Sqrrl – Hunting Threats Before They Do Real Damage
- Please tell me a little bit about yourself and your background.
- Before diving into product details, let’s talk about your company and product at a high level. You claim that Sqrrl is the “the threat hunting company” – what exactly do you mean by that?
- Your one product is Sqrrl Enterprise – please tell me about it.
- What can you tell me about your pricing model?
- Do you offer a service where I can have you help me immediately if I know or suspect that I have suffered a cyber-attack?
- What are the types of attacks that are easiest to hunt? Which are the hardest?
- What are the top 3 tips you would offer for companies to avoid security attacks?
- How do you define your market? Who is your specific target audience within that market?
- How many active customers do you have today? Where they are mainly located?
- How would you describe your current typical customer?
- What methods do you normally use to attract and engage with new customers?
- Who do you see as your main competitors?
- How do you see your tools as different as and/or better than theirs?
- How do you see threat hunting technology and the security market in general, evolving in the coming years?
- What are your future plans for Sqrrl?
- What is the story behind the name Sqrrl?
- How many employees do you have today? Where are they located?
- How many hours a day do you normally work? What do you like to do when you are not working?
Wouldn’t it be great if instead of reacting to security attacks we could actually proactively hunt them down and disrupt them before they do any damage? According to Mark Terenzoni, CEO of Sqrrl - a threat hunting company - this is something that is not only possible today, but is actually necessary today in order to stay ahead of cyber-attacks.
The assumption today needs to be that security threats have already penetrated the walls of the network and are preparing to attack. The Sqrrl threat hunting platform uses technology developed and used by the NSA (National Security Agency) to enable security analysts to find these adversaries hidden inside their network before it is too late.
Please tell me a little bit about yourself and your background.
I joined Sqrrl four years ago. I was brought in by the investors to drive the strategic direction of the company. Before that I worked at a variety of networking and storage companies – both startups and large companies. My most recent position before joining Sqrrl was as Senior Vice President at F5 Networks.
Before diving into product details, let’s talk about your company and product at a high level. You claim that Sqrrl is the “the threat hunting company” – what exactly do you mean by that?
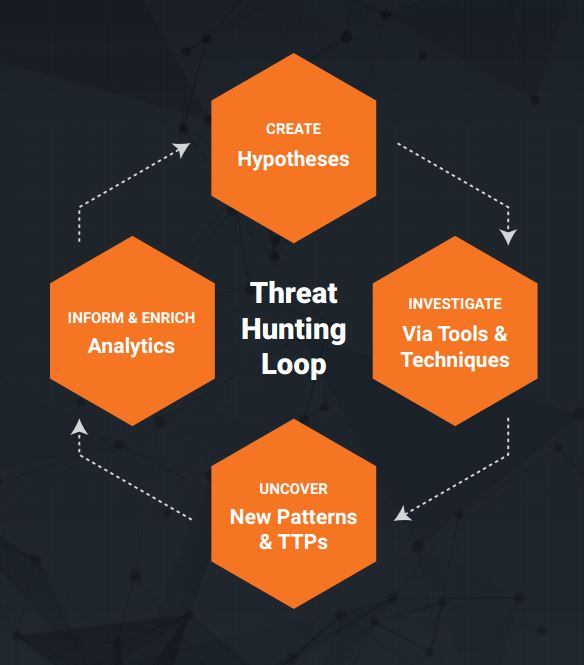
We define cyber threat hunting as “the practice of searching proactively and iteratively through a network or data set to detect and isolate advanced threats that evade automated solutions.”
The typical situation today is that after a company’s security team spends days analyzing a security attack, they then first ask the question “Why didn’t we detect this earlier?” What needs to change is that you should not wait to react to cyber-attacks. You must be proactive to understand what is happening in your network before it is too late.
We break the process down into three steps or phases:
- Target:Scope the data sets that will be used in your investigation. Hunts can branch from various starting points.
- Hunt:Proactively and iteratively search through network and endpoint data to detect and isolate advanced threats that evade more traditional security solutions.
- Disrupt:Seamlessly pivot from hunting to forensic analysis, in order to disrupt adversaries before they fully execute their attacks. These analyses can also generate new indicators that can be fed into complementary security systems, creating a valuable security feedback loop.
Your one product is Sqrrl Enterprise – please tell me about it.
Our Sqrrl Enterprise platform is a global leader in threat hunting. We believe that in order to really achieve the goal of threat hunting that I defined previously, the hunting platform must have the following characteristics and capabilities:
- Big Data capabilities
- Behavior analytics
- Real-time security behavior graph
- Hunting workflow
- Single structural view of many different data sources
- Extensibility
- Massively scalable
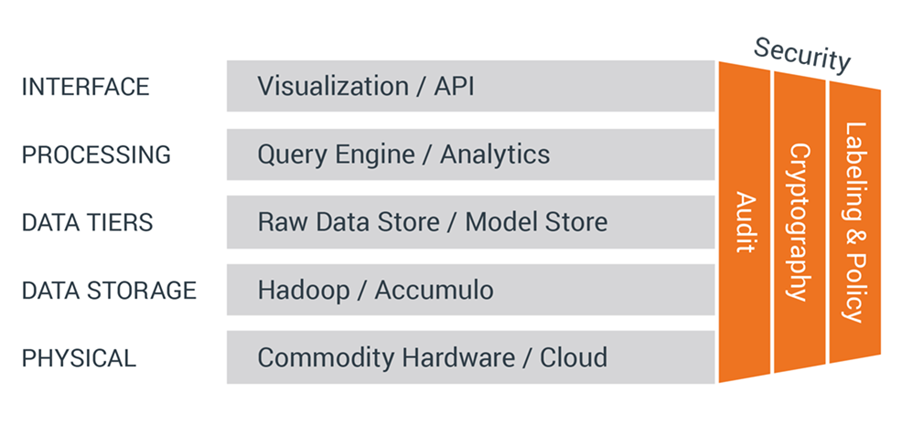
Let me share with you some of the background of the company. The company founders and much of the development team came out of the NSA (National Security Agency). Back in 2008, they worked together on a very large, distributed database project that was started in order to meet the NSA’s rapidly growing data needs. The project eventually became known as Apache Accumulo and is used today throughout the Department of Defense and the U.S. Intelligence Community. It is a NoSQL database that is extremely scalable and provides very high performance.
