COVID Test Data Breach: 1.3 Million Patient Records Exposed Online

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password protected database that contained nearly 1.3 million records, which included COVID-19 testing information and personally identifiable information such as the patient’s name, date of birth, and passport number.
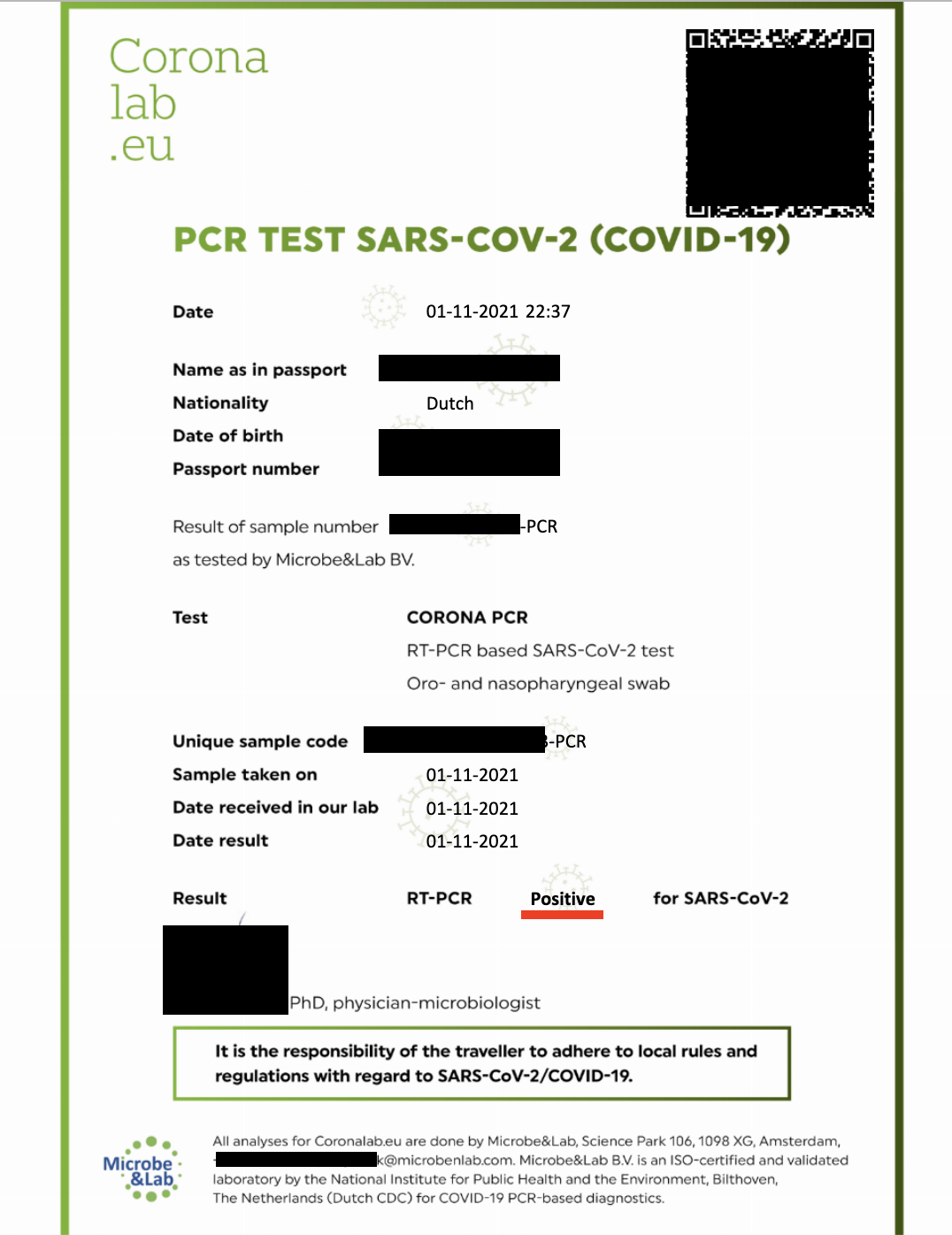
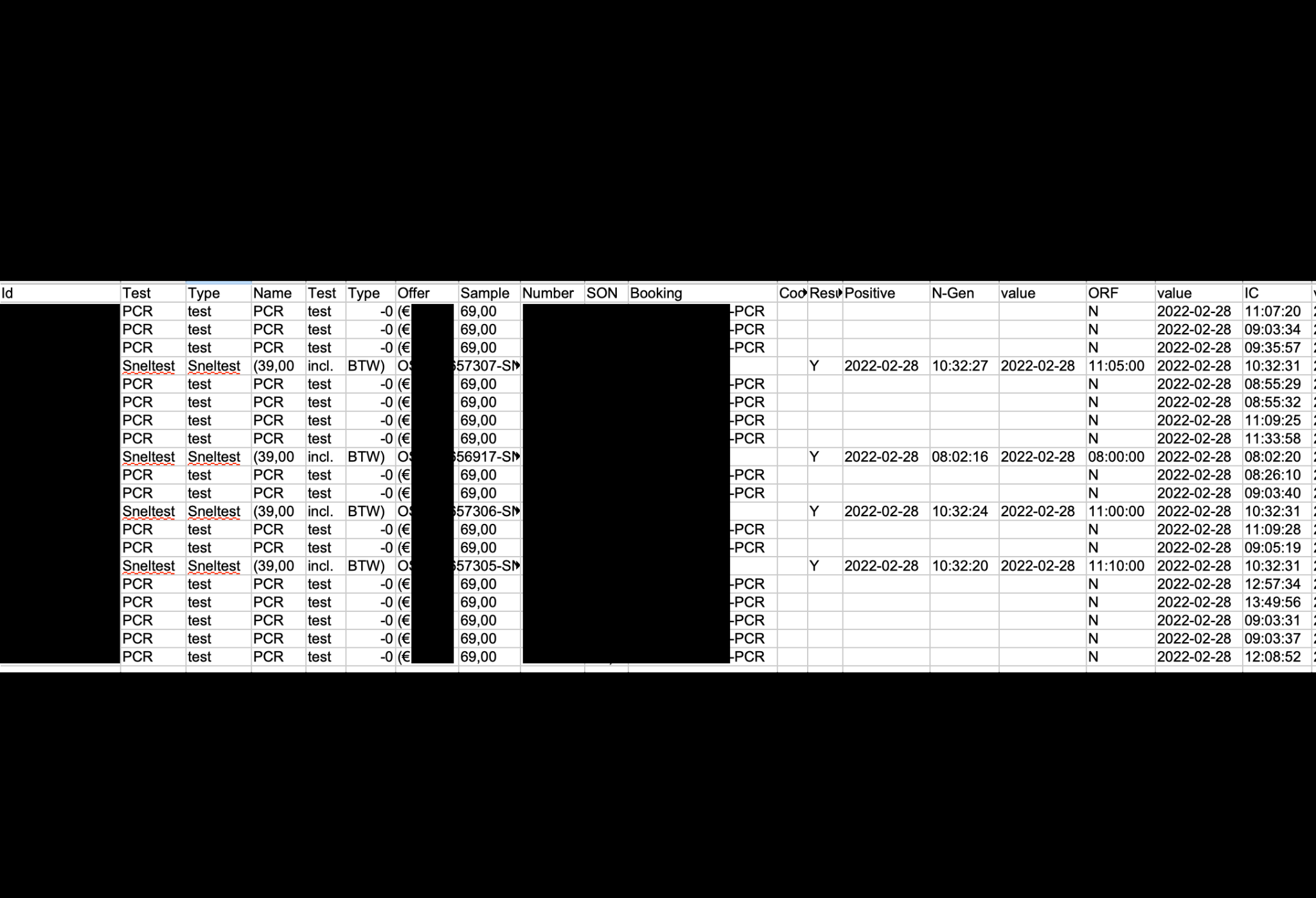
The publicly exposed database contained an estimated 1.3 million records that included 118,441 certificates, 506,663 appointments, 660,173 testing samples, and a small number of internal application files. The exposed certificates and other documents were all marked with the name and logo of Coronalab.eu. Although the website appears to be offline, Coronalab is owned by Microbe & Lab, an ISO-certified laboratory based in Amsterdam, Netherlands. According to the NL Times, “CoronaLab is one of the two largest commercial test providers in the Netherlands”. I sent multiple responsible disclosure notices and did not receive any reply and several phone calls also yielded no results. The database remained open for nearly 3 weeks before I contacted the cloud hosting provider and it was finally secured from public access. In most cases the organization replies or closes public access immediately after receiving a responsible disclosure notice. Another research-based online publication, Cybernews, claimed to have found a similar leak around the same time of my discovery. I cannot confirm if it's related or not.
