UK Age Verification Law: Online Safety Act Privacy Guide 2026
- What Is the New UK Age Verification Law? Online Safety Act Explained
- What Are the Risks of the New UK Age Verification Laws?
- How UK Age Verification Methods Work: Which Is the Most Private?
- How To Stay Safe While Verifying Your Age Online
- Online Safety Act Timeline: When Will The Age Verification Law Come Into Effect?
- Which Websites Will Need To Verify Your Age?
- Public Response to the New Age Verification Law
- How Have Online Platforms Responded to the New Age Verification Law?
- FAQs on the UK Age Verification Law
- Conclusion
The UK's new age verification requirements take effect July 25th, 2025, fundamentally changing how you access online content. Under the Online Safety Act, platforms must verify users' ages before allowing access to adult content and other potentially harmful material. This affects everything from social media and gaming sites to adult content platforms.
While designed to protect children, critics warn that mandatory ID checks and facial scans pose serious privacy risks, with millions of adults forced to share sensitive data with third-party services. However, different approaches require different levels of personal data sharing, from credit card details to facial scans and government ID uploads.
What Is the New UK Age Verification Law? Online Safety Act Explained
The UK’s Online Safety Act 2023 is a new law that requires platforms to implement "highly effective" and “robust” age verification systems by July 25th, 2025. The law’s goal is to protect children from easily accessing harmful online content. It will be enforced by Ofcom, the UK’s communications regulator.
Why does the UK have a new age verification law? The legislation targets alarming statistics about children's exposure to inappropriate content. Research shows that 8% of children aged 8–14 in the UK visit online pornography sites, including 3% of 8–9-year-olds1 (Ofcom, 2025). At the same time, there are 14 million adult porn consumers in the UK, highlighting the challenge of protecting kids while preserving adults’ rights.
As such, the law primarily targets websites dedicated to pornographic and adult content. However, virtually any website or online service that stands the slightest chance of hosting harmful content falls under its purview. This includes sites with user-uploaded content, such as social media platforms, video hosting sites, forums, gaming services, and more.
While Ofcom has some discretion when it comes to the interpretation, these are the types of content that will be restricted under this law:
- Pornography and adult sexual content
- Violent or extreme content, such as gore, torture, and graphic violence
- Self-harm, suicide, and eating disorder content (so-called pro-ana/mia forums or those that encourage forms of self-harm)
- Content promoting illegal drugs or substance abuse
- Content promoting dangerous challenges/stunts or risky behaviour
- Content depicting or glorifying criminal activity (theft, terrorism, or organized crime)
- Hate and abusive content (including extremist propaganda targeting minors)
The enforcement mechanisms carry significant weight. Non-compliant platforms face fines up to £18 million or 10% of their global annual revenue, whichever is higher. In extreme cases, Ofcom can request court orders to block sites entirely through UK internet service providers (ISPs).
Additional safeguards protect adult access rights. The law requires that verification systems maintain user privacy and comply with UK data protection regulations. The Information Commissioner's Office (ICO) oversees privacy compliance, ensuring platforms can't use age verification as a pretext for excessive data collection.
What Are the Risks of the New UK Age Verification Laws?
Of course, age verification measures are already common practice when accessing adult content. The difference is that they typically rely on self-declaration, without requiring any actual proof. While revealing your age isn’t usually dangerous on its own, the new law requires proof — such as a government ID — which dramatically increases the personal data you share.
That data, when stored or processed by age verification providers, becomes a potential gold mine for cybercriminals, hackers, or even snooping governments.
If your personally identifiable information (PII) falls into the wrong hands, it can be used to:
- Impersonate you online by opening accounts or accessing services in your name.
- Construct targeted phishing or spear-phishing attacks — using your real details to appear credible.
- Conduct financial fraud by using credit cards, applying for loans, or making purchases in your name.
- Commit identity theft by using it to steal even more sensitive data.
- Extort or blackmail you by leveraging your private habits.
- Continue to track or surveil your online behavior.
Even “less severe” data points — like date of birth, address, or a photo — can become powerful building blocks for broader identity-based attacks.
How UK Age Verification Methods Work: Which Is the Most Private?
