Twingate is Revolutionizing VPN As We Know It
Twingate provides a seamless way to securely access your company’s private resources and eliminate the need for VPNs. Twingate replaces your VPN with a faster, more secure, and easier-to-manage remote access solution designed for today’s world of distributed work. It can be set up in 15 minutes or less and requires virtually no changes to your company’s existing network and workflows. Twingate is also designed to eliminate the structural security issues with VPNs, and enables you to adopt a “zero trust” approach to managing access to your company’s private applications and data. In this interview, Twingate CEO Tony Huie discusses the complexities of the zero-trust approach and its promising future for organizational security. Share
What led you to found Twingate?
When we started Twingate in 2019, we believed that the secure access problem (aka the “VPN problem”) was more than just a technology problem. It was a usability problem. For over 20 years, VPNs have been the default remote access solution for millions of companies, delivering the same mediocre user experience during that whole time.
We first saw the power of treating usability as a first-class citizen when we helped take Dropbox to the business market a decade ago. Back then, we saw how the simplicity and ease-of-use of Dropbox could revolutionize outdated workflows and clunky, legacy products like file servers. When we dug into the secure access problem, it was clear that the same patterns existed. There was a decades-old technology in VPN that was causing friction and frustration for end-users and IT teams, but alternatives were too hard to adopt. More than that, VPNs created structural security problems that were resulting in massive security breaches and urgent security advisories from the NSA.
Every company we talked to wanted to move off their VPN and adopt a “zero trust” model for securing remote access, but they couldn’t find a solution on the market that made the complexity of switching worth the pain. We decided to build Twingate to fix this. Our goal is to help millions of companies around the world finally eliminate the headache (and security issues) with VPNs and move to a zero trust access model.
How is Twingate different from the competition?
Twingate is the first zero trust access solution with the ease of use and deployment you expect from a modern technology product. Twingate is designed to be painless to deploy and works out-of-the-box for any environment, whether in the cloud, on-prem, or both. End users get a fast, seamless experience that doesn’t get in the way of their work, and IT teams significantly reduce the overhead of managing and scaling remote access. More importantly, Twingate is “secure by design” and immediately reduces VPN-borne security threats and public attack surfaces.
We created Twingate because we felt nearly every other product on the market assumes that security and usability are tradeoffs. We think that is a false choice, and we architected Twingate to be secure and easy to use. Underlying this are a number of technical innovations our team has built to bring a full networking stack that runs on your device. This allows Twingate to automatically segregate and optimally route traffic before it leaves your device and for any application. This means no more choppy or dropped Zoom calls and fast access to the tools your employees need to get their work done.
In comparison, a majority of the products currently available are reliant on traditional VPN technology and structures. This results in significant restrictions on performance and increases deployment intricacy, as the issues with VPNs (performance, usability, security) are foundational. We are of the opinion that to effectively resolve these "VPN Problems," it's necessary to begin from scratch and design for the demands of the contemporary world.
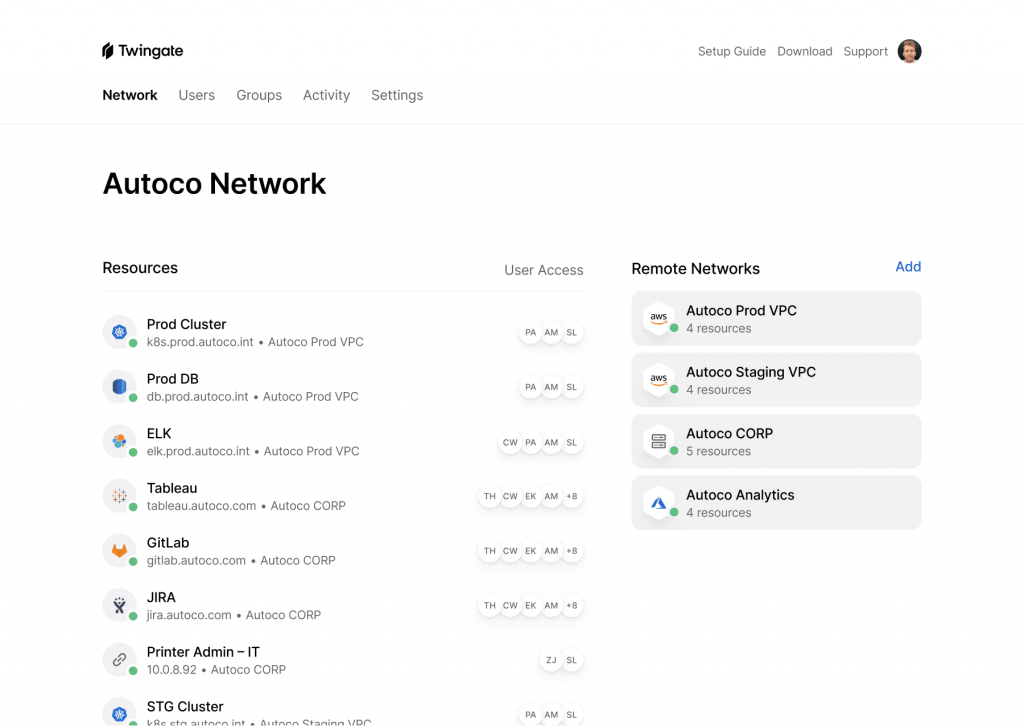
Here's a quick view of the Twingate dashboard
What are the most common use cases for Twingate?
