Science of Cybersecurity by Alan Radley- Free Chapter Included
How can we characterise Cybersecurity? How do data breaches, hacks, system exploits and computer intrusions happen - and why? What occurs when Cybersecurity really works effectively, and can we systemise it? Or will the clever hacker always break into any networked device, sweeping all defences aside? On a quest for insightful answers in this ground-breaking book, Dr Alan Radley proceeds to completely deconstruct, rationally analyse, meticulously rebuild and then sanely reassess the entire field of Cybersecurity. A rigorous scientific methodology is applied to networked system design, leading to a comprehensive new model - and accurate taxonomic tree - of all possible types and classes of cyber attacks and associated countermeasures. The upshot is a wholly original, astute and fearlessly honest - yet practically oriented - treatise on Cybersecurity. Outlined here for the first time is a logical explanation of the fundamental theory and principal axioms of Cybersecurity as developed from first principles, and in a format ideally suited to both - the engineering-minded professional - and the less technically-oriented. Share
The above is a summary of the book Science of Cybersecurity, wrriten by Alan radley in order to provide a concise scientific characterisation of Cybersecurity which, according to hum, has not been achieved anywhere else before.
A second volume is already in production, tentatively entitled: The Science Of Cybersecurity; Volume 2: A Comprehensive Taxonomy of Cyber-threats and Effective Countermeasures (- by Alan Radley). Further volumes are planned for which Alan intends to collaborate with other authors.
Science of Cybersecurity is on Amazon here. Below is the first chapter of the book, brought here exclusively for vpnMentor readers.
CHAPTER I- Introduction
THE SUBJECT at hand is the secure transfer of meaning between individual human beings—using networked computers. Our goal is to characterise a point-to-point communication system for replicating information patterns—encapsulated as discrete units of data (e.g. messages/files/folders)—between remote computer nodes; whilst protecting the social integrity (privacy) of said patterns in place and time. A second goal of this book is to establish a safe procedure for point-to-point information transfer—and by means of logically consistent definitions, axioms, analysis and exposition.
The British physicist Professor Donald MacKay (1922-1987) once said that the informational content of a message/representation consists of three components; metrical, descriptive, and selectional [1]. Accordingly, in terms of the point-to-point transfer of information units (datums) between two humans—or the one-to-one replication of meaning from a sender to receiver—we can differentiate between the information pattern that is sent (i.e the atomic, symbolic and/or metrical data being replicated—the digital 0s and 1s etc), and the descriptive and selectional capacity of the receiving system/human.
In other words, the receiver engages in a process of interpretation by utilising his or her ‘beholder’s share’ [2]. Hence the meaning of a message is crucially dependent on the specific way(s) in which the receiver decodes and
interprets the message. Ergo meaningful, effective and efficient communication between two parties depends upon a certain degree of synchronisation and agreement in terms of factors such as language, experience, truth, history, plus mode and context of the communication process itself.
Whereby it is important to realise that the entire subject matter of (communications) cybersecurity depends upon— and is (entirely) developed from—the axiomatic statements and principles presented in the previous three paragraphs. In sum, this book is a characterisation of said axioms. We begin with a simple question—what is security— in-and-of-itself—and especially in terms of digital information sharing? In order to be able to formulate an
answer we must narrow our field of study—and concern ourselves solely with person-to-person (point-to-point) information transfer. We can differentiate this topic from all other information transfer types which involve either a source-point and/or end-point that is not a human being.
Ignored methods include machine-to-machine, machine-to-person, and person-to-machine techniques. In other words; we are not concerned with those cases where a computer initiates transfer(s) of information between machines, or does so automatically from machine to human or vice-versa.1
1 N.B. Most principles—discussed herein—for private/secure point-to-point information transfer—apply also to these other communication types.
Communication Of Meaning
A datum of any idea or thing is a pattern of meaning, an abbreviated description, definition or set of ‘facts’ concerning the thing in question; typically prescribing an event, object, feeling, etc.; in token of, as a sign, symbol,
or evidence of something [Axiom 1].
Datums are typically expressed within the boundaries of a specific language, medium, media and/or code; and normally each datum has an inherent lifetime whereby it may be created, stored, communicated, replicated, lost
and/or destroyed etc. Each datum has a human and/or machine creator/author, plus normally human owner(s) and user(s) (ref. social accessibility (or privacy) status) [Axiom 2]. Datums come in three kinds [Axiom 3]:
• A private datum is accessible only by a restricted group of people—or a particular set of human beings; and is inaccessible to all other persons [Axiom 3.1].
• A secret datum is accessible only by a single human being—typically the owner and often the author; and is inaccessible to all other persons [Axiom 3.2].
• An open datum is (potentially) accessible by anyone— or by an unrestricted group of people [Axiom 3.3].