A variety of age verification methods already exist with differing privacy implications, levels of accuracy, and feasibility. While the list isn’t exhaustive, the 7 methods explained below have been approved by Ofcom itself as “highly effective age assurance” techniques according to the Online Safety Act. So, online services will most likely offer one or more of these services to verify UK users’ age.
Understanding each method will help you make an informed decision about how to best protect your personal data while accessing the services you need. Here's how the 7 approved methods work and their respective privacy risks:
1. Email-Based Age Estimation
This method asks for your email address and uses it to identify associated account history to estimate your age. Services like Verifymy examine factors like account creation date, related financial accounts, and digital footprint patterns to determine if you're likely over 18.
Will age verification data be permanently stored? Data retention depends on the specific service’s privacy policy, but Verifymy says that it will only keep your information for up to 28 days2. Verification services only get a “yes/no” answer from third parties that you’re over the age of 18 — no other information is shared. If the data is stolen, only your email and whether you’re over or below 18 will be revealed.
Because it asks only for your email, this is arguably the most private option, but its accuracy is questionable. It depends on having a solid online profile with highly trusted institutions. You’ll also need to accept the fact that the verification service will poll your age status across numerous online sources.
2. Mobile Network Operator Checks
This method uses your mobile phone number to check your contract and verify your age. Similar to the email verification method, your mobile contract provider can confirm your over-18 status without sharing any other personal details with the verification service.
The process typically involves sending an SMS or using your mobile data connection for verification. Verification systems like Yoti can both look at who pays the bill as well as whether the specific phone number user is potentially an underage user on a family package.
Again, this method involves minimal data sharing. However, you may prefer to provide a less intrusive personal contact, like your email. Another issue is that pay-as-you-go mobile users may not be able to use this method, as you typically don’t need to verify your age like on a contract.
From a cybersecurity perspective, two concerns are multi-factor authentication and “Smishing” (SMS phishing). Many online services, including banks, use mobile numbers for 2FA, so an exposed number could be used to gain access to your accounts. SMS-based attacks are also increasingly common, accounting for up to 39% of mobile threats in 20243.
3. Open Banking Verification
When you choose this method, you're redirected to your bank's secure login system to confirm your age. You’ll provide your login credentials, and the bank confirms you're over 18 to the verification service without sharing any additional info. Verification firms like OneID provide this approach.
The online platform will only receive a yes/no confirmation of your age status, no account balances, transaction history, or other financial information. However, there are still valid concerns about sharing between three parties: your bank, the verification service, and the requesting platform.
There’s also a small but valid cybersecurity concern: while Open Banking uses encrypted APIs designed to prevent tampering, poorly implemented integrations could be vulnerable to spoofing or man-in-the-middle attacks. A compromised third-party app could theoretically intercept login tokens or redirect users to spoofed pages mimicking bank logins.
That said, no major Open Banking age-verification breaches have been reported to date, and banks in the UK must comply with strict PSD2 security standards.
4. Digital Identity Services
Digital identity platforms like Yoti store encrypted identity information that you can selectively opt to share with specific services. You only have to create a digital identity wallet once by uploading identification documents, and then you can control what information gets shared with different services.
The main advantage lies in that it gives you granular control over when and with whom your data is shared and that you don’t have to keep repeating the verification process on different platforms using different sets of documents. The only scary part is the initial document upload and trusting a new service.
As an extra precaution, your documents and information are often stored separately so that a single breach is unlikely to expose all your information in a way that’s clearly linked together. It would be like giving hackers some puzzle pieces without a reference image or clear way to put them together.
However, digital identity services aren’t 100% guaranteed to be safe. For example, in July 2024, the ID verification service AU10TIX was hit with a data breach, leading to the exposure of sensitive information of millions of users of popular platforms like TikTok, Uber, and X (Twitter)4.
5. Facial Age Estimation
AI-powered facial recognition analyzes your live selfie to estimate your age without requiring identity documents. The system checks that you're human, that only one person appears in the image, and that you're not holding up a photograph.
Most verification services using facial age estimation also employ anti-spoofing measures to prevent users from tricking the system with photos or videos. Some AI models are up to 95% accurate at placing user uploads within certain age groups (Research Gate, 2023)5.