One of key principles behind Twingate is to make a product that is not only simple to use, but powerful and flexible to serve diverse use cases. We’ve been excited to see our users utilize Twingate for a wide range of use cases in a company setting. These include:
- Managing access for contractors and vendors to company apps - access controls can be configured for the whole enterprise via a single admin console
- Cloaking or replacing Bastion servers for secure access to private servers - Twingate allows remote access to private servers without publicly exposing any network entry points like a Bastion server does
- Protecting legacy applications with multi-factor authentication and allowing identity providers to be used with applications that don’t natively support them
- Enabling IP based restrictions (i.e. IP whitelisting) for public SaaS apps without the need for VPN
- Easily accessing multi-cloud or complex environments with a single interface - unlike a VPN, users don’t need to manually select between different gateways to find the resource they need
- ...and more
We have customers with both technical and business users. Technical users like engineering and DevOps teams use Twingate to easily manage and secure access to infrastructure that might be spread over multiple cloud providers like AWS, GCP, and Azure. IT and business users have deployed Twingate to add more protections for sensitive internal applications like admin interfaces and financial software, and improve the connectivity performance for remote workers.
How has the COVID-19 pandemic affected your business?
When we started Twingate, we always believed that with the advent of cloud and mobile technologies, work was going to inevitably be more distributed and global. With the COVID-19 pandemic forcing many of the world’s workforces to move to a fully remote work model, those trends just got pulled forward. In other words, the “Future of Work” arrived early.
Since our launch, we’ve been blown away by the feedback we’ve received and have had the privilege of working with customers from around the world. The move to remote work only intensified the usability, performance, and security challenges with VPNs. We see many companies aggressively accelerating their plans to migrate away from VPNs.
How do you envision the future of this evolving industry?
While we are living in unprecedented times, the underlying trends driving our industry have been in the works for over a decade. It’s clear that every company will have to be re-wired for a world in which work is increasingly distributed and global. Outdated technology like VPNs and the legacy perimeter-based security paradigms will be replaced with modern products and technologies that are natively designed for a distributed world. This means that nearly every network and security product that today sits centrally in a company’s physical office or datacenter (firewalls, NACs, VPNs, etc.) will be reimagined and replaced with new alternatives. We’re excited to partner with our customers to bring these new products and experiences to life.
What’s ahead for Twingate?
Our focus with Twingate is to make the promise of “zero trust” a reality. Zero trust concepts have been around for over a decade and referenced by industry analysts like Gartner and Forrester for years. However, despite the advantages of the zero trust model, it has largely been out of reach for most companies due to the complexities of migrating to that model.
The Twingate team is hard at work crafting a product that can help companies get on a real, achievable path to zero trust. This starts with a product that is simple to deploy and easy to use for employees, all the while dramatically upleveling the security posture of an organization. We’re hard at work extending our platform and excited to bring “zero trust” to life for our customers.




Please, comment on how to improve this article. Your feedback matters!