Stop Worrying About your Shared Files, Ascema is Here to Help
GeoLang is an award-winning UK-based software development company specialising in the field of enterprise security and business resilience, offering leading Information Management solutions to help your organisation manage and protect its sensitive and high-value information across all data networks– including on-premise, hybrid or in the cloud. We had a chat with CEO Debbie Garside in order to understand what their product, Ascema, is all about. Share
Please describe the background that led you to founding GeoLang.
I'm a serial entrepreneur, and I’ve been running IT related startups for 30 years. GeoLang was incorporated in 2006, originally to support the work we were doing with standardization bodies; R&D into International, European and British Standards. We were fortunate to receive contracts from BSI and ISO. Our work within standards led us into the cybersecurity arena through different organizations that we became involved with, such as ICANNand ITEF. I was active in the ICANN forum, I was an administrator for the general forum, and I was also very active within the Internet Engineering Task Force. I was the principal UK expert for Language and Coding, as well as a BSI chair and an ISO convener. I also wrote British and international standards, for language encoding. We were led down the cybersecurity path by the work that we were doing and it became a natural transgression.
What can you tell us about your product, Ascema?
The partnership between Jaguar Land Rover and the University of Surrey gave rise to Ascema. The University possessed an algorithm that had its roots in a UK-based intelligence agency, serving as the British counterpart to the American NSA.
Jaguar Land Rover had identified a risk to their intellectual property and security in supply chains and, in particular, they were looking at how to prevent data leakage in the cloud. So, we created a collaboration between the three parties. GeoLang was brought in as the organization tasked with developing a solution, interacting with the business analysts from Jaguar Land Rover for 18 months. We had support from UK government in terms of funding to do the research and development via InnovateUK, which is the UK’s government national funding body; essentially we followed the UK innovation eco-system in the development of Ascema. We discovered 32 use case scenarios within Jaguar Land Rover that were relevant to the field of data loss prevention.
That's how Ascema was born. Since then, we have developed and patented new algorithms. We built the Ascema platform, which at its core, is a fingerprinting, indexing and matching algorithm that works at high speed and scales to protect unstructured content; content within documents and data streams, such as email content and any text based content and we can work in any language or script. So, a use case scenario would be protecting the sensitive content within a patent document or a contract, or mergers and acquisitions agreements. That’s unstructured content which actually needs protecting within systems. In particular, we were looking at how to enable cloud adoption by de-risking it.
