Report: Theta360 Data Breach Leaks Millions of Private Photographs
vpnMentor's research team has discovered that Theta360 experienced a huge data breach.
Hacktivists from our research team, Noam Rotem and Ran Locar, found the breach in Theta360's photo sharing system. The leak exposed at least 11 million public and private photographs.
The data breach exposed thousands of users' photos, many of whom chose to keep their images private. The breach did not expose users' most personal information, but in many cases, we located their usernames, first and last names, and the captions they wrote in the exposed database.
We couldn't directly access users' social media accounts through Theta360's system.
Timeline of Discovery and Reaction
- May 14: We discover the leak in Theta360's database
- May 15: We contact Theta360 about the leak
- May 15: Theta360 responds to our team
- May 16: The leak is closed
We want to note that Theta360's response to our discovery was the most professional of any company that we've contacted about a leak. They quickly and efficiently closed the breach to protect their users.
Examples of Entries in the Database
Theta360 is a photo sharing platform. It's run by RICOH, a Japanese imaging and electronics company. They are also an industry leader in sales of 360º cameras. In 2016, the company sold at least 160,000 units. They expect to maintain their leader status with projected sales of 250,000 units in 2019.
We could access more than 11 million unencrypted posts from Theta360's database.
We viewed both the posts themselves and identifying information about the poster. This included public and private accounts.
The exposed data included:
- The user's name
- Usernames
- UUID (Universal Unique Identifier) of each photo posted
- Caption included on each post
- Privacy settings
By inserting the UUID of the photos into the Elasticsearch database, we could access any exposed photos. In some cases, we could easily connect the usernames in the database to the user's social media account.
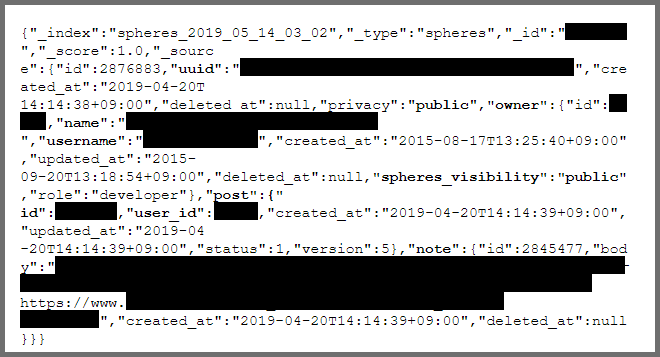
It might not seem like a massive security breach to be able to find public photos. However, it's a huge invasion of privacy. Additionally, using the same methods, we could access photos from users' private profiles.
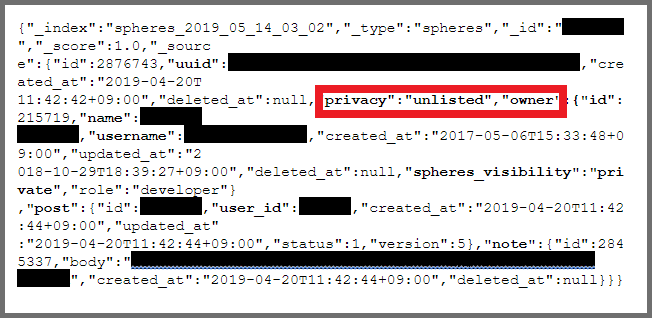

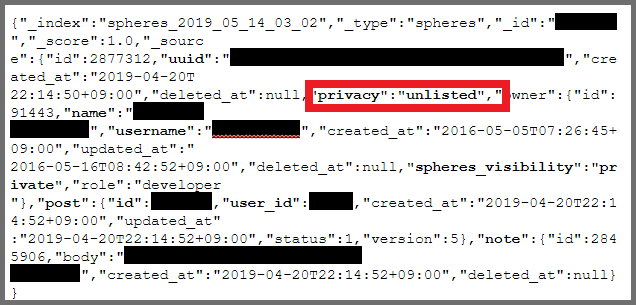
The final example below demonstrates the extent to which the leak compromised users' privacy. Here, the user chose to mark their account as unlisted. This should have masked their presence on Theta360. The account was not only visible on the database, but we could also access the user's private pictures.

Data Breach Impact
Theta360's database obscured more sensitive data like location coordinates. However, this was a major privacy breach that could have a far-reaching impact if malicious actors had the opportunity to download the database.
Many users who posted photos privately obscured personal or private information. For example, some parents choose to keep images of their children private, as they do not want pictures of their kids to be freely available on the internet. Other parents might feel that posting pictures of their children is an invasion of privacy. If you're a parent who is concerned about how data breaches may affect your children, you can refer to our guide to protecting your children on the internet.
Posts like those uncovered in the Theata360 breach could give a bad actor the information they need to steal someone's identity. They only need the date, contents of the photo, and caption.
Family privacy and identity theft are not the sole concerns. If we combed through all 11 million posts, we could have uncovered illicit photos that were intended to remain private.
Publicizing illicit photos can have far-reaching consequences for the subjects. In some professions, this could cost a user their job, as was the case of a teacher whose nude picture was leaked.
For others, leaked photos may share information about affairs or even vacations that need to remain secret. Geotags in data can easily lead to more sensitive information about a user.
How We Discovered the Breach
We discovered the leak in Theta360's database through our web-mapping project. Led by Ran and Noam, the research team scans ports to look for known IP blocks. They then use this information to find open holes in the company's web systems. They can then look for leaks and other weaknesses.
The researchers often have an idea of where a leak may be coming from, which they can use to examine the database to confirm its identity.
After discovering the leak, we contact the owner of the database to inform them about holes in their security. If possible, we also alert the affected users. This way, we can work with companies to make the internet safer and more secure.
While we thoroughly analyzed the accessible data, our research team adheres to ethical standards and refrains from downloading the actual database.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
We recently discovered a huge data breach impacting 80 million US households. We also revealed that Freedom Mobile experienced a breach affecting more than 1.5 million customers. Additionally, you may want to read our VPN Leak Report and Data Privacy Stats Report.
Please share this report on Facebook or tweet it.





Please, comment on how to improve this article. Your feedback matters!