Giving Platform for Nonprofit Organizations Exposed Donor Records in Major Data Breach

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password protected database that contained just under 1 million records, which included information of a donor platform, including details of charitable organizations, and donors.
The publicly exposed database contained a total of 948,029 records with a size of 465.27 GB. Upon further research, it appeared that the database belonged to a company named DonorView that is developed and owned by Massachusetts-based Connected View. I immediately sent a responsible disclosure notice, and the database was secured from public access several days later and I did not receive a confirmation or reply.
DonorView is a cloud-based fundraising and donor management software solution designed to assist nonprofit organizations, including charities, schools, religious institutions, and other nonprofit entities in managing their fundraising efforts and donor relationships. It provides a suite of tools and features to help nonprofits streamline their operations and improve their fundraising campaigns. According to their website, 200,000+ organizations in 160+ countries manage their data in DonorView; with this tool, these nonprofits have purportedly raised $2,900,000,000 and seen a 46% increase in revenue.
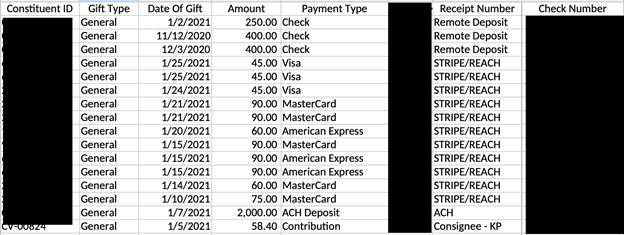
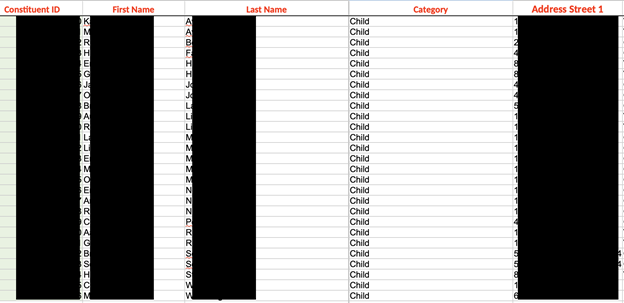
Among the discovered records were.xlsx,.csv, and.PDF files containing a wide range of information, including donations or gifts broken down into categories and details of payment methods such as PayPal and Venmo monthly summaries, payroll deductions, checks, or credit cards. Some of these donation records also contained transaction specifics, completion statuses, and the frequency of donations (one time, monthly, or yearly basis). Many of these documents also contained personally identifiable information (PII) such as donor names, addresses, phone numbers, emails, and more. The documents listed a massive number of “constituents”, which possibly refer to an organization's members, donors, volunteers, or partners. There were also documents that appeared to show information about businesses that either supported or gave donations to individual charitable organizations, or would be prospects for future donations.
DonorView claims to have over 200,000+ users on its website, but with the database containing just under a million documents, it is unclear exactly how many donors were affected as this would have taken a massive amount of time to manually analyze. When data that contains PII is exposed, it is a race against the clock to validate ownership and report my findings so the organization can restrict public access as soon as possible — hopefully, before the data can be exploited. I conducted a random sampling of records and saw one single document that contained over 70k names and contact details of what appeared to be donors. Among other potentially sensitive information in the database, I saw a document that raised money for children through a hospital charity that contained various details, including the child’s name, attending doctor’s name, outlined medical conditions, and waivers indicating whether the child’s image could be used for marketing purposes. It is important to note that while many of the records were marked as “decline” regarding image use, the PII within the document was, at the time of my access, publicly exposed in the document.
The DonorView platform includes communication and engagement tools like email marketing and donor communication templates to help nonprofits engage with their supporters and keep them informed about the organization's activities and initiatives. The exposed database contained 1,525 folders with various engagement files such as event images, buttons, team members, sponsors, logos, etc. The database also contained a shared folder with 653 sub-folders, which is where the spreadsheets believed to contain donor data were stored.
 This screenshot was taken from DonorView’s website, and it shows some of the company’s more well-known clients.
This screenshot was taken from DonorView’s website, and it shows some of the company’s more well-known clients.
Potential Risks of Exposed Charity Data
Any data incident that exposes donor information is a significant concern. Hypothetically, criminals would have sufficient information to contact donors and pose as a charity or cause donors have previously supported and are passionate about, to initiate a fraudulent donation request. The database even contained donor templates that could be modified and sent to prospective donors. Criminals could potentially create similar email addresses and contact donors to update their payment information. In such situations, the criminal could then ask for credit card and banking information or additional personal data. With insider knowledge and the donor’s history details, the victim would have no immediate reason to suspect potential fraud. I am not saying this risk is imminent, I am only highlighting the potential risks of how potential vulnerabilities could be exploited via exposed charity records. Only DonorView would know who else may have accessed the records and the timeline of the exposure.
Another thing that organizations should be aware of are the file formats in which they store documents. Older binary file format are also a potential risk. Some legacy systems may still use.xls files but it is highly recommended to use the newer.xlsx format for improved compatibility and more enhanced security features. There are numerous potential risks of.xls files that include limited encryption or password capabilities, and vulnerabilities to macro viruses that can be embedded in Excel macros. These malicious scripts can execute harmful actions on the user's computer when the file is opened. To mitigate possible security risks, I recommend using the.xlsx file format for any spreadsheets and to consider converting older.xls files to.xlsx. Although DonorView does use the more secure.xlsx file type, at the time of my limited review, I didn’t see any of the documents with enhanced encryption or password protection security measures.
Companies that provide services to charities and nonprofits like DonorView should have comprehensive cybersecurity measures in place. I highly recommend that organizations that collect and store sensitive data use encryption, access controls, regular security audits, employee training, and have an incident response plan in place. Such protocols should include informing potentially affected individuals transparently about any breach or data incident, to minimize the impact on their customers and business.
For donors who may have potentially had their names, contact information, and donation history exposed, I recommend being aware of any suspicious emails or phone calls asking for your personal, credit, or banking information. In other non-related breaches, cybercriminals have attempted to exploit exposed data for phishing scams. If you suspect that the person or organization soliciting donations or personal information is not legitimate, I recommend that you should contact the organization through official communication channels to verify the request. Individuals who take a proactive approach to safeguarding their personal information can help mitigate potential risks and lower the chances of being the victims of fraud.
As an ethical security researcher, my primary focus is to protect the data of individuals and organizations from potential security threats. I never download or extract the data that I find. In the course of my research, I identified a data exposure and my immediate action was to responsibly report the findings. It is unclear how long the records were publicly exposed or who else may have had access to the database. I am not implying or insinuating that anyone else accessed these records and only highlighting potential risks of the exposure. Upon sending a responsible disclosure notice to DonorView regarding my findings, the database was subsequently secured from public access. However, I did not receive any formal response or statement from DonorView by the time of this publication. It is not my intention to imply wrongdoing or to suggest that exposed records, charities, or individuals were ever at risk. My objective is purely to contribute to heightened cybersecurity awareness and to advocate for robust data protection measures across digital platforms and repositories.
Disclaimer: The content and images in this article are the property of vpnMentor. We permit our images and content to be shared, as long as a credit with a link to the source is provided to vpnMentor as the original author. This way, we can continue our mission to provide expert content and maintain the integrity of our intellectual property.





Please, comment on how to improve this article. Your feedback matters!