How does Ascema work?
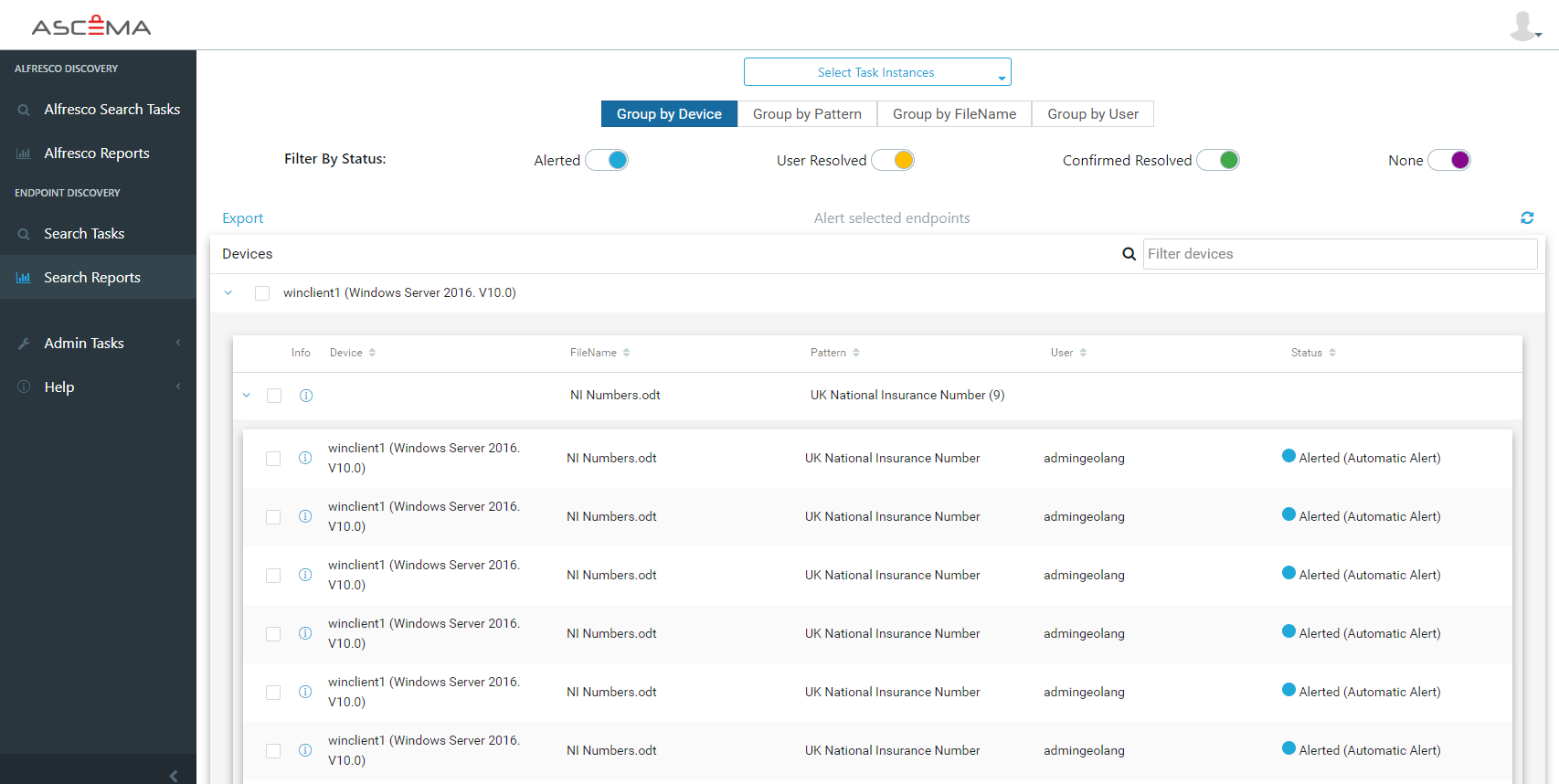
The platform incorporates the fingerprinting indexing and matching as well as traditional pattern matching for national health numbers, passport numbers, PCi and PII as well as traditional DLP and automated classification. In addition we have developed data discovery solutions for endpoints and server. So in short, it's a platform that detects, protects, remediates and reports on content with machine learning algorithms that can be trained with just one document to recognize information types and automatically classify them.
Ascema is integrated at the API level with cloud applications and we have also integrated with on premise applications such as Windows file servers, email solutions and endpoints.
We offer a federated DLP solution for enterprise- authorized applications; in essence protecting across the digital application estate of an enterprise. The premise for this was looking at enterprise data and looking at the risks to that data.
What we discovered in 18 months of working with Jaguar Land Rover and all their departments was that the biggest risk to data today is not from hackers but from insider threat; your own employees, who all have access to your crown jewels on a daily basis.
Can you describe the profile of an insider threat?
When most people think of insider threats, they visualize somebody walking around in a black coat with sunglasses and a hat - stealth mode; you’ve seen the pictures. But that’s not what insider threat is all about. Insider threat may be categorized as three distinct actors.
- Erroneous Employee: an employee going about their day to day business and inadvertently sharing sensitive data outside of the organization or a bonafide enterprise group. This is classic end user error which accounts for over 90% of insider threats.
- The Opportunist, Malicious Insider: somebody who doesn’t necessarily know what they’re doing, but may be leaving the company and thinking, hey, I’m just going to take this information with me. So, they use enterprise- authorized applications to steal the information. They email the information to themselves. For example, a Chinese scientist for a major pharmaceutical group emailed patents to China just before she left the company, using the company’s own email system. Those sorts of problems are very easy to solve.
- The Malicious Insider, the Edward Snowdons of this world, going about in stealth mode, who are really thinking about what they’re doing and quite difficult to stop. You can put all sorts of systems and solutions in place but you’ll never stop them 100%. All you can do is put systems and solutions in place that will make it difficult for them to bypass. If you have the right systems in place, they will leave breadcrumbs, little tracks that can be used as evidence if they’re picked up by the right systems.