Of course, the obvious issue is that they aren’t 100% accurate, with most modern solutions having an error margin of about 2.3 years. So, you would likely have to use a backup verification method via customer support if it fails repeatedly.
Another increasingly contentious issue is the storage of personal biometric data by third parties. This could be used to create deepfakes, commit fraud, or even track your activity across social platforms. However, many providers delete the original images immediately after processing.
Is it safe to store biometric data online? It can be, but it’s critically important that it’s stored temporarily, as it’s clearly become a target for hackers. The most prominent recent example is an Australian National leak that exposed the facial biometrics of about 1 million Australians6.
6. Credit Card Validation
In most countries, being an adult (over 18) is a requirement for being the primary holder of a credit card. And almost all banks keep records on the age of their account holders due to regulatory requirements as well.
When using your credit card to verify your age, the process typically involves validating your payment method with a mini-transaction that either charges nothing or is immediately reversed. This may also trigger a two-factor authentication check from your bank.
As long as you use a trusted financial service or payment method, this process should be safe. No credit card details or other info beyond the fact that you have an active account and are 18+ should get passed back to the site you’re trying to access.
However, scam sites could use the verification mandate to redirect you to fake payment pages. Even if a payment doesn’t get through immediately, your card details could be stolen by who knows who.
What’s the risk of payment age verification? So-called payment gateway breaches can expose full credit card numbers, names, expiration dates, and billing addresses, such as the SlimCD breach that exposed nearly 1.7 million customers’ credit card data in 20247.
7. Photo ID Matching
This is the most common approach most of us have had to perform when creating an online account with some government or financial services. You upload a selfie of your face while holding your government-issued ID, which is then confirmed by a human or AI-assisted reviewer. The service may also validate your ID’s authenticity by checking with the relevant government office.
Despite it being the most widely used option today, the privacy risks are significant. If anyone unauthorized were to access your uploaded files, they’d know what you look like and have virtually all your personally identifiable information — your full name, date of birth, address, and official photo.
This makes it an obvious, high-value target for cybercriminals and ransomware gangs. Being aware of the verification provider’s privacy and security policies is therefore essential.
Data storage varies by provider, but most retain ID images for several weeks. Persona, used by Reddit, stores verification photos for a maximum of 7 days before deletion. However, the verification status itself may be retained longer.
How To Stay Safe While Verifying Your Age Online
In an ideal world, we could rely on sites that require age verification to act in our best interests at all times. However, it’s important to take steps to protect your own privacy and ensure that you only entrust your data to reputable services to begin with. While compliance with UK law is mandatory and largely unavoidable, here are some things you can try:
- Choose verification methods with minimal data exposure. When there’s a choice, choose the method that you are most comfortable with and that requires the least PII. Email-based verification is generally the safest, while uploading government ID is the most intrusive.
- Use a trusted VPN when completing verification processes. A VPN masks your real IP address and location and encrypts all data during the upload and download process. This minimizes your digital footprint and the risk of data interception. It also makes it possible to safely access the non-UK version of sites, which don’t require verification.
- Research data retention policies. See which verification services are being used and look at their privacy/data retention policies. Services like Persona delete verification photos within 7 days, while others may retain data for months. Shorter retention periods reduce long-term privacy risks.
- Monitor your accounts for signs of data breaches. Set up alerts with services like Have I Been Pwned, Firefox Monitor, or Google Account Alerts to know immediately if your email or ID information appears in a leak.
- Use dummy email addresses for verification purposes. Create a separate email account for age verification to compartmentalize your digital identity and reduce cross-platform data correlation.
- Share the minimum info necessary during verification. Many platforms request optional information beyond age confirmation, like gender. Provide only the minimum required data to complete verification.
- Enable two-factor authentication. This makes it harder for unauthorized parties to access your accounts on platforms containing your verification status, even if they have some of your information.
- Regularly audit platforms with your verification data. Periodically review which services have your verification information and delete accounts you no longer use to minimize your exposure footprint.
- Request data removal. You can send a request to verification services to remove your verification data. However, this will likely be different for each service, so it’s best to check with them before you provide the information.
Online Safety Act Timeline: When Will The Age Verification Law Come Into Effect?