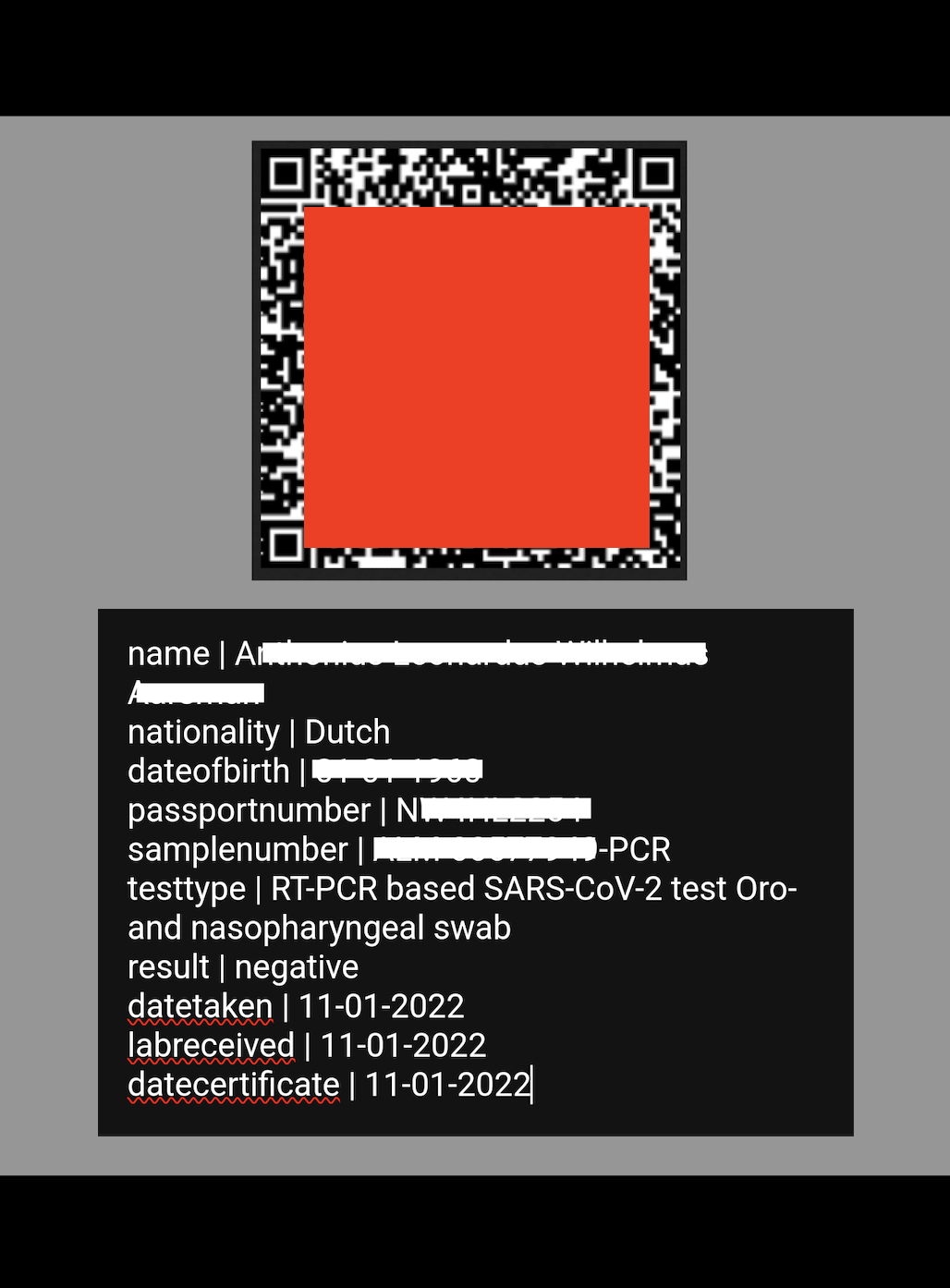
The exposed COVID test records contained each patient’s name, nationality, passport number, and test results, as well as the price, location, and type of test conducted. The database also contained thousands of QR codes and hundreds of.csv files that showed appointment details and many patients’ email addresses. With personal data and emails exposed, cybercriminals could attempt to exploit this information or launch targeted phishing campaigns using internal information or posing as a laboratory employee. The criminal could potentially reference test dates, locations, or other insider information that only the patient and the laboratory would know. Any potential exposure involving COVID test data combined with PII could potentially compromise the personal and medical privacy of the individuals listed in the documents.
According to the Microbe & Lab website: Coronalab.eu is an online platform which helps individuals and companies to test for COVID-19. We do this with a fast COVID test service (PCR test, the Rapid test and the Serological test) with which we can guarantee same day results. Tests include a free travel certificate.
