How Bitcoin Works: The Beginner’s Guide to Bitcoin That Won't Leave You Frustrated
- How Bitcoin Came to Be
- How Bitcoin Works at the Transaction Level
- Beginner’s Guide to Using Bitcoin
- How Bitcoin Works with PayPal
- Credit Card Companies Drop Pornhub
- How to Make Money from Cryptocurrency
- Understanding Bitcoin’s Legal Status
- The Dark Side of Bitcoin
- The Biggest Online Scam In History
- Other Implementations of Blockchain beyond Bitcoin Basics
Most people do not understand the concept and process of Bitcoin. Our extensive guide dives into the nitty-gritty in an easy-to-understand manner that won't leave you confused or frustrated. Share
Have you heard of Bitcoin?
It’s almost a rhetorical question in today’s market. Bitcoin continues to gain mainstream popularity and is discussed constantly in the media. However, that doesn’t mean everyone understands what it is.
In fact, most people don’t. The nature of the technology on which Bitcoin operates — the blockchain — can be too intimidating.
This Bitcoin guide will explain the nitty-gritty concepts relating to blockchain and how Bitcoin works in an easy-to-understand manner. It’s a long read, but we’ve broken it down into digestible sections!
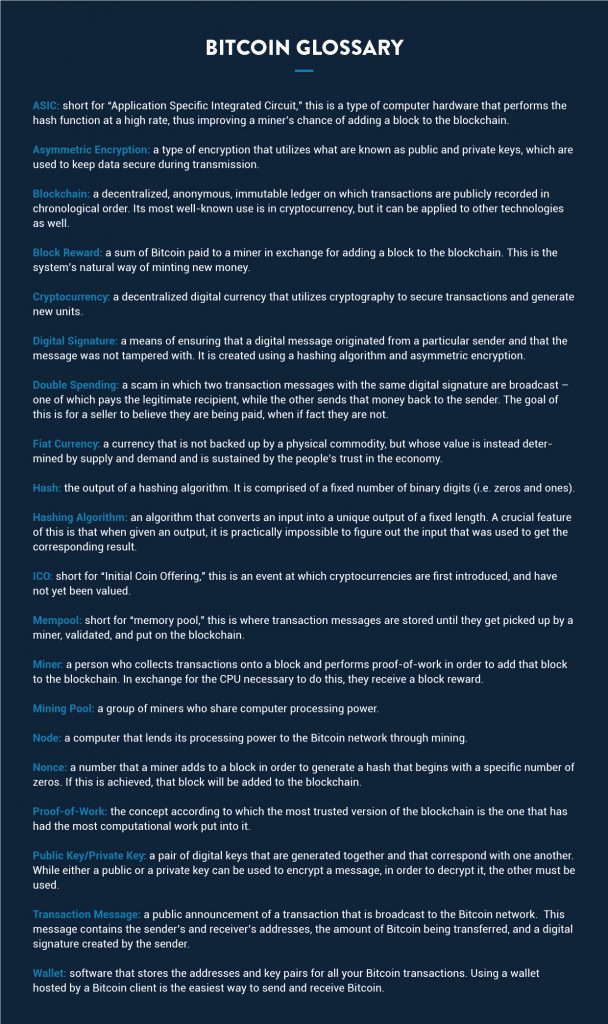
The concept of Bitcoin and blockchain includes a lot of specific terms. For quick definitions, you can reference this glossary:
1. How Bitcoin Came to Be
1. Who Invented Bitcoin?
Bitcoin was invented by an anonymous person, or possibly a group of people, under the pseudonym Satoshi Nakamoto. In October 2008, Nakamoto published a paper on blockchain which circulated throughout the cryptographic community, laying out the foundational principles of how Bitcoin works.
In 2009, Nakamoto completed the Bitcoin software’s code and invited other people from the open-source community to contribute.
He mined the first block himself on January 3, 2009. As per the public records of his Bitcoin addresses, Nakamoto currently owns Bitcoin worth over $40 billion, making him one of the wealthiest people in the world.
No one knows who Satoshi Nakamoto is, though many journalists have investigated. People have speculated that he may be a number of students or celebrities, but nothing has yet been proven. While it sounds ridiculous, some have even claimed that Satoshi Nakamoto is a time traveler from the future.
What isn’t up for debate is that by inventing Bitcoin, Satoshi Nakamoto revolutionized the concept of money, solving many of the problems that occur with traditional currency.
2. The Problem with Traditional Currency
We all know how to withdraw cash from an ATM and buy a pack of gum using that cash. But how many of us actually know why these transactions work? Why does everyone accept that our plastic credit cards and paper money have any value? For anyone interested in modern financial mechanisms, understanding how Bitcoin works could offer a fresh perspective.
Traditionally, currency was bound to some physical commodity, like gold. So, for instance, in the year 1900 gold was worth $20.67 per ounce. That meant that the U.S. government was only allowed to mint $20.67 worth of currency if it had an ounce of gold in the reserves to back it up. It also meant that any holder of U.S. currency could go to the government and exchange it for its equivalent worth in gold.
In the US, this system ended in 1971, when the American dollar became a fiat currency — meaning it has no intrinsic value. Instead, the currency’s value is determined by supply and demand and is sustained by trust in the economy. In recent decades, all the world’s major currencies have been converted to the fiat system.
While a fiat currency allows the government to promote economic stability through the control aspects of the economy like credit supply, liquidity, and interest rates, it could also lead to the government printing more money than it should — causing hyperinflation.
Another problem with fiat currencies is that the system is centralized and requires a lot of regulation. In other words, every transaction needs to be facilitated by a financial body — e.g., a credit card company or a bank — to make sure it’s carried out correctly. That’s why when you go to an ATM that doesn’t belong to your bank, or when you transfer money from your account to a friend’s, you often pay a fee.
You can read more about decentralized currency in this article.
3. How Bitcoin Works to Solve Centralized Currency Problems
Bitcoin aims to solve the problems associated with fiat currencies.
Using Bitcoin, you can transfer funds to anyone within seconds and with minimal transaction fees. This is possible because the Bitcoin system is decentralized.
Understanding Bitcoin involves recognizing that it operates as a distributed, decentralized ledger on which all financial transactions are recorded. This ledger is implemented through a technology known as the blockchain. Each block on the blockchain represents a series of transactions. Once enough transactions have been carried out, the block is completed and cannot be altered.
Using this public ledger, Bitcoin aims to solve a number of problems:
- Decentralization: The most crucial feature of how Bitcoin works is that it’s decentralized, meaning a single authority or person can’t control it. The code for the software is open-sourced and maintained by volunteers. The system is run by an open network of computers spread around the world. Whoever wants to participate can pitch in and start contributing.
- Anonymity: Unlike traditional financial systems, Bitcoin software doesn’t need to know your identity. Your identity is your Bitcoin address. Your ability to carry out financial transactions depends only on whether you have sufficient funds in your account.
- Immutability: The Bitcoin network and the underlying blockchain are immutable. That means, once a transaction is done, it can’t be reversed. This immutability ensures that a person to whom money was sent receives it. One might think that this would be problematic for e-commerce, where the buyer needs to be protected. However, even with Bitcoin, this can be achieved with escrow accounts.
- Limited supply: Traditional fiat currencies have unlimited supplies, since reserve banks can mint as much money as they want. However, the amount of Bitcoin that can ever be produced is capped at 21 million. The value of the currency is determined by demand and the perceived benefit that people see in it.
Now, let’s take a deep dive to understand how Bitcoin works. To do this, we will look at the problems associated with building a decentralized currency system and see how the Bitcoin system solves them.
2. How Bitcoin Works at the Transaction Level
1. Bitcoin Authenticates the User with a Digital Signature
When you go to a bank to perform a transaction, you have to authenticate yourself. You may do this with your driver’s license, social security card, or handwritten signature. In any case, these mechanisms are in place so that only you can withdraw or transfer money that you own. If someone tried to impersonate you, they would be caught (hopefully).