The UK’s Online Safety Act first received Royal Assent on 26 October 2023. Online platforms and services have thus had time to prepare for a phased rollout of guidance, enforcement, and compliance measures. The critical deadline for the implementation of its “robust” age verification practices is 25 July 2025.
At the time of writing, Ofcom has already begun assessing platforms, issuing guidance, and launching enforcement ahead of full implementation.
Here’s a timeline of the key events so that you can prepare for any changes that might come to your favorite websites or online services:
- 26 Oct 2023: Online Safety Act receives Royal Assent, repealing earlier Digital Economy Act mandates.
- Dec 2024: Ofcom publishes Illegal Harms Codes of Practice, which outlines its risk assessment guidance and enforcement protocols.
- 16 Jan 2025: Ofcom issues its final age assurance and children’s access assessment guidance. Publishers of pornographic content are forced to implement certain age checks by January 17.
- 25 Jul 2025: All in-scope services must have fully operational age verification systems to prevent child access to pornography and harmful content. Sites may face enforcement actions immediately if they are found to be non-compliant after this date.
Ofcom has made it clear that they will focus their efforts on large services first, like OnlyFans and Pornhub. However, all online services that are available to users in the UK must become compliant sooner rather than later. The regulators expect full compliance by 2026.
Which Websites Will Need To Verify Your Age?
The sweeping scope of the OSA means that virtually any website that may host “harmful” content for minors will have to comply with its guidelines. With a very broad definition of “harmful,” it means that it won’t only impact sites dedicated to adult content or porn, but almost any website where the public can upload content without immediate moderation.
For example, under Part 3 of its official guidance, Ofcom also defines “user-to-user” and “search services” as potentially problematic. In fact, Ofcom has identified 60+ “high-risk” services and said that it’s received commitments from over 1,300 other sites to implement age verification measures8.
Although it’s impossible to create an exhaustive list, here are some of the most popular sites that are or will likely be regulated under this new law:
Social media platforms:
- Facebook and Instagram
- TikTok
- X/Twitter
- Discord
Gaming platforms with user-generated content:
- Steam (community and forum features)
- PlayStation Network and Xbox Live
- Roblox and Minecraft
- Fortnite Creator Mode
- VRChat
- Twitch
Search engines and content aggregators:
- Google Search (SafeSearch bypass for explicit results)
- Bing, Yahoo, DuckDuckGo, and others
- YouTube and most other video platforms
- News aggregators with violent or disturbing content
Adult content platforms:
- Porn streaming sites, like Pornhub, Xvideos, XHamster, YouPorn, RedTube
- Live cam and interactive services, like Chaturbate, Stripchat, Cam4
- Adult dating services, like AdultFriendFinder
- Adult content subscription sites, like OnlyFans and FanCentro
Messaging and communication apps with discovery features:
- Telegram
- Signal
Public Response to the New Age Verification Law
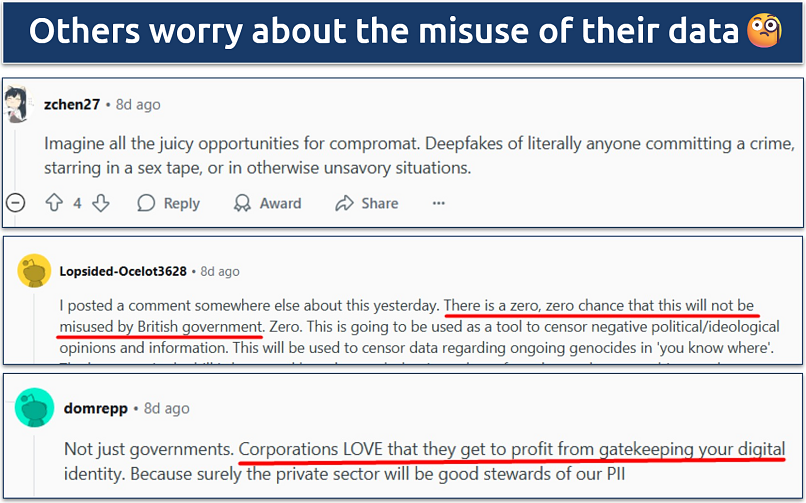
The public, privacy advocates, and cybersecurity professionals have all expressed valid concerns about its implementation. Most revolve around doubts about the efficacy of the measures to prevent underage access to content, assurances regarding secure data storage and handling practices, and the intensifying policing of internet activity by the state.