During the height of the pandemic, proof of a negative COVID test was required for nearly all everyday life activities. In many cases, testing was often mandatory for travel, special events, and even employment. There was a massive amount of COVID test data collected in a short period of time, which needed to be accessible for patients or verifications, yet still secure from unauthorized access. Even under normal conditions, data and cloud storage infrastructure takes time to build, test, and properly configure. The speed of the pandemic and the massive amount of testing data forced many laboratories and medical facilities around the world to rush the process. This increased the risk for permission and configuration errors in data storage and data protection. In my professional opinion, now that the pandemic is mostly behind us, it is time for organizations to review the massive amounts of data they have stored and determine if these records are still needed. If they are, organizations must ensure the data is secured from unauthorized access. The records should be encrypted or anonymized to prevent unwanted data exposures or threats from malicious actors.
Possible risks of this exposure
Leaked COVID-19 test results could potentially turn into a breach of personal and health information, compromising the individual privacy of those who may have been affected. The issue of COVID became a contentious political issue full of misinformation, conspiracy theories, and social repercussions that divided people around the world. Many people still don’t want to disclose their vaccine status or if they previously tested positive for COVID for fear of stigmatization. It is not known if anyone else gained access to the exposed COVID test data.
The public exposure of COVID tests has a range of potential future risks due to the fact that so much is still unknown about the long-term health effects of the virus, and we don’t know how pandemic-era data could be used years later. Hypothetically, insurers could raise premium rates if research showed that those who were infected with the virus had a higher risk of future health issues. Overall, leaked COVID test results not only pose risks to personal and medical privacy, but they could also affect how patients view public healthcare providers and how much they trust them to safeguard their medical data. It's crucial for healthcare organizations and technology providers to prioritize data security, including data storage and cybersecurity measures. Another important issue healthcare providers must face is to implement clear record retention policies to determine how long medical records should be kept and how to prevent the risks associated with data that is no longer being actively used.
A passport is a government-issued identity document that contains information intended to be private. Exposed passport details — such as the document number, full name, date of birth, and nationality — could be potentially valuable pieces of information for identity thieves and cyber criminals. Passport data has the potential to be misused for various fraudulent activities, ranging from travel-related fraud (such as booking flights, renting cars, or hotel reservations) to opening financial accounts in the passport holder's name. I am not implying that the people whose passports were exposed were ever at imminent risk; I only mean to provide a real-world example of potential repercussions.
The database contained a large number of test result QR codes. A Quick Response (QR) code can store various types of data, such as website URLs, text, contact information, or commands. Nearly every phone camera can scan a QR code without any additional software. When QR codes store and transmit sensitive data (such as personal details, passport data, and medical test results) in plain text, the codes represent a potential security risk in case they are publicly exposed. In this instance, I was able to scan numerous QR codes and see the test results and all the confidential personal data they contained. As useful and as user friendly as QR codes are, they can be a major security risk. For example, the codes can be easily changed to redirect users to fake websites or prompt them to download malware or other malicious applications. I highly recommend any organization that uses QR codes containing personal information to implement proper security measures to safeguard sensitive data. Encrypting the information, for instance, can help prevent potential threats to privacy and security.
It is unknown how long the data was publicly exposed or if anyone else may have accessed the thousands of COVID-related records. Only an internal forensic audit would identify if others may have accessed the database or performed any other suspicious activity. It is also unclear if customers, patients, or the authorities have been notified of the data incident. The General Data Protection Regulation (GDPR) governs data protection and privacy for individuals within the EU and the European Economic Area (EEA). Medical data, including COVID test results, are classified as sensitive personal data or as a special type of personal data under the GDPR regulations. Organizations who collect and store medical data must adhere to the GDPR's stringent requirements regarding data protection, ensuring confidentiality and security when processing potentially sensitive information. This also includes the technical measures to safeguard data against unauthorized access or any public data exposure.
As an ethical researcher, I never download the data I discover. I only access a minimal sample for verification purposes and redact PII for privacy. Although all records were marked with names and logos of Coronalab and Microbe & Lab, it is unknown who owned or managed the database. I imply no wrongdoing by Microbe & Lab, CoronaLab.eu, or any of their partners or affiliates. Furthermore, I do not imply that patients or data are at imminent risk. I publish my findings to raise awareness and underscore the importance of cybersecurity best practices.



Please, comment on how to improve this article. Your feedback matters!