In contrast, Bitcoin uses a public ledger on which everyone records their transactions. But what’s to keep people from adding fraudulent transactions that benefit them? For instance, Bob could simply add to the ledger that Alice sent him money.
To prevent this, Bitcoin transactions are broadcast to the network along with a digital signature.
A digital signature ensures two things:
- The designated sender has sent the message.
- The message has not been tampered with.
This digital signature is created using a hashing algorithm and asymmetric encryption.
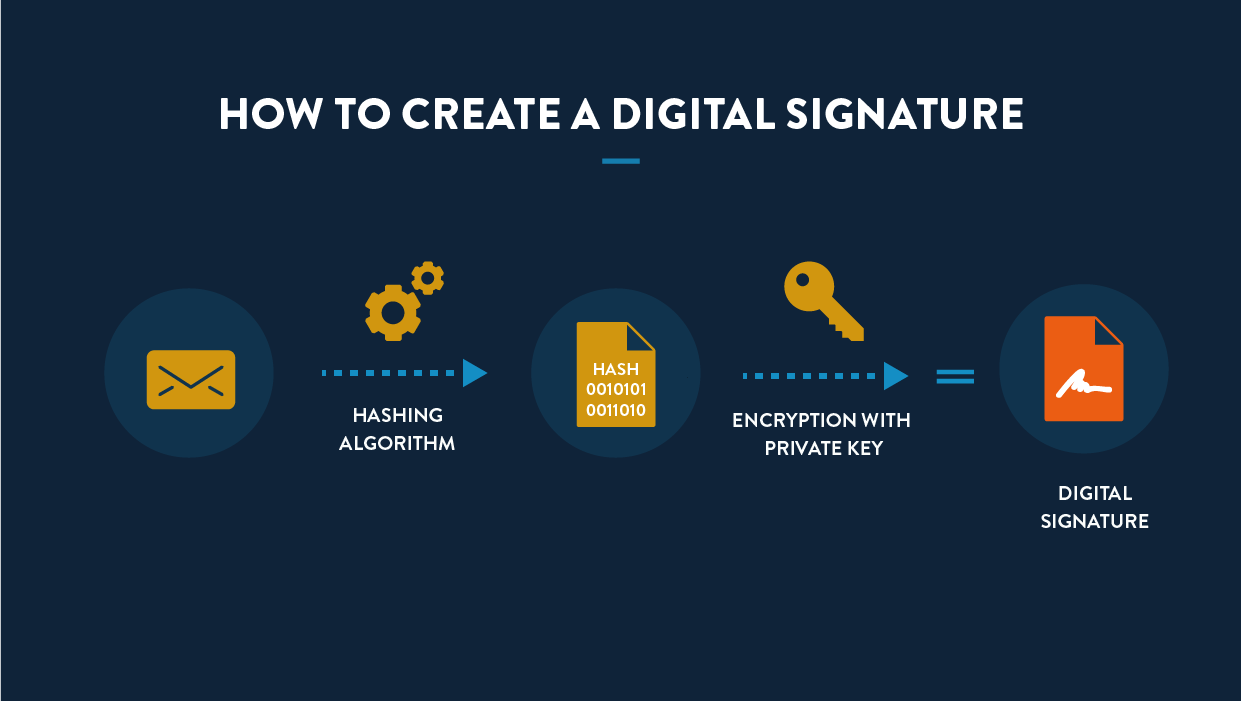
Hashing, an important component of how Bitcoin works, uses an algorithm that irreversibly converts an input into a unique output of a fixed length. Bitcoin’s hashing algorithm is SHA256, which means the output — also known as a hash or digest — has 256 binary digits (i.e., zeros and ones).
You can think of hashing as a mathematical technique by which you can convert an input value into an output value very quickly. However, when given an output value, figuring out the input value used to get the corresponding result is practically impossible.
One way to conceptualize this is by making a cake. The input is flour, sugar, eggs, etc., and the output is the finished cake. The algorithm is the oven that turns the raw ingredients into the finished product. Once you have the cake, you can’t turn it back into the raw ingredients. It’s also impossible to determine exactly what the raw ingredients were and how much of each was used.
To create a digital signature, the message broadcast to the network first needs to be hashed. Then, the hash needs to be encrypted.
As mentioned earlier in this Bitcoin guide, the type of encryption Bitcoin employs is known as asymmetric encryption — a form of encryption that uses what are known as public and private keys.
Asymmetric encryption works because each person has a public and private key that correspond with one another. While you can use the public and private keys separately to encrypt a message, to decrypt it, you need both. In other words, if you encrypt with a public key, it must be decrypted with a private key and vice versa.
The private key belongs to one person, and no one else has access to it. In contrast, you can give anyone your public key. Say Alice wants to send Bob a private message. Alice encrypts the message using Bob’s public key that he gave her. Bob is the only one with his private key, so he’s the only one who can decrypt it. If Bob wants to send Alice a private message, he encrypts it using her public key, and only she can decrypt it.
With Bitcoin, the aim isn’t to send a private message — remember, the ledger is public. Nevertheless, asymmetric encryption ensures that the message was actually sent by the person you thought it was and that it hadn’t been tampered with.
Let’s say Alice wants to send Bob one Bitcoin. So she broadcasts two things to the network:
- A message (containing the details of the transaction). The transaction is unencrypted and contains the link to previous transactions. It also contains input and output values, which help determine whether there are enough funds for the transaction to be considered valid.
- A digital signature (i.e., the hashed message that she’s encrypted with her private key).
Bob then authenticates the transaction by:
- Applying the hash algorithm to the message, giving him Hash A.
- Decrypting the digital signature Alice created using Alice’s public key. This gives him Hash B.
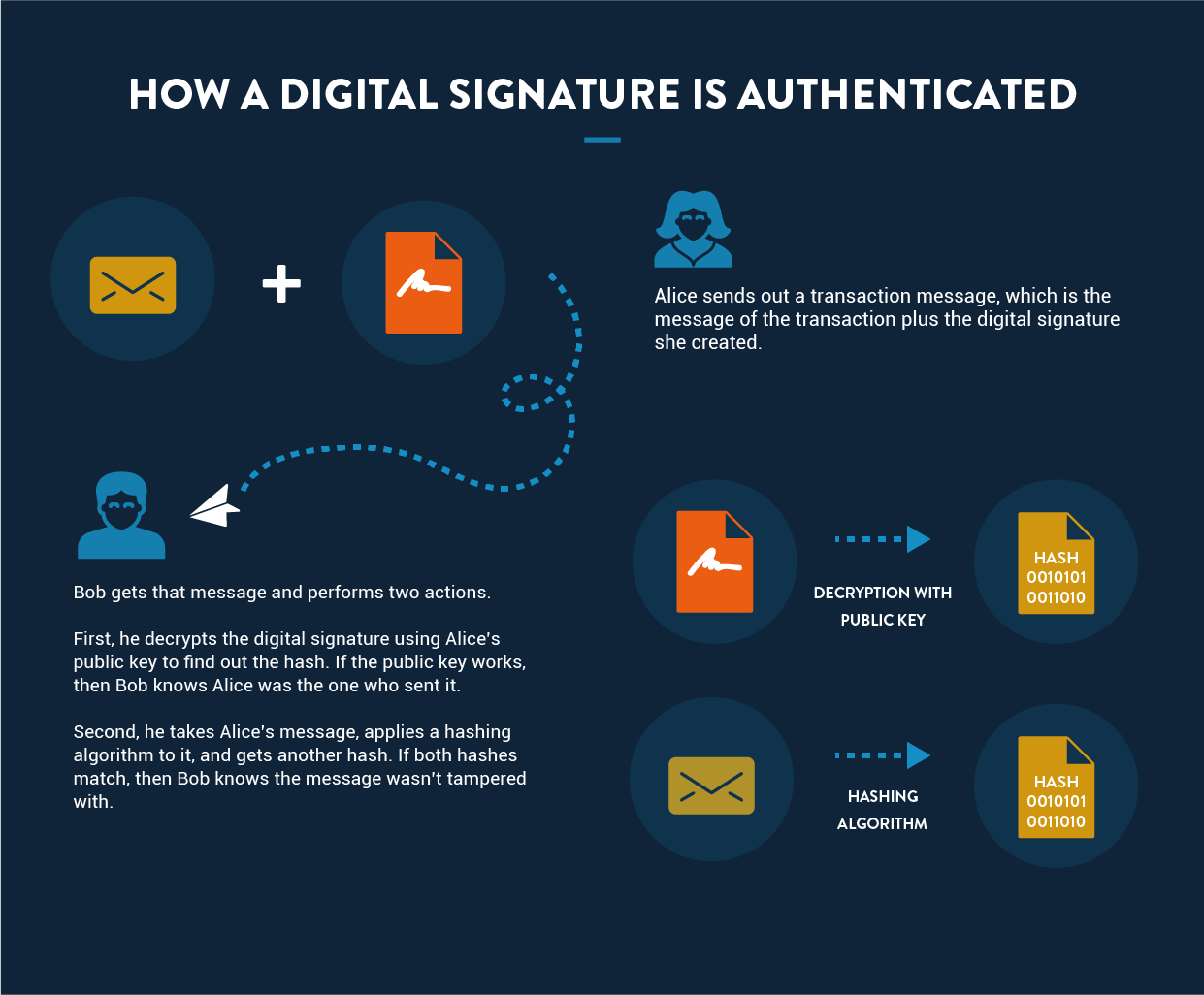
Since both hashes were derived from the same message, they should be the same. If they are, it proves that nobody tampered with the message. And since Bob was able to decrypt the hashed message using Alice’s public key, and Alice is the only one with access to her private key, it also ensures that the message came from her.