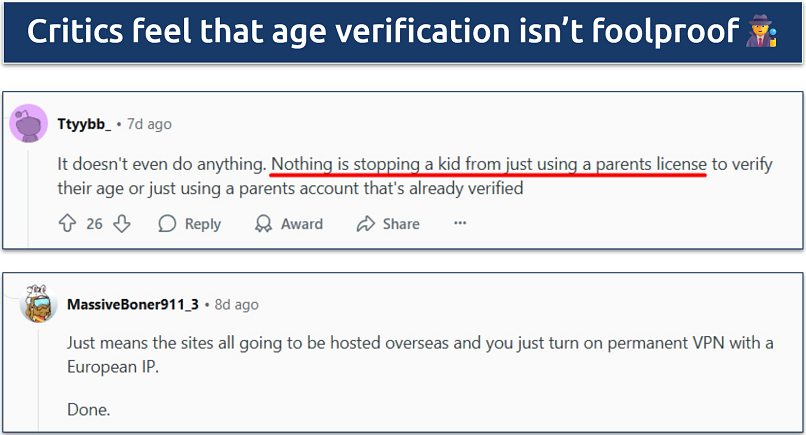 Some feel that teenagers will always find a workaround if they're motivated
Some feel that teenagers will always find a workaround if they're motivated
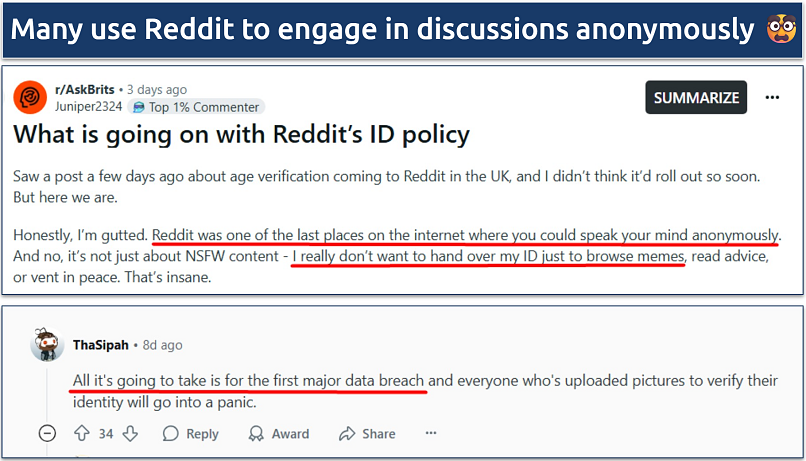
What do Redditors have to say about age verification? On Reddit, one of the sites that has already implemented age checks, Brits are actively expressing their concerns over how the new guidelines will impact their privacy:
These concerns are shared by the cybersecurity community. In speaking to the BBC, Chelsea Jarvie cautioned against "normalizing mass identification online.” The Age Verification Association itself states that “the only non-hackable database is no database at all.” Considering the track record of the last few years, it’s likely only a matter of time until there’s a major data breach involving this new age verification data.
However, the National Society for the Prevention of Cruelty to Children (NSPCC) highlights the new law’s importance to protecting children online: “It is time tech companies take responsibility for ensuring children have safe, age‑appropriate experiences online and we welcome the progress that Ofcom are making in this space.”
How Have Online Platforms Responded to the New Age Verification Law?
Online platforms have responded in very different ways to the new rules, from immediate compliance to threatening a complete withdrawal from the UK market. Some argue that the rules are too complex and costly for smaller businesses to implement, while others raise the same privacy and duty of care concerns as the public.
Reddit has embraced third-party Photo ID verification through Persona, offering users two verification methods: selfie submission or government ID upload. For now, Bluesky has implemented multiple verification options, but they are still voluntary and under development.
In response, Wikipedia mounted legal opposition, arguing that age verification requirements would compromise user privacy and potentially violate human rights. The video-sharing site BitChute announced a complete withdrawal, displaying disclaimers to UK users explaining they cannot access the platform due to the verification requirements.