A communication system is a system or facility for transferring datum(s)/patterns-of-meaning between persons and equipment. The system usually consists of a collection of individual communication networks, transmission
systems, relay stations, tributary stations and terminal equipment capable of interconnection and interoperation so as to form an integrated whole [Axiom 4].
Prior to the widespread adoption of the Internet— information assurance concerned reliable data storage/processing. But today, whilst data backups and storage etc are vital, security is more often associated with data communications security—herein our primary concern.
Accordingly, in the present book we shall explore just one of twelve possible security sub-system types (communication of private-datums): wherein we analyse transfer of private datum-copies existing on a point-to-point communication system (whilst superficially considering aspects of data storage and presentation wherever necessary). Other sub-system security measures may be necessary in a real system—and in order to protect
standard computer processing, storage and presentation operations; and not only for private datums but for secret and open datums as well (see Appendix J).
Throughout our exposition, we place emphasis on human-to-human communication(s)—noting: A) that whilst we recognise that interpersonal communications by means of networked computers inevitably relies on a
combination of several human-to-machine and machine-to-machine communications etc; these aspects relate largely to low-level system-implementation details—and in any case said aspects fall ‘down-stream’ in logical and data-processing terms—and therefore any top-level security principles will normally apply throughout all low-level subsystems; and: B) that any full consideration would include aspects of all twelve security sub-system types and would likely see the present book growing to over one thousand pages in length.2
2 See Appendix J for information on the 12 security sub-system types.
We ostensibly exclude from our discussion all systems of public information sharing (i.e. open-datums) and social networks whereby the information transfer is one-to-many, many-to-one or many-to-many (i.e. Facebook / Twitter). Accordingly—SECURITY—for a person-to-person communication system—can be defined as protection of secrecy, privacy or openness of meaning; or the safe transfer of single/multiple datum(s) between human(s) [Axiom 5].
In this context—PRIVACY—implies that:
• A communication system exists that connects humans together via socially restricted access-nodes;
• The source datum (+ meta-data) is sent from sender to receiver node as a single or uniquely accessible copy;3
• Both access-nodes may serve as memory-nodes for the datum, so long as socially unique access is preserved;
• The datum is protected from unwarranted social access (i.e. who can see, know & change it) by the system;
• Protection of datum access is for specified place(s) and time(s) and to achieve a state of persisted privacy.
We submit that the aforementioned list of axiomatic predicates—for secure and private communication—are valid, sound, consistent, self-evident and complete. QED.
3 In this context—‘uniquely accessible’ refers to protection of Social Accessibility Status (or Privacy Status (i.e secret, private, or open status)) for the communicated datum; whereby (within the boundaries of) the communication system—no change(s) to the pre-existing privacy status can happen (it is immutable in terms of accessibility).
It is salient (for upcoming discussion(s)) to consider how we obtain access to any item in the real-world. To access an item, we:
A. Look for the item—or scan a scene—and in order to identify/delineate the desired thing and so to discover its whereabouts, form and/or precise location (whilst distinguishing it from background clutter). Next we:
B. Move towards the item—or a navigate a path to its location—before grasping/touching it (whilst avoiding any path-blocking objects and/or overcoming any movement difficulties present); and finally we:
C. Study/map/open-up/decode the item—and in order to understand its contents and/or meaning (may require prior knowledge/special techniques and/or unlocking methods and/or unique key(s)).
In a similar fashion, we can define—INFORMATION SECURITY—sometimes shortened to InfoSec, as the practice of defending information (datums) from unauthorised access—including unapproved: inspection, use, copy, disclosure, disruption, modification, recording or destruction of said item(s).
Cybersecurity is a general term that can be used regardless of the form the data may take (e.g. electronic, physical).
Cybersecurity is the (continuous) state of preventing unauthorised communication-system actors/intruder(s) from:
A) Locating the item; and/or
B) Grasping the item; and/or
C) Opening-up the item.
Accordingly, we now define a process of secure information transfer—that consists of private data shared during a one-to-one information replication. Our exposition defines (for the first time) a comprehensive set of cybersecurity—definitions—and axiomatic first principles.
Let us now establish some logical truths. Firstly, in summary, we can state that—SECURITY—for a private, secret and/or open datum is the preservation of social accessibility status (or privacy status)—by means of the explicit protection of said datum’s status. Protection implies the use of systems and procedures— both human and/or machine—to defend said privacy status.
Social Accessibility (Privacy) Status
The ability of a person to see, know and/or change a datum’s form and/or content [Axiom 6].
Privacy [cp. Secrecy = datum is accessible by only one person]
A private-thought/datum is distributed/available to a limited number of people; and hence some form of social sharing (& trust), plus protection is implied; and in order to prevent it from morphing into an open-thought/datum
(or partially open-thought/datum).
Protect = Lock, Block or Conceal an item [Axiom 7].