2. How Bitcoin Stores Information
Another potential problem with a decentralized network like Bitcoin is storage. To understand how Bitcoin works, you need to consider how this network manages and stores data.
Where can we store everyone’s balances and their transaction histories?
In conventional centralized systems, dedicated servers are owned and maintained by financial institutions, such as banks, that store all the data. Although this data is supposed to be highly secure and confidential, hackers have gained access to this information on numerous occasions in recent years.
In the Bitcoin system, there is no single authority that controls the data. Instead, all the information is public.
Bitcoin does this by employing a peer-to-peer distributed network. The data is distributed across thousands of participating computers connected via the internet, known as nodes. Each node has access to the ledger (or blockchain), which gets updated every time a new transaction (or block) gets added.
These transactions are carried out according to a set of rules, known as the Bitcoin protocol.
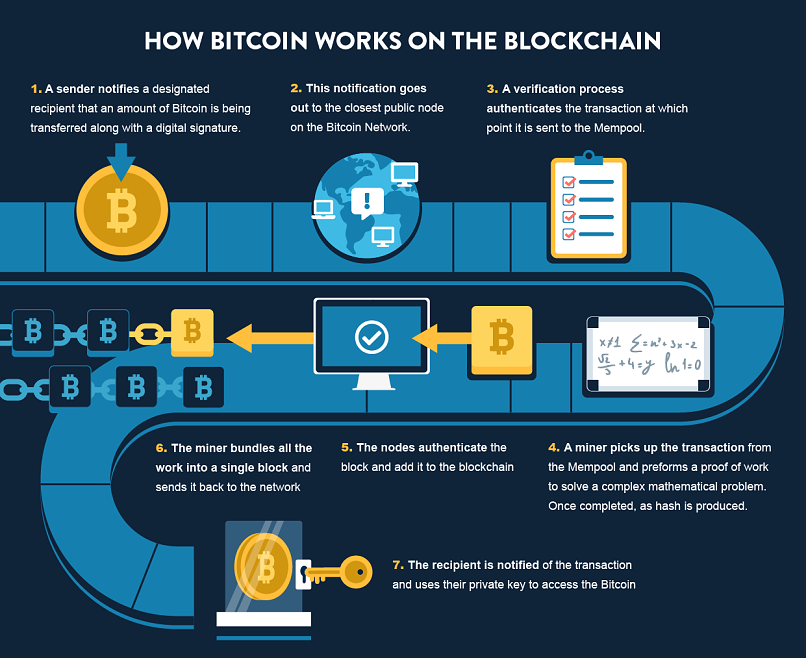
3. How to Carry Out Bitcoin Transactions
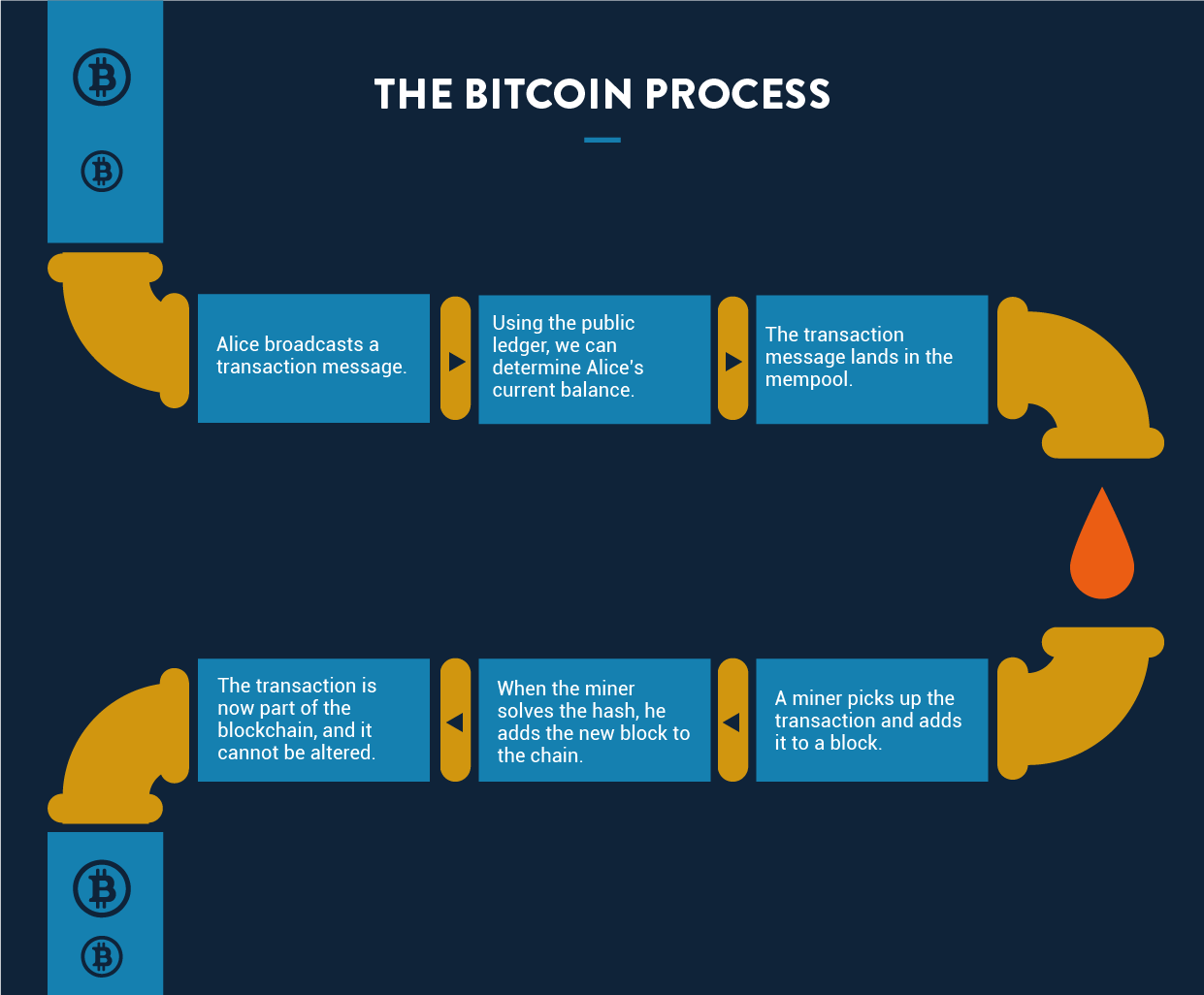
Suppose Alice wants to send one Bitcoin to Bob.