 It states that the new rules are "hostile" to its "values and principles"
It states that the new rules are "hostile" to its "values and principles"
As high-priority targets of this bill, many porn sites, like Pornhub, Stripchat, and YouPorn, have already confirmed their compliance with Ofcom in June of 2025.
However, many smaller websites are considering geoblocking UK traffic entirely. Implementation costs for comprehensive age verification systems can exceed smaller sites' entire operating budgets. Others may simply move their servers overseas to remove themselves from the UK government’s jurisdiction.
FAQs on the UK Age Verification Law
What is the safest age verification method?
Email-based verification typically offers the lowest privacy risk, requiring minimal personal information and short data retention periods. It doesn’t require uploading any sensitive documents, either. Avoid photo ID verification when possible, as it requires sharing comprehensive identity information that can be used for identity theft.
Can I avoid having my age verified online in the UK?
Complete avoidance isn't possible if you want to access affected UK platforms after July 25th, 2025. However, you can minimize verification frequency or risk by choosing platforms with longer verification periods and avoiding services that require repeated verification. Technically, it’s also possible to use a VPN or similar tool to access the international versions of these sites without verification.
Is it illegal to use a VPN to avoid UK age verification?
Ofcom’s enforcement targets online services, not individual users — there’s no legal provision to punish people for using VPNs. VPNs are legitimate privacy tools in the UK, widely used for security and data protection. However, platforms may still detect VPN usage and block access until verification is completed in order to comply with the Online Safety Act.
Can websites see my personal information during verification?
It depends, but generally, no. Most third-party verification services only pass an “age confirmed” status to websites, not your full details. Whether you use credit card checks, open banking, or email, the platform usually won’t see financial or personal data. Photo ID verification exposes the most information to the verification provider, but reputable services claim they only share anonymized confirmation, not full identity documents, with the requesting site.
How long is verification data stored?
It varies from just a few days to months. Persona (Reddit) deletes photos within 7 days, while Verifymy keeps email data up to 28 days. Some digital ID services may store encrypted data indefinitely, and facial recognition tools often delete images after processing. Always check retention policies — shorter storage means less chance of getting caught up in a data breach.
Can I request online services to delete my verification data?
Yes — under UK GDPR, you can request deletion of personal data, though services may retain verification status for compliance. Contact providers like Persona, Yoti, or Verifymy directly to request deletion. UK-based data deletion services such as Rightly or DeleteMe UK can help manage requests across multiple platforms. Deleting verification data may revoke platform access, so check each service’s policy first.
Conclusion
For the first time, under the UK’s new age verification laws, millions of adults must weigh the cost of sharing personal data against their right to access content freely. With many sites already implementing these measures and more on the way, consumers must educate themselves about different verification methods to manage risk and make informed decisions.
Users should favor services that delete data quickly and share only anonymized confirmation. They also have to make the choice regarding which platforms are worth using at the cost of increasing their online footprint. Finally, online services must be held accountable and scrutinized to maintain secure data handling practices, with data breaches becoming increasingly commonplace.
References
- https://www.ofcom.org.uk/media-use-and-attitudes/media-habits-children/childrens-passive-online-measurement/
- https://verifymy.io/age-verification-and-estimation/age-assurance-privacy-policy/
- https://keepnetlabs.com/blog/smishing-statistics-the-latest-trends-and-numbers-in-sms-phishing/
- https://cyberinsider.com/breach-at-id-verification-service-highlights-privacy-dangers/
- https://www.researchgate.net/publication/375059460_Age_Estimation_from_Facial_Images_Using_Custom_Convolutional_Neural_Network_CNN/
- https://www.biometricupdate.com/202405/reported-australian-biometric-data-breach-prompts-arrest-and-hysteria/
- https://www.malwarebytes.com/blog/news/2024/09/payment-provider-data-breach-exposes-credit-card-information-of-1-7-million-customers/
- https://www.ofcom.org.uk/online-safety/illegal-and-harmful-content/online-safety-industry-bulletins/online-safety-industry-bulletin-May-25/



Please, comment on how to improve this article. Your feedback matters!