Our solutions deal with insider threat within enterprise- authorized applications such as email, cloud collaboration environment, windows file servers and endpoints. We believe that end users should be assisted by technology to do their jobs, and that end users should not be losing their positions through data breach. It's up to the enterprise to put solutions in place to protect their sensitive data, and that’s what Ascema is designed to do. This is now reinforced by the recent General Data Protection Regulation which came into force in May 2018 where organizations must educate end users and also provide tools to assist them with managing sensitive data. It was our primary goal to develop an elegant, simple to use and deploy solution that is accessible to companies of any size, from enterprise with thousands of employees down to micro enterprises.
What happens once Ascema is activated?
Ascema Data Discovery and Data Loss Prevention technologies take just minutes to deploy to an enterprise- authorized application such as Office 365, Box, Exchange online, Exchange on premise, or Windows file server. Depending on what you wish to do, it’s generally a 3-step process. As an end user, if you want to protect your unstructured data or market sensitive data, it’s easy to highlight text within a document, right-mouse click on it, and choose ‘Protect with Ascema’.
We have five intervention levels: track, alert, block sharing outside of a named set of collaborators, block sharing externally, and quarantine. So, it’s very simple for the end user to protect their data if they wish an equally as easy for enterprise administrators to create enterprise wide protection strategies using automated classification..
From an enterprise point of view, it’s also simple to train the system to recognize template-based data. Organizations such as Jaguar Land Rover, follow template processes which often hold sensitive data. As a use case scenario, Jaguar Land Rover have 500 RFQ (Request for Quotation) engineers who use templates every day. They’re creating many requests for quotations for parts, and each of these documents will contain snippets of intellectual property within them. Being able to automatically protect all these templates as they are created and as they flow around the enterprise- authorized applications is simple.
Again, a 3-step process. Upload one template into the Ascema system, choose to classify, choose the intervention level, and then, whenever we see the data flowing around the system based on these templates, it will be protected and classified automatically.
If someone tried to copy a snippet of information from one of those documents and paste it into an email and send it outside the organization, Ascema will protect it in real time and report back to the content owner–the person who originally protected the content, and also to the enterprise as a whole. All that happens in real time.
How do you balance the conflict between security and ease of use?
It doesn’t affect ease of use because it is an API integration with no latency whatsoever. The end user will be guided in appropriate behavior. If they are behaving appropriately, they will not see anything. If they behave inappropriately, Ascema will alert the end user about what they should and shouldn’t do, depending on the level of protection that has been chosen for the content. It depends on how much interaction the end user can have with that content, so they can choose to override it in some cases, depending on the configuration of the original owner. They wouldn’t be able to override it if it was set to block sharing outside of a named set of collaborators or the enterprise or quarantine for example. It’s designed to be as unobtrusive as possible, whilst also assisting the end user to behave appropriately with sensitive data. The system also educates end users on data protection policies for the various data and different types of documents.
We believe that this system allows the enterprise to use DLP to remediate where most 98% of current DLP solutions are only tracking as IT administrators are afraid they will block something inadvertently. Our system puts protection in the hands of the enterprise and the individual employees who are owners of the data where required. Most systems don’t allow for end user interaction; it’s the end users who know the importance of the data, not the system analysts so by excluding them these antiquated systems are not taking advantage of a significant security resource, an enterprises own workforce. The system analyst or business analyst are looking at thousands of lines of reports and events, but have no idea what they are. This is what I term generally as ‘after the horse has bolted’ technology.
In terms of reporting, we do report at enterprise level to those system analysts, end users and department heads. But within that reporting, we offer contextualization, which is what our competitors don’t do. We give the event in context and give a little bit of the content around it. If we detect a credit card number, we give a few words about it so you can see that it is a credit card number, while redacting the actual number to prevent further risk of sensitive data leaving the organization. It's about being smart, reporting back to the people that matter within the enterprise, so that they can make appropriate decisions.
We're integrated with Windows endpoints, we can also integrate with Mac, Windows file server, Microsoft word, Office 365, Exchange, and all office applications. We have a strong technology partnership with Alfresco, and we can report out to HP Arcsight, IBM QRadar and any other SIEM. We extend the capabilities of traditional classification solutions such as Boldon James and Titus in that we can read their classifications and protect the actual content within the documents that have been classified; as opposed to just labelling them. Thus, we are detecting, protecting, remediating and reporting in real time at a level of granularity otherwise unavailable.
In April 2018 we were acquired by the Shearwater Group PLC who are supporting our scale up plans.



Please, comment on how to improve this article. Your feedback matters!