First, we need to verify that Alice owns at least one Bitcoin. There is no single entry in the blockchain network where you can see how much currency a person holds. Instead, the balance is derived by calculating all previous transactions, known as the transaction chain.
When you first download the Bitcoin software, you receive a complete copy of the transaction chain (which is why downloading can take up to 24 hours). Once you have the transaction chain, determining Alice’s current balance is easy.
Once it’s verified that Alice owns enough Bitcoin to make the transaction, the next step is to broadcast the transaction message. This message contains the sender’s and receiver’s addresses, the amount being transferred, and the sender’s digital signature. When broadcast publicly, any node in the network can relay the message and pick it up for execution.
Before it’s executed, the transaction is added to a pool of unconfirmed transactions before it is executed, known as a mempool (short for ‘memory pool’). From there, it’s picked up by miners.
Miners are basically the mediators who validate transactions (Bitcoin mining will be explained in more detail below). Once the transaction is validated, the miner adds it to the newest block. A block has a fixed size, so a new block must be created after a certain number of transactions. The current block is linked to the previous block, forming a blockchain.
But who decides which transactions should next be added to the latest block?
Typically, miners are free to pick or leave whichever transactions they wish. To incentivize them to choose yours, you can pay them a small part of the transaction. This, however, should not be viewed as necessary since miners have another incentive to make blocks, known as a block reward.
Whenever a new block is added to the chain, the miner who submits it is rewarded with new Bitcoin. The exact amount of reward has changed over time and decreases as the network grows. Block rewards are the system’s natural way of minting new money.
When the transaction becomes a part of the blockchain, it is officially executed.
4. How Blocks are Validated
Above, we discussed how newly verified transactions are added to a block, which is then added to the existing blockchain. But how do we know that the new transactions are legitimate?
Miners must perform a proof-of-work.
Essentially, proof-of-work is a system in which the most trusted version of the ledger is the one that’s had the most computational work put into it. Proof-of-work requires that data be difficult and time-consuming to create but easy and fast to validate.
This is done using the hashing technique detailed earlier in this Bitcoin guide. As previously discussed, a hash is created by performing an algorithm on an input to generate a fixed-length output.
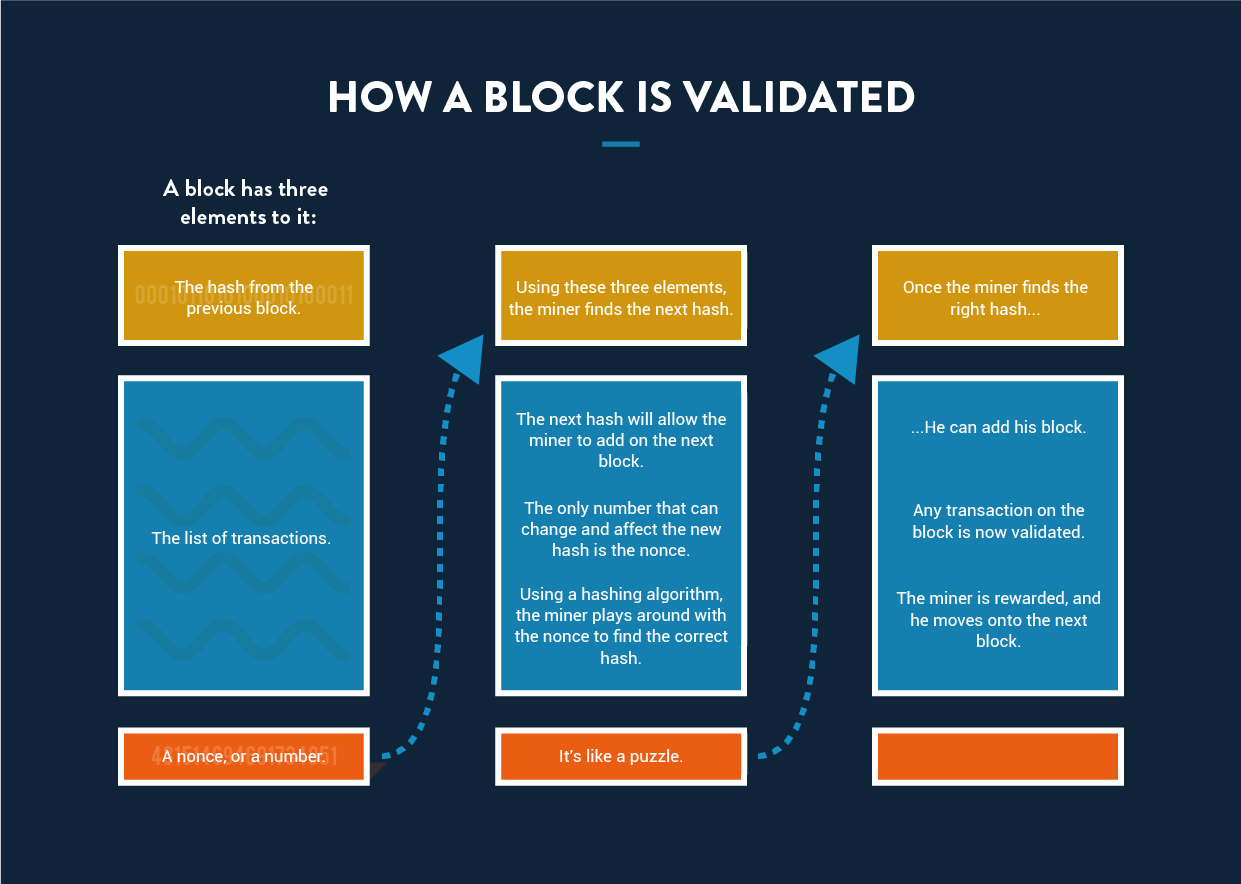
Here, miners must solve a mathematical puzzle to add their block to the existing blockchain, and this puzzle takes some time to solve. Specifically, this puzzle is to guess an input that will result in a hash that begins with a certain number of zeros.
Here’s how Bitcoin mining works:
Say a miner is working on a block. At the top of this block is the hash of the last block on the blockchain. Beneath that are all the transactions that the miner has picked up. Beneath that, the miner adds a number called a nonce. Then he performs a hash algorithm on the entire block.
As mentioned, his goal is to get a hash that begins with a certain number of zeros. If you recall, if the input changes even slightly, it will result in a completely different output. To get the correct number of zeros, the miner needs a precise number at the bottom. So how does the miner know which number to put there?
He doesn’t.
He has no choice but to randomly guess different numbers until he gets the correct hash. Whichever miner manages to do this first gets his block added to the blockchain.
According to the Bitcoin protocol, this whole process should take about 10 minutes. Because there are constantly new miners with different amounts of computing power, the number of zeros required will periodically change. This adjustment is a key element of how Bitcoin works and ensures that the network remains balanced.
This process allows new blocks to be added to the chain and also performs another essential function — it ensures the security and integrity of the entire system.
How?
Well, because each block contains the hash of the last block as its header, even one change to one character in any of the transactions would lead not only to a change in that block’s hash — but to every single block in the chain.
That means that if someone wants to alter a transaction, they would have to recalculate every single block that came before, which would require an impossible amount of computing power. It also means that each time a new block is added, the blockchain gets more secure.