In 2011 the core engine was released as open source software. In 2012, a group of the core creators, and contributors to the Accumulo project co-founded Sqrrl, taking this engine and positioning it for use cases in the enterprise environment.
What can you tell me about your pricing model?
We try to keep is pretty simple and in the hands of the customer. It is a subscription model, where the cost depends on two main factors:
- How much data you want to store in the system
- How many named analysts (i.e. users) do you have.
Do you offer a service where I can have you help me immediately if I know or suspect that I have suffered a cyber-attack?
That’s a good question. We are not really going after that market. Most of our customers engage with us for ongoing infrastructure support. However, we do have several partners who specialize in emergency incident responses that are using our tools.
What are the types of attacks that are easiest to hunt? Which are the hardest?
We don’t focus on the simple stuff. To protect against basic attacks, we tell our customers to be sure to have proper policies in place (and to enforce them).
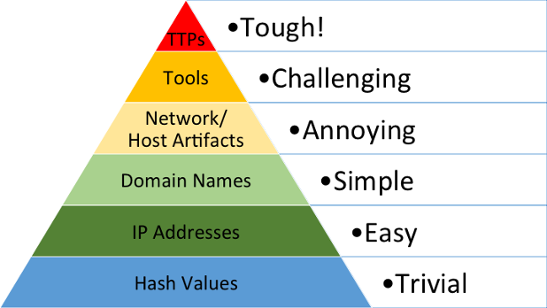
Our software hunts for various Indicators of Compromise (IoCs). There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Our Security Advisor, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. The diagram shows how difficult (painful) it is to collect and apply an IoC to cyber security tools as well as how much pain the IoCs can inflict on cyber adversaries
What are the top 3 tips you would offer for companies to avoid security attacks?
Unfortunately, we are past the phase where prevention is the answer, so my top three tips would be:
- Collect your logs.
- Train your people.
- Know where all of your assets are located.
How do you define your market? Who is your specific target audience within that market?
We target mainly the top global 1,000 companies, although any organization with a SIEM (Security Information and Event Management) system or a SOC (security operations center) would be a natural potential customer for us. We engage with companies across all vertical markets, including governments.
How many active customers do you have today? Where they are mainly located?
We serve companies all across the world. We currently have about 40 active customers, including ten Fortune 100 companies.
How would you describe your current typical customer?
Our typical deal size is $300K - $500K. Our objective is to make Level 1 Security Analysts more productive and to make Level 3 analysts more proactive.
What methods do you normally use to attract and engage with new customers?
We don’t spend a lot of time or effort on outbound marketing. We focus instead on thought leadership and sharing high quality content on our web site. This causes customers to come to us, so that more of our leads are inbound. We are increasingly becoming “top of mind” in the security industry.
Who do you see as your main competitors?
Our main competitors today are companies using log management systems to try to piece together some information on their own.
How do you see your tools as different as and/or better than theirs?
Our platform comes as a complete package with comprehensive support, ensuring it is ready to operate seamlessly from the moment you start using it. The tool itself offers a multitude of significant benefits:
- Modern analytic technology that scales to Petabytes on commodity hardware
- Behavior graph that fuses disparate information in real-time
- Visual presentation of full situational awareness
How do you see threat hunting technology and the security market in general, evolving in the coming years?
The situation today is that companies spend 90% of their budget on prevention and 10% on detection and response. The trend is shifting towards 40% prevention and 60% detection and response. This is in recognition and admission of the fact that the bad guys will get in.
A few more of my observations are:
- The role of the CSO (Chief Security Officer) is becoming increasingly important and prominent.
- The attack surface area is changing and growing rapidly, with the increased use of mobile devices and cloud-based solutions.
- The marketplace is still very “noisy.” The companies that survive are those that truly innovate and that solve customer problems.
What are your future plans for Sqrrl?
We plan to continue to be a market leader. This is not easy – the product roadmap never ends, because the attackers are always innovating. We will continually add more detection analysis tools, refine our visualization tools, and integrate more seamlessly into our customers’ existing infrastructure.

What is the story behind the name Sqrrl?
This too stems from our NSA roots. Secret Squirrel was a cartoon spy character in the 1960s.
How many employees do you have today? Where are they located?
We currently have 50 employees, the majority of whom are located in our Cambridge, Massachusetts headquarters. We have expansion plans to grow rapidly in the second half of this year.
How many hours a day do you normally work? What do you like to do when you are not working?
I spend most of my time thinking about how I can help customers protect themselves from cyber threats. This can translate into long days at times. It doesn’t feel like that much, though, since the day flies by so quickly.
When I am not working I love to spend time at my kids’ sporting events and to just hang out with my family.




Please, comment on how to improve this article. Your feedback matters!