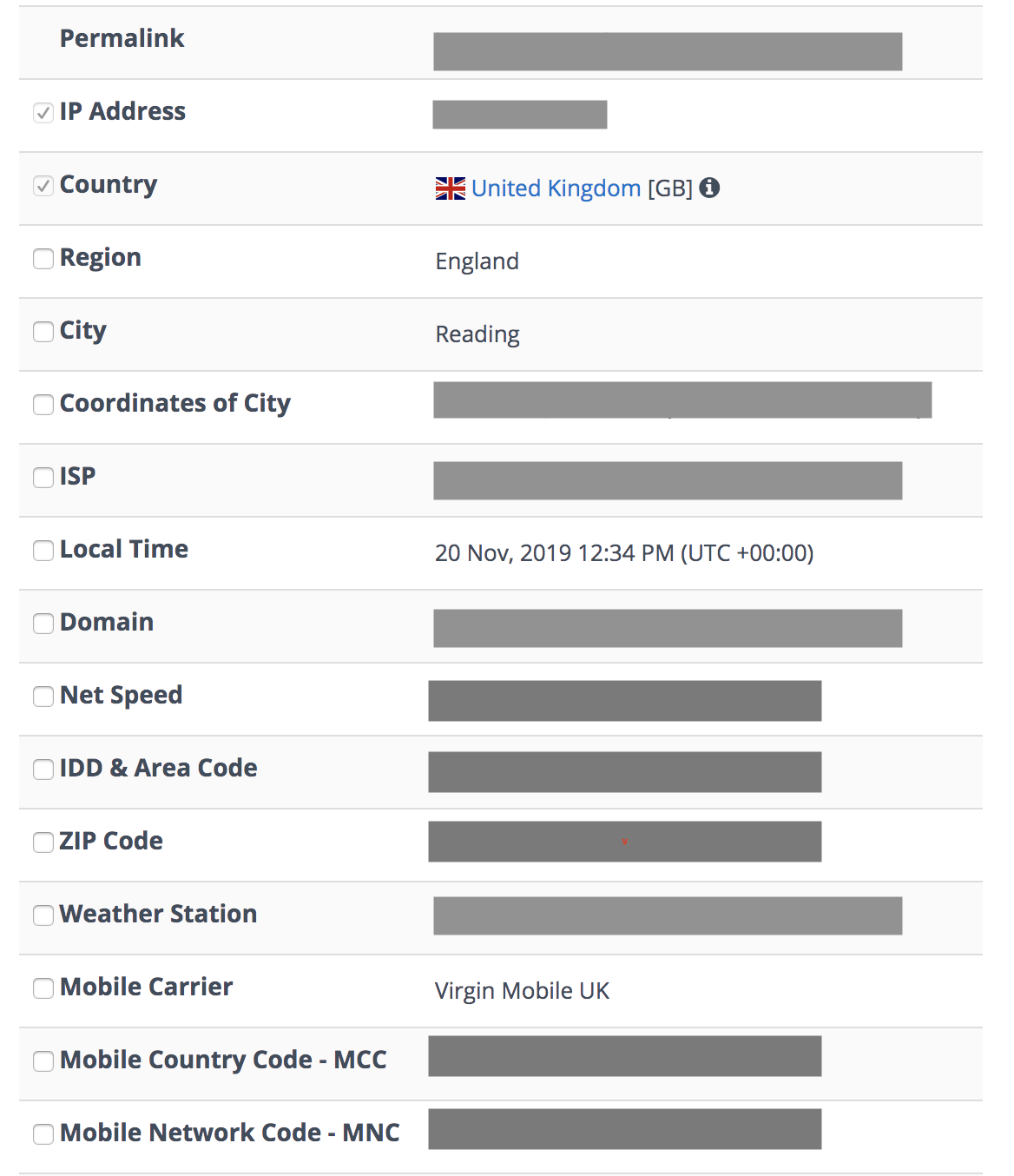 Worst of all, this data breach happened in the lead up to Christmas, when many people will be stocking up on presents, and potentially buying them from LightInTheBox.
Worst of all, this data breach happened in the lead up to Christmas, when many people will be stocking up on presents, and potentially buying them from LightInTheBox.
Advice from the Experts
LightInTheBox could have easily avoided this leak if they had taken some basic security measures to protect the database. These include, but are not limited to:
- Secure your servers.
- Implement proper access rules.
- Never leave a system that doesn't require authentication open to the internet.
Any company can replicate the same steps, no matter its size. For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For LightInTheBox Customers
You can contact LightInTheBox directly and find out how they are resolving this issue and plan on protecting your data better in the future. If you're a customer of LightInTheBox and are concerned about how this breach might impact you, or data vulnerabilities in general, read our complete guide to online privacy. It shows you the many ways cyber criminals target internet users, and the steps you can take to stay safe. You can also use a VPN to hide some of the data exposed in LightInTheBox. A VPN will mask your IP address and country of residence, giving you an added layer of protection even if your data is leaked.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in LightInTheBox's databases as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test open holes in systems for weaknesses. They examine each hole for data being leaked. When they find a data breach, they use expert techniques to verify the database's identity. We then alert the company to the breach. If possible, we will also alert those affected by the breach. Our team was able to access this database because it was completely unsecured and unencrypted. The company uses an Elasticsearch database, which is typically not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing the database schemata. The purpose of this web mapping project is to help make the internet safer for all users.
As ethical hackers, we're obliged to inform a company when we discover flaws in their online security. This is especially true when the companies data breach contains such private information. However, these ethics also mean we carry a responsibility to the public. LightInTheBox customers must be aware of a data breach that impacts them also.
About Us and Previous Reports
vpnMentor is the world's largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users' data. In the past, we've discovered a breach in Biostar 2 that compromised the biometric data of over 1 million people. We also recently revealed that a company owned by major hotel chain AccorHotels exposed over 1TB of guests' data. You may also want to read our VPN Leak Report and Data Privacy Stats Report.
[Publication date: 16.12.2019]




Please, comment on how to improve this article. Your feedback matters!