5. How Proof-of-Work Prevents Double Spending
Suppose Alice has an online shop that accepts Bitcoin payments. Bob comes to her website and places an order for an iPhone. If Bob chooses Bitcoin as the payment option, understanding how Bitcoin transactions work becomes crucial for both parties. Alice would, of course, wait for the payment confirmation before sending the iPhone.
But because of the way blockchain works, Bob could try to defraud Alice by initiating two transaction messages with the same signature — one in which he sends the money to Alice, and another in which he sends it to himself at a different address.
Once Alice sees the transaction message sending her the money, she would ship the product. However, if the transaction in which Bob sends himself the money makes it onto the blockchain before the legitimate transaction, then that’s the one that’s going to go through — so Bob ends up getting his iPhone for free.
This makes it seem like if Alice were wise, she wouldn’t send the iPhone right after the transaction was broadcast; instead, she would wait until it’s on the blockchain.
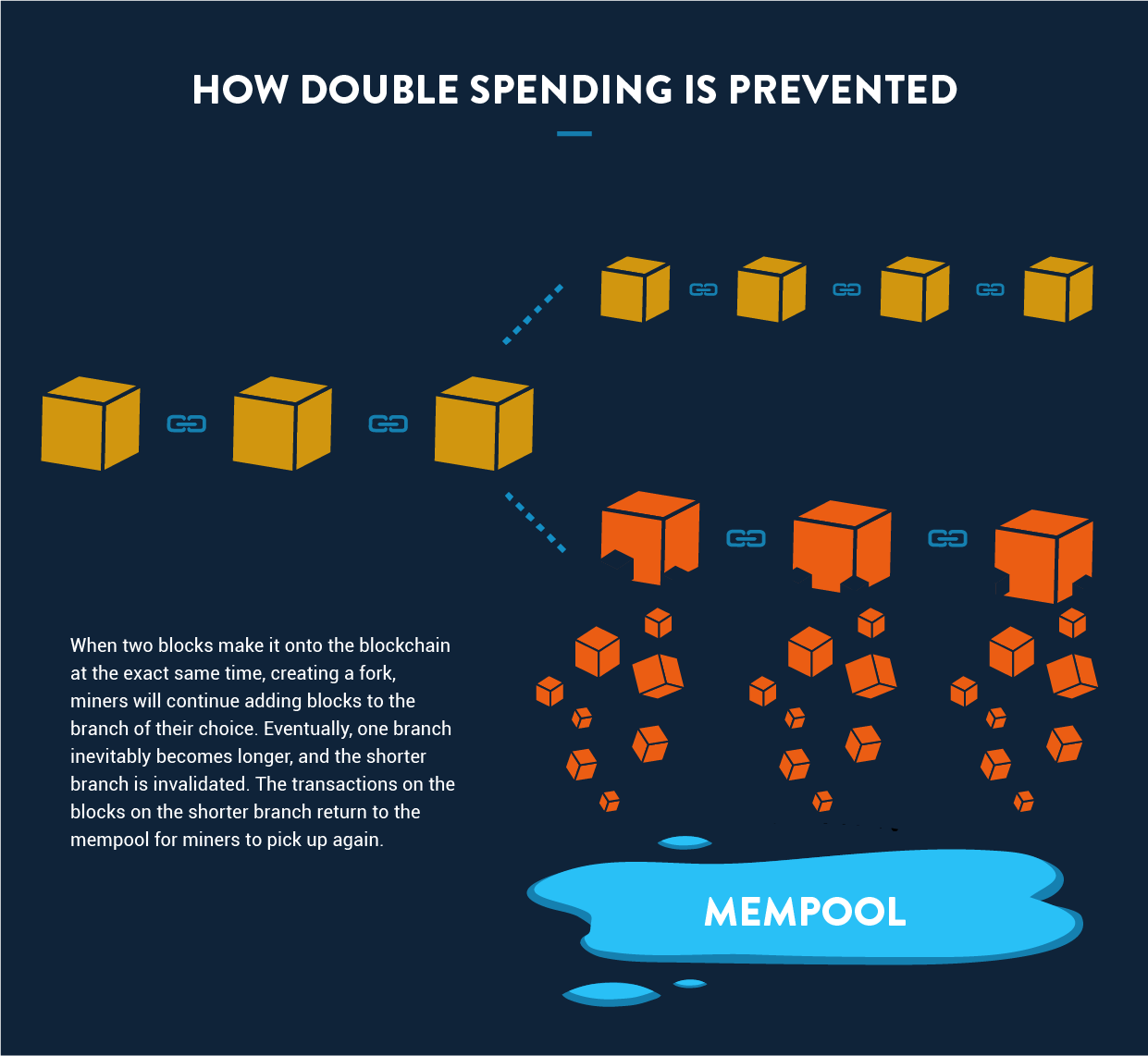
But actually, not even that is good enough.
This is because occasionally, more than one block is added at a time, creating a fork in the chain. In these instances, the next miner who finishes a block can choose which branch he wants to add to. Pretty quickly, one branch will become longer than the other. When this happens, the shorter branch is dumped, and all the transactions on it are shunted back to the mempool.
Because of this, a transaction should only be considered complete after at least six blocks are added to the chain. The transactions that have been recently added to the blockchain are sometimes referred to as hot transactions.
From this, we again see how proof-of-work — i.e., doing more computational work — secures transactions.
But let’s take a look at another hypothetical: What if Bob managed to create two branches, with one block containing the legitimate transaction, and the other the fraudulent one? Bob also then added to the fraudulent branch at the same rate other miners added to the legitimate one.
Alice, seeing the branch with the legitimate transaction grow, would get a false sense of security, leading her to send the iPhone. Eventually, Bob could make his chain longer, sending the legitimate transaction back to the mempool. Because it has the same signature as the fraudulent transaction, if it gets picked up again, it will be considered invalid.
It’s an interesting hypothetical, and in theory could work.
But in reality it’s impossible.
This is because it takes computational power and time to solve and add a block. Even with an incredibly powerful processor, Bob would need to control more than half the CPU on the Bitcoin network to pull off this stunt. That’s why this concept is sometimes referred to as a 51% attack.
In the Bitcoin process, the branch with the legitimate transaction would end up longer, and the fraudulent transaction would get dumped back in the mempool. By the time it gets picked up by another miner, it would be considered invalid because the signature was already used in the legitimate transaction.
All that said, even if Bob did somehow manage to gain control of the network, the amount of time and resources it would take to cheat the system just isn’t worth it. He would earn more Bitcoin simply by mining according to the rules.
3. Beginner’s Guide to Using Bitcoin
There are numerous ways you can use Bitcoin, but all basically involve the same process. Understanding how Bitcoin works comes down to three steps: acquiring Bitcoin, managing your wallet, and trading Bitcoin for goods and services. Let’s look at the steps one by one.
1. How to Buy Bitcoin
Besides mining Bitcoin (which we discuss in Section 2), you can simply purchase it. This can be done through an online exchange or by making an Over The Counter (OTC) transaction.
OTC transactions are trades made with another individual — generally via a broker who manages negotiations. This is the favored method for those seeking to buy substantial sums of Bitcoin (i.e., in the hundreds of thousands or millions of dollars worth). This is because exchanges don’t have the liquidity to facilitate such large transactions.
Although OTC trades aren’t regulated like exchanges, a reputable broker will ensure that no fraud occurs. Some high-profile brokers include Interactive Brokers, eToro, and Robinhood.
For those learning how Bitcoin works, exchanges like Coinbase, Coinmama, or itBit are the safest and easiest way to procure Bitcoin. To avoid foreign exchange fees, buy from an exchange in your country, which are typically directly integrated with local banks.
Exchanges are straightforward to navigate. You just go to the website and follow the sign-up instructions, and you can get started buying Bitcoin right away.
Note that most exchanges require personal information such as your name, email, and phone number. And obviously, if you’re using your credit card to buy Bitcoin, or are doing so via a bank transfer, it will have that information too.