Lock—unsafe-actor(s) cannot open/know an item’s form/content.
Block—unsafe-actor(s) cannot reach/grasp an item’s form/content.
Conceal—unsafe-actor(s) cannot see/find an item’s form/content.
Security = Protect accessibility status of item.
Access = Find, contact and/or know an item.
Posses = Find (see/locate) plus contact (reach/grasp/hold) an item.
Note that within the concept/remit of locking an item; ofttimes there is a difference between having and knowing an item. Locking creates a gap/barrier or unbridgeable chasm—between possession and full access/understanding— for unauthorised parties—and especially in relation to the inner meaning of information.
Now that we have established the fundamental theory of secure communication of meaning; we need to specify the basic features of a practical security system.
We begin by identifying a secret-datum (analogous to a secret-thought)—which has not yet left the source-point (or sender’s mind); and which is assumed to be unique in that nobody else can know (or discover) the precise form or content of the datum at the source-point. Once the datum arrives at the destination-point; then it is a private-datum; because it now exists—ostensibly solely—as an identical copy in both locations simultaneously (it is a private-thought).
As an aside, an open-datum is one that anyone may access—but open-thoughts/datums are not a subject of this book (see the companion book ‘Self as Computer’ [3]).
Note also that the terms private, secret and open thought, are simply analogues of the relevant datum types (See Appendix A). Hence forth adjudging that a point-to-point communication is private and secure; is equivalent to
saying that the original unit of meaning existing at the ‘source’ node has, as a result of the one-to-one replication, only one accessible copy—at the ‘receiver’ node.
Furthermore this copy is—unequivocally—accessible only by the (trusted) human for whom the communication was intended (i.e. it is access-controlled).
We call such a process single-copy-send—or socially secure communication [Axiom 8]—whereby the process of communication may itself be private (no public meta-data exists); and there is no possibility of any nth-party
obtaining a copy of the communicated datum. A party might be able to guess the informational contents of the datum—or presuppose that the sender/receiver parties possess it and/or have exchanged it—but that is altogether different from certain knowledge.
Note that for a secret-datum socially secure communication restricts access to just one person. Hence the sender and receiver/viewer are the same person; and the system simply ‘memorises’ the datum. In a like manner, open-datums are memorised by the system; but are then somehow made available to any party; which assumes that the system itself has a special kind of security (social accessibility protection) whereby said datum(s) are broadcast by means of the system to many/all humans. Implied here is that the system must be open-access or ubiquitous in terms of meaning dissemination.
It seems prudent—at this point—to ask another straight-forward question; specifically: What is the nature—and architecture—of secure and private cyber-communication?
In actual fact—answering this pivotal question—will be the primary task of this short book.
And in order to formulate an answer; it is necessary to first establish the key facets of the desired communication ‘chain’ between the parties who wish to exchange information in a secure fashion.
Human Communication
Transfer of discrete package(s) of meaning—messages— between people; or the one-to-one replication of datum(s) between minds, plus nominal meta-data (perhaps).
Socially Secure Communication
Communication that protects socially restricted access (secrecy or privacy) for the replicated meaning—datum(s) + nominal meta-data (perhaps).
Open Communication
Communication that protects socially open access for the replicated meaning—datum(s)—and also any meta-data for the communication process itself (perhaps).
Single-Copy-Send
Communication of a datum (+ meta-data) with guaranteed social security.
Addendum: Note that accurate determination of the (measured/judged + time-bound) social accessibility status (i.e. Privacy Status)—and its associated protection status or Security Status (for a datum-copy)—means judging
whether (or not) an (ostensibly) private-datum is/has-been/can-be (i.e. at-present/ in-the-past/future) communicated with absolute or partial/absent security—and this may sometimes be difficult to achieve with any degree of
confidence /assurance. Privacy Status (for a datum-copy) is the legitimate (but potentially transitory/changeable) social accessibility status (i.e secret, private, or open). Whereas Security Status (for a datum-copy) is a protected or
unprotected Privacy Status, and accordingly may be known or unknown at any specific epoch—and is equivalent to the measured/judged privacy protection status. A datum-copy’s Privacy Status works together with its Security Status to perpetuate and defend the datum’s inner meaning.
Accordingly, we are now in a position to characterise Information Security (or cybersecurity/InfoSec) in terms of an interesting new copy-centric metric which is defined by a few simple questions:
• How many copies are there?
• Where are the copies?
• Who can see, know and/or change a copy?
• How long do copies hang around?