If you choose to use an exchange, this point in the process — when you buy or sell Bitcoin — is when you can lose your anonymity. Bitcoin transactions made through exchanges are not anonymous, as the exchange will have your personal information and the transaction details.
2. How to Manage Your Bitcoin Wallet
On the Bitcoin network, owning Bitcoin simply means having an address and private key. As mentioned earlier in this Bitcoin guide, this private key allows you to encrypt digital signatures.
Without a private key, you have no access to your Bitcoin and no way of proving that it belongs to you, so you should keep it in as secure a place as possible.
You receive a private key when you are issued a Bitcoin address. The key is a 256-bit length of data, which can also be represented alphanumerically. For example, people sometimes use it in hexadecimal form — meaning 64 characters in the range of 0-9 or A-F. The most common option is to use the Wallet Import Format (WIF), which is 51 alphanumeric characters, the first of which is always the number 5.
Here’s an example of a WIF private key:
5KJvsngHeMpm884wtkJNzQGaCErckhHJBGFsvd3VyK5qMZXj3hS
Losing your private key is like losing your Bitcoin. If you lose your private key, you cannot recover your Bitcoin. Similarly, if someone else gets hold of your private key, then he or she can withdraw all your Bitcoin.
So, how do you protect your private keys and your coins?
One option is to store your coins offline. Storing your coins and private key on a USB drive ensures that attackers and hackers cannot steal your information. However, if you lose that drive — or if someone manages to steal it physically — you’re out of luck.
Another option is to store your Bitcoin with a third-party provider — or client — that offers a Bitcoin wallet. This is a type of software that stores the addresses and key pairs for all your Bitcoin transactions.
However, the growing number of attacks these days targeting crypto exchanges have made it slightly unsafe to store your keys with them. Experts recommended you store your keys offline.
3. How to Use Bitcoin for Transactions
How Bitcoin works when making transactions is very simple. If you have a specific person to whom you want to send money, you just need their Bitcoin address, which you enter into your Bitcoin client. If the person you’re sending money to uses the same client as you, you often need to enter the email address to which they linked their account.
Online businesses that accept Bitcoin usually have a button that you click that will automatically bring you to your wallet, allowing you to make the payment from there. For wallets installed on mobile devices, they often provide a QR code to scan with your phone.
4. How Bitcoin Works with PayPal
In late 2020 PayPal announced customers could now buy, hold, and sell numerous cryptocurrencies on its platform, including Bitcoin, Ethereum, Bitcoin Cash, and Litecoin.
That move was just the beginning of a long-term strategy to incorporate digital currencies into PayPal’s operations.
By 2021, customers could use the cryptocurrencies to make purchases at more than 26 million websites currently using PayPal for transactions. That same year, PayPal announced it would enable cryptocurrencies on Venmo, its popular peer-to-peer payment app.
By 2024, Paypal launched its own stablecoin, PayPal USD (PYUSD), which is fully backed by the US dollar. Additionally, PayPal partnered with crypto.com to provide more crypto payment options for users.
The same month PayPal made its announcement, then-Twitter CEO Jack Dorsey’s financial company Square announced it had purchased 4,709 bitcoins for a price of $50 million. That investment represented one percent of Square’s total assets through the second quarter of 2020.
Even establishment financial institutions such as Fidelity Investments are dipping their toe into the cryptocurrency pool. In August 2020, Fidelity announced the launching of its first Bitcoin Fund. Fidelity clients can now access the Wise Origin Bitcoin Index Fund I through a new business unit called Fidelity Digital Funds.
By establishing both acquisition and retail features, PayPal represents perhaps the most accessible ‘gateway’ yet for Bitcoin and the other cryptocurrencies. Through PayPal, Bitcoin traders can purchase Bitcoin and store it in PayPal’s digital wallet. They can do this as an investment or as an alternative means of payment for any online purchase. This serves as an easy entry point for those learning how to use Bitcoin.
While PayPal may hope this will make Bitcoin the online payment currency of choice, some doubt this will take place anytime soon. Industry expert and author of several Cambridge University studies on cryptocurrencies and Blockchain, Michael Rauchs, suggests that people who acquire Bitcoin will be more interested in holding on to it for its likely increasing investment value than spending it online.
Even if the initial tendency is to treat Bitcoin as more of an investment, the widespread appeal and trusted track record of PayPal is likely to introduce Bitcoin and how it works to a much wider audience at a much faster pace.
5. Credit Card Companies Drop Pornhub
In December 2020, the major credit card companies announced they would no longer be associated with Pornhub. Launched in 2007, Pornhub is the biggest porn website in the world, with more than 130 million daily visitors.
The credit card boycott resulted from the December 2020 NY Times story which showed how the site contained several videos depicting child sexual abuse, rape, and revenge porn. Right away, Porhub underwent self-regulating corrective measures by deleting the majority of their videos and eliminating the site’s download capabilities which made it easy for illegal content to resurface.
Ultimately, these efforts proved to be too little, too late. Within days of the NY Times story, MasterCard cut all ties with Pornhub, quickly followed by Visa and Discover Card.
Pornhub first accepted cryptocurrency as payment on its site in 2018 when Verge and Tron blazed the trail, soon followed by Pumapay and stablecoin. Just months before the credit card boycott, Pornhub announced that Bitcoin and Litecoin would be accepted as payment. This shift toward cryptocurrencies is a key part of how Bitcoin works as a decentralized and censorship-resistant form of money.
The fallout from the NY Times article bodes well for Bitcoin’s future value. It’s unlikely Pornhub’s 76 million active paid members are going to go away. More likely, they will use Bitcoin (as the best-known cryptocurrency) as a payment method.
There are several examples of the porn industry driving innovation in technology. In the late 1970s, Betamax and VHS were fighting for videocassette supremacy. Betamax had the superior quality but VHS cassettes were better for producing and distributing feature-length videos. Beta didn’t want to have their platform used for adult videos and this was one of the leading factors in VHS becoming the home video standard.
The porn industry was largely responsible for the boom of online payment technology around the turn of the millennium. In 1999, online users spent more than USD 1.3 billion on porn sites. This worked out to more than people were spending on books and airfare.
The porn industry didn’t invent online payment, it simply became the engine behind the rapid proliferation of online payments. History seems to be repeating itself in how Bitcoin works as an alternative payment method when mainstream methods won’t work.
How to Make Money from Cryptocurrency
Blockchain technology is completely new and there are plenty of opportunities to monetize it. There are basically two ways: mining and investing.
1. Bitcoin Mining Explained
Mining is a slow but safe method of earning money from Bitcoin and other cryptocurrencies. As we explained earlier in this Bitcoin guide, miners are the people on the network who validate transactions in exchange for a reward. In the case of Bitcoin, there are two types of rewards — one that is received for adding a new block, and the other for picking up a particular transaction.
Different cryptocurrencies have different mechanisms for paying miners; some may only pay for transaction fees, while others incentivize them through other means.
You can participate in the Bitcoin mining process by donating CPU to the network. Because CPU requires electricity, you should consider how your earnings from mining will compare to the costs you will incur. This will depend on the country you’re in and the cost of electricity. The extremely low cost of electricity in China is the reason why the majority of the miner network resides there.
Other factors that will contribute to your calculation are the hash power of your hardware and the current price of Bitcoin.
For more serious miners, there is specialized hardware available with high hash rates that will give the miner better odds of solving a block. An ASIC (Application Specific Integrated Circuit) is the general term used for such a device. With the combination of an ASIC and cheap electricity, you could find the mining business profitable.
You can either be an individual miner or you can be a part of a group of miners who share CPU. The latter is known as a mining pool, and is generally a good idea for those without a lot of hardware. In a mining pool, members are paid in proportion to the amount of CPU power they contribute. For Bitcoin mining, the following pools are well known:
- F2pool based in China
- BTC.com also based in China
- Braiins (formerly Slush) based in the Czech Republic
For other cryptocurrencies, you’ll need to research which pools are worth joining. Generally, pools are created as soon as a currency starts gaining traction.
2. How to Invest in Bitcoin
Direct investment is a quick but risky way to make money from cryptocurrencies. If you don’t have the time or resources for mining, you can simply purchase the cryptocurrency from an exchange. Bitcoin has shown astonishing returns over the past few years, and has caught the attention of all sorts of investors.
While you can purchase crypto coins any time, there is a special time period when the opportunity for profit (and loss) is at its highest: the ICO (Initial Coin Offering). For those familiar with equity investing, you can say that it’s similar to an IPO (Initial Public Offering).
An ICO is an event at which crypto coins are first introduced to the world and have not yet been valued. At that time potential investors assess the project and decide whether to invest in it. If the project is implemented and gains traction, the value of the coins rise, earning stakeholders a profit.
Cases in which people bought Bitcoin and were later shocked include:
- In 2009 a Norwegian student researching encryption bought 5,000 BTC for around $22, and then totally forgot about it. Four years later, when the media brought Bitcoin into the limelight, he remembered his purchase and was surprised to find that it was worth around $850,000 at the time. He sold one-fifth of his coins to purchase a luxury home in a posh area of Oslo, and the rest is worth $250 million as per today’s exchange rate.
- On May 22, 2010, computer programmer Laszlo Hanyecz bought two pizzas using Bitcoin. He paid around 10,000 BTC, which at that time was only worth around $41. However, at the current exchange rate, those bitcoins are worth more than $600 million, making them the most expensive pizzas ever purchased. In an interview, Laszlo stated that since Bitcoin barely had any value back then, he was excited that he could buy anything with it.
- James Howell, an IT engineer from Newport, Wales, started mining Bitcoin using his laptop in 2009. He collected over 7,500 Bitcoin and then stopped. Later, he sold his laptop on eBay, but before doing so removed the hard disk where his Bitcoin private keys were stored. He kept the hard disk in a drawer hoping to cash out the bitcoins when their value increased. But a few years later, during some house cleaning, the hard disk was thrown out by mistake. As of today’s exchange rate, the lost bitcoins are worth around $500 million. James wanted to carry out a search operation at the landfill — an expensive and complex task — but due to environmental concerns and the possibility of hazardous gasses leaking out, the operation was not carried out.
Even with stories of vast increases in Bitcoin’s worth, however, investors should bear in mind that the value of cryptocurrencies can fluctuate wildly. For example, between October 2023 and September 2024, Bitcoin’s value has risen and fallen unpredictably.
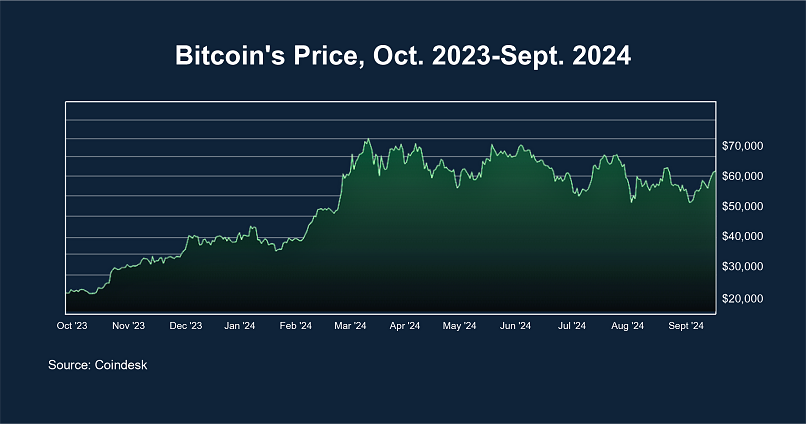
Cryptocurrencies in general are highly volatile, and past performance is no guarantee of future success. In other words, just because the value of Bitcoin has increased in the past doesn’t mean it will continue to do so. That’s why potential investors need to understand the process of how Bitcoin works before they begin investing.
Our advice is to not invest more than you can afford to lose. DO NOT shell out all or even a major chunk of your hard earned money hoping for great returns. You may get lucky, but the risk of losing it all if Bitcoin’s price takes a significant dip isn’t worth it. You can see the latest Bitcoin exchange rates on our Bitcoin calculator.
Understanding Bitcoin’s Legal Status
With the rising popularity of Bitcoin, cryptocurrencies in general have caught the attention of government and financial regulatory bodies. Unlike counterfeit fiat currency, which is illegal, in most countries Bitcoin itself is legal.
However, due to the anonymous and unregulated nature of Bitcoin, many governments have placed restrictions on its use. Some worry that Bitcoin and other cryptocurrencies will lead to a loss of the government’s financial control.
Most countries don’t have clear laws regarding the use of cryptocurrencies, so people are often confused as to its status. Therefore, you should check your country’s rules regarding Bitcoin’s legality, and keep in mind that these laws are subject to change.
Holding Bitcoin in Algeria, Columbia, Nepal, Bangladesh, and several other countries is illegal. In contrast, in the United States, Bitcoin is not only legal, but is considered a commodity by the CFTC (Commodity Futures Trading Commission). Regarding taxes, the rules are similar to any other asset.
In many countries, such as India, Bitcoin falls into a gray area in which the government has not declared it illegal, but does discourage its use by issuing warnings against it. This often leads to questions about how the Bitcoin process works and how it is regulated.
What should not need to be stated is that you should not use Bitcoin to buy or sell items or services that are illegal. If a type of transaction is illegal using fiat currency, it is also illegal using Bitcoin or, for that matter, any other cryptocurrency.
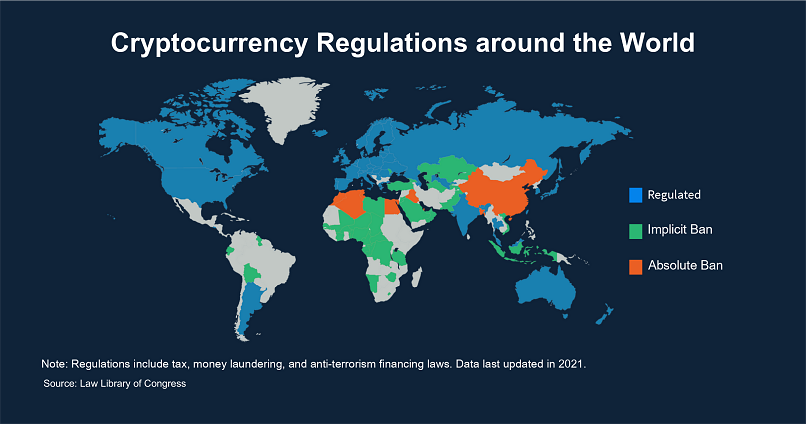
The Dark Side of Bitcoin
Though Bitcoin has many advantages — which we have discussed at length — some government warnings against it are not entirely unfounded.
Some criminal elements look to take advantage of all the excitement and media hype surrounding Bitcoin. For instance, there are cyber criminals who launch Ponzi schemes promising astronomical returns on investments. Only after their money has disappeared do people realize they were duped. Many governments are therefore running awareness campaigns emphasizing the importance of understanding how Bitcoin works and advising people to stay skeptical and invest cautiously.
There are also many other ways cryptocurrency is misused, including:
- With the anonymity and ease of transfer of Bitcoin, terrorist groups have tried fundraising using their Bitcoin addresses. While this has not been very successful in the past, it could at some point succeed. However, user anonymity is restricted to the blockchain network. Once Bitcoin is converted to some other currency, user identity and transactions can be tracked via your IP address. And because every transaction on the blockchain is public, tracking the movement of funds is easy.