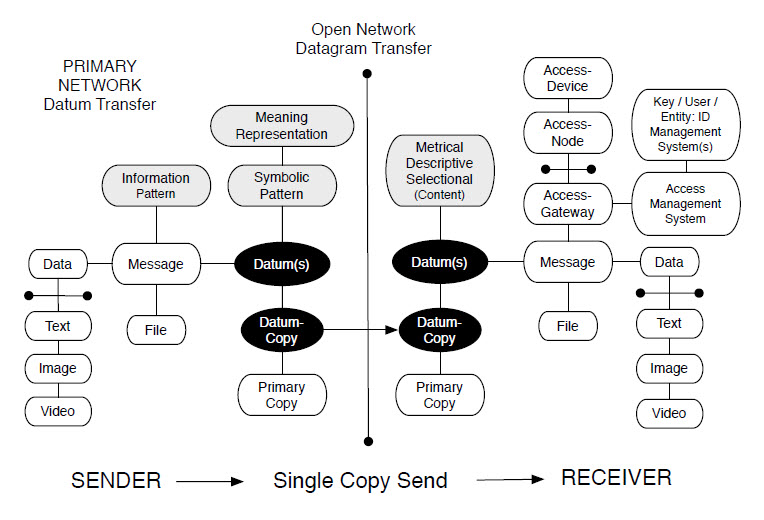
Figure 1: Replication of a Primary Copy
Primary Copy
A primary-copy is a place-holder for a private datum of meaning—existing within the boundaries of a point-to-point communication system; whose content and form are restricted in terms of social access (i.e who can see, know & change the same); whereby the datum is (ideally) communicated via single-copy-send from the source-point to any (and all) designated receiver-point(s) [Axiom 9].
Secondary Copy
A secondary-copy is a (communicated/backup) replication of a primary-copy—existing within (or outside) the boundaries of a point-to-point communication system—that may be legitimately produced by the communication process itself (e.g. a central server copy); and/or be illegitimately created as a result of the unwarranted activities of a hacker [Axiom 10].
Note: Single-copy-send is compatible with legitimate secondary copies due to the fact that, for instance, in a central-server network setup, ostensibly private secondary copies are generated to enable offline sharing and storage of data.
Christian Rogan pointed out to me that the peer-to-peer primary communication copy is also (from one perspective) the true version/copy, which leads to another solution often described as Self-Aware, whereby the object (file or data) enforces its own security protocols/policies.
Tertiary Copy
A tertiary-copy is a replication of a primary or secondary copy—which is generated post-communication by extracting datum(s) from a large body of communication data (e.g. a transatlantic data pipe) [Axiom 11].
N.B. Tertiary copies (whilst nefarious) are compatible with socially secure communication or single-copy-send—because for example—the datum-copies may be protected from unsafe-actors by means of strong encryption and/or coding etc.
Cybersecurity as a Science
Our ambitious aim is to establish the first founding principles/laws of a new Science of Cybersecurity.4 However some experts are adamant that cybersecurity can never be established as a science. This is claimed to be so because—any and all social accessibility protections which are put in place will always have human opponents. That is, in this field alone, human antagonists exist—who work constantly to try and break any security measures present.
Accordingly, cybersecurity cannot ever be a science—but is more akin to a game, war or political struggle.5 However, whilst the author acknowledges the existence of vital social elements within the boundaries of the highly technical field of cybersecurity; it is his belief that application of the scientific method—consisting of a combination of empirical observation and logical reasoning—must always play a significant and foundational role in any cybersecurity scenario whatsoever. QED.
Our goal is to bring formalism to a field that doesn't even have one—that is to bring unity, consistency and order—to the field of Information Security (communicative-aspects). Strangely absent is any kind of top-level theory, and missing are fundamental definitions and/or first-principles etc. Ergo, the system-designer's job becomes one of—collecting partial formalism(s)—before somehow stitching them together. The net result is—partial truth(s) and/or sub-optimal approaches—or at least major difficulties.
Conversely, we seek to establish a foundational framework for the entire field of: information-security; and by means of comprehensive, integrated and holistic perspective(s)— combined with use of the scientific method.
4 See Appendix M: “What Kind of a Science is Cybersecurity?”.
5 N.B. Wars are won by use/application of Science!
Notes
1. MacKay, Donald., Information, Mechanism and Meaning, The MIT Press,1969.
2. Gombrich, Ernst., Art and Illusion, 1960.
3. Radley, A., Self As Computer, 2015.
4. Radley, A., Computer As Self, Proceedings of the 4th International Conference in Human-Computer Interaction, Tourism and Cultural Heritage, Rome, Italy., 2013.
The only truly secure system is one that is powered off, cast in a block of concrete and sealed in a lead-lined room with armed guards.
— Gene Spafford
If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.
— Bruce Schneier
Hacker
In the computer security context, a hacker is someone who seeks and exploits weaknesses in a computer system or computer network. Hackers may be motivated by a multitude of reasons, such as profit, protest, challenge, enjoyment, or to evaluate those weaknesses to assist in removing them.
Monoculture
A monoculture is the case where a large number of users run the same
software, and are vulnerable to the same attacks.




Please, comment on how to improve this article. Your feedback matters!