- On May 12, 2017, a global ransomware outbreak, known as the Wannacry attack, occurred. This malware took control of victims’ computers and demanded money in exchange for relinquishing it. While the ransomware used was not new, one of the distinguishing features of this attack was that the money was demanded in the form of Bitcoin. This incident obviously brought Bitcoin a lot of bad publicity and raised questions about how Bitcoin works in illegal activities.
- Many online scams that have led to people having their Bitcoin stolen. Typical online banking has several layers of protection, such as a password, two factor authentication, and OTP. But with Bitcoin, only the private key is needed to completely empty someone’s wallet. Fraudsters steal these keys from people’s computers with keyloggers, Trojan horse hacks, and phishing attacks. Understanding Bitcoin is essential to recognizing these risks. Another type of scam involves online sellers advertising a product with a huge discount, and accepting only Bitcoin as payment. Once the buyer pays, the seller ships a very poor quality product — or worse, nothing at all. And since Bitcoin payments are irreversible, there’s no recourse.
- Another category of scam involves an ICO. Since the cryptocurrency market is highly unregulated, some people deliberately launch fraudulent blockchain projects. They promise some breakthrough innovation and convince investors to contribute capital. But instead of actually developing the project, they simply declare it unsuccessful and take all the invested money for themselves. Since bankruptcy is relatively easy to declare, and investing always involves the potential for loss, there is very little that can be done to protect those who back these projects. There are many legitimate ICOs as well, but it can be difficult to differentiate the good and the bad. So if you do consider investing in a new blockchain project, perform due diligence before opening up your wallet.
The Biggest Online Scam In History
Launched in Bulgaria in September 2014, Onecoin eventually became one of the biggest online scams in history, taking in more than $4 billion in just a few years. Onecoin turned out to be a Ponzi scheme designed by its founders, Ruja Ignatova, and Sebastian Greenwood.
Onecoin appeared to be completely legitimate with all the protocols and safeguards investors would expect. Coins were obtained through mining with Onecoin acting as a central network. The coins could later be exchanged for Euros through OneCoin Exchange xcoinx.
According to their YouTube explainer video, Onecoin had Know-Your-Customer (KYC) protocols in place to guard against money laundering. It also laid claim to being the first cryptocurrency with a monthly audit of its blockchain.
In reality, OneCoins weren’t mined using computer resources. Instead, their worth was predetermined by the scammers who programmed the coin to gradually increase from €0.50 ($0.56) to €29.95 ($33.68) in value. They even went so far as to award coins that didn’t exist to their members. Following a lengthy investigation, police determined that there was no true blockchain that was public and verifiable.
Other Implementations of Blockchain beyond Bitcoin Basics
Bitcoin served as the initial and continues to be the predominant embodiment of blockchain technology. But people have found a number of ways to use the technology.
1. Cryptocurrencies
One way people have used blockchain is to create variations on Bitcoin. These often advertise themselves as better or enhanced versions of Bitcoin, and are collectively known as altcoins. Some of the major altcoins are:
- Litecoin: Litecoin launched in 2011 and varies only slightly from the Bitcoin process. One difference is that it takes less time to generate blocks. Compared to the 10 minutes it takes Bitcoin, Litecoin generates a block every 2.5 minutes. This means that Bitcoin transactions are verified more quickly. Another difference is the hashing algorithm used. Bitcoin uses SHA256 for the proof-of-work algorithm, whereas Litecoin uses scrypt. One feature of scrypt is that it’s harder to create optimized CPU or GPU hardware to solve the puzzle faster, making the system more fair for miners. That said, today there do exist ASICS that can be used to mine Litecoin.
- Zcash: Zcash was launched in 2016. Like Bitcoin it provides secure transactions over a distributed ledger. However, Zcash is different from Bitcoin in that it uses a different proof-of-work algorithm (called zk-SNARK) and employs a different privacy strategy. In the Bitcoin process, the sender, receiver, and the amount of money being transferred are all public, whereas with Zcash they can remain private and shielded. By the end of 2017, Zcash had already crossed the one billion dollar market cap.
- Dogecoin: Dogecoin was launched as a joke in response to what some perceive as cryptocurrency mania. Its logo is a coin bearing the face of the dog known from the popular Doge internet meme. It is a complete replica of Bitcoin and offers no differentiation or enhancement, primarily because it was not meant to be taken seriously. Initially the value of the coin was extremely low. However, its value rose significantly and it began taking on serious investors — recently reaching a two billion dollar market cap. The creators, unhappy with the fact that the coin had become the very thing it was meant to mock, eventually removed themselves from the project. Finally, the value decreased significantly when Ryan Kennedy, the owner of a Dogecoin exchange called Moolah, was arrested for fraud. However, starting in January 2018, the valuation started increasing again.
In late January 2021, Dogecoin’s value suddenly skyrocketed 613% in one week. This resulted in its market cap climbing 380% in just 24 hours — to $6.9 billion.
What was behind this incredible surge? Dogecoin was caught in the wake of the most famous stock pump and dump scheme in recent memory. In January 2021, an amateur stock trading community on Reddit called WallStreetBets (WSB) decided to take aim at major hedge funds by pumping up stock which the hedge funds had bet would fail.
Through its subReddit group, WSB rallied enough supporters to target Gamestop and send that stock through the roof, costing the hedge funds a collective $5 billion. The shockwaves reverberated through the financial and political circles. Wall Street establishment called for immediate action, resulting in a lock on Gamestop trading.
Looking for another target for a similar move, WSB turned to Dogecoin. Unfortunately for Dogecoin, the new heights were short-lived. Within days the stock fell approximately 72% to $0.022.
The stock would rebound once again in early February thanks to a single tweet by Elon Musk. When Musk tweeted a Vogue parody cover with a picture of a dog under the banner ‘Dogue’, the stock price shot up 50% within 90 minutes of the posting.
B. Non-currency implementations
As outlined earlier in this Bitcoin guide, the blockchain system is applicable to more than cryptocurrencies. There are many other novel ideas based on the construct that are worth billions of dollars.
- Ethereum: Ethereum is to applications what Bitcoin is to currency. It provides an infrastructure for apps to run without a central server. Like Bitcoin, it depends on nodes across the internet. In this case, the nodes provide the CPU necessary for an app to run. To prevent abuse and to eliminate low quality apps, Ethereum requires that applications spend a currency called ether. The code developed in the Ethereum network is run by a software called the Ethereum virtual machine. Developers use smart contracts to develop the application, which are executed automatically whenever specified conditions are met. For example, one smart contract could be to automatically ship a product once payment is received. Ethereum apps are called DAPs (decentralized applications), and hundreds of them have already been successfully launched. Examples are apps that deal with digital signatures, prediction software, electric car charging management, and online gambling sites.
- Ripple: While Bitcoin is intended for the public, Ripple is meant for banks and payment networks. Currently, banks employ the protocol SWIFT (Society for Worldwide Interbank Financial Telecommunication), which requires the involvement of intermediaries. This, plus fluctuations in currency exchange rates, often leads to transactions being delayed. Ripple enables financial institutions to transfer, settle, remit, and exchange payments in real time without incurring large costs. Although it has yet to be officially adopted, many banks have already begun using Ripple in trial phases. One important difference between Ripple and Bitcoin is that not everyone is allowed to join the network. The computers need to identify themselves and need permission to take part. In that sense, it is not truly decentralized or public.
As we have seen, there are some negative aspects of Bitcoin, and these should be considered by potential investors and addressed by the appropriate authorities. However, that doesn’t mean we should abandon it altogether. Blockchain is a true innovation capable of solving innumerable problems, and understanding how Bitcoin works is essential to using it appropriately.
Did you find this beginner’s guide to Bitcoin helpful? If so, share it with your friends and colleagues on Facebook and Twitter.
Leave a comment
This post is a game-changer for beginners trying to understand Bitcoin! You've made a complicated topic much more approachable. For those interested in exploring more about investment options, be sure to check out the best altcoins to invest and diversify your crypto portfolio.





Please, comment on how to improve this article. Your